OWASP ZAP is a GUI interface that tests the vulnerabilities of a website, and using the details ZAP produces, you can find possible attack vectors on your target machine or machines on the network. We are using one internal lab machine and two machines on the public internet to look for holes and vulnerabilities. The first time you start ZAP, you will see their Apache License, which you must accept. The license mentions that you must not use ZAP to scan a machine or site to which you do not have rights. It is not legal to scan sites you don't have rights to and we will not be amused if we find out you are scanning our test sites without permission. We might consider allowing you to scan the sites with permission, but you will have to ask first.

The next dialog is a question of whether you wish to use, or continue to use, ZAP with a session. Persist is an odd way to describe the very first time you use ZAP but that is what you are asked. We are going to name our session generic-corp=ws2K12-01 because it is a session of Windows web servers.

Hitting the Start button on the dialog opens a file-save dialog. We are going to create a folder called ZAP and put the file in that folder.

Finally, we see the main dialog with its several locations and tabs. We are going to start by typing a URL in the field called URL to attack:.

The IP
http://192.168.56.103 is our little Windows Server 2012 lab computer.
There is not a lot of data on the test box but whatever problems it has, we can see from the ZAP dialog. Note in the following image, ZAP is showing the active attack, which is testing for many vulnerabilities.

We could continue searching for issues here from the attack platform but there is another way to use ZAP.
ZAP works well as a standalone tool, but it is even better when used as a proxy. You can use Firefox, or in this case Iceweasel, as your attack control panel and run all the traffic through ZAP. Click the button to get the Firefox extension.

The button opens a local window in Firefox/Ice Weasel.

Click on the Click to setup! button. You will get the standard install success dialog from Ice Weasel.

Next, you will get a dialog asking if you want to enable the site as a Blug-n-Hack provider. You will have to accept that you are setting up a Man-in-the-Middle proxy, with which you can intercept and modify all traffic to your browser.

Now you are ready to use both Plug-n-Hack and ZAP using the ZAP extension.

The next two images are the help screens for Plug-n-Hack (PNH) and OWASP ZAP. We will use the ZAP commands for the remainder of this section.
The ZAP commands are pretty simple to use. We are going to run an HTTP session and spider a couple of sites. These are sites that belong to us, and we do not give you permission to attack/test our sites. Please test your own!

We will start by spidering the local lab Windows Server 2012 webserver. Spidering collects all of the data and page names available in the site under test. Currently, it seems to be having a little bit of trouble with its database connection.

Next, we will try to spider our site, http://30309.info. What is going on? The notification is showing us that we cannot use 3039.info. You have to be extremely careful not to scan sites you do not own or have the owner's permission to test. We knew ahead of time that there was nothing at 3039.info, but what if there was something there? You might get a visit from law enforcement officers or you might find your IP was being blocked ("black holed").

It is obvious on inspection that there is a typo in the URL, so the spidering fails. Let's try our site, http://syswow.com. We go to the site and then start the spider command.

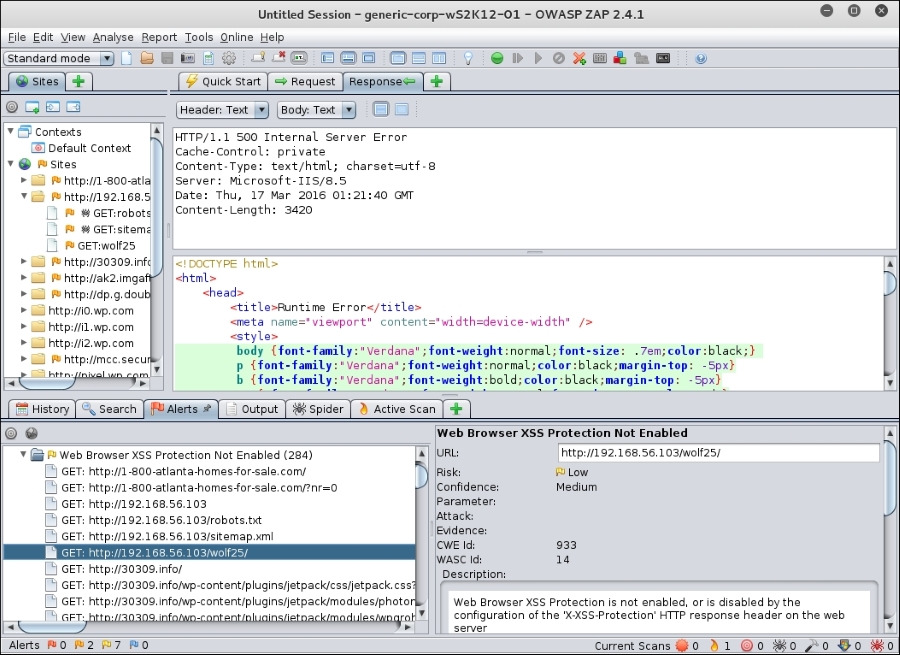
Looking back at the ZAP interface, it is plain that there has been a lot going on. All the sites we tested have produced a good deal of data. The first thing to look at is the cross-site scripting vulnerability (XSS). There are XSS vulnerabilities on all of these sites, and in most cases, there are dozens of vulnerable pages!
When you have finished the ZAP scan, you can produce reports as XML output or as HTTP output. Either output is very easy to customize with your company logos or extended text.

