These days, Network Access Controller (NAC) appliances are becoming more common on networks. NACs do give an increased level of security, but they are not the "end all" solution that their vendors' marketing and sales materials suggest that they are. We will show you a simple method of bypassing NAC controls on a company network.
The following information comes from a real hack to a real company we performed a while back. Of course, all the names and IP addresses have been changed to protect the company. This is not theory. This is a real world hack. The good thing for the company in this dramatization is that we are the good guys. The sad thing is that it only took about 30 minutes to figure this out, and maybe two hours to fully implement it.
We will be bypassing the NAC for the company widgetmakers.com. Widget Makers has two networks: one the corporate LAN (CorpNET), and the other a production network (ProdNET), containing classified data. The two networks are of a flat design, and both networks have full access to each other. A NAC appliance was configured and installed on the CorpNET. Employees must now use a NAC agent on their machines to connect to the CorpNET. Widget Makers uses SIP phones for voice communications. These phones are not on a separate VLAN. They are connected to the CorpNET VLAN for ease of use. Widget Makers also has a number of network printers on the CorpNET.
NAC appliances use an agent that is installed on the user's machine for login and verification of the user and machine's identity. These appliances can be configured to use a Remote Authentication Dial in User System (RADIUS) server or Domain Controller for the user credentials. Sometimes the NAC appliances use certificates to authenticate the machine. Trying to spoof an internal machine's MAC address without an agent and a login will normally result in the MAC address getting locked out of the network.
The weakness in the system is the agents. Most NAC systems are proprietary and tied to one vendor. One vendor's agent will not work with another, and there is not a standard for NAC controls. Most vendors only make agents that run on Windows; thus, if you have a Mac or Linux workstation on your network, it cannot be joined to the network using NAC controls.
So what do you do with the phones, printers, and workstations not running a Windows operating system to get them to work within the NAC controls? You have to whitelist their MAC and IP addresses within the NAC settings. Thus, by taking one of these devices off the network and spoofing its identity, you now have access to the restricted VLAN with the access level of the device you have spoofed. Normally, on a flat network, you have access to everything in all local networks.
One of the easiest marks for this hack is a SIP phone. People would definitely notice if a printer went offline. Everyone uses printers. To use a printer for this type of exploit, you must pick a printer that isn't used often. Phones are a different case. Offices always have extra phones for guests, and often, if you know the work schedule of the employees, you can pick a phone of someone who is on vacation. Unplug their phone and tape your Dropbox under the desk and connect it to the phone drop and you are in:
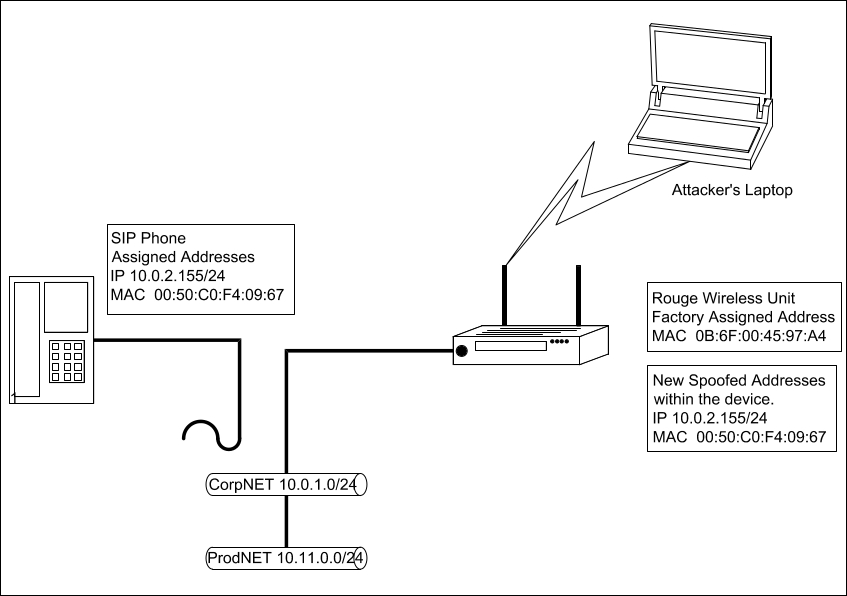
So how do you protect from this?
First thing, don't count on NAC being the ultimate security feature on your network. NAC should be only one layer of many in the security architecture of the network. Actually, it should be one of the upper layers of your network security. One simple workaround is to turn off (unplug) network ports that are not in use. This will not save you from a hacker subverting a deskphone of somebody who is on vacation, but it can keep an empty cube from becoming a hacker's headquarters.
The first layer of any network security should be proper segmentation. If you can't route to it, you can't get to it. Notice in the preceding diagram that CorpNET and ProdNET have full access to each other; an attacker coming in through CorpNET spoofing a network device can gain access to the restricted ProdNET.
