Vulnerability scan analysis is the next step to scanning. For a vulnerability scan assessment to be successful and effective, an accurate analysis of vulnerabilities is absolutely necessary. As most of the scanners produce the scan output in line with the vulnerability plugins available in its repository, a human analysis is highly recommended to avoid false positives and false negatives. In general, a false positive or a false negative represent a scenario where vulnerabilities are either inaccurately reported or not reported at all in the scan output. The definitions are as follows:
- False positive: More commonly encountered, this term means vulnerabilities reported as active in the system do not exist in reality; this means it may be a result of incorrect vulnerability reporting
- False negative: An output in a vulnerability scan will essentially mean that a vulnerability that exists in reality in the infrastructure is not reported in the scan output
In this chapter, we will learn how to effectively analyze the output of the Nessus scan result by covering the following topics:
- Result analysis
- False positive analysis
- Vulnerability analysis
- Vulnerability exploitation
In the previous chapter of this book, we learnt about performing and saving the scan result. This section covers how to read and interpret the Nessus scan report. For the purpose of illustration, a sample report is used for highlighting the vulnerabilities in a Linux system. The report we use for reference is saved in the HTML format and includes details such as Hosts Summary, Vulnerabilities By Host, and Vulnerabilities By Plugin, which were chosen while saving the report.
Nessus offers different options such as HTML, PDF, and comma-separated values (CSV) to save a report. While saving the report—to get the summary and details by vulnerability or host—both the options should be selected.
A typical Nessus Scan Report in HTML format is shown in the following screenshot:
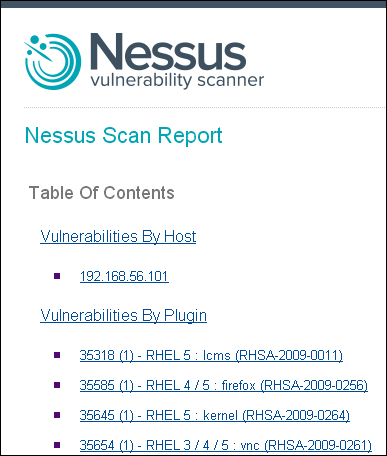
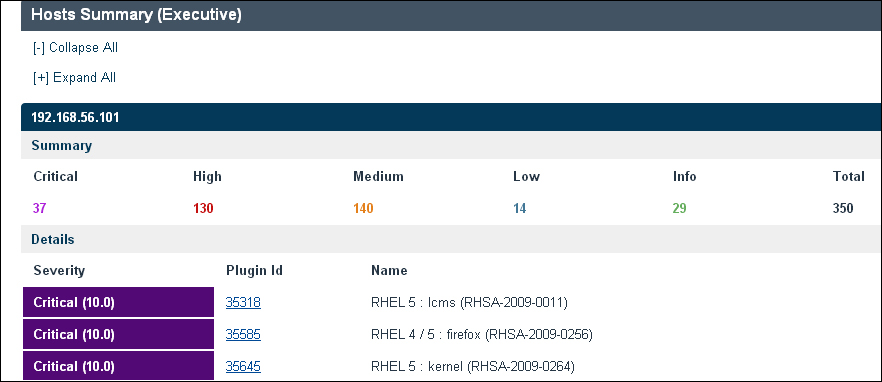
The Hosts Summary (Executive) section will include the count of vulnerabilities against each critical category along with a summarized details of each vulnerability; this includes the following:
The following screenshot displays a sample report showing the host's summary:
The Vulnerabilities By Host section of the report gives a summary of the vulnerability findings per host. The Summary gives details about the scan running time, basic details about the host scanned, and the count of the number of vulnerabilities grouped together by the critical rating.
