OWASP ZAP (Zed Attack Proxy) is a very versatile tool for web security testing. It has a proxy, passive and active vulnerability scanners, fuzzer, spider, HTTP request sender, and some other interesting features. In this recipe, we will use the recently added "Forced Browse", which is the implementation of DirBuster inside ZAP.
For this recipe to work, we need to use ZAP as a proxy for our web browser:
- Start OWASP ZAP and, from the application's menu, navigate to: Applications | Kali Linux | Web Applications | Web Application Fuzzers | owasp-zap.
- In Mantra or Iceweasel, go to the main menu and navigate to Preferences | Advanced | Network, in Connection click on Settings…
- Chose a Manual proxy configuration and set
127.0.0.1as the HTTP proxy and 8080 as the port. Check the option to use the same proxy for all protocols and then click on OK.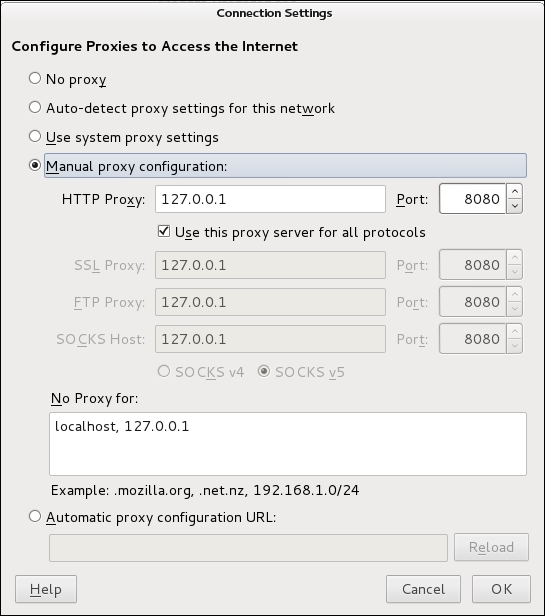
- Now, we need to tell ZAP the file where it is going to get the directory names from. Go to ZAP's menu and navigate to Tools | Options | Forced Browse and then click on Select File…
- Kali Linux includes some word lists. We will be using one of them: select the file
/usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-small.txtand click on Open.
- An alert will tell us that the file was installed. Click on OK and on OK again to leave the Options dialog.
- Having configured the proxy properly, browse to
http://192.168.56.102/WackoPicko. - We will see ZAP reacting to this action by showing the tree structure of the host we just visited.

- Now, in ZAP's upper-left panel (the Sites tab) right-click on the
WackoPickofolder inside thehttp://192.168.56.102site. Then in the context menu navigate to Attack | Forced Browse directory:
- In the bottom panel, we will see that the Forced Browse tab is displayed. Here we can see the progress of the scan and its results:

When we configure our browser to use ZAP as a proxy, it doesn't send the requests directly to the server that hosts the pages we want to see but rather to the address we defined, in this case the one where ZAP is listening. Then ZAP forwards the request to the server but not without analyzing the information we sent.
ZAP's Forced Browse works the same way DirBuster does; it takes the dictionary we configured and sends requests to the server, as if it was trying to browse to the files in the list. If the files exist the server will respond accordingly, if they don't exist or aren't accessible by our current user, the server will return an error.
Another very useful proxy included in Kali Linux is BurpSuite. It also has some very interesting features; one that can be used as an alternative for the Forced Browse we just used is Burp's Intruder. Although it is not specifically intended for that purpose, it is a versatile tool worth checking.
