Follow the given instructions to get started:
- Let's first connect to our access point Wireless Lab and go to the settings area that deals with wireless encryption mechanisms:
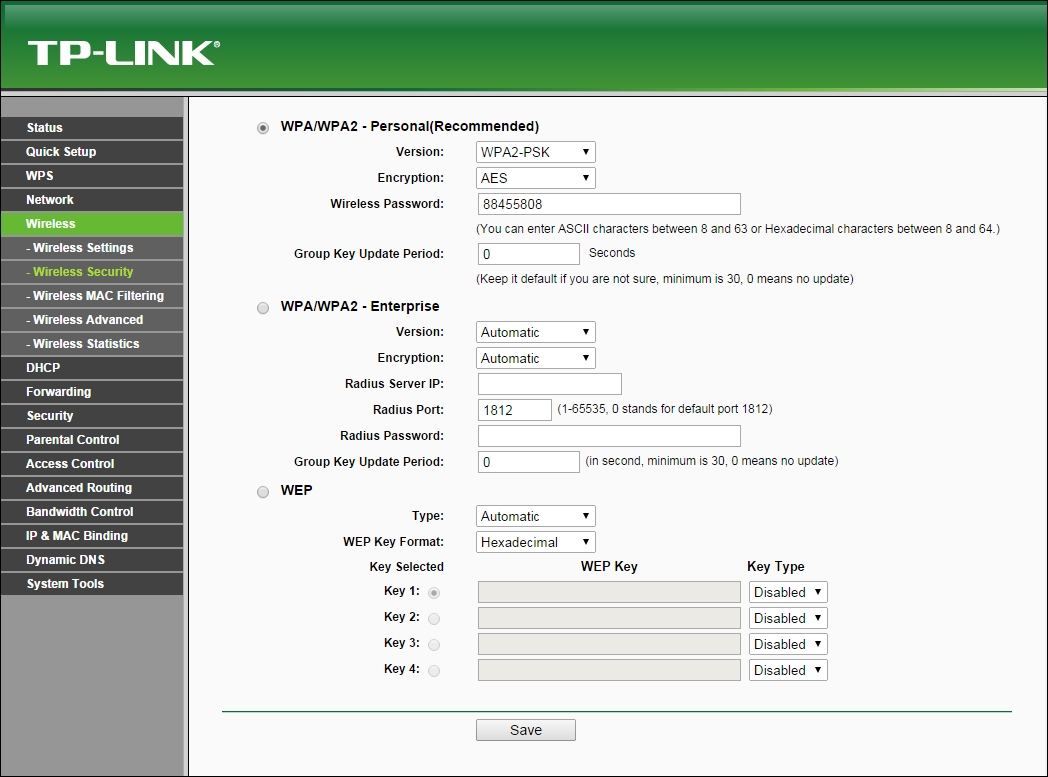
- On my access point, this can be done by setting the Security Mode to WEP. We will also need to set the WEP key length. As shown in the following screenshot, I have set WEP to use 128bit keys. I have set the default key to WEP Key 1 and the value in hex to
abcdefabcdefabcdefabcdef12as the 128-bit WEP key. You can set this to whatever you choose:
- Once the settings are applied, the access point should now be offering WEP as the encryption mechanism of choice. Let's now set up the attacker machine.