The following screenshot is a sample report showing the host's summary:
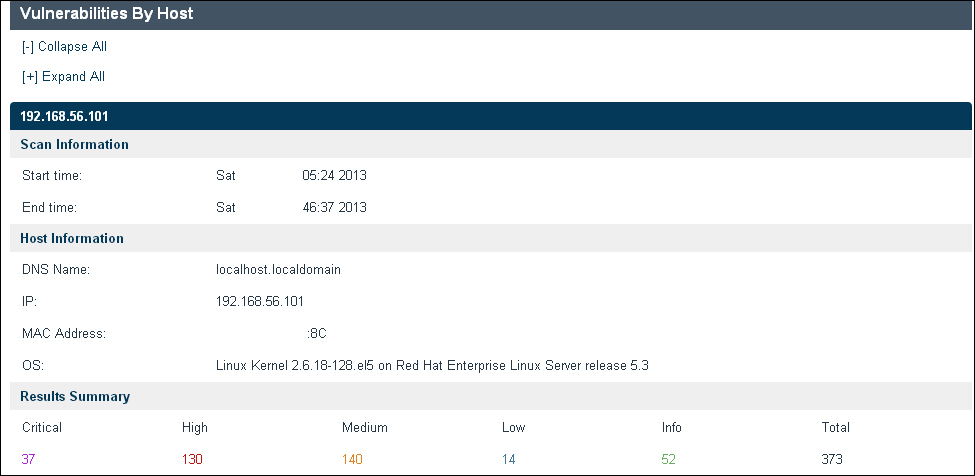
The preceding screenshot displays the Vulnerabilities By Host option with the following sections:
- Scan Information: This section displays the scan's Start time and End time in the day/time/year format.
- Host Information: This section displays the DNS Name, IP, MAC Address, and OS.
- Results Summary: This section gives a count of the vulnerabilities that are grouped together as per the criticality rating assigned by Nessus. These categories are Critical, High, Medium, Low, and Info. It also shows the Total count of vulnerabilities reported by Nessus.
Tip
Common Vulnerability Scoring System (CVSS)
Based on the scoring system, Nessus uses Common Vulnerability Scoring System (CVSS) to rate vulnerabilities. This is an open source vulnerability-rating system based on the characteristics and impact of vulnerability. It includes parameters such as the intrinsic features of vulnerability, features of vulnerability that change over time, and the characteristics of vulnerability that are specific to an environment. Details of the same can be found at http://www.first.org/cvss/cvss-guide.
The following table lists the CVSS scores based on the vulnerability rating used by Nessus. As explained earlier in this chapter, the rating reported by Nessus can be analyzed further as follows:
|
CVSS score |
Criticality |
|---|---|
|
0 |
Info |
|
<4 |
Low |
|
<7 |
Medium |
|
<10 |
High |
|
10 |
Critical |
Note
CVSS scores are referenced from different content available over Internet, including Nessus user guide available at http://www.tenable.com.
The Vulnerabilities By Plugin section contains all the relevant details about the vulnerability. The following section displays a screenshot with the details captured for describing the vulnerability, along with a brief explanation of each field.
