Chapter 2
FortiGate Hardware Overview
Information in this chapter:
• FortiGate Custom Hardware Accelerations Overview
• Features of the Last Four Generations of Content Processor (CP) ASIC Functionalities
• Features of the Network Processor (NP) ASIC Functionalities
• FortiGate Hardware Accelerations Behaviors
- Firewall Acceleration using NP ASIC
- VPN Acceleration using NP and CP ASIC
- UTM Acceleration using CP and SP ASIC
• The ‘Black Art’ of FortiGate Sizing
• Assessing The Recommended FortiGate Solution
As information technology matures, the threats against it evolve ever more quickly and increase in complexity. It’s not just a firewall component that is needed in today’s networking environment but several products are needed to help mitigate potential threats towards and most dominantly from within a company’s networks [1]. Network components such as Application aware firewall controls, Intrusion Detection & Prevention, Anti-virus/Anti-spyware, Anti-spam, Web content filtering, and Data Loss Detection & Prevention systems are just some the needed components to help mitigate potential threats. Fortinet have and continue to reshape the network security world with the concept of combining majority of these key network security components into one cohesive solution for the constant changing security landscape of threats. The solution Fortinet developed created a new category of network component in which market researcher, IDC called a UTM (Unified Threat Management) solution. The FortiGate UTM appliances and system products were formed and are considered Fortinet flagship products line. The purpose of this chapter is to provide insight from the beginning to the current FortiGate products line. In addition, we will cover topics surrounding the FortiGate solution that are not entirely covered by Fortinet own documentation such as its proprietary hardware and software features and sizing the solution. Lastly, we’ll provide a high-level overview of Fortinet’s remaining products portfolio.
FortiGate Hardware Overview
The Fortinet Way
Fortinet product focus has always been an appliance-based solution. So why was the appliance based-solution chosen over a typical software-based approach? We can see from the evolution of routers and firewalls, appliances provided a more focused way of handling these functions with through custom software & hardware features. From a business standpoint, we could see this approach has been a successful model for many companies such as Cisco, Juniper, Netscreen, and Fortinet. Now although you can have hardware customized into an appliance form factor it does not always mean there are also further customized circuitry within an appliance. Most security appliances out there are built from a general purpose computer foundation. The biggest limiting factor in general purpose computers for any security network performance handling capabilities are the circuit board bus and CPU. From a very high level, Figure 2.1 shows a typical general purpose computer designed appliance in which the CPU handles all network communication. Competition with this architecture would suffer performance constraints as additional UTM features are enabled.
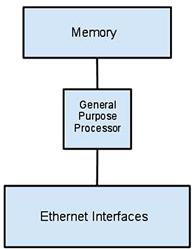
Figure 2.1 High-Level CPU only Architecture
Throughout the evolution of firewalls, companies that are more focused on developing software to operate on general purpose machines also leverage special add-on hardware acceleration components installed within the computer ISA, EISA, or PCI slots. Generally these types of cards could provide additional memory expansion, or additional dedicated processors such as ASIC (Application Specific Integrated Circuits) to offload encryption algorithm computations used for IPSec. Although the additional add-on cards do help boost performance they do not provide higher performance when compared to dedicated appliances with specialized custom hardware that are integrated into a close system architecture design.
The Fortinet Way
Tighter integrations with Close system architectures
Fortinet’s FortiGate UTM solution is built from the ground up with the idea of a close system architecture providing the ability to tightly integrate proprietary software with custom hardware technology. Case in point, a single packet could flow through multiple inspection engines all in one pass through their solution without having to disassemble and reassemble each time it has do apply Anti-virus/spyware, Web Filtering, IDS, IPS, Application Controls, DLP or Anti-spam. In addition, each security engine component for these inspection technologies is modular with fault-tolerance capabilities. This protects against scenarios where resources are consumed or for some reason an inspection process goes offline (see Chapter 6 for additional information). Many vendors who claim to support a single-pass architecture are limited to an all or nothing approach. So if one module fails, the entire inspection flow fails.
So how does Fortinet addresses performance concerns on their UTM platforms, especially when additional features are enabled? Besides providing a turn-key solution in which the custom hardware design is combined with proprietary software, Fortinet appliances also include various proprietary custom chipsets known as FPGA (Field Programmable Gate Array) along with custom circuit boards to help boost performance. From a FPGA/ASIC architecture, let’s examine the advantage it has with Fortinet solution to performance handling at the application layers of their UTM FortiGate solutions. Using the high-level diagram in Figure 2.2, we’ll illustrate the packet flow handling with Fortinet’s Content Processor (CP) ASIC. When packets arrive into the Ethernet interfaces, a general purpose processor would direct traffic to the CP ASIC when application layer inspections are required to assist with content inspection. The CP ASIC was specifically developed to help offload content inspection capabilities from the general purpose processor(s) against threat patterns loaded into memory for comparisons. Patterns are also dynamically loaded into memory to be used by the CP ASIC for comparisons. These processors can perform protocol recognition and parsing providing a quicker way of reassembling data streams to be inspected for potential malicious content. CP ASIC are primarily used to offload application controls, Anti-virus/spyware, intrusion detection & prevention, and other application level security functionalities.
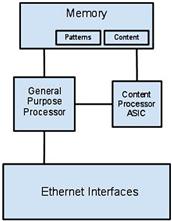
Figure 2.2 High-Level Content Processor (CP) ASIC Architecture
In addition, the CP ASIC provides additional cryptography acceleration which will be outlined in detail in the hardware accelerations section. Cryptography accelerations help increase performance for IPSec and SSL capabilities on the product. Besides CP ASIC, Fortinet has also incorporated another content level FPGA/ASIC called a SP (Security Processor). The security processor combines FPGA logic with multi-core/multi-threaded CPU operating at the interface level. This provides additional intrusion detection & prevention, IPv6, and Multicast accelerations. These types of ASIC were originally offered as add-on modules but have since been migrated into newer FortiGate models.
So we understand Fortinet has developed custom hardware to help with application level inspection but how about network level accelerations? Network acceleration hardware was also another area Fortinet has invested in with the development of the NP (Network Processor) ASIC. Given the name of network processor, its purpose is similar to other network processors on the market used for high speed processing of network level flows. These processors are typically designed in-line with the network flow communications path as illustrated in Figure 2.3—High-Level Content Processor (CP) ASIC and Network Processor (NP) ASIC Architecture. With the NP ASIC positioned in-line it helps reduce load on the overall system. In addition, Fortinet’s custom NP ASIC design provides multi-gigabit speed when processing in stateful firewall traffic filtering, Network Address Translations (NATs), protocol anomaly detection, and expedited delivery of latency-sensitive traffic at the interface level. These processors can also be used for IPSec VPN traffic offloading capabilities.