- Let's bring up
Wlan0by issuing the following command:ifconfig wlan0 up - Then, we will run the following command:
airmon-ng start wlan0 - This is done so as to create
mon0, the monitor mode interface, as shown in the following screenshot. Verify that themon0interface has been created using theiwconfigcommand: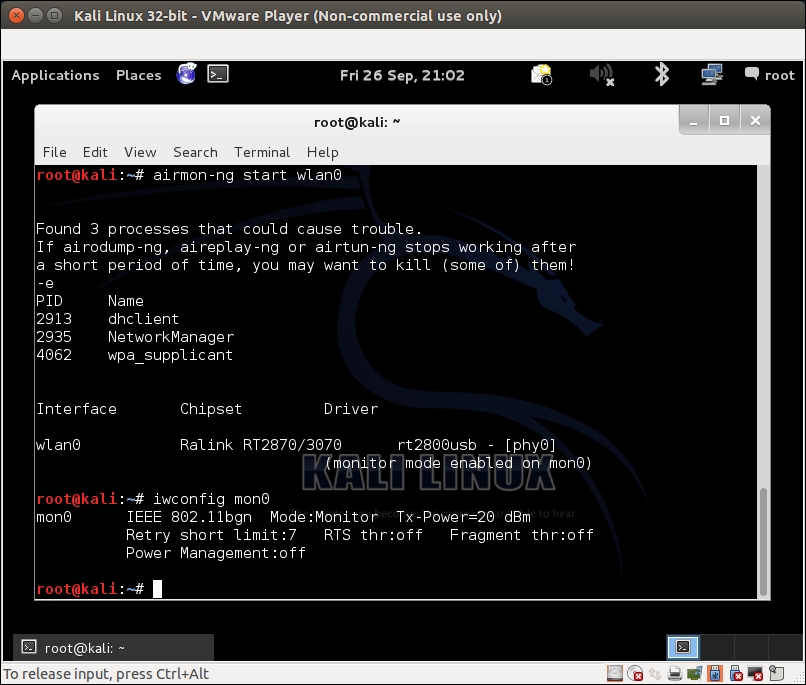
- Let's run
airodump-ngto locate our lab access point using the following command:airodump-ng mon0 - As you can see in the following screenshot, we are able to see the Wireless Lab access point running WEP:

- For this exercise, we are only interested in the Wireless Lab, so let's enter the following command to only see packets for this network:
airodump-ng –bssid 00:21:91:D2:8E:25 --channel 11 --write WEPCrackingDemo mon0The preceding command line is shown in the following screenshot:
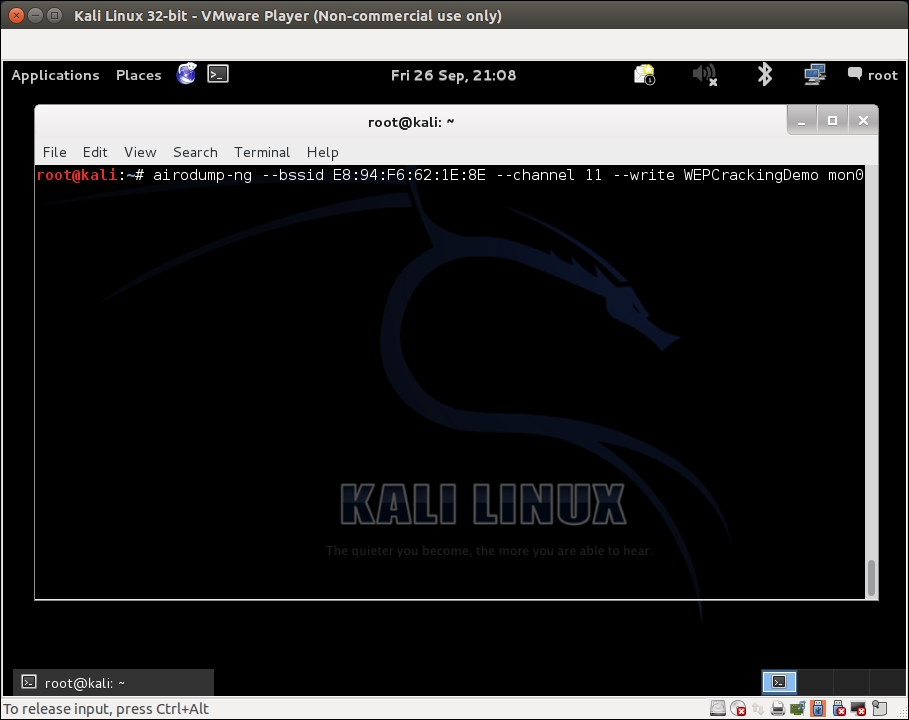
- We will request
airodump-ngto save the packets into apcapfile using the--writedirective: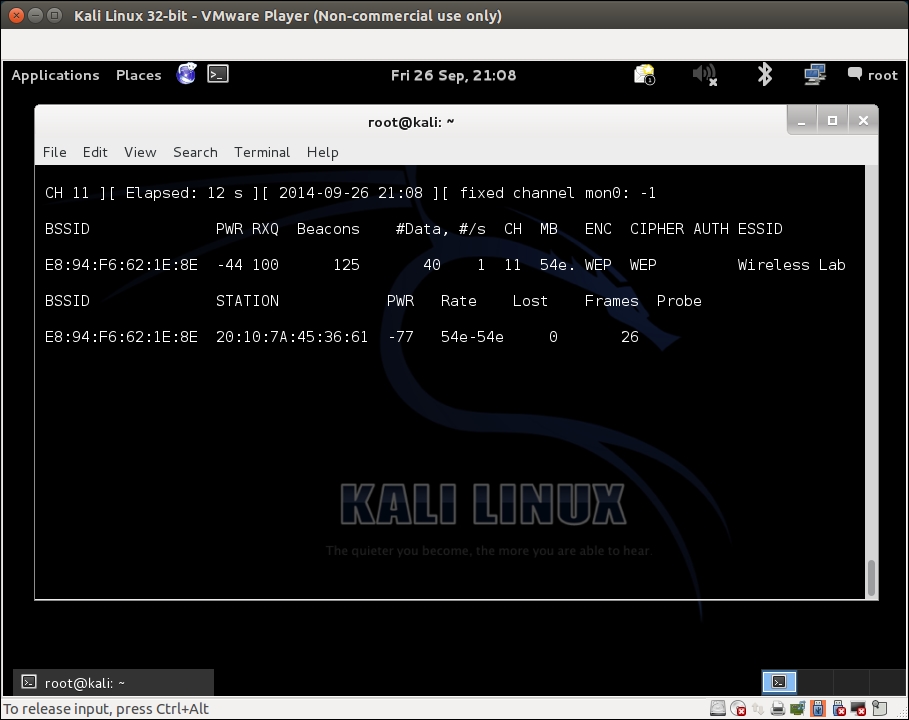
- Now let's connect our wireless client to the access point and use the WEP key as
abcdefabcdefabcdefabcdef12. Once the client has successfully connected,airodump-ngshould report it on the screen. - If you do an
lsin the same directory, you will be able to see files prefixed withWEPCrackingDemo-*, as shown in the following screenshot. These are traffic dump files created byairodump-ng: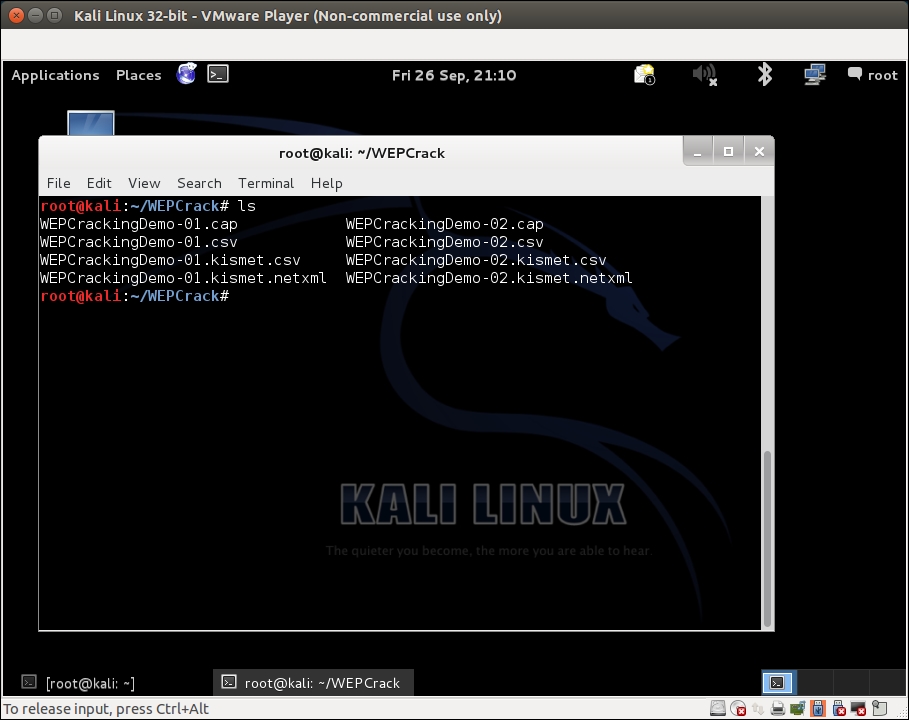
- If you notice the
airodump-ngscreen, the number of data packets listed under the#Datacolumn is very few in number (only 68). In WEP cracking, we need a large number of data packets, encrypted with the same key to exploit weaknesses in the protocol. So, we will have to force the network to produce more data packets. To do this, we will use theaireplay-ngtool: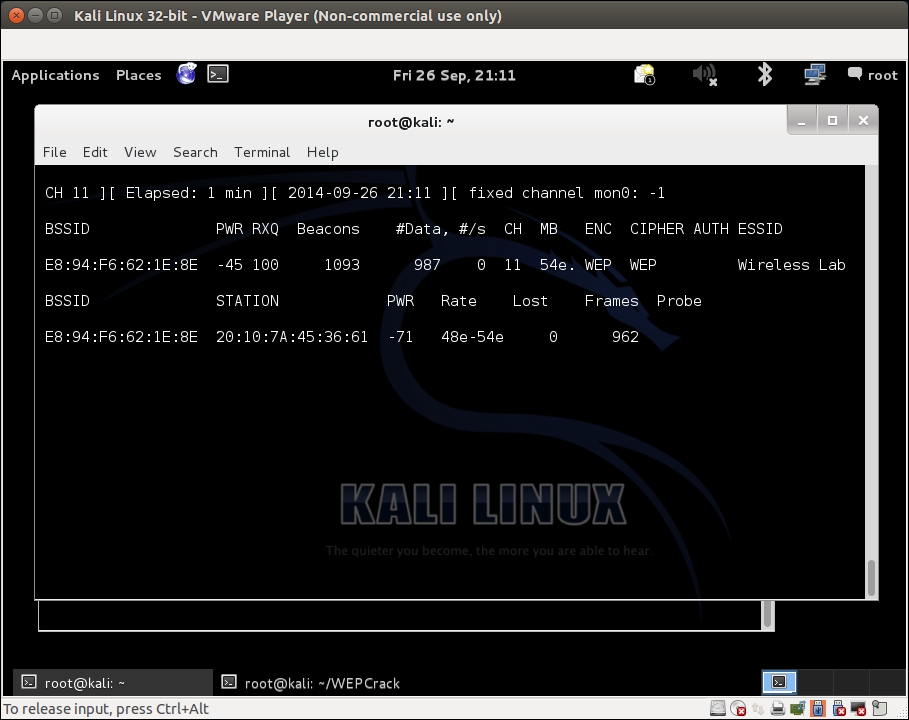
- We will capture ARP packets on the wireless network using
