OK, let's fire up Metasploit. First, because Metasploit uses a client/server model, we need to turn on the Metasploit services. In Kali 1.x, you had to start the Metasploit server in the Menu Bar. Go to Applications | Kali Linux | System Services | Metasploit | community/pro start:

A terminal window will open and the services will start up. A marked improvement in Kali 2 means that all you have to do is click the Metasploit link on the left side-bar or in the main Applications menu.
Metasploit uses the PostgreSQL v9.1 database server. It can take several minutes for the services to start.

Once the services have started, type msfconsole to start the Metasploit console. When we type workspace, we can see the workspaces. We will set up a new workspace shortly.
When the console is ready, it will show you a little talking cow (# cowsay++) introducing you to Metasploit:

To get a list of the console commands, type help at any time.
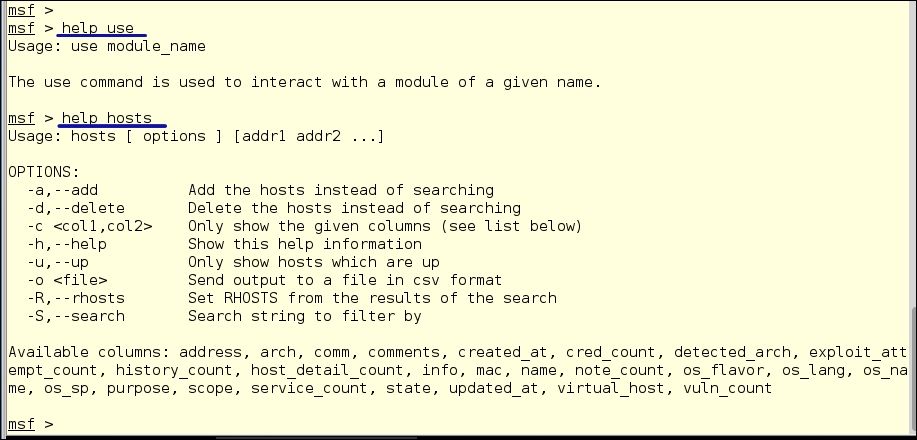
msf > help
To get help on individual commands, type help <command>; the screenshot below shows two examples showing the use and hosts command help. We have a listing showing its usage and explanation of any flags that work with the command.