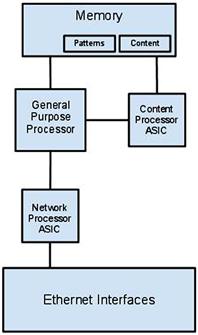
Figure 2.3 High-Level Content Processor (CP) ASIC and Network Processor (NP) ASIC Architecture
Evolution of FortiGate
Fortinet first appliance product release was the APSecure 300 which was launched as a network-based Anti-virus, IPSec VPN, and Firewall solution. The first product name was derived from the company’s previous name of APSecure which was later changed to Fortinet. With the new company name, Fortinet product naming convention has been pretty straight forward and obvious with using a portion of the company name thereby all of its current product naming convention starts with Forti…! Before any sales were made the first Fortinet appliance was quickly renamed from APSecure 300 to FortiGate 300. Eventually additional models came about such as the FortiGate 50, 100, 200, and 400.
The initial appliance incorporated both a proprietary harden OS, called FortiOS (v2.16 was the first official release) and a proprietary hardware circuit board designed with a general purpose CPU along with a chipset design that provided performance offloading capabilities using a FPGA (Field Programmable ASIC). The original FPGA was from a third party and was used in the first hardware releases of the FortiGate 50, 100, 200, 300, and 400 models. Within a year the third-party FPGA was replaced with the first Fortinet custom developed FPGA called a CP1 (Content Processor v1). The initial CP1 provided offloading accelerations capabilities related to content (Layer 7) inspection and encryption algorithm accelerations. Because the CP1 was based on a programmable ASIC rather than a static ASIC, it was not limited to the functionality designed into the silicon. To assist with the constant change in method of content inspection, Fortinet cleverly designed it’s own proprietary language used to reprogram the CP via it’s FortiOS firmware updates. The proprietary language use to communicate with the CP ASIC is called CPRL (Compact Pattern Recognition Language).
Throughout the years, Fortinet came out with several iterations of the Content Processor ASIC and eventually additional types of ASIC(s) use to offload additional functionalities. As of this writing, the Content Processor has been through its eighth generation. An ASIC design and development is not an easy task, it’s generally involves 1–3 years process from beginning to end. The cost in developing an ASIC is not low. The initial cost of developing a single ASIC technology from scratch requires a multi-million dollar investment and generally takes years in development cycle. That Fortinet has gone through eight cycles of this development effort is a testament to Fortinet’s industry leadership.
Current FortiGate Solutions
As with any innovative company, to keep up with the evolution of technology and market demands Fortinet had produced many FortiGate models since their first product in late 2002. Besides hardware changes, there were also accompanying software changes. From a hardware stand point, newer circuit board designs with faster bus speeds and more memory along with newer ASIC(s) that had evolved with additional performance handling features and faster processing power. As of this writing, Fortinet has developed four different types of ASIC each with two or more revision enhancement such as the CP8, NP4, SP2, and SoC ASICs which we’ll go into further detail on the following sections. From a software standpoint, additional feature enhancements were added in almost every major and minor release of FortiOS.
The FortiGate operating system, FortiOS, is considered firmware—encompassing not only a proprietary kernel used to operate the entire solution but all the necessary programming for the everyday operation of the solution. FortiOS is stored and loaded from on-board flash during boot-up of the solution. The FortiOS firmware itself is upgradeable via its graphical interface or command line interface over the network or via a USB-connected device. Additional details of the firmware release cycles and upgrade process would be outline in the next chapter.
We’re not going to outline every hardware product release and features per release as the majority of this information can be founded at the following web links:
For latest Fortinet product releases:
Fortinet website (www.fortinet.com).
For End of Sale/End of Support products references:
With a valid support login, this information can be founded at https://support.fortinet.com/EndUser/ProductLifeCycle.aspx.
For current and past feature FortiOS releases:
There are two locations this information can
a. At Fortinet main documentation website which is publicly available at: http://docs.fortinet.com.
b. Each FortiOS firmware release includes release notes. Release notes are a good source of information on new features added, upgrade & downgrade processes, FortiGate models the firmware is supported on, bugs that were addressed, and any known bugs pending resolution. Firmware release along with release notes do require a valid support login to access them at: http://support.fortinet.com.
As of this writing, the current FortiGate appliances ranges from the FortiGate 20C at the low end appliance models to the 5000 series modular system chassis solutions. The FortiGate solution is the only solution in the market as of this writing with the most third party certifications. Certification such as ICSA Labs certifications on Gateway Anti-Virus Detection, Network Firewalls, Network IPS, and SSL-TLS VPN. In addition, Virus Bulletin 100, IPv6 Ready Phase 2, NSS UTM, Common Criteria EAL-4+, and FIPS-140-2. It’s safe to state that Fortinet pretty much have all market sizes covered with their breath of FortiGate platform offerings.
Virtualized Appliances
To keep up with the industry movement towards virtualization, Fortinet has also ported over the FortiGate UTM into a Virtual Machine offering. Virtualized versions of the FortiGate UTM solution are provided in a Virtual Machine Open Virtualization Format (VM OVF). VM versions are also available with most of Fortinet product portfolio offerings that would be highlighted towards the end of this chapter. Benefits of moving to a virtualized solution are beyond the scope of this book but this information can be founded at any virtualization vendor website such as VMWare website: http://www.vmware.com/virtualization/.
Although virtualization might be a viable option for some of the Fortinet product offerings such as their central management solutions, FortiManager and FortiAnalyzer, there are sacrifices to consider when virtualizing the FortiGate itself. One sacrifice encountered with a VM version of FortiGate would be related to performance. Based on our discussion earlier in this chapter, the FortiGate appliance and system solutions incorporate custom hardware to help accelerate performance and reduce load concerns when compared to other competitors developing their solution off of general purpose computers. The same idea of custom hardware goes out the window with a VM version of the FortiGate.
FortiGate Custom Hardware Accelerations Overview
The purpose of the section is to highlight Fortinet key differentials of their various ASIC technologies used within their FortiGate UTM solution. For complete technical details of Fortinet hardware accelerations please reference their “FortiOS Handbook: Hardware” documentation located at Fortinet public documentation site [2] under the FortiGate section.
