Nessus system configuration settings can be referred to under the Configuration tab. This has five different groups of settings as follows:
- General Settings
- Feed Settings
- Mobile Settings
- Result Settings
- Advanced Settings
The General Settings tab can be seen under Configuration by logging in to Nessus with administrator privileges. There are two different options of General Settings that exist in the Setting Type dropdown:
- SMTP Server
- Web Proxy
The SMTP server settings allow you to configure the SMTP server with your Nessus server to send out results of completed scans by automated e-mails.
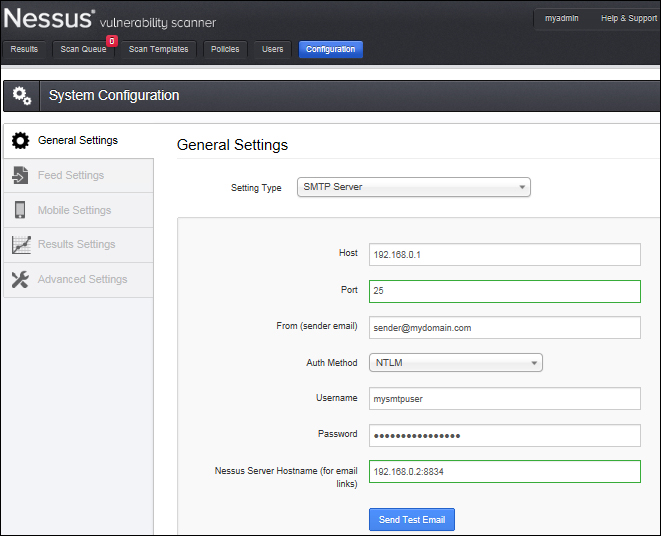
Different settings for SMTP can be configured as per your SMTP configuration. SMTP settings are explained in the following table:
|
SMTP setting |
Description |
|---|---|
|
Host |
The SMTP server hostname or IP. |
|
Port |
The port number to connect the SMTP server. |
|
From (Sender email) |
E-mail ID from the report e-mails should appear as a sender. |
|
Auth Method |
The SMTP authentication method. |
|
Username |
The username with which to authenticate to the SMTP server. |
|
Password |
The password corresponding with this username. |
|
Nessus Server Hostname |
This is only for the e-mail links, Nessus server hostname, or IP address to be specified. |
|
Send Test Email |
Lets you test by sending a test e-mail. |
Some organizations host a web proxy server between the external and internal networks to pass the traffic through. To update Nessus with the latest plugins in a web proxy environment, it is necessary to configure web proxy settings as per organization setup. This enables Nessus to reach the Nessus plugin server over the Internet to download the latest plugins.
Different settings for the web proxy can be configured as per your web proxy configuration. These settings are explained in the following table:
|
Web proxy setting |
Description |
|---|---|
|
Host |
The proxy hostname or IP. |
|
Port |
The port number for the proxy to connect. |
|
Username |
The username to connect the proxy to. |
|
Password |
The password for the username to connect the proxy to. |
|
User-agent |
Required if the proxy uses filter-specific HTTP user agents. The custom user agent string needs to be specified. |
The issue of mobile device security has become the priority in recent times with the widespread use of mobile devices in the corporate domain with concepts such as Bring Your Own Device (BYOD) being used proactively. Such devices when connected to corporate networks bring with them the inherent vulnerabilities of their mobile platforms. Nessus offers a mobile security scanning option where information and vulnerabilities for mobile devices recently connected to respective servers are scanned.
Currently, plugins related to the iPhone 4, the iPad, Windows Phone, and Android devices are included, and Nessus has the ability to scan Active Directory Service Interfaces (ADSI) and Apple Profile Manager to identify mobile devices connected to these servers, and to identify vulnerabilities.