The following screenshot is for illustration purposes only; additional reference links and Common Vulnerability and Exposures (CVE) have been removed:
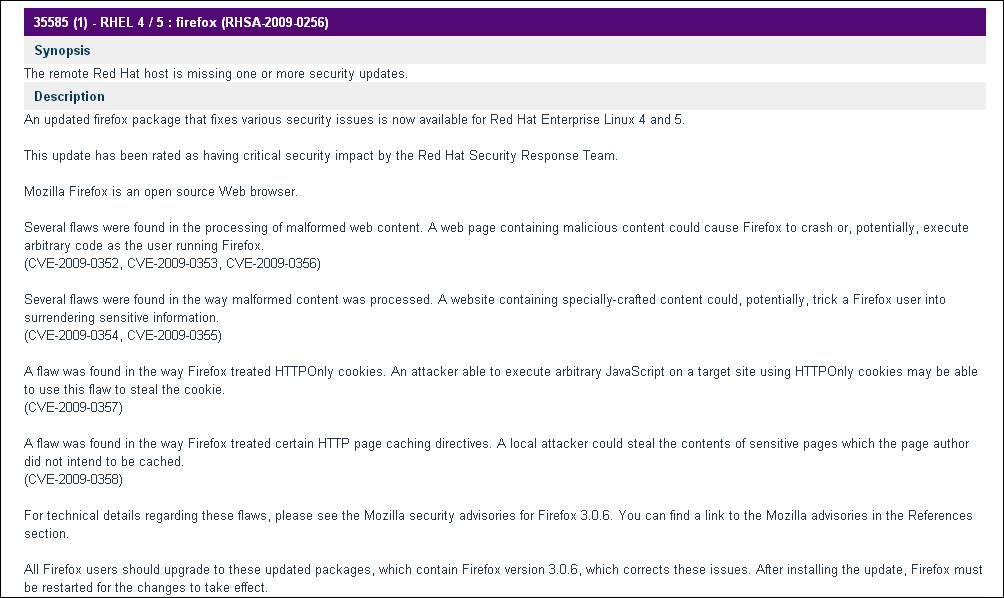
The following screenshot displays References and the CVSS Base Score in the report:
The following screenshot displays the Plugin Information section:
The vulnerability details which are captured in the preceding screenshots are as follows:
Tip
Common Vulnerability and Exposures (CVE) is a database of publicly known security vulnerabilities and exposures. Each vulnerability is assigned a unique CVE number, which is cross-referenced in the Nessus report for providing further details about the vulnerability. For further information, refer to http://cve.mitre.org.
Common Weakness Enumeration (CWE) is a dictionary of common weakness types, which gives details about various commonly known vulnerabilities. This is also referenced by Nessus for better understanding of the vulnerabilities. For further information, refer to http://cwe.mite.org.
False positive refers to the issues or vulnerabilities highlighted by any scanning tool, but which don't actually exist on the target system. The false positive rate differs from tool to tool; the few common pointers that can be considered for a false positive analysis are listed as follows.
The following are the basic understandings of an organization that will aid in the false positive analysis:
- Basic organization infrastructure details, such as the network landscape, infrastructure, OS, application, and technology used, will help cross-check the Vulnerability Assessment (VA) result against the technology and versions actually implemented to remove a false positive
- This becomes more beneficial in situations where the VA scan in a periodic cycle uses the internal infrastructure where these details are readily available
- In case of a time-bound scanning done as an external consultant, it is difficult to have access to all such details. In such cases, as a part of the pre-engagement prerequisites, access to relevant infrastructure stakeholders can be sought for understanding the technology details
In case of a large number of vulnerabilities, at least the most critical ones should be cross-verified for a false positive before being reported.
If there is access to servers/devices on which the VA scan is conducted, vulnerabilities can be crosschecked by logging in to the server or by trying to put a proof of concept against the vulnerability. For example, if the vulnerability states that a clear text File Transfer Protocol (FTP) or Telnet service is running in the server, we can either log in to the server to crosscheck if these services are actually running, or give a proof of concept by trying to connect FTP or the Telnet protocol from the testing machine.
Open source scanning tools such as Nmap can also be used to enumerate the infrastructure again for open vulnerabilities to cross-check the findings of the VA report.
In general terminologies, vulnerability analysis is considered similar to vulnerability assessment. However, I feel there is a small difference between these two. Vulnerability analysis is a part of the vulnerability assessment cycle, where you identify the vulnerability, quantify the risk, and prioritize the risk. Vulnerability analysis investigates the vulnerabilities that are detected by a vulnerability assessment tool.
It should be noted that vulnerability analysis is an optional step that depends on the vulnerability assessment tool's capability, scanning environment, in-depth analysis, and so on. Investigation of vulnerability should be done considering all these factors. Nowadays, most of the vulnerability assessment tools fetch automated reports that have no or minimal false positives. Nessus is one of these.