Fortinet custom ASIC development milestones:
2002—Started out with the first development of the Content Processor (CP) ASIC. This was the first phase in hardware performance acceleration for content level scanning along with IPSec VPN cryptography and key exchange acceleration.
2005—Development of the first Network Processor (NP1) ASIC. Originally named the FortiAccelerator (FA2 ASIC), was developed as an interface based processor to provide firewall acceleration and additional IPSec VPN offloading capabilities.
2008—Security Processor (SP) ASIC came about providing additional accelerations for IPS, IPv6, and Multicast.
2009—System on a Chip (SOC) ASIC was an industry first of combining a CPU and two different ASIC technology (CP & NP) into a single chip. This type of ASIC are primarily marketed in the low end units to reduce footprint of the circuit board design thus providing high performance firewall and VPN accelerations in a smaller package.
Features of the Last Four Generations of Content Processor (CP) ASIC Functionalities
CP4 ASIC
• DES/3DES/AES in accordance with FIPS46-3/FIPS81/FIPS197.
• SHA-1 and MD5 HMAC with RFC1321 and FIPS180 compliance.
• HMAC in accordance with RFC2104/2403/2404 and FIPS198 compliance.
CP5 ASIC
Provides the following addition to the previous version:
• High performance IPSEC Engine improvements.
• Random Number generator with ANSI X9.31compliance.
• Public Key Crypto Engine supports high performance IKE and RSA computation used in IPSec and SSL accelerations.
CP6 ASIC
Provides the following addition to the previous version:
• Dual CPRL Content Processors.
• SSL/TLS protocol processor for SSL content scanning and SSL acceleration.
CP8 ASIC
Provides the following addition to the previous version:
• Over 10 Gigabits throughput IPS Content Processor for packet content matching with signatures.
• ARC4 in compliance with RC4.
• Public key exponentiation engine with hardware CRT support.
• Primarily checking for RSA key generation.
• Handshake accelerator with automatic key material generation.
• Sub public key engine (PKCE) to support up to 4094 bit operation directly.
• Message authentication module offers high performance cryptographic engine for calculating SHA256/SHA1/MD5 of data up to 4G bytes.
Tip
CLI command to determine which CP version
The command use to determine whether a CP ASIC exist or what version of the CP ASIC is ‘get hardware status’. Example output:
Features of the Network Processor (NP) ASIC Functionalities
NP1 ASIC
• 4 Gbps of IP packet forwarding throughput (bi-directional with 2 × 1 Gigabit interfaces).
• 1 Million+ sessions of searching and dynamic network address translation (DNAT).
• 350Mbps+ of IPSec ESP encryption/decryption processing (3DES+MD5 only).
• Support for session timeout.
• IP/TCP/UDP checksum calculation offloading.
• Up to 512 Virtual Domain support.
NP2 ASIC
Provides the following addition to the previous version:
• 8 Gbps of IP packet forwarding throughput (bi-directional with 4 × 1 Gigabit interfaces or 11 Gbps with 10 Gigabit interface).
• 1 Gbps+ of IPSec ESP encryption/decryption processing (DES, 3DES, AES-128, AES-192, AES-256) and AH (MD5, SHA-1).
• Enhanced Extension Interface (EEI) support between NP2 providing 8× Gigabit interfaces to scale up to 16Gbps IP packet forwarding throughput.
• Jumbo frames support up to 9000 bytes.
• Packet fragmentation & de-fragmentation.
NP4 ASIC
Provides the following addition to the previous version:
• 40 Gbps of IP packet forwarding throughput (bi-directional with 2 × 10 Gigabit interfaces).
• 10 Million+ sessions of searching and dynamic network address translation (DNAT).
• 12 Gbps+ of IPSec ESP encryption/decryption processing (DES, 3DES, AES-128, AES-192, AES-256) and AH (MD5, SHA-1).
• Seamlessly scalable system with switch chips to support any throughput.
• Policy-based & Per-IP Traffic shaping and counter per session/per VLAN.
Tip
CLI command to determine which NP version
There no direct way to determine whether a NP ASIC exists or what version of the NP ASIC is but there is a CLI command that can be used in a trial and error fashion to confirm these two questions. This command would be the ‘get hardware npu <npu version> list’. Where <npu version> could be np1, np2, or np4—if either entry takes then this provide the answer otherwise there’s no NP ASIC in the product.
# get hardware npu np2 list

Note: Command only works on FortiGate appliances and system models with built-in ASIC chipset therefore FortiGate VM versions would not have this CLI option.
FortiGate Hardware Accelerations Behaviors
In this section we’ll highlight some of the intricacy involved when using the Fortinet ASICs. The following outline is based on the more recent ASIC versions. There are three security acceleration technologies with FortiGate platforms supporting these types of ASIC we will dig into.
Firewall Acceleration using NP ASIC
“Fast path” is a term use to indicate a session or a flow is being processed by the ASIC. The alternative is “slow path” which is traffic handled by the main process unit processor (CPU).
Fast path session offloading requirements:
• NP based ASIC provides firewall accelerations at wire speed for all packet sizes. With a single NP4 ASIC, it can scale up to 40 Gbps (bi-directional) stateful firewall offloading.
• There are a limited number of interfaces on each FortiGate model that are tied to certain NP ASIC versions. Given the NP ASIC is designed to sit in-line with the flow of communication (as noted in Figure 2.3—High-Level Content Processor (CP) ASIC and Network Processor (NP) ASIC Architecture), the NP1 can support up to 2 × 1 Gbps interfaces and NP2 up to 4 × 1 Gbps. For optimal performance, ingress and egress interface should be terminated to the same ASIC. See Table 2.1 on NP Shared port mappings on various FortiGate models. There also existing FortiGate modules such as the double-width AMC module, ADM-XB2 with an NP2 ASIC that leverages dual 10 Gbps interfaces thus ingress and egress needs to reside within the module in order to achieve the NP2 maximum IP forwarding rate of up to 11 Gbps (bi-directional).