The Mobile Settings tab presents options to configure the settings for the following type:
- ActiveSync (Exchange)
- Apple Profile Manager
- Good For Enterprise
This can be seen in the following screenshot:
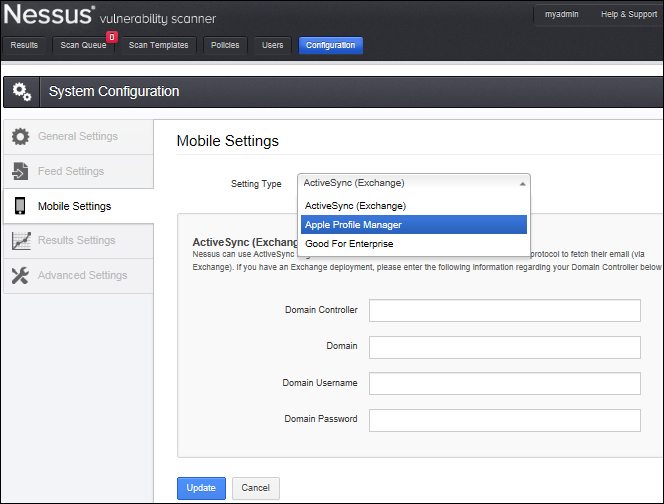
Nessus can be configured to use ActiveSync for gathering information about all the mobile devices that use this protocol to fetch their e-mail (via Exchange). If you have an Exchange deployment, you can configure the domain controller settings, as listed in the following table:
|
ActiveSync mobile setting |
Description |
|---|---|
|
Domain Controller |
The domain controller IP. |
|
Domain |
The domain name. |
|
Domain Username |
The username to connect the domain to. |
|
Domain Password |
The password for the username to connect to. |
Nessus can be configured to use Apple Profile Manager for gathering information about all the iOS devices. If you have Apple Profile Manager deployed, you can configure the Apple Profile Manager settings, as listed in the following table:
|
Apple Profile Manager mobile setting |
Description |
|---|---|
|
Apple Profile Manager server |
The Apple Profile Manager server IP. |
|
Apple Profile Manager port |
The Apple Profile Manager server port to connect to. |
|
Apple Profile Manager username |
The username to log in with. |
|
Apple Profile Manager password |
The password that corresponds with the username. |
|
SSL |
Check/uncheck this option based on the environment. |
|
Verify SSL Certificate |
Check this option if you want the SSL certificate to be verified. |
|
Force Device Updates |
Check this option if you want a device update to be forced. |
|
Device Update Timeout (Minutes) |
The device update timeout in minutes. |
Nessus can be configured to use Good Mobile device management for gathering information about all the mobile devices that use this protocol. If you have Good For Enterprise deployed, you can configure the settings listed in the following table:
|
Good For Enterprise mobile setting |
Description |
|---|---|
|
GMC Server |
The GMC server IP needs to be mentioned here. |
|
Port |
The port number to use to connect with the GMC server. |
|
Domain |
The domain name. |
|
Username |
The username to connect with. |
|
Password |
The password that corresponds with the username. |
|
SSL |
Check/uncheck this option based on the environment. |
|
Verify SSL Certificate |
Check this option if you want a device to be verified. |
Result Settings can be seen under Configurations. This allows you to add rules to disable plugins or change their severity.
The following screenshot shows how to add a new plugin rule:
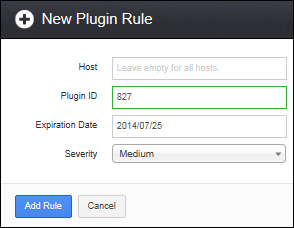
The following table illustrates the new plugin rule options in detail:
|
New plugin rule option |
Description |
|---|---|
|
Host |
If the result plugin rule is only for a particular IP/host, the host can be mentioned in the Host field. If the rule is to be applied for the entire host scanned, this can be left blank. |
|
Plugin ID |
The plugin ID to be provided to specify which plugin the rule is for. |
|
Expiration Date |
The expiration date for a rule can be specified here in case it needs to expire on a particular date. |
|
Severity |
Severity can be set from the dropdown as per the rule you want to set. It may be Hidden, Informational, Low, Medium, High, or Critical. |
The Nessus GUI configuration menu contains several configurable options.
It is recommended that these settings be reviewed and modified appropriately based on your scanning environment. The option can be changed and saved using the Save button or can be removed altogether using the X sign present next to the option.
Special care should be taken while modifying the max_hosts and max_checks values in the upcoming table. These values represent the maximum number of checks and hosts being scanned at one time and have a direct impact on the scanning to be performed. The max_checks value, if greater than 5, can have an adverse impact on target servers, so it should be avoided. Similarly, a high value of max_hosts can overwhelm the host scanning system, and it depends on the capacity of the host on which Nessus is installed. It is recommended that this value also be kept relatively low (can start with 10); it can be optimized as per the environment and system capability.
The following screenshot shows some of the options from the table following it; options can be added or removed using the Add Settings tab and the X button respectively.