Aireplay-ngand inject them back into the network to simulate ARP responses. We will be starting Aireplay-ng in a separate window, as shown in the next screenshot. Replaying these packets a few thousand times, we will generate a lot of data traffic on the network. Even though Aireplay-ng does not know the WEP key, it is able to identify the ARP packets by looking at the size of the packets. ARP is a fixed header protocol; thus, the size of the ARP packets can be easily determined and can be used to identify them even within encrypted traffic. We will runaireplay-ngwith the options that are discussed next. The-3option is for ARP replay,-bspecifies the BSSID of our network, and-hspecifies the client MAC address that we are spoofing. We need to do this, as replay attacks will only work for authenticated and associated client MAC addresses:
- Very soon you should see that
aireplay-ngwas able to sniff ARP packets and started replaying them into the network. If you encounter channel-related errors as I did, append–ignore-negative-oneto your command, as shown in the following screenshot:
- At this point,
airodump-ngwill also start registering a lot of data packets. All these sniffed packets are being stored in theWEPCrackingDemo-*files that we saw previously:
- Now let's start with the actual cracking part! We fire up
aircrack-ngwith the optionWEPCRackingDemo-0*.capin a new window. This will start theaircrack-ngsoftware and it will begin working on cracking the WEP key using the data packets in the file. Note that it is a good idea to have Airodump-ng collect the WEP packets,aireplay-ngdo the replay attack, andaircrack-ngattempt to crack the WEP key based on the captured packets, all at the same time. In this experiment, all of them are open in separate windows. - Your screen should look like the following screenshot when
aircrack-ngis working on the packets to crack the WEP key:
- The number of data packets required to crack the key is nondeterministic, but generally in the order of a hundred thousand or more. On a fast network (or using
