When testing a web application, we will need to interact with the browser's address bar, add and change parameters, and alter the URL. Some server responses will include redirects, reload, and parameter changes; all these alterations make the task of trying different values for the same variable very time consuming; we need some tool to make them less disruptive.
Hackbar is a Firefox add-on that behaves like an address bar but is not affected by redirections or other changes caused by the server's response, which is exactly why we need to begin testing a web application.
In this recipe, we will use Hackbar to easily send multiple versions of the same request.
If you are not using OWASP Mantra, you will have to install the Hackbar add-on to your version of Firefox.
- Browse to Damn Vulnerable Web Application (DVWA) and log in. The default user/password combination is:
admin/admin. - From the menu on the left, select SQL Injection.

- Enter a number in the User ID text box and click on Submit.
Now we show Hackbar by pressing F9 or clicking on the icon
 :
:
Hackbar will copy the URL and its parameters. We can also enable the option of altering the POST requests and Referrer parameter, which is the one that tells the server about the URL from which the page was requested.
- Let's make a simple modification, change the
idparameter's value from 1 to 2 and click on Execute or use the key combination Alt + X:
We can see that the
idparameter corresponds to the textbox in the page, so, using the Hackbar we can try any value by modifyingidinstead of changing the User ID in the text box and submitting it. This comes in handy when testing a form with many inputs or that redirects to other pages depending on the inputs. - We replaced one valid value with another, but what will happen if we introduce an invalid one as
id? Try introducing an apostrophe asid: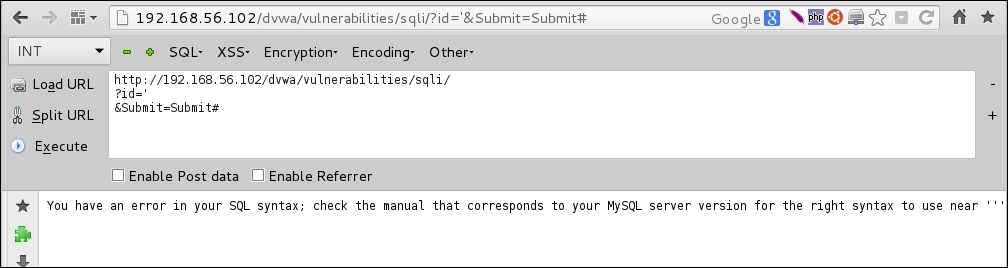
By introducing a character not expected by the application, we provoked an error in it; this will prove useful later when we test for some vulnerabilities.
Hackbar acts as a second address bar with some useful features, such as not being affected by URL redirections and allowing the modification of POST parameters.
Also, Hackbar gives us the possibility to add SQL Injection and cross-site scripting code snippets to our requests and to hash, encrypt, and encode inputs. We will go more deep into SQL Injection, cross-site scripting, and other vulnerabilities in the later recipes in this chapter.