The advanced setting options and their uses as per the Nessus documentation are mentioned in the following table:
|
New plugin rule options |
Description |
The default value |
|---|---|---|
|
allow_post_scan_editing |
If enabled, post scan editing is possible. |
Yes |
|
auto_enable_dependencies |
Automatically activates the plugins that depend on it. If disabled, not all plugins may run despite being selected in the scan policy. |
Yes |
|
auto_update |
Controls automatic plugin updates. If enabled and Nessus is registered, it fetches the newest plugins from plugins.nessus.org automatically. Disable if the scanner is on an isolated network not able to reach the Internet. |
Yes |
|
auto_update_delay |
The number of hours to wait between two updates. Four hours (4) is the minimum allowed interval. |
24 |
|
cgi_path |
During the testing of web servers, use the colon-delimited list of CGI paths. |
|
|
checks_read_timeout |
Lets you specify the read timeout for the sockets of the tests. |
5 |
|
disable_ntp |
Disables the old NTP legacy protocol. |
Yes |
|
disable_xmlrpc |
Disables the new XMLRPC (web server) interface. |
No |
|
Dumpfile |
Lets you specify the location of a dump file for debugging output if generated. |
|
|
global.max_hosts |
The maximum number of hosts that can be scanned. |
130 |
|
global.max_scans |
If set to nonzero, this allows you to define the maximum number of scans that may take place in parallel. |
0 |
|
global.max_simult_tcp_sessions |
The maximum number of simultaneous TCP connections |
50 |
|
global.max_web_users |
If set to nonzero, this defines the maximum of (web) users that can connect in parallel. |
1024 |
|
listen_address |
The IPv4 address to listen for incoming connections. If set to 127.0.0.1, this will restrict access to local connections only. |
0.0.0.0 |
|
listen_port |
The port to listen for (the old NTP protocol). Used for pre-4.2 NessusClient connections. |
1241 |
|
log_whole_attack |
Allows you to log every detail of the attack and is helpful for debugging issues with the scan, but this may be disk intensive. |
No |
|
Logfile |
Where the Nessus logfile is stored. |
|
|
max_checks |
The maximum number of simultaneous checks against each host tested. |
5 |
|
max_hosts |
The maximum number of hosts checked at one time during a scan. |
5 |
|
nasl_log_type |
Direct the type of NASL engine output in |
Normal |
|
nasl_no_signature_check |
Allows you to specify whether Nessus should consider all NASL scripts as being signed. Selecting Yes is unsafe and is not recommended. |
No |
|
non_simult_ports |
Lets you speficy those ports against which two plugins should not be run simultaneously. |
139, 445, 3389 |
|
optimize_test |
Lets you optimize the test procedure. Changing this to No will cause scans to take longer and typically generate more false positives. |
Yes |
|
plugin_upload |
Lets you designate whether administrator users may upload plugins. |
Yes |
|
plugins_timeout |
The maximum lifetime of a plugin's activity (in seconds). |
320 |
|
|
The range of ports the port scanners will scan. Can use the keywords the Default or All as well as a comma-delimited list of ports or ranges of ports. |
Default |
|
|
Lets you specify whether Nessus should purge the plugin database at each update. This directs Nessus to remove, redownload, and rebuild the plugin database for each update. Choosing Yes will cause each update to be considerably slower. |
No |
|
|
Directs Nessus to use more or less memory when idle. If Nessus is running on a dedicated server, setting this to High will use more memory to increase performance. If Nessus is running on a shared machine, setting this to Low will use considerably less memory, but at the price of a moderate performance impact. |
Low |
|
|
Lets you reduce connections in case of congestion. |
No |
|
|
Allows you to specify whether to anonymously report crashes to Tenable. |
Yes |
|
|
The location of the Nessus rules file ( |
|
|
|
Safe checks rely on banner grabbing rather than active testing for a vulnerability. |
Yes |
|
|
If this is enabled, the list of plugin dependencies and their outputs are not included in the report. A plugin may be selected as part of a policy that depends on other plugins to run. By default, Nessus will run those plugin dependencies but will not include their outputs in the report. Setting this option to No will cause both the selected plugin and any plugin dependencies to appear in the report. |
Yes |
|
|
If this option is set, Nessus will not scan a network incrementally (10.0.0.1, then 10.0.0.2, then 10.0.0.3, and so on) but will attempt to slice the workload throughout the whole network (for examaple, it will scan 10.0.0.1, then 10.0.0.127, then 10.0.0.2, then 10.0.0.128, and so on). |
No |
|
|
Makes sure that only "strong" SSL ciphers are used while connecting to port 1241. Supports the keyword strong or the general OpenSSL designations as listed at http://www.openssl.org/docs/apps/ciphers.html. |
Strong |
|
|
Lets you stop scanning a host that seems to have been disconnected during the scan. |
No |
|
|
Lets you stop a scan that seems to be hung up. |
No |
|
|
The throttle scan is for when the CPU is overloaded. |
Yes |
|
|
Lets you specify where the Nessus web server (user interface) log is stored. |
|
|
|
The idle session timeout for Nessus. |
30 |
|
|
The port for the Nessus web server to listen for (the new XMLRPC protocol). |
8834 |
All these advanced settings need to be analyzed properly before being applied. The recommended settings may vary from environment to environment.
A few sections of this chapter, which are specific configuration settings, have been referenced from learning material available on Nessus website: http://www.tenable.com.
