Follow these instructions to get started:
- Replicate the entire setup as in the previous lab. Fire up Wireshark. Interestingly, even the MITM-bridge shows up. This interface would allow us to peer into the bridge traffic, if we wanted to:
- Start sniffing on the
at0interface so that we can monitor all traffic sent and received by the wireless client:
- On the wireless client, open up any web page. In my case, the wireless access point is also connected to LAN and I will open it up by using the address
http://192.168.0.1:
- Sign in with your password and enter the management interface.
- In Wireshark, we should be seeing a lot of activity:
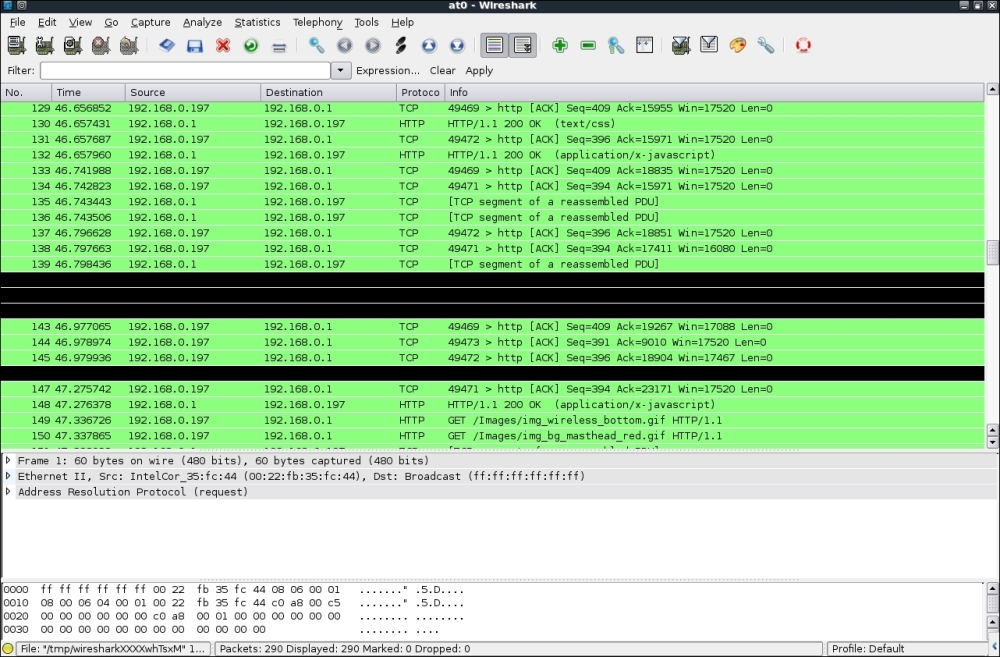
- Set a filter for http to see only the web traffic:

- We can easily locate the HTTP post request that was used to send the password to the wireless access point:

- Next is a magnified view of the preceding packet:
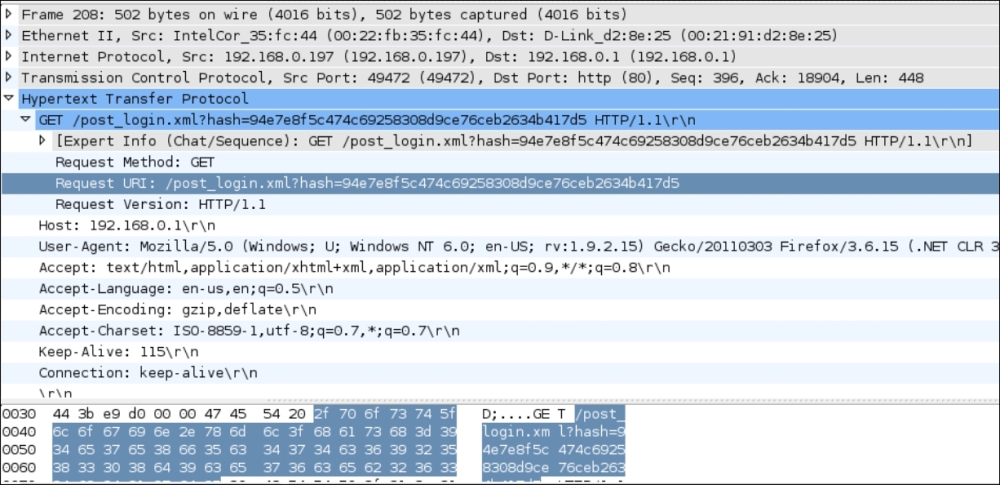
- Expanding on the HTTP header, allows us to see that actually the password we entered in plain text was not sent as is; instead, a hash has been sent. If we take a look at the packet, labeled as number 64 in a screenshot on the previous page, we can see that a request was made for
/md5.js, which makes us suspect that it is amd5 hashof the password. It is interesting to note here that this technique may be prone to a replay attack if a cryptographic salt is not used on a per session basis in the creation of the hash. We leave it as an exercise for the user to find out the details, as this is not part of wireless security and hence beyond the scope of this book: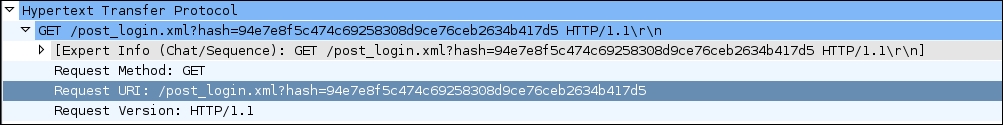
- This shows how easy it is to monitor and eavesdrop on traffic sent by the client during a man-in-the-middle attack.
The MITM setup we created now allows us to eavesdrop on the victim's wireless traffic without the victim knowing. This is possible because, in an MITM, all the traffic is relayed via the attacker's machine. Thus, all of the victim's unencrypted traffic is available for eavesdropping for the attacker.
In today's world, all of us would like to keep what we search for on Google private. The traffic on Google search is unfortunately over HTTP and plain text by default.
Can you think of an intelligent display filter you could use with Wireshark to view all Google searches made by the victim?
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
