File inclusion vulnerabilities occur when developers use request parameters, which can be modified by users to dynamically choose what pages to load or to include in the code that the server will execute. Such vulnerabilities may cause a full system compromise if the server executes the included file.
In this recipe, we will test a web application to discover if it is vulnerable to file inclusions.
- Log into DVWA and go to File Inclusion.
- It says that we should edit the get parameters to test the inclusion. Let's try this with
index.php.
It seems that there is no
index.phpfile in that directory (or it is empty), maybe this means that a local file inclusion (LFI) is possible. - To try the LFI, we need to know the name of a file that really exists locally. We know that there is an
index.phpin the root directory of DVWA, so we try a directory traversal together with the file inclusion set../../index.phpto the page variable.
With this we demonstrate that LFI is possible and a directory traversal too (using the
../../, we traverse the directory tree). - The next step is to try a remote file inclusion; including a file hosted on another server instead of a local one, as our test virtual machine does not have Internet access (or it should not have rather, for security reasons). We will try including a local file with the full URL, as if it were from another server. We will also try to include Vicnum's main page by giving the URL of the page as a parameter on
?page=http://192.168.56.102/vicnum/index.htmlas shown below: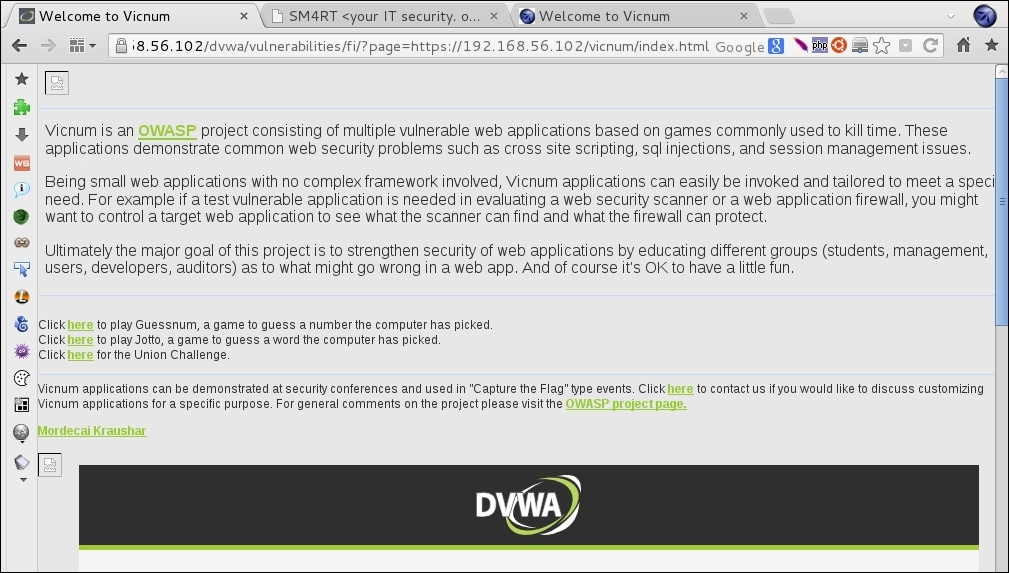
We were able to make the application load a page by giving its full URL, this means that we can include remote files; hence, it's a Remote File Inclusion (RFI). If the included file contains server-side executable code (PHP, for example), such code will be executed by the server; thus, allowing an attacker a remote command execution and with that, a very likely full system compromise.
If we use the View Source button in DVWA, we can see that the server-side source code is:
<?php $file = $_GET['page']; //The page we wish to display ?>
This means that the page variable's value is passed directly to the filename and then it is included in the code. With this, we can include and execute any PHP or HTML file in the server we want, as long as it is accessible to it through the network. To be vulnerable to RFI, the server must have allow_url_fopen and allow_url_include in its configuration, otherwise it will only be a local file inclusion, if file inclusion vulnerability is present.