When a vulnerability assessment is done by a security operation center (SOC) or an internal security department where you don't want to put much effort in doing manual analysis, you prefer to give all the scan results to the different teams for vulnerability closure. In this case, you are not very concerned about the severity of the vulnerability, and so on. If we talk about a different scenario where you are engaged with a firm as a third-party auditor and you are doing a vulnerability assessment, then in this case, each vulnerability you report to the firm will be taken very seriously and has to have proper justifications for the vulnerability's existence, severity, applicability, and so on.
In this section, we will explore the second scenario mentioned previously that talks about a third-party consultant doing an audit or a technical vulnerability assessment for a client, where a vulnerability report needs to be perfect in terms of applicability, risk severity, environment dependencies, and no false positives.
Once you get the scan result report from a vulnerability scanner such as Nessus, you can do a detailed review of each vulnerability to check at least the following areas:
- False positives
- Risk severity
- Applicability analysis
- Fix recommendations
Risk severity is the severity of the risk associated with each vulnerability, depending on the environment and nature of the business. Risk severity can be quantitative or qualitative. Generally, it is preferred, and industry-wise recognized, to use risk severity as qualitative. Risk can be categorized as Critical, High, Medium, Low, and Info. A few organizations categorize them only as High, Moderate, and Low.
Most of the large-enterprise organizations that go through different security certifications, such as ISO 27001, have their risk management process defined. These risk management processes define their risk severities as well as their definitions, risk matrix, risk acceptance criteria, and so on. While performing a vulnerability assessment, you may need to recategorize the risk severity ratings if you follow the risk matrix.
For example, vulnerability on the public website of an organization that is running without SSL. This vulnerability might be declared to have a High risk rating by a vulnerability scanner, where-as, if you do a vulnerability analysis, it may declare a different risk level.
Let's take a scenario where you are doing a vulnerability assessment for a small NGO; they have no sensitive information on their website and the vulnerability of SSL is discovered. All information available on the website is public. In this scenario, you may say the vulnerability risk rating is Low or Info, whereas the scanning tool might report it as High.
In a different scenario, where you are doing vulnerability assessment for a medium-sized firm which does surveys on their website and public reports, the same vulnerability of SSL is discovered. Most of the information recorded here is confidential and should not be compromised. In this scenario, you can say that the vulnerability risk rating is Medium or High and will be rated as High by the scanning tool.
Another scenario where you are doing a vulnerability assessment for a large bank, which has net banking login on their website. Bank customers log in to use the net banking service and do their financial transactions; again, the same SSL vulnerability is discovered. In this case, if SSL is not implemented, this is a critical risk rating vulnerability, and the tool will report it as High.
It is very important for us to relook at the risk ratings given by vulnerability scanningtools if we want to treat risks based on their risk ratings.
Each vulnerability discovered by vulnerability assessment tools may not be applicable to the organization. Vulnerability applicability is used for checking if the vulnerability reported by an automated vulnerability-assessment tool is applicable to the organization or not.
For example, vulnerability such as a weak password existing in an application. This vulnerability might be declared to have a High risk rating by a vulnerability scanner, where-as, if you do vulnerability applicability analysis, it may be declared as not applicable.
Let's take a scenario where you are doing the vulnerability assessment of a small organization. The vulnerability scanner reports weak password vulnerability for an application. It is found by the tool that some of the passwords for that application were only seven-characters long, which is reported as a High risk severity vulnerability. While doing an applicability analysis, we found that the organization has approved a security password policy that considers a password as strong even if it is seven-characters long; hence, this vulnerability is not applicable to the organization.
It is important to relook at the risks and see if they are really applicable for the organization or not.
Nessus gives fix recommendations in the tool-generated report for each vulnerability. A few of them can be fixed using multiple ways, for instance, by using compensatory controls. A vulnerability can be patched or fixed in multiple ways.