Table 2.1 FortiGate models and Modules with ASIC types & Interface Mappings

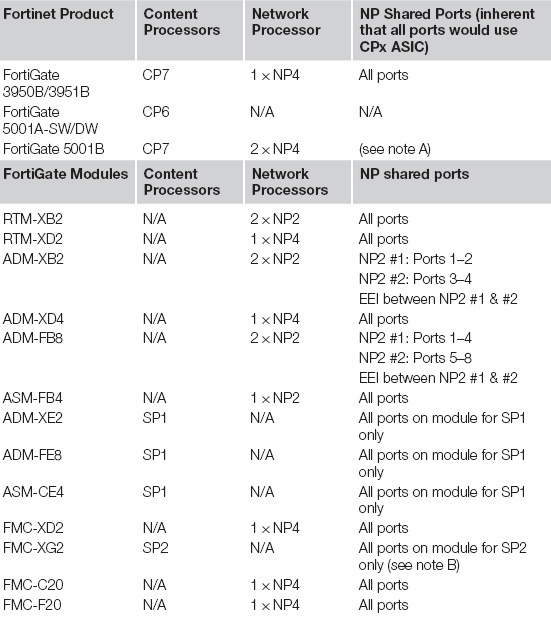
Note A: The NP4 processors on the FortiGate 5001B are linked internally using 2 × 10 Gbps Attachment Unit Interface (XAUI) links (XAUI-link1 and XAUI-link2). For optimal performance, ingress and egress traffic should traverse the same XAUI link and NP4 processors. The NP4 ASIC shared ports are:
• port1, port3, and fabric1 are connected to NP4-1 and XAUI-link-1.
• port2, port4, and base1 are connected to NP4-1 and XAUI-link-2.
• port5, port7, and farbic2 are connected to NP4-2 using XAUI-link-1.
• port6, port8, and base2 are connected to NP4-2 using XAUI-link-2.
Note B: FMC modules supports internal facing interfaces connected to FortiGate models with ISF (Integrated Switch Fabric) supporting these modules such as the FortiGate 3950B. With the ISF, all on-system-based ports (excluding management ports) on these FortiGate models (e.g. on 3950B port1-6) could leverage the SP2 ASIC for its related acceleration functions.
• The NP2 ASIC provides an EEI (Enhanced Extension Interface) to connect two NP2 communication paths together. This pair of NP2 ASIC can be found in limited FortiGate models therefore the ingress and egress interface pairs can be spanned out between the two NP2 supported in-line interfaces. See Figure 2.4 on various FortiGate models with EEI.
![]()
Figure 2.4 Fortinet’s First Appliance, The APSecure 300 Model
• The NP4 ASIC eliminates the EEI requirement to span multiple supported interfaces. Enhancements to the circuit board design combine multiple interfaces for leveraging the NP4 ASIC offloading capabilities.
• In order to be processed as fast-path using the NP2 or NP4, the traffic flow must have the following characteristics:
• Ingress and egress interface must traverse through same NP ASIC.
• Layer 2 Ethernet frame type & length of 0x0800 (IPv4), 0x8100 (IEEE 802.1Q), 0x8809 (IEEE 802.3ad LACP).
• When using link aggregation (IEEE 802.3ad LACP), the links needs to be defined within the same NP ASIC port mapping.
• Layer 3 protocol must be IPv4.
• Layer 4 protocols must be TCP, UDP, or ICMP.
• Traffic originating from FortiGate itself does not qualify.
• Qualified Layer 3 or 4 traffic must not require session-helpers usage.
• Firewall policy must not have application layer inspection features enabled such as Anti-virus, Web filtering, Anti-spam, Application controls, DLP, or IDS/IPS.
• Per policy Traffic shaping profiles are supported whereas Per-ip traffic shaping profiles are only supported on NP4.
• Port-based traffic bandwidth definition such as the interface CLI-based command for inbandwidth and outbandwidth are not supported on NP2. NP4 only supports outbandwidth setting.
Tip
High Availability (HA) offloading capabilities
In a configured Active/Active High Availability FortiGate cluster using FGCP (FortiGate Clustering Protocol), TCP base traffic are load balanced to other Active FortiGate cluster members by a designated FortiGate device within the cluster. Once the load-balanced traffic qualifies for the NP ASIC traffic characteristics, all subsequent traffic designated to be load balanced to corresponding cluster member devices continues to use the fast path. NP ASIC fast path session are not synchronized through heartbeat interface in a HA cluster thereby providing additional offloading capabilities without adding any addition burden on FortiGate main processor.
Fast Path subsequent packet requirements:
In order to maintain the existing session to be processed by the NP ASIC, the following traffic characteristics must continue to be met otherwise traffic would be processed via slow path with FortiGate main processor (CPU).
• Subsequent inbound packets into NP must not be fragmented.
• Subsequent outbound packets from the NP must not require fragmentation to a size less than 385 bytes. Thus, the MTU (Maximum Transmission Unit) for the NP interfaces should also meet or exceed 385 bytes setting.
Tip
Disabling NP ASIC offloading
For testing or troubleshooting purposes, the offloading of traffic to the NP ASIC can be disabled per ASIC with the following command:
The <npu version> could be substituted for ‘np1’, ‘np2’, or ‘np4’ whereas <NPx ID> is the NP ASIC id—if you substitute the <NPx ID> with a ‘?’ it would provide the NP ASIC ID list then re-issue the command and replace <NPx ID> with the corresponding ID, e.g. if the FortiGate model has 2 × NP2 ASIC then the ID starts out with ‘0’ for the first NP2 and ‘1’ for the other NP2.
This command is a temporary global command. When system is rebooted it would default back to ‘fastpath enable’. To confirm whether fastpath is disabled or enabled, use command of:
Look for the above example of ‘NAT Performance:’—if BYPASS shows ‘disable’ that means fastpath is disable—otherwise if it shows ‘BYPASS (Enable)’ then fastpath is enabled.
Note: Command only works on FortiGate appliances and system models with built-in ASIC chipset therefore FortiGate VM versions would not have this CLI option.
VPN Acceleration using NP and CP ASIC
The FortiGate main processor, along with the CP ASIC, assists with IPSec tunnel IKE setup. Once the tunnel is established, IPSec ESP payload packets are offloaded to NP ASIC. To meet the fast path requirements of NP ASIC, the following configuration and traffic characteristics are required:
• IPSec tunnel has to be configured as a tunnel interface and not as the default policy-base IPSec setup.
• In IPSec phase1-interface setting, the Local Gateway IP must be defined as the IP address of the local terminating interface. For example, if the IPSec tunnel is being terminated on port1, it’s the port1 IP address that needs to be defined.