aireplay-ng), this should take 5-10 minutes at most. If the number of data packets currently in the file is not sufficient, thenaircrack-ngwill pause, as shown in the following screenshot, and wait for more packets to be captured; it will then restart the cracking process:
- Once enough data packets have been captured and processed,
aircrack-ngshould be able to break the key. Once it does, it proudly displays it in the terminal and exits, as shown in the following screenshot:
- It is important to note that WEP is totally flawed and any WEP key (no matter how complex) will be cracked by
Aircrack-ng. The only requirement is that a large enough number of data packets, encrypted with this key, are made available toaircrack-ng.
We set up WEP in our lab and successfully cracked the WEP key. In order to do this, we first waited for a legitimate client of the network to connect to the access point. After this, we used the aireplay-ng tool to replay ARP packets into the network. This caused the network to send ARP replay packets, thus greatly increasing the number of data packets sent over the air. We then used the aircrack-ng tool to crack the WEP key by analyzing cryptographic weaknesses in these data packets.
Note that we can also fake an authentication to the access point using the Shared Key Authentication bypass technique we learnt in the last chapter. This can come in handy if the legitimate client leaves the network. This will ensure that we can spoof an authentication and association and continue to send our replayed packets into the network.
In the previous exercise, if the legitimate client had suddenly logged off the network, we would not have been able to replay the packets as the access point will refuse to accept packets from un-associated clients.
Your challenge will be to fake an authentication and association using the Shared Key Authentication bypass we learnt in the last chapter, while WEP cracking is going on. Log off the legitimate client from the network and verify that you are still able to inject packets into the network and whether the access point accepts and responds to them.
