These days, security is the most vital subject for any organization irrespective of their size or the kind of the business they do. The primary reason for this is that organizations don't want to lose their reputation or business over compromises affecting security; secondly, they have to meet legal and regulatory requirements. When it comes to technical security of the infrastructure, Vulnerability Assessment and Penetration Testing (PT or PenTest) play the most vital role. This chapter illustrates what a PT or PenTest is, why it is required and how to set up and manage Nessus for your organization.
This chapter will introduce you to Nessus, a tool for vulnerability assessment and penetration testing. We will also cover the following topics:
- Vulnerability Assessment
- Penetration testing
- Introduction to Nessus
- Installing Nessus on different platforms
- Updating Nessus plugins
- Nessus user management
- Nessus system configuration
Vulnerability Assessment (VA) and Penetrating Testing (PT or PenTest) are the most common types of technical security risk assessments or technical audits conducted using different tools. These tools provide best outcomes if they are used optimally. An improper configuration may lead to multiple false positives that may or may not reflect true vulnerabilities. Vulnerability assessment tools are widely used by all, from small organizations to large enterprises, to assess their security status. This helps them with making timely decisions to protect themselves from these vulnerabilities. This book outlines the steps involved in conducting Vulnerability Assessments and PenTests using Nessus. Nessus is a widely recognized tool for such purposes. This section introduces you to basic terminology with reference to these two types of assessments.
Vulnerability in terms of IT systems can be defined as potential weaknesses in system/infrastructure that, if exploited, can result in the realization of an attack on the system.
An example of a vulnerability is a weak, dictionary-word password in a system that can be exploited by a brute force attack (dictionary attack) attempting to guess the password. This may result in the password being compromised and an unauthorized person gaining access to the system.
Vulnerability Assessment is a phase-wise approach to identifying the vulnerabilities existing in an infrastructure. This can be done using automated scanning tools such as Nessus, which uses its set of plugins corresponding to different types of known security loopholes in infrastructure, or a manual checklist-based approach that uses best practices and published vulnerabilities on well-known vulnerability tracking sites. The manual approach is not as comprehensive as a tool-based approach and will be more time-consuming. The kind of checks that are performed by a vulnerability assessment tool can also be done manually, but this will take a lot more time than an automated tool.
Penetration Testing has an additional step for vulnerability assessment, exploiting the vulnerabilities. Penetration Testing is an intrusive test, where the personnel doing the penetration test will first do a vulnerability assessment to identify the vulnerabilities, and as a next step, will try to penetrate the system by exploiting the identified vulnerabilities.
It is very important for you to understand why Vulnerability Assessment or Penetration Testing is required. Though there are multiple direct or indirect benefits for conducting a vulnerability assessment or a PenTest, a few of them have been recorded here for your understanding.
Vulnerability Assessment uncovers the loopholes/gaps/vulnerabilities in the system. By running these scans on a periodic basis, an organization can identify known vulnerabilities in the IT infrastructure in time. Vulnerability Assessment reduces the likelihood of noncompliance to the different compliance and regulatory requirements since you know your vulnerabilities already. Awareness of such vulnerabilities in time can help an organization to fix them and mitigate the risks involved in advance before they get exploited. The risks of getting a vulnerability exploited include:
- Financial loss due to vulnerability exploits
- Organization reputation
- Data theft
- Confidentiality compromise
- Integrity compromise
- Availability compromise
The well-known information security standards (for example, ISO 27001, PCI DSS, and PA DSS) have control requirements that mandate that a Vulnerability Assessment must be performed.
A few countries have specific regulatory requirements for conducting Vulnerability Assessments in some specific industry sectors such as banking and telecom.
This section describes the key phases in the life cycles of VA and PenTest. These life cycles are almost identical; Penetration Testing involves the additional step of exploiting the identified vulnerabilities.
It is recommended that you perform testing based on the requirements and business objectives of testing in an organization, be it Vulnerability Assessment or Penetration Testing. The following stages are involved in this life cycle:
- Scoping
- Information gathering
- Vulnerability scanning
- False positive analysis
- Vulnerability exploitation (Penetration Testing)
- Report generation
The following figure illustrates the different sequential stages recommended to follow for a Vulnerability Assessment or Penetration Testing:
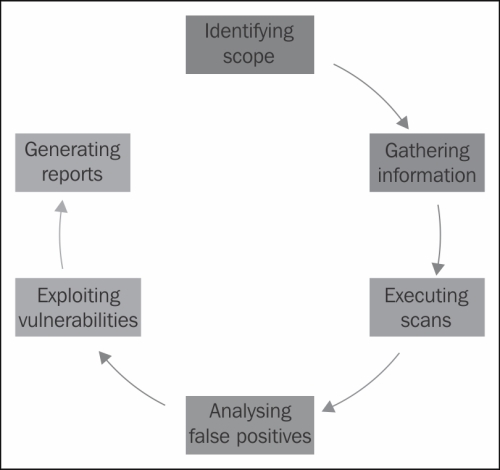
Scoping is the primary step of any security assessment activity. In order to execute a VA or PenTest, the first step is to identify the scope of the assessment in terms of infrastructure against which the assessment is to be conducted, for example, servers, network devices, security devices, databases, and applications. Scoping depends on the business objective of the Vulnerability Assessment. During the scoping, a scanning window should also be agreed upon. Also, the types of attacks that are permitted should be agreed upon. After deciding on the scope of assessment, this phase also includes planning and preparation for the test, which includes deciding on the team, date, and time of the test. Another major factor that should be taken care of prior to beginning the engagement is signing a formal engagement agreement between the security tester and the party on whose infrastructure these tests will be performed. Scoping should also include identifying the count of infrastructure elements to be tested.
