Follow these instructions to get started:
- Let's first bring up our rogue access point using
airbase-ngand give it the ESSIDRogue: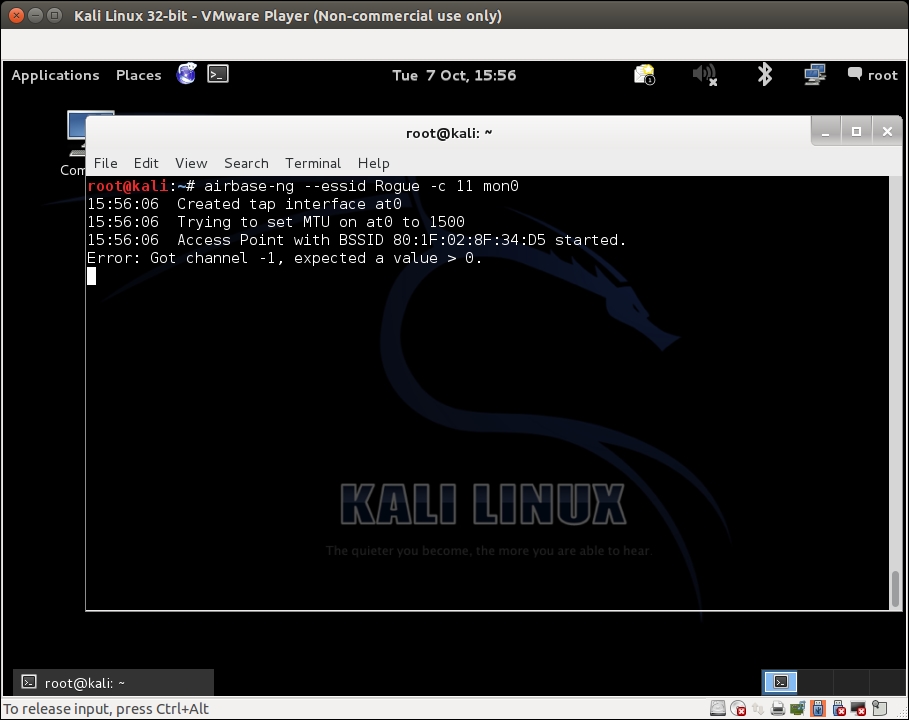
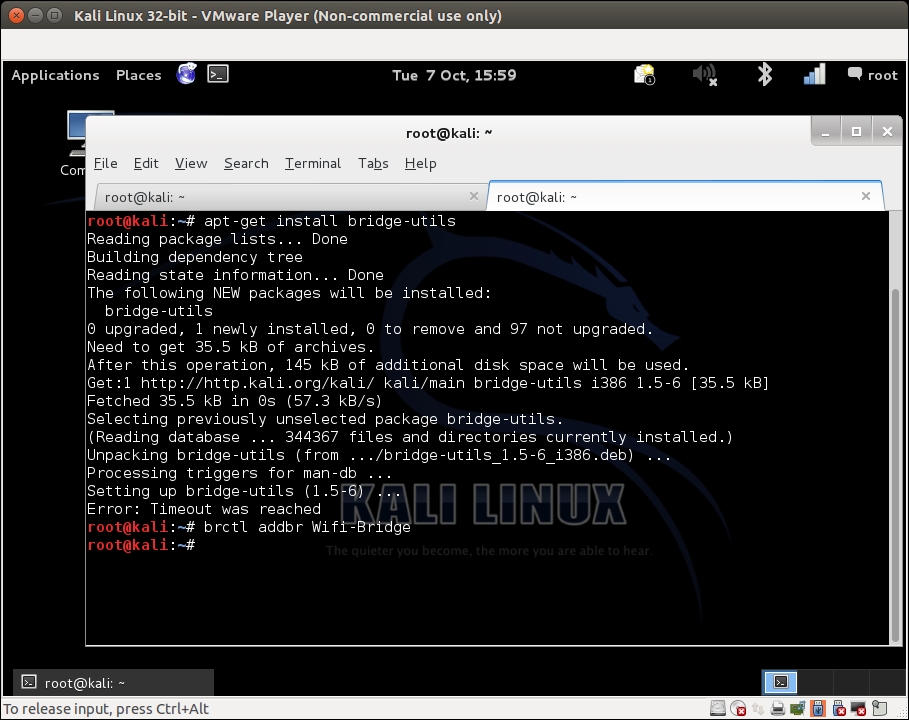
- We now want to create a bridge between the Ethernet interface, which is part of the authorized network, and our rogue access point interface. To do this, we will first install
bridge-utilsfiles, create a bridge interface, and name itWifi-Bridge. The following screenshot shows the required commands in action:apt-get install bridge-utils brctl addbr Wifi-Bridge
Let's see the following output of the command:
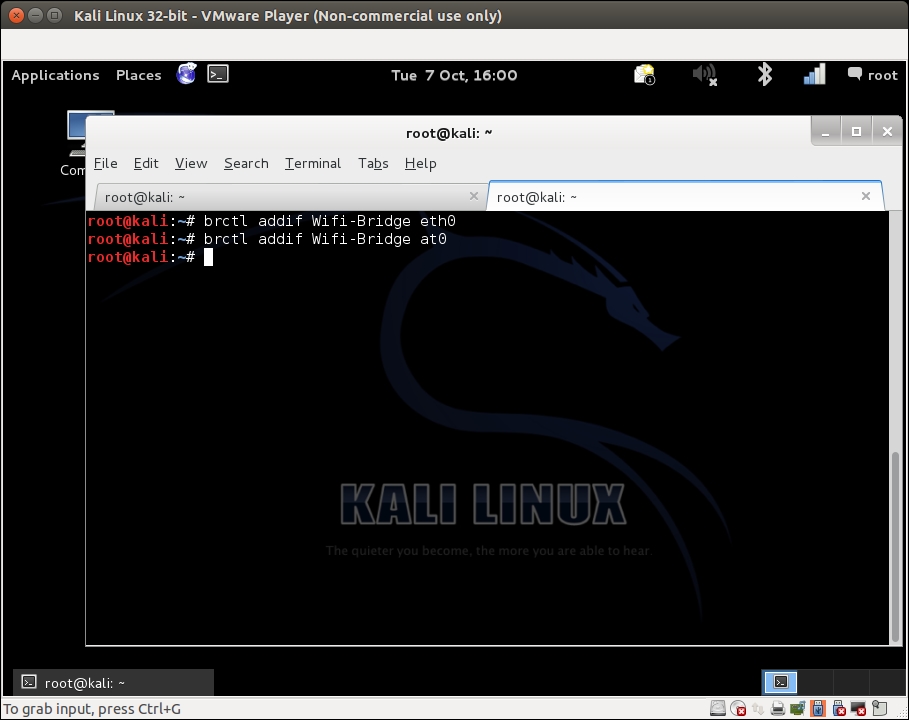
- We will then add both the Ethernet and the
At0virtual interface created by Airbase-ng to this bridge:brctl addif Wifi-Bridge eth0 brctl addif Wifi-Bridge ath0
The screenshot of the command as follows:
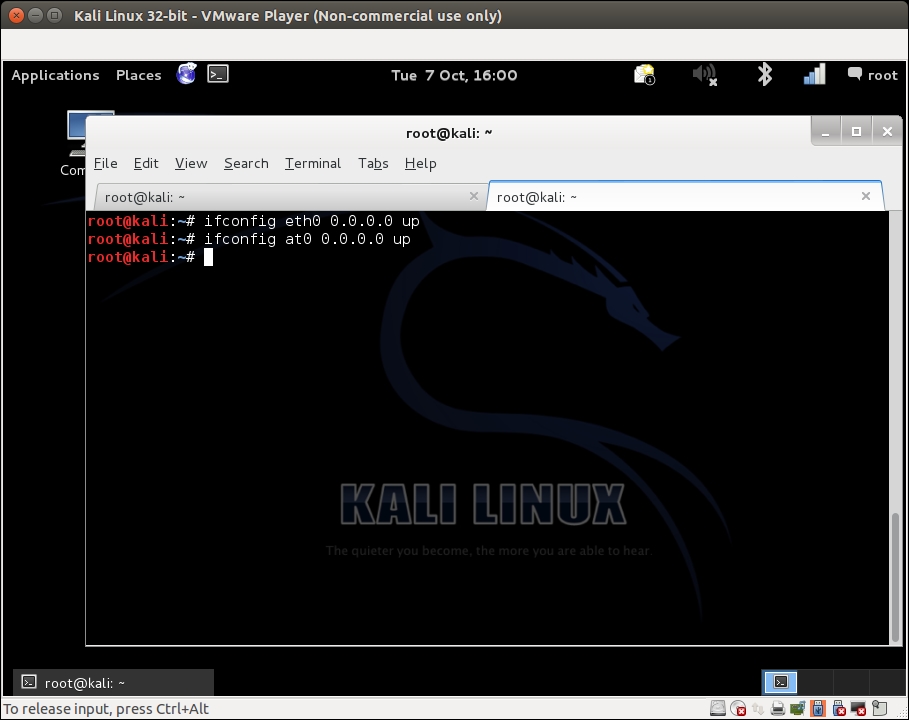
- We will then bring with these interfaces up to bring the bridge up with the following commands:
ifconfig eth0 0.0.0.0 up ifconfig ath0 0.0.0.0 up
The screenshot of the command as follows:
- We will then enable IP forwarding in the kernel to ensure that packets are forwarded:
echo 1 > /proc/sys/net/ipv4/ip_forwardThe screenshot of the command as follows:
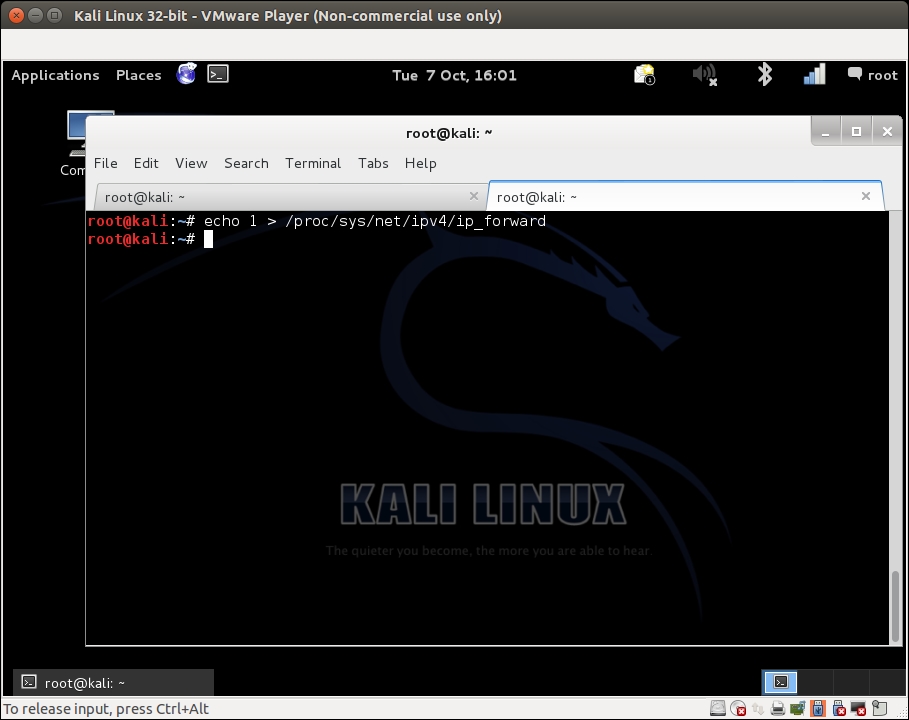
- Brilliant! We are done. Now, any wireless client connecting to our rogue access point will have full access to the authorized network using the wireless-to-wired
Wifi-Bridgewe just built. We can verify this by connecting a client to the rogue access point. Once connected, if you are using Vista, your screen might look like the following: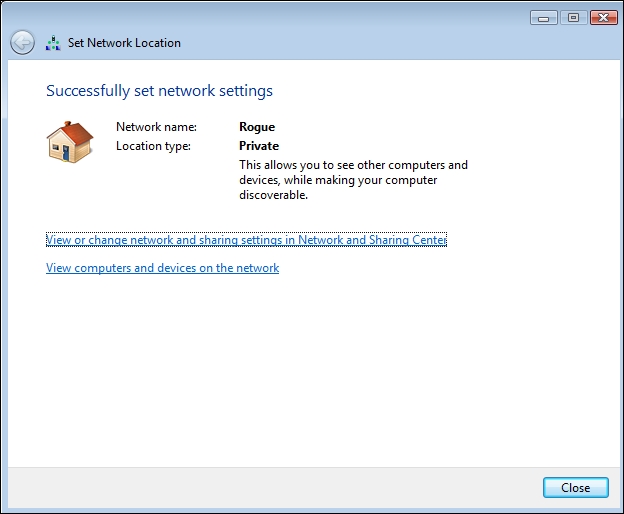
