We can proceed with the following steps:
- We will decrypt packets from the WEP capture file we created earlier:
WEPCrackingDemo-01.cap. For this, we will use another tool in the Aircrack-ng suite calledairdecap-ng. We will run the following command, as shown in the following screenshot, using the WEP key we cracked previously:airdecap-ng -w abcdefabcdefabcdefabcdef12 WEPCrackingDemo-02.cap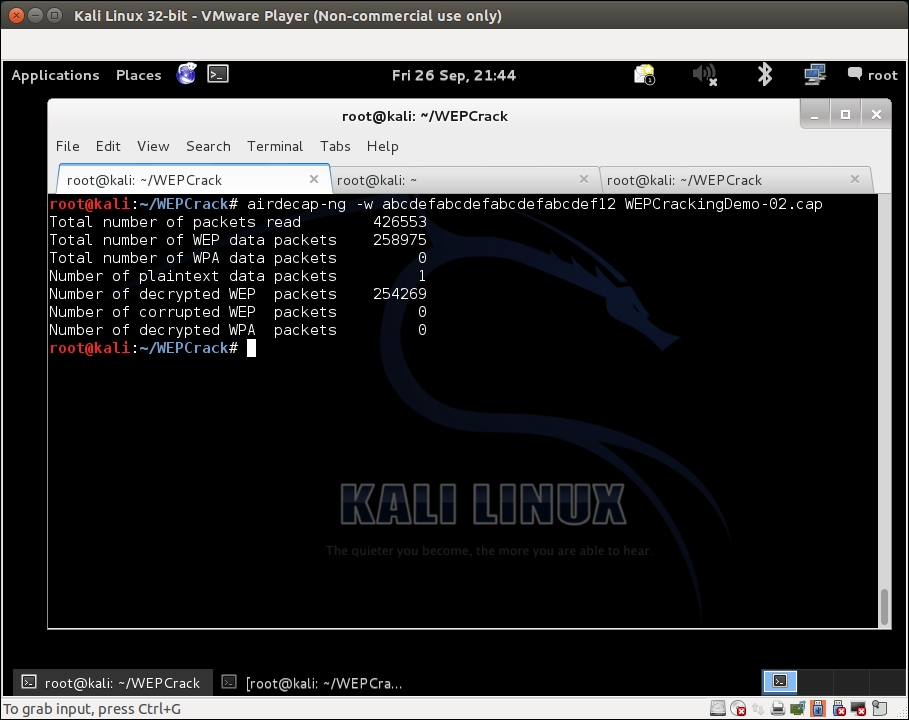
- The decrypted files are stored in a file named
WEPCrackingDemo-02-dec.cap. We use thetsharkutility to view the first ten packets in the file. Please note that you may see something different based on what you captured: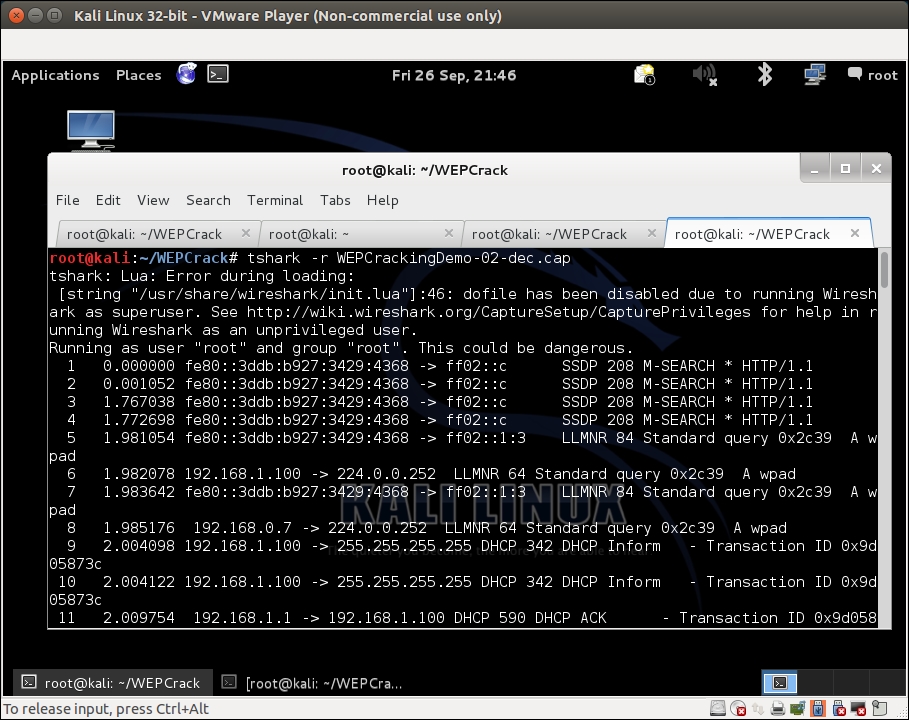
- WPA/WPA2 PSK will work in exactly the same way as with WEP, using the
airdecap-ngutility, as shown in the following screenshot, with the following command:airdecap-ng –p abdefg WPACrackingDemo-02.cap –e "Wireless Lab"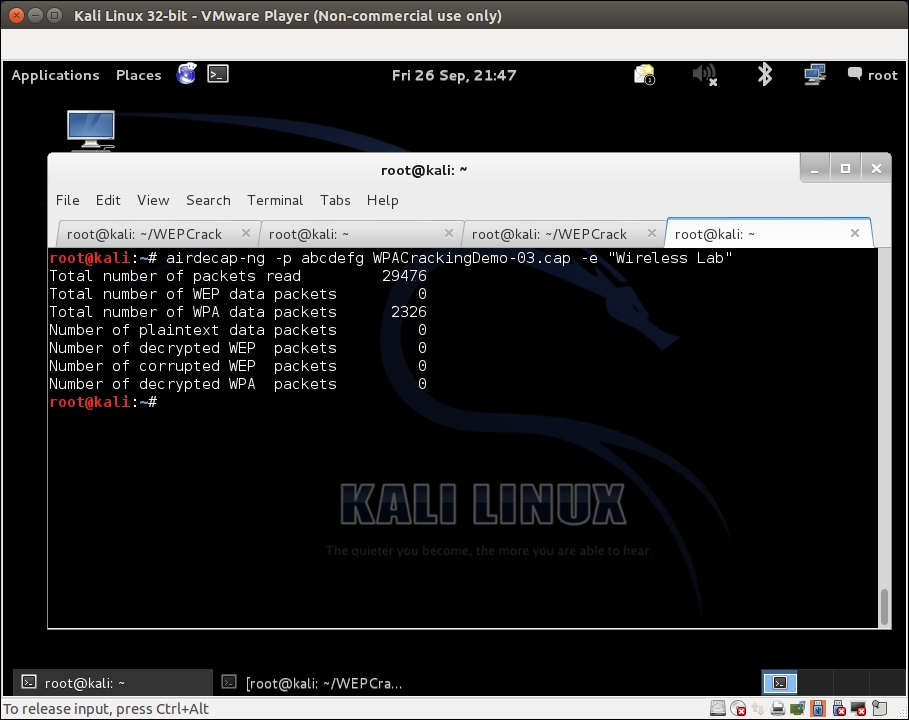
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