Apart from the infrastructure scope and other program management modalities, the exact scope, the organization's approach to the business objective, and the methodology of the assessment should be decided. For deciding on the business objective, the organization should identify the type of attack that it would like to get mimicked.
An example of an objective that a company might seek is: "To find out what an external attacker can achieve by targeting externally exposed infrastructure with only the knowledge of a publicaly exposed IP address." This type of requirement will be met through an external Blackbox penetration testing of infrastructure and applications, and the approach and the methodology should be in accordance with that.
Based on the accessibility of infrastructure from the Internet or intranet, the testing can be done from an external or internal network. Also, based on the type of details, the infrastructure testing can be Blackbox or Greybox. And depending on the type of infrastructure, the plugins or features of a vulnerability scanning tool should be enabled, aided by appropriate manual checks.
Note
In Blackbox testing, only details such as the IP address are shared with the tester. Details giving an insight to the infrastructure, such as type and OS version, are not shared with respect to Nessus Scanner; this type of testing will involve a non credential scan (explained in Chapter 2, Scanning). This allows the tester to mimic an external attacker with limited knowledge about the infrastructure.
Greybox testing will include some details of the infrastructure to be shared, such as the type of device and software version that allow getting more comprehensive and administrator credentials fed to the tool for more comprehensive results. In addition, to mimic an internal attacker with knowledge about the infrastructure with respect to Nessus Scanner, this type of testing will involve credentialed scanning, giving more comprehensive results.
Information gathering is the second and most important stage of a VA-PT assessment. This stage includes finding out information about the target system using both technical (WhoIS) and nontechnical passive methods such as the search engine and Internet groups). This step is critical as it helps in getting a better picture of the target infrastructure and its resources. As the timeline of the assessment is generally time bound, information captured during this phase helps in streamlining the effort of testing in the right direction by using the right tools and approach applicable to target systems. This step becomes more important for a Blackbox assessment where very limited information about the target system is shared.
Information gathering is followed by a more technical approach to map the target network using utilities such as pings and Telnet and using port scanners such as NMAP. The use of such tools would enable assessors to find a live host, open services, operating systems, and other information.
The information gathered through network mapping will further validate information gathered through other passive means about the target infrastructure, which is important to configure the vulnerability scanning tool. This ensures that scanning is done more appropriately.
This stage involves the actual scanning of the target infrastructure to identify existing vulnerabilities of the system. This is done using vulnerability scanners such as Nessus. Prior to scanning, the tool should be configured optimally as per the target infrastructure information captured during the initial phases. Care should also be taken that the tool is able to reach the target infrastructure by allowing access through relevant intermediate systems such as firewalls. Such scanners perform protocol TCP, UDP, and ICMP scans to find open ports and services running on the target machine and match them to well-known published vulnerabilities updated regularly in the tool's signature database if they exist in the target infrastructure. The output of this phase gives an overall view of what kind of vulnerabilities exist in the target infrastructure that if exploited can lead to system compromise.
As an output of the scanning phase, one would obtain a list of vulnerabilities of the target infrastructure. One of the key activities to be performed with the output would be false positive analysis, that is, removing any vulnerability that is falsely reported by the tool and does not exist in reality. All scanning tools are prone to report false positives, and this analysis can be done using methods such as correlating vulnerabilities with each other and previously gathered information and scan reports, along with actually checking whether system access is available.
Vulnerability scanners give their own risk rating to the identified vulnerabilities; these can be revisited considering the actual criticality of the infrastructure element (server or network device) to the network and impact of the vulnerability.
In case system owners require proof of existing vulnerabilities or exploits to understand the extent to which an attacker can compromise a vulnerable system, testers will be required to demonstrate exploits in a controlled environment with out actually making the infrastructure unavailable, unless that's a requirement. Penetration Testing is the next step to Vulnerability Assessment aiming to penetrate the target system based on exploits available for the identified vulnerabilities. For exploitation, our own knowledge or publicaly available exploits of well-known vulnerabilities can be utilized. Penetration Testing or Vulnerability Exploitation can be broadly divided into phases such as preexploitation, exploitation, and postexploitation.
Activities in the pre-exploitation phase are explained in phases 1 to 4, that is, enumerating the infrastructure and identifying the vulnerability.
Once any vulnerability is exploited to gain access to the system, the attacker should aim to further detail the network by sniffing traffic, mapping the internal network, and trying to obtain a higher privilege account to gain the maximum level of access to the system. This will enable testers to launch further attacks on the network to further increase the scope of compromised systems. The postexploitation step will also involve clearing of tracks by conducting activities such as clearing logs and disabling antivirus.
As a post-exploitation phase tester, you can demonstrate how an attacker can maintain access to the system through backdoors and rootkits.
After completing the assessment as per the scope of work, final reporting needs to be done covering the following key areas:
- A brief introduction about the assessment
- The scope of assessment
- The management/executive summary
- A synopsis of findings with risk severity
- Details about each finding with their impact and your recommendations to fix the vulnerability