Let us illustrate this through a sample vulnerability. A vulnerability such as the cleartext protocol FTP is found open on a server. The fix usually recommended is used as a secured protocol for file transfer such as Secure File Transfer Protocol (SFTP). Another solution may be to analyze the requirement of having FTP open. There might be a case where FTP was left open during testing; now even in production, FTP is open and is no longer in use. In this case, the FTP port should be closed on that server. In this scenario, we see that for the same vulnerability there are two fixes: one is to use SFTP instead of FTP, another is to close the FTP port. Likewise, it is recommended to apply the fixes wisely.
In Chapter 1, Fundamentals, we covered the differences between a vulnerability assessment and a penetration testing exercise. Basically, the difference between these two is related to exploiting the vulnerabilities. In a vulnerability assessment, you are required to discover the vulnerabilities only; but in a penetration test, you are also required to exploit the vulnerabilities that you found during the vulnerability scan.
Penetration testing may not necessarily be intrusive; it can also be limited to the proof of concepts. Nowadays, most of the organizations want to have their pentest (penetration test) scope limited only till the proof of concepts are produced, because if you do an intrusive test, your system/service may go down.
There are multiple penetration testing tools available in the market that are equipped with scripts, programs, payloads, and injections, for carrying out penetration testing.
The following are a few examples showing how a vulnerability can be exploited. The following vulnerabilities have been reported by a Nessus scanner on a sample machine.
A vulnerability title is of the first example is a Cross-site scripting (XSS) found on an application homepage.
Let's take a scenario where the vulnerability scan resulted in a vulnerability of XSS for one of the applications scanned while running on a target host. Details for the XSS are given in the following Nessus report, reflecting on which application the page vulnerability exists:
|
Nessus report head |
Nessus report example text |
|---|---|
|
Synopsis |
The remote web server hosts a PHP script that is prone to a cross-site scripting attack. |
|
Description |
The version of phpMyAdmin fails to validate BBcode tags in user input to the An attacker may be able to leverage this issue by injecting arbitrary HTML or script code into a user's browser to be executed within the security context of the affected site. For example, this could be used to display a page with arbitrary text and a link to an external site. |
|
Solution |
Upgrade to phpMyAdmin 3.4.0-beta1 or later. |
|
See Also |
http://www.phpmyadmin.net/home_page/security/PMASA-2010-9.php |
|
Plugin Information |
Publication date: January 6, 2011, Modification date: October 24, 2011 |
|
Risk Information |
Medium 4.3 (CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N) 3.6 (CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N) |
|
Vulnerability Information |
Cross-site scripting allows an attacker to run scripts that may lead to stealing the web browser session information or creating web links to deface the web application. |
|
References Information |
BID 45633 CVE CVE-2010-4480 XREF OSVDB:69684 XREF EDB-ID:15699 |
|
Plugin Output |
Nessus is able to exploit the issue using the following URL:
|
Once a cross-site scripting is reported by a vulnerability scanner, and if you are engaged to conduct penetration testing for that machine, you are required to further penetrate the vulnerability. This can be done by running malicious scripts, to do the proof of concept, and by exploitation.
Cross-site scripting, which is also known as XSS, can either be in an input parameter that takes some input in the URL or be in one of the input boxes on the web application. To exploit it, you need to tamper the end user's input that goes in the parameter which further displays the same input. You may want to use a tools such as Burp Suits, Bayden Tamper IE, or any other HTTP traffic interceptor. By using the interceptor, you can fiddle with the HTTP request going from the client machine to the server.
To test if XSS exists or not, the following sample payloads can be used as input to the end user's input parameters:
<script>alert("XSS Exist")</Script>
"><script>alert("XSS Exist")</Script>The preceding payloads need to be tweaked based on the code which you are exploiting.
To penetrate further, you can use the following sample payloads:
<script>alert(document.cookie)</script> onmouseenter="alert(document.cookie); onreadystatechange="alert(document.cookie);
This will pop up the live cookie details on the screen, as shown in the following screenshot:
In case of persistent XSS, where end user inputs get stored in the database and are displayed again for all users from the database while browsing the application page. You should try the following payload, which creates a hyperlink on the web page, which will redirect the user to the attacker's website:
http://TargetIP:8080/ShowingImage.asp?id=<img%20src="http://attackerURL.com/images/1/419979.JPG"> <a href = "http://www.attackerURL.com">click</a>
XSS can be exploited further with a deep understanding of scripts and coding.
