Burp Suite's Intruder has the ability to perform fuzzing and bruteforce attacks against as many parts of an HTTP request as we want to; it is particularly useful when performing dictionary attacks against login pages.
In this recipe, we will use Burp Suite's Intruder with the dictionary we generated in Chapter 2, Reconnaissance, to gain access through a login.
Having a password list is necessary for this recipe, it can be a simple word list from the language the target is in, a list of the most common passwords, or the list we generated in the Using John the Ripper to generate a dictionary recipe in Chapter 2, Reconnaissance.
- The first step is to set up Burp Suite as a proxy to our browser.
- Browse to
http://192.168.56.102/WackoPicko/admin/index.php. - We will see a login page; let's try and test for both username and password.
- Now go to the proxy's history and look for the POST request we just made with the login attempt.

- Right-click on it and select Send to intruder, from the menu.
- The intruder tab will get highlighted, let's go to it and then to the Positions tab. Here, we will define what parts of the request will be used for testing.
- Click on Clear § to clear the pre-selected areas.
- Now, we have to select what to use as test inputs. Highlight the value of the username (the test word) and click on Add §:
- And do the same for the value of the password and select Cluster bomb, as the attack type:

- The next step is to define the values that Intruder is going to test against the inputs we selected. Go to the Payloads tab.
- Using the text box that says Enter a new item and the Add button, fill the list with the following:
user john admin alice bob administrator user
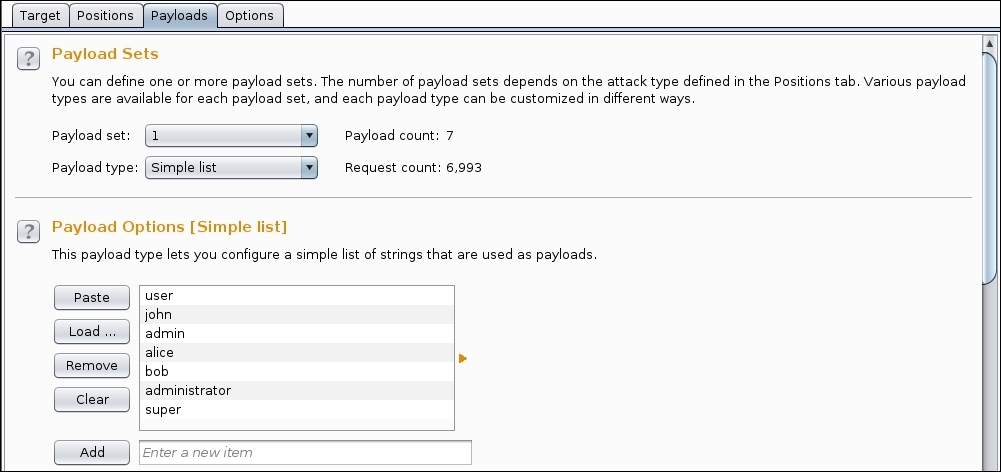
- Now select list 2 from the Payload Set box.
- We will fill this list using our dictionary. Click on Load … and select the dictionary file.
- We now have two of our payload sets loaded and are ready to attack the login page. In the top menu, navigate to Intruder | Start attack.
- If we use the free version, an alert will tell us that some functionality has been disabled. For this case, we can do without that functionality. Click OK.
- A new window will pop up showing the progress of the attack. To distinguish a successful login, we will check the length of the response. Click on the Length column to sort the results and make the identification of a response with different lengths easier.
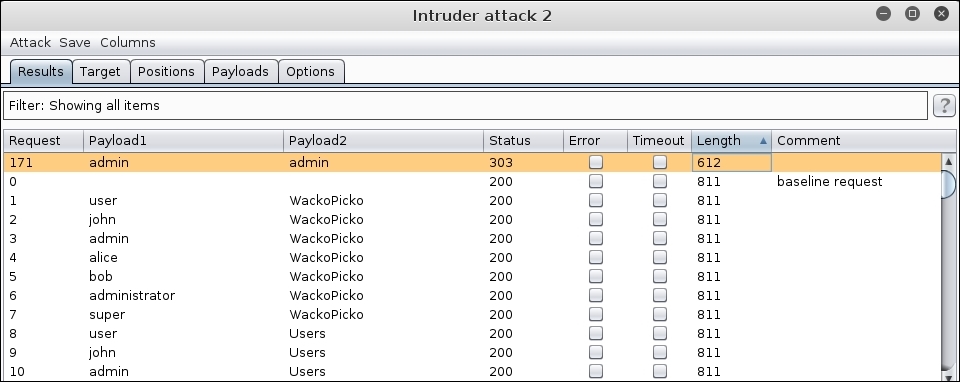
- If we check the result that has a different length, we can see that it is a redirection to the admin's index page, as shown in the following screenshot:

What Intruder does is, it modifies a request in the specific positions we tell it to, and it replaces the values in those positions with the payloads defined in such sections. Payloads may be, among other:
- Simple list: A list that can be taken from a file, pasted from the clipboard, or written down in the textbox.
- Runtime file: Intruder can take the payload from a file being read in runtime, so if the file is very large, it won't be loaded fully into memory.
- Numbers: Generates a list of numbers that may be sequential or random and presented in a hexadecimal or decimal form.
- Username generator: Takes a list of e-mail addresses and extracts possible usernames from it.
- Bruteforcer: Takes a character set and uses it to generate all the permutations inside the specified length limits.
These payloads are sent by Intruder in different ways, which are specified by the attack type in the Positions tab. Attack types differ in the way the payloads are combined and permuted in the payload markers:
- Sniper: With a single set of payloads, it places each payload value in every marked position one at a time.
- Battering ram: Similar to Sniper, it uses one set of payloads, the difference is that it sets the same value to all positions, on each request.
- Pitchfork: Uses multiple payload sets and puts one item of each set in each marked position. Its useful when we have predefined sets of data that should not be mixed; for example, testing already known username/password pairs.
- Cluster bomb: Tests multiple payloads one against the other so that every possible permutation is tested.
As for the results, we can see that all the failed login attempts get the same response, one that is 811 bytes long in this case; so we suppose that a successful one would have to be different in length (as it will have to redirect or send the user to her home page). If it happens that successful and failed requests are the same length, then we can also check the status code or use the search box to look for some specific patterns in response.
Kali Linux includes a very useful collection of password dictionaries and wordlists in /usr/share/wordlists. Some files we will find there are:
rockyou.txt: RockYou.com was hacked on December 2010; more than 14 million passwords were leaked and this list contains them.dnsmap.txt: Contains common subdomain names, such as intranet, ftp, or www; it is useful when we are bruteforcing a DNS server../dirbuster/*: Thedirbusterdirectory contains names of files commonly found on web servers; these files can be used when using DirBuster or OWASP-ZAP's Forced Browse../wfuzz/*: Inside this directory, we can find a large collection of fuzzing strings for web attacks and brute forcing files.