• In IPSec phase2-interface settings, the configuration should consist of:
• Encryption algorithm must be DES, 3DES, AES (128 | 192 | 256 bit), or null
• Authentication algorithm must be MD5, SHA1, or null
• If encryption is null then authentication must be null
• If Anti-Replay detection is enabled then the following settings must be defined within CLI to enable Anti-replay offloading onto NP:
set dec-offload-antireplay enable
set enc-offload-antireplay enable
Note: Command only works on FortiGate appliances and system models with built-in ASIC chipset therefore FortiGate VM versions would not have this CLI option
• Packets originating from FortiGate itself (local host address within FortiGate) can be offloaded by enabling the following CLI command:
• Authentication algorithm such as MD5 and SHA1 used for HMAC checking is by default enabled to offload to NP but can be disabled with following CLI command:
UTM Acceleration using CP and SP ASIC
• Inherently, all traffic processed by the FortiGate main processors works in conjunction with CPx ASIC for additional offloading capabilities. This functionality are dependent on the version of CP ASIC capabilities as outlined in the above section titled ‘Features of the last four generations of Content Processor (CP) ASIC functionalities’.
• SP ASIC provides acceleration of traffic with characteristics related to the features it supports such as Multicast traffic, Intrusion Protection, Application Controls, flow-base Anti-virus/spyware flow-base Web Filtering, flow-base DLP, and IPv6. The following traffic characteristics are required for this acceleration:
• Ingress and egress Ethernet connectivity has to reside within the same SP ASIC interface port mappings (see Table 2.1 on modules and FortiGate models with this ASIC).
• For Multicast acceleration, multicast firewall policies must be defined on the interface port mappings support by the SP ASIC.
• For IPv6 acceleration, IPv6 firewall policies are required to be defined on the interface port mappings supported by the SP ASIC.
• For Intrusion Protection, Application Controls, flow-base Anti-virus/spyware flow-base Web Filtering, and flow-base DLP: IPv4 firewall policies with related UTM profiles and sensor for these application layer inspection are required to be defined on the interface port mappings supported by the SP ASIC.
The ‘Black Art’ of FortiGate Sizing
FortiGate sizing has always been considered as a black art we will try to tackle this subject in this section. Sizing any network product depends on various network elements with the environment’s current and potential growth requirements. First and foremost, knowing the need for the product will help identify the elements surrounding the integration of the product in your environment. This includes such things as placement of the solution in your architecture and performance requirements. If there’s an expectation to have the solution in place long enough to create a return on investment then the solution needs to be sized not just for today’s environment but also for growth over × number of months or years. When sizing a UTM solution, the elements involved in determining the proper solution is far greater to that of a typical network device such as a router or a switch. Given that a UTM solution can potentially replace multiple security stand-alone point products, each of these security product functions needs to be considered into the sizing of the proposed UTM solution. As with any investment, it’s imperative a sizing exercise be done prior to any purchase. Besides figuring out which device best fits your current and future network environment, further diligence is needed to verify that the proposed solution does fit and work in your environment. You may wish to acquire the actual proposed UTM solution for a hands-on evaluation. At the end of the day, you do not want an incorrectly sized complex security & networking device in your environment that could potentially cause issues and cost more money to correct the problem.
To help determine which FortiGate UTM solution best fits your environment, there are two steps:
Step 1: Sizing Data Gathering — Gather as much information as possible to help with sizing the appropriate solution
Step 2: Assessing The FortiGate Solution—Taking that gathered data from Step 1 and apply the responses to several areas of information to identify the appropriate FortiGate model.
Sizing Data Gathering
Let’s go over questions that should be answered to size a FortiGate UTM solution. The questions are separated in two general parts, Security Requirements and Network Requirements:
(1) Security Sizing Requirements Questions:
The purpose of these security related sizing questions is to determine the actual needs of the UTM solution. Each FortiGate UTM solution has fixed limit of resources allocated to certain functionalities. We’ll outline some of these fixed resources to consider for each service with the below questions.
a. What are the security feature requirements today?
b. What are the security feature requirements that could be needed over the time for the purchase will be amortized and should this be considered in sizing the solution? Given the benefits of a UTM handling multiple features at an overall lower TCO (Total Cost Ownership) there could be the possibility of replacing an existing stand-alone point security solution when the service contracts expires e.g. an existing firewall, web filtering, intrusion protection system, etc.
c. How many network users or devices expected to traverse through UTM solution?
Terminology
In-line vs. Sniffer mode
In-line mode: Traffic flows through solution for inspection.
Sniffer mode: Monitoring only mode on a switch port configured for Port Mirroring.
Here’s a high-level checklist of security features currently offered on FortiGate UTM solutions along with related resources that could affect sizing:
• Number of expected firewall policies and objects
• Concurrent connections (or sessions) support
• New session setup per second handling
• The type of VPN protocol used e.g. IPSec vs. SSL
• If IPSec: encryption requirements, number of site to site (device to device VPN), # software remote VPN clients, or both
• If SSL: encryption requirements, # of web-mode termination, # of tunnel-mode termination
- In-line: Flow-based method (faster performance) vs. proxy-based method (more secure). If proxy-based method, number of connections (or sessions/users) expected to be scanned
- Sniffer mode for monitoring only
• Protocols needed for scanning
• Custom block/warning message usage
- In-line Transparent (transparent in a way there’s no modified needed on client end to support this) Flow-based method (faster performance) vs. proxy-based method (more secure). If proxy-based method, # of users expected
- Sniffer mode for monitoring only
- Explicit (want client to adjust web browser proxy settings to point to UTM) web proxy support. If so, number of explicit web proxy users
• Custom block/warning/disclaimer message usage
- In-line with prevention capabilities
- Sniffer mode for monitoring only
• Intrusion Detection or Prevention
- In-line with prevention capabilities
- Sniffer mode for monitoring only
• Custom block/warning message usage
- In-line Transparent (transparent in a way there’s no modified needed on client end to support this) Flow-based method (faster performance) vs. proxy-based method (more secure). If proxy-based method, # of users expected
- Sniffer mode for monitoring only
• Wan optimization expected protocol usage
• Expected number of hosts/subnets used
• Historical logging & reporting
• Number of UTM devices to support logging
(2) Network Sizing Requirements Questions:
a. Where’s the UTM expected to be placed within your network architecture? Possible locations include the network perimeter, the access layer, distribution, or core of your network.
b. What are the expected overall network performance requirements for the related security requirements for the placement of the solution?
c. What is the current network performance where the UTM solution will be placed? Some of this data can be gathered from existing security or network solutions. The more complete answer on these questions the more accurate sized UTM solution could be proposed. Such as:
• What is the current peak and/or average network throughput in bits or bytes per second?
