Nessus is well-known as a vulnerability scanner, but it also provides the option to do compliance checks. Using this option, it can be cross-checked whether the secure configuration settings of an infrastructure, such as servers, network devices, database, and desktop, are in compliance with the defined policy or best practices an organization is following.
The compliance check audit is an important and necessary feature required as per the current security needs of an organization. All security-aware organizations define and implement secure configuration settings for their IT and network infrastructures to prevent them from being compromised by security threats that can be realized due to any misconfiguration. Also, such compliance requirements for security hardening and checking the implementation also arise because of regulatory requirements when a company has to adhere to different compliance regulations, such as ISO 27001 for a information security management system, HIPAA for the health industry, and SOX for a financial domain.
To check the compliance of servers, network devices against these defined controls, or a secure configuration, a regular compliance check activity is required. Conducting such compliance checks manually, especially when the size of the infrastructure is large, and even when post sampling and controls to be checked per device are large in number, will be a tedious and time-consuming job. This may also result in the possibility of errors and time consumed in a to-and-fro exchange between operation and compliance teams for the preparation, validation, and correction of artifacts.
The compliance check option offered by Nessus will help to conduct such a check in an automated manner. Nessus also offers options to modify the compliance files for them to be in line with an organization's device-hardening policies.
Tip
Vulnerability Scan will typically identify well-know vulnerabilities present in the system, for which a plugin is available, and will identify missing patches.
Auditing will check the compliance of the infrastructure with the secure configuration defined in the local policy.
Resulting less vulnerabilities during a vulnerability scan doesn't mean that the system is securely configured. For example, if the password policy of an organization mandates a minimum of 10 characters because it handles sensitive information, a server might have patches updated or have relatively less vulnerabilities in the output of a VA scan conducted. This is because the server will not ensure that a password policy of 10 characters is configured. This feature is available with Nessus professional feed.
Nessus compliance checks are available for major platforms such as server OSes (Windows and Unix), databases, desktops, and network devices, as well as audit standards such as PCI DSS.
This chapter will cover the following major areas:
- Audit polices
- How to configure the Nessus compliance check policy
- Compliance reporting in Nessus
- The compliance check option for different types of infrastructures
To conduct these compliance audits, policies are available in the files with the .audit extension, which are available for different infrastructure elements such as databases, Windows, and Cisco. These audit files also contain the common checkpoints covered under well-known standards such as SOX and PCI-DSS. These files also have recommendations from well-known security governance and advisory bodies such as NIST and CERT.
These audit files can be tweaked in line with the local policy or hardening documents. Tenable offers options to download these audit files from its support site and provides documentation to understand the syntax of these files to create them with customizations as per your requirements. Tenable also offers tools to convert a Windows policy file with the .inf extension to one with the .audit extension.
To enable the use of the compliance check option, an end user first needs to click on he + Add Policy. The compliance check option is available under Policies | Plugins Preferences.
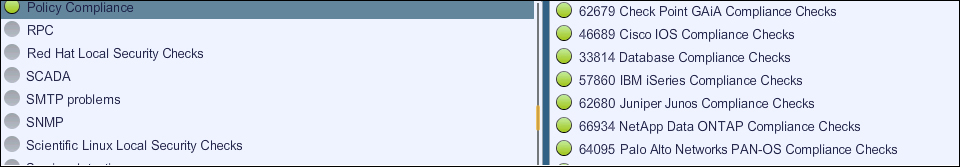
Out of the various Nessus plugins available, the plugin family of interest for a compliance check is Policy Compliance. This plugin check covers different infra components such as servers and the network.
The following screenshot shows the Policy Compliance plugin family:
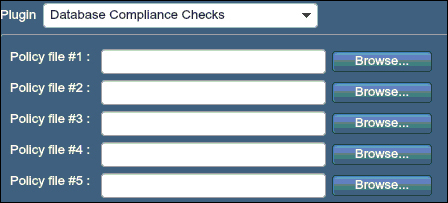
To use customized audit files, use the Preferences option under Policies. Under the Preferences tab, there is a drop-down menu to choose different compliance checks such as Cisco IOS Compliance Checks and Database Compliance Checks. Here, a user will also get an option to choose and upload more than one audit file that will be used to perform the compliance checks.
The following screenshot shows the Database Compliance Checks option selected:
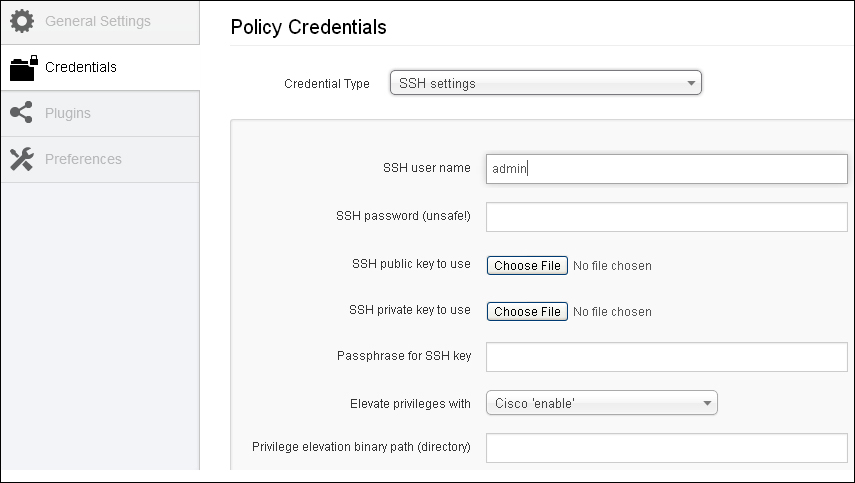
For Nessus to do a compliance check, credentials should be provided for it to log in to the system to do local checks. The credentials used should be those of a privileged account, that is, a super user privilege in case of a Unix account with administrative privilege to read the local machine policy. In case of a database compliance check, database credentials will be required. In case of a Cisco IOS compliance check, the enable password is required to do a configuration audit. The credentials can be added under Policies | Credentials as it was done during the VA scanning.
The following screenshot is an example of how to provide credentials in case of a Cisco configuration audit: