Wmap is not a vulnerability scanner by itself. It is a Metasploit module that uses all the Web-vulnerability and Web-server related modules in the framework and coordinates their loading and execution against the target server. Its results are not presented as a report but as entries to Metasploit's database.
In this recipe, we will use Wmap to look for vulnerabilities in our vulnerable_vm and check the results using Metasploit console commands.
Before we run the Metasploit console, we need to start the database server that it connects to, to save the results we generate:
service postgresql start
- Start a terminal and run the Metasploit console:
msfconsole - Once it loads, load the Wmap module:
load wmap - Now, we add a site to Wmap:
wmap_sites -a http://192.168.56.102/WackoPicko/ - If we want to see the registered sites:
wmap_sites -l - Now, we set that site as a target for scanning:
wmap_targets -d 0 - If we want to check the selected targets we may want to use:
wmap_targets -l
- Now, we run the test:
wmap_run -e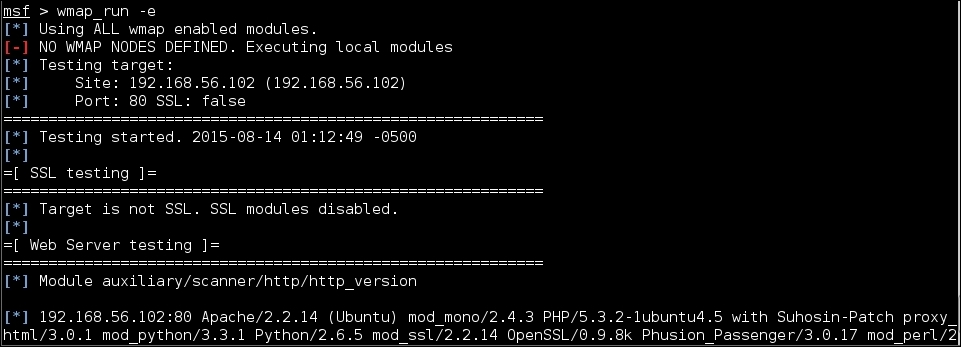
- We will have to use Metasploit's commands to check recorded vulnerabilities:
vulns wmap_vulns

Wmap uses Metasploit's modules to scan for vulnerabilities in target applications and servers. It gets information about sites from Metasploit's database and modules send their results to that database. A very useful aspect of this integration is that if we are performing a penetration test on multiple servers and are using Metasploit in this test, Wmap will automatically get all the Web servers' IP addresses and known URLs and integrate them as sites so that when we want to run a Web assessment, we only have to choose targets from the sites list.
When executing wmap_run, we can select which modules we execute by using the -m option and a regular expression; for example, the next command line will enable all modules except the ones that contain dos, which means no denial of service tests:
wmap_run -m ^((?!dos).)*$
Another useful option is -p, it allows us to select, by regular expressions, the paths we want to test. For example, in the next command, we will check all URLs that include the word login:
wmap_run -p ^.*(login).*$
Finally, if we want to export our scan results, we can always use the database features in Metasploit; for example, exporting the full database to a XML file is done using the following command in an msf console:
db_export -f xml /root/database.xml