• What is the current peak and/or average new connections per second?
• What is the current peak and/or average network volume?
• What is the network packet size distribution?
d. Will the UTM solution operate in-line, off-line, or a mixture of both in-line and off-line? If in-line, what’s the planned operational mode such as Transparent (layer 2) mode, NAT/Route (layer 3) mode, or both?
e. How many physical (including any redundant interface or 802.3ad LACP connectivity needs) and expected logical interfaces (802.1q VLANs)?
f. What are the required physical interface requirements? e.g. Fast Ethernet, 1G fiber or copper, 10G.
g. If there are multiple network physical or logical interfaces, what are the expected performance requirements for communications between these in either in-line or off-line?
h. Is there a need for path or device redundancy? e.g. redundant interface support and High Availability clustering.
i. Is there a need for jumbo frame?
j. Is there a need to virtualize the UTM components into their own isolated UTM function via virtual domain (VDOM) (see Chapter 4 on VDOM description)? If so, which ones are likely to be used now and in the future?
k. Are there any power supply requirements such as AC vs. DC? Is redundant power needed (depending on whether device redundancy is required redundant power may not be a critical requirement).
Assessing the Recommended FortiGate Solution
With the majority of the previous questions answered, the next step is to assess which FortiGate platform best meets the above requirements. To provide a more accurate decision on the platform of choice, we will need to analyze three areas:
I. Feature Capabilities—To determine which platform would meet the requirements features
II. Feature Capacity—To determine which platform would handle the requirement features based on current and future growth feature requirements
III. Performance Capabilities—To determine which platform would meet current throughput & load requirements as well as expected future growth
Feature Capabilities
From a supported feature capabilities standpoint, the majority of the features are supported across all FortiGate platforms but there are a handful of features that are not. The information is maintained in the FortiOS documentations found at http://docs.fortinet.com/fgt.html.
Here’s a quick reference of supported features that are limited to certain FortiGate models:
• VDOM (virtual domains) are supported FortiGate 50B and higher models. By default it includes up to 10 VDOM license. FortiGate 1240B and higher has the ability to scale above 10 VDOMs (see those datasheets for maximum VDOM capacity).
• WAN optimization and Web caching are supported only on FortiGate models with on-board storage (4G or higher) or with solid state hard drives options. WAN optimization requires both ends of a connection to be FortiNet technology. For example FortiGate to FortiGate or FortiClient to FortiGate.
• 802.3ad link aggregations are supported on FortiGate 200B and higher models.
• High Availability is supported on FortiGate 40C and higher models.
• Localized SQL logging is supported on FortiGate models with solid state drives.
• SSL inspection and SSL offloading are supported on FortiGate models with SoC or CP6 & higher ASIC. Certain models maybe software restricted from leveraging this feature even though the hardware model supports this chipset. For example, FortiGate 20C has a SoC but function is disabled.
Feature Capacity
To find the feature capacity of each FortiGate platform, Fortinet provides publicly a Maximum Value Guide of all FortiGate platforms which can be found at: http://docs.fortinet.com/fgt/handbook/40mr3/fortigate-max-values-40-mr3.pdf (as of this writing, FortiOS 4.0 MR3 was the most current version — in general the max value guide can be found in the related FortiOS version section under FortiGate products).
Review of this Maximum Value Guide will provide insight as to any feature settings that might affect current and future requirements.
Examples of such feature capacity limits include:
Some of the feature capacities can also be founded in the product datasheets.
The FortiGate datasheets and Maximum Value guide refer to System level vs. VDOM level capacity. Technically, all devices by default operate in a single VDOM instance even without VDOM enabled. So the capacity for VDOM denotes the capacity of the device. If VDOM is enabled then the combined capacity would equal the System level capacity. For example, a FortiGate 1240B can handle 10,000 gateway-to-gateway IPSec tunnels at the System level and 5000 at a VDOM level: If no VDOM configuration exists then the overall number of supported gateway-to-gateway tunnels would be 5000 (by default a device without VDOM enable is treated like a single VDOM instance). If two configured VDOMs exist then the number of gateway-to-gateway tunnels between the two VDOMs (max 5000 per VDOM) would be no more than 10,000 supported tunnels. Further, if there are three VDOMs, VDOM-A has 2000 tunnels configured, VDOM-B has 5000 tunnels configured then VDOM-C cannot have more than 3000 tunnels configured because it would reach the System level capacity of 10,000.
Performance Capabilities
The majority of FortiGate platform performance characteristics can be found on their main website. For a quick reference product matrix showing each FortiGate model specifications in a single area see: http://www.fortinet.com/doc/FortinetMatrix.pdf.
For a more in-depth specification, individual FortiGate datasheets are located at: http://www.fortinet.com/products/fortigate/.
Reviewing datasheets quickly helps to determine the potential FortiGate model ranges; in particular which FortiGate platform would meet the network throughput requirements:
• Feature performance capabilities such as Firewall, IPS, Anti-virus, and IPSec & SSL VPN throughput numbers.
Tip
Additional general performance numbers
All performance testing are done in house using testing tools such as BreakingPoints [4] to provide the results. Not all performance metrics are highlighted in datasheets but here are some general rules regarding this missing features:
-For supported security features configured or using flow-base inspection methods such as Anti-virus, Web Filtering, DLP, and Application control, the expected performance should be slightly higher then published IPS throughput numbers.
-Supported security features that are configured for proxy-based inspection such as Web Filtering, DLP expected performance should be slightly higher then the published Anti-virus throughput numbers.
Also note, when particular security features are enabled it is not assumed that all traffic would fall into that throughput range. It is only the policy definition with the related security feature setting which could be affected by the stated performance throughput. For example, on a FortiGate 1240B, the anti-virus (proxy-based) throughput is noted as 900Mbps. There exists a policy in which anti-virus is the only security inspection service enabled within a policy, traffic that triggers the supported anti-virus proxy-based ports would be limited to 900 Mbps whereas other traffic that does not trigger the proxy listening ports would not have this limit.
