In recent years, the development of graphics cards has evolved enormously, the chips they include now have hundreds or thousands of processors inside them and all of them work in parallel. This, when applied to password cracking, means that, if a single processor can calculate ten thousand hashes in a second, one GPU with a thousand cores can do ten million. That means reducing cracking times by a thousand or more.
Now we will use Hashcat in its GPU version to crack hashes by brute force. If you have Kali Linux installed on a computer with an Nvidia chip, you will need cudaHashcat. If it has an ATI chip, oclHashcat will be your choice. If you have Kali Linux on a virtual machine, GPU cracking may not work, but you can always install it on your host machine, there are versions for both Windows and Linux.
In this recipe, we will use oclHashcat, there is no difference in the use of the commands between that and cudaHashcat, although ATI cards are known to be more efficient for password cracking.
You need to be sure you have your graphics drivers correctly installed and that oclHashcat is compatible with them so you need to do the following:
- Run
oclHashcatindependently, it will tell you if there is a problem:oclhashcat - Test the hashing rate for each algorithm it supports in benchmark mode:
oclhashcat --benchmark - Depending on your installation, oclHashcat may need to be forced to work with your specific graphics card:
oclhashcat --benchmark --force
We will use the same hashes file we used in the previous recipe.
There have been some troubles reported on the default oclHashcat Kali Linux installation so, if you have problems running oclHashcat, you can always download the latest version from its official page and run it right from where you extract the archive (http://hashcat.net/oclhashcat/).
- We will first crack a single hash, let's take admin's hash:
oclhashcat -m 0 -a 3 21232f297a57a5a743894a0e4a801fc3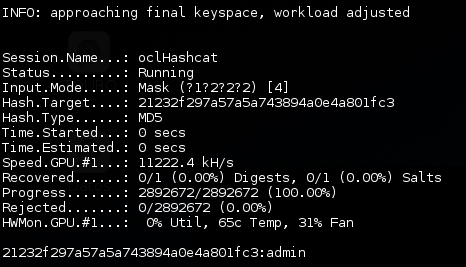
As you can see, we are able to set the hash directly from the command line and it will be cracked in less than a second.
- Now, to crack the whole file, we need to eliminate the usernames from it and leave only the hashes, as shown:

We have created a new file containing only the hashes.
- To crack the hashes from a file, we just replace the hash for the file name in the previous command:
oclhashcat -m 0 -a 3 hashes_only_6_7.txt
As you can see, it covered all the possible combinations of one to seven characters (at a rate of 688.5 million hashes per second) in less than three minutes and would take a little more than two hours to test all the combinations of eight characters. That seems pretty good for brute force.
The parameters we used to run oclHashcat in this recipe were the ones defining the hashing algorithm to be used: -m 0 tells the program to use MD5 to hash the words it generates and the type of attack. -a 3 means that we want to use a pure brute force attack and try every possible character combination until arriving at the password. Finally, we added the hash we wanted to crack in the first case and the file containing a collection of hashes in the second case.
oclHashcat can also use a dictionary file and make a hybrid attack (brute force plus dictionary) to define which character sets to test for and save the results to a specified file (it saves them to /usr/share/oclhashcat/oclHashcat.pot). It can also apply rules to words and use statistical models (Markov chains) to increase the efficiency of the cracking. To see all its options, use the --help command, as shown:
oclhashcat --help