- Notice that it receives an IP address from the DHCP daemon running on the authorized LAN:
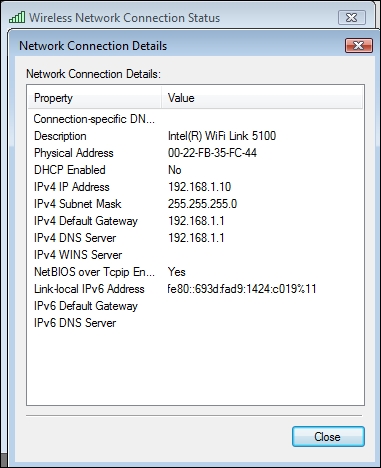
- We can now access any host on the wired network from this wireless client using this rogue access point. Next, we will ping the gateway on the wired network:
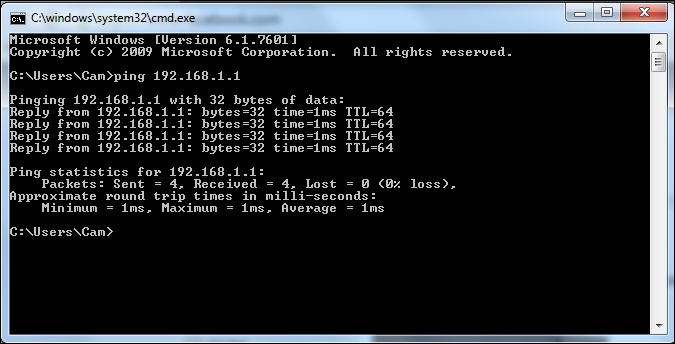
We created a rogue access point and used it to bridge all the authorized network LAN traffic over the wireless network. As you can see, this is a really serious security threat as anyone can break into the wired network using this bridge.
Check whether you can create a rogue access point that uses WPA/WPA2-based encryption to look more legitimate on the wireless network.
Q1. What encryption does a rogue access point use in most cases?
- None.
- WEP.
- WPA.
- WPA2.
Q2. What is the advantage of having the same MAC address as the authorized access point in an evil twin?
- It makes detecting the evil twin more difficult.
- It forces the client to connect to it.
- It increases the signal strength of the network.
- None of the above.
Q3. What do DoS attacks do?
- They bring down the overall throughput of the network.
- They do not target the clients.
- They can only be done if we know the network WEP/WPA/WPA2 credentials.
- All of the above.
Q4. What do rogue access points do and how can they be created?
- They allow backdoor entry into the authorized network.
- They use WPA2 encryption only.
- They can be created as software-based access points or can be actual devices.
- Both 1 and 3.