Narrowing down the FortiGate platform based on the above criteria would help provide the minimum platform model but in most cases this is not enough. As the traffic load increases, the traffic patterns would vary (e.g. various packet sizes, more internet usage during a certain time, large file transfers occurring at various time, etc.), having varying traffic loads and patterns does not provide a predictable way of determining what effects this has on various features therefore finding the proper FortiGate platform is difficult to predict. The goal of the sizing exercise is to find a solution that best fits in your environment at the cheapest possible cost. Anyone can oversize the solution as a precaution but from a cost perspective this is generally not advised. Further discussion throughout the chapters will provide additional insight to help narrow down the FortiGate platform of choice.
Given the innovative capabilities at Fortinet, features may change after the writing of this book. It’s always best to consult the latest published Fortinet documentations and, if possible, a certified Fortinet reseller or Fortinet sales engineer.
Centralized Management Platform Overview
Fortinet centralized management solutions include the FortiManager and FortiAnalyzer products. FortiManager provides the centralized management of multiple FortiGate devices in a single management view. The FortiAnalyzer provides a centralized view of real-time & historical logging along with reporting capabilities of logs collected from FortiGate devices and various Fortinet products. Fortinet’s approach in offering two separated components for centralized management provides a scalable and flexible option for consumers. For example, a customer may not want to centrally manage their solution but want the historical logging and reporting capabilities. Rather then paying extra for central management capabilities and/or having to work through the management interfaces to get to the historical logging & reports, the solutions may be purchased separately. In our opinion, having your management capabilities, especially with historical logging and reporting residing in the same solution, would not only burden the overall solution but also run the risk of running out of storage space on the local disk. Having the centralized management solution (both policy management and logging & reporting) separated provides the following benefits:
1. Improves scalability. Ability to move to higher disk capacity drives.
2. Provides flexibility. Can manage and log/report separately without having to depend on each operation.
3. Reduces performance burdens and increases reliability. Relieves additional system burden on overall UTM architecture. With central management is built into UTM/NGFW solutions, when unit goes offline i.e. power reasons, defective device, network outages then central management along with logging & reporting could be inaccessible or lost.
As of this writing, here are some key features available for each of the management platform:
FortiManager provides:
• Web GUI management for all features. In addition, a java client for policy management.
• Centralized security policy management of multiple FortiGate UTM solutions.
• Centralized security policy management of multiple FortiClient end point solutions.
• Administrative Domains (ADOM) providing a virtualized group of managed devices within a single separated management view. In addition, administrator can be restricted to their assigned ADOM for management.
• Customizable administrative web portal.
• Global object database support, providing use of common configuration across global policy and/or unique policy per managed UTM solutions.
• Manual & scheduled pushes of policies and firmware updates to UTM solutions.
• CLI and TCL scripting support with manual or scheduled push capabilities to managed UTM solutions.
• XML API support for third-party integration.
• Mini-FDN (FortiGuard Distributed Network) support to provide Anti-virus/Spyware and IDS/IPS signature updates. In addition, support for a localized Anti-Spam RBL and Web URL categorization database.
FortiAnalyzer provides:
• Centralized logging and reporting management for various Fortinet products.
• 300+ predefined reports along with report customization capabilities.
• SQL database support locally or externally. Integrated SQL query & schema tools for further customizable reporting.
• Administrative Domains (ADOM) providing a virtualize group of managed devices within a single separated management view. In addition, administrator can be restricted to their related ADOM for management.
• Centralized quarantine capabilities for FortiGate UTM solutions. Providing a centralized repository for infected and blocked files.
Fortinet Product Portfolio
Besides Fortinet’s offering of their FortiGate UTM solutions and their related central management capabilities, there are several other products Fortinet offers. We’ll highlight the purpose and key points on each of their product offerings.
High-level overview of Fortinet’s service and other non-UTM product offerings:
FortiGuard
FortiGuard is Fortinet’s threat research and response service for the FortiGate UTM platforms and for most of the other offerings. The services offered here are primarily subscription based, providing signature updates for anti-virus, intrusion prevention, and application controls. In addition, direct access to real-time anti-spam reputation databases and web filtering URL categorization databases for the FortiGate UTM solution. The FortiGuard service is maintained and updated by security researchers around the world. Upon discovery of new threats, research and development of the related service signatures are synchronized with over two dozen global data centers where updates are distributed hourly to hundreds of thousands Fortinet UTM devices. Besides actively tracking global threats, developing, and maintaining security services for their UTM offerings, Fortinet security researchers also actively find exploits. To see both current and historical discovered vulnerabilities, see the FortiGuard web site [3]. For further details on FortiGuard, please reference Chapter 6.
FortiCarrier
The FortiCarrier solution is an extension of the FortiGate solution. It leverages the same features as in the current FortiGate FortiOS but adds features used in service provider infrastructures such as GTP firewall, secure MMS (MulitMedia Messaging Services), and IMS SIP signaling firewall capabilities. As of FortiOS 4.0 MR3, all of the SIP related features in FortiCarrier was ported over leaving GTP and MMS features as the main differences for the FortiCarrier product line. The FortiCarrier platforms are limited to the FortiCarrier 3810A, 3950B, and the 5000 series system products with the FortiCarrier 5001A-DW and 5001B blades. For further details on the FortiCarrier products visit: http://www.fortinet.com/products/forticarrier/.
FortiBridge
FortiBridge is a stand alone product used in conjunction with the FortiGate UTM platforms to provide a bypass method when the UTM solution goes offline. The FortiBridge bypass capabilities provide a automatic bridging of traffic by routing traffic around an inline FortiGate UTM in an event of a power outage or a system fault. There are three version of this product:
FortiBridge-2002: Provides two segment bypass protection with 8 × 10/100/1000 copper interfaces.
FortiBridge-2002F: Provides two segment bypass protection with 4 × GbE SFP (fiber or copper) and 4 × GbE fiber interfaces.
FortiBridge-2002X: Provides two segment bypass protection with 4 × 10 GbE SFP+ and 4 × 10 GbE LC Fiber interfaces.
Given this is an external bypass solution; it only works with a FortiGate UTM solution deployed in a transparent (layer 2) mode. This could be a cheaper alternative network redundancy solution then purchasing another FortiGate device for a high availability configuration. The only downsides to this solution are the transparent mode requirement (typical with any bypass solution on the market) and when the FortiGate UTM solution goes offline then there are no security enforcement in place. Since the FortiGate is offline and the external bypass solution is in bypass mode therefore bypassing security inspections usually performed by the FortiGate solution. For further details on the FortiBridge products visit: http://www.fortinet.com/products/fortibridge/.
FortiAP
FortiAP is an 802.11x wireless access point (AP) offering. As of this writing there are three commercial grade FortiAP models offered by Fortinet, FortiAP-210B, FortiAP-220B, and FortiAP-222B. All three models support 802.11a/b/g/n standards and operate on both 2.4 GHz b/g/n and 5 GHz a/n spectrums. The 210B has single radio whereas the other two have two radios. The 222B can be used outdoors unlike the other two models which are indoor only. Each radio supports multiple wireless clients with ability to span across multiple wireless network segments each with its own SSID and with different access rights. Having multiple radios in a single FortiAP provides options for dedicating certain wireless frequency spectrums to specific uses. A radio could also be dedicated for wireless rogue AP (Access-Point) detection. Rogue detection provides another layer of defense by detecting unauthorized access points being used in your network environment. In addition, on-wire rogue AP detection is possible by leveraging the dedicated wireless radio detected rogue AP MAC address and correlating the FortiGate wireless controller MAC entries from potential wireless user client using the rogue AP on the network. If a rogue AP is detected on your physically connected network (on-wire), the FortiGate has the ability to suppress and block network activities coming from the discovered rogue AP. These APs are used in conjunction with the FortiGate UTM solution acting as a wireless controller for the AP and providing fast roaming capabilities between FortiAPs. The wireless controller function is included in almost all FortiGate models (check datasheet to confirm support). With the FortiGate providing the wireless controller functionality, it adds additional benefit for a secure wireless infrastructure by leveraging all the FortiGate offered UTM features. For further details on the FortiGate built-in wireless controller feature will be covered in Chapter 7 of this book.
FortiToken
FortiToken provides a two-factor authentication solution for use with the FortiGate platforms administrative access, IPSec VPN, SSL VPN, and Identity Policy Authentications. It provides another layer of security with a one-time password (OTP) capability used in conjunction with an existing single-factor authentication, such a static password. The seeding of the OTP is managed by our FortiGuard Center as a cloud-based repository. The FortiToken can also be used as a stand alone external authentication method used in conjunction with the FortiAuthenticator product (see description on this product below). Further details on this product will be covered in Chapter 5.
FortiAuthenticator
FortiAuthenticator is a user-based identity management solution, used for user authentication, two-factor authentication with FortiToken, and identity verification network access. The user authentication credentials use a build-in standardized RADIUS or LDAP server configuration. It may also be integrated with third-party authentication servers such as Microsoft Active Directory by using LDAP. For further details on the FortiAuthenticator product visit: http://www.fortinet.com/products/fortiauthenticator/.
FortiMail
FortiMail is a comprehensive messaging security solution. It provides Anti-Virus, Anti-Spam, Data Loss Prevention, and Identity-Based Encryption for email. The product can operate in Gateway (MTA), Transparent and also offer a full email server mode capability. As of this writing there are four appliance models (FortiMail 200D, 400C, 2000B, 3000C), a chassis blade (5002B) version, and a Virtual Machine (VM) version. For further details on the FortiMail product visit: http://www.fortinet.com/products/fortimail/
FortiWeb
FortiWeb is a WAF (Web Application Firewall) that is used to protect, load balance, and accelerate content to and from web server(s). As a WAF, it provides protection for web applications and related database content by mitigating common threats like cross-site scripting, buffer overflows, denial of service, SQL injection, and cookie poisoning. It addresses the OWASP Top 10 web application vulnerabilities. FortiWeb also provides server load balancing, content-based routing, data compression, and SSL encryption accelerations. The product is ICSA Labs certified and also provides a built-in vulnerability scanner module that helps with PCI DSS compliance requirement 6.6. As of this writing there are three appliance models (FortiWeb 400C, 1000C, 3000C) and also a Virtual Machine (VM) version. For further details on the FortiWeb product visit: http://www.fortinet.com/products/fortiweb/.
FortiScan
FortiScan is a vulnerability management solution which provides a central network-level and OS-level vulnerability scanning of devices throughout the network. In addition, it provides patch & remediation management, asset management, and compliance reporting capabilities that are compliant with regulatory and best practices for FDCC, NIST SCAP, SOX, GBLA, HIPAA, PCI/DSS, FSIMA, and ISO 17799. For further details on the FortiScan product visit: http://www.fortinet.com/products/fortiscan/.
FortiDB
FortiDB is a database security and compliance product which provides a central management view of policy compliance and vulnerability management for databases. It supports majority of the commercial databases such as Oracle, MS SQL Server, Sybase, and DB2. As of this writing the product comes in three models (FortiDB-400B, 1000C, and 2000B) and also in a Virtual Machine (VM) version. The main difference between the FortiDB models are the licensing structure each model supports which are based on number of database instances used for the product. For further details on the FortiDB product visit: http://www.fortinet.com/products/fortidb/.
FortiBalancer
FortiBalancer is an application delivery controller. It provides Layer 2 through Layer 7 load-balancing capabilities. In addition, it provides a built-in caching supporting HTTP 1.1, in-line HTTP compression, TCP connection multiplexing, TCP accelerations, IPv6 support, and SSL offloading/acceleration. The product can be deployed in proxy and transparent mode configuration. As of this writing there are three versions of the FortiBalancer (FortiBalancer-400, 1000, and 2000). For further details on the FortiBalancer products visit: http://www.fortinet.com/products/fortibalancer/.
FortiClient
FortiClient is a software-based endpoint security client providing various security features for enterprise and mobile devices. As of this writing there are four versions of the client offering various features for several different OS platform and mobile devices. The versions of FortiClient and supported features are:
FortiClient (standard)—Provides IPSec & SSL VPN, two-factor authentication support, Wan Optimization, and Application detection & enforcement along with Policy compliance enforcement when used with FortiGate UTM devices.
FortiClient Premium—Provides all of the above features and adds Anti-Virus, Anti-Spam, Application-based firewall, and Web Filtering.
FortiClient Lite—Is a free edition that only provides Anti-virus/spyware functionality.
All versions of the FortiClient are supported on most Windows versions in 32 bit or 64 bit. At this time, only the standard FortiClient is support on OSX.
Fortinet also offers a stand alone SSL VPN client for tunnel mode usage to a FortiGate solution. This stand alone SSL VPN client can be installed separately with no additional cost. Although, access to this client is available at Fortinet support website with a valid FortiCare support contract login. This endpoint SSL VPN client can support Linux and Mac OS besides Windows OS.
For further details on the FortiClient products visit: http://www.fortinet.com/products/endpoint/ or http://www.forticlient.com.