The vulnerability title for the second example is exploitation of weak or easily guessable passwords found on the router.
Nessus has the capability to review Cisco device configurations against industry's best practices. One of the common vulnerabilities, which can be observed when the administrator has not carefully configured the Cisco device, is using default or weak passwords.
Cisco Internetwork Operating System (Cisco IOS) is the operating system for Cisco network devices such as routers and switches. We will take the example of a router for illustration purposes. The Cisco router configuration files have all the relevant configurations for the router to perform it's routing functionality in the network.
Cisco IOS provides an option to set different types of password: type 0 typically means a password with no encryption, type 7 means a password encrypted using service password encryption command, which uses a proprietary algorithm, and type 5 means the password is protected with the enabled-secret command, which uses MD5 hashing in the configuration. When we see type 5 or type 7 passwords in the Cisco router configuration, they will appear as encrypted.
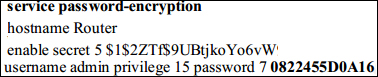
A Cisco type 7 password is not considered to be safe, as it is encrypted using a weak algorithm, and can be cracked.
While scanning the Cisco router configuration by providing credentials with appropriate privileges, Nessus will highlight the use of a weak password.
It can be exploited once the Nessus report highlights the use of a weak type 7 password and can be cracked further using one of the many freeware utilities available on the Internet. For demonstration purpose, following URL is used:
http://www.ibeast.com/content/tools/CiscoPassword/index.asp
If the Nessus highlight uses of weak or type 7 passwords post scanning of the Cisco router; we have used a type 7 password used in our example (
0822455D0A16
).
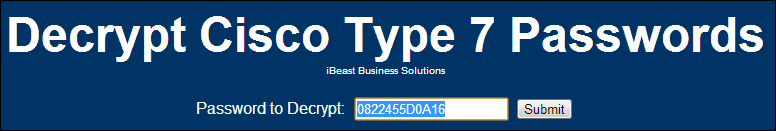
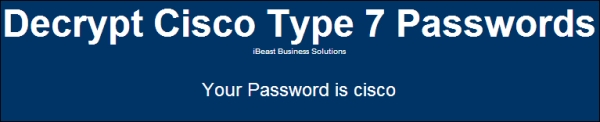
If we take this password and use the preceding link to crack it, within a few seconds we will come to know that the default password, that is, cisco, has been used.
In the following screenshot, we enter a type 7 password in a commonly available password cracking tool:
The following screenshot displays the tool giving the output (cracked password):
The vulnerability title for the third example is possible SQL Injection.
SQL Injection is an application vulnerability which can be discovered by Nessus. SQL Injection allows an attacker to inject or run a malicious SQL command by which the attacker directly communicates with the database running behind the application and executes the SQL queries. This can be as destructive as running an fdisk command on a database server which will completely format the server, and creating a local admin on the server will compromise the server in all aspects. This also allows an attacker to run extended stored procedures, which are very powerful commands. By running malicious SQL queries, the attacker can modify the input strings that form the SQL queries in such a way that the outputs will reveal the required schema and data from the database.
When a SQL Injection vulnerability is reported by the vulnerability scanner and you are engaged in doing a penetration test, you need to exploit it further.
The following is the process for exploitation:
On the application login page, where the username and password need to be entered, use the input injections, mentioned in the following table, to check if a SQL Injection really exists for that particular page:
|
Serial number |
Injection strings |
|---|---|
|
1 |
Username: Password: |
|
2 |
Username: Password: |
|
3 |
Username: Password: |
All exploits are unique in nature, hence, I recommend to construct your injections, scripts, and payloads depending on your target machine.
