As seen in the previous recipe, exploiting SQL Injections may be an industrious process. SQLMap is a command-line tool, included in Kali Linux, which can help us in the automation of detecting and exploiting SQL Injections with multiple techniques and in a wide variety of databases.
In this recipe, we will use SQLMap to detect and exploit an SQL Injection vulnerability and will obtain usernames and passwords of an application with it.
- Go to
http://192.168.56.102/mutillidae. - In Mutillidae's menu, navigate to OWASP Top 10 | A1 – SQL Injection | SQLi Extract Data | User Info.
- Try any username and password, for example
userandpasswordand then click on View Account Details. - The login will fail but we are interested in the URL; go to the address bar and copy the full URL to the clipboard.
- Now, in a terminal window, type the following command:
sqlmap -u "http://192.168.56.102/mutillidae/index.php?page=user-info.php&username=user&password=password&user-info-php-submit-button=View+Account+Details" -p username --current-user --current-dbYou can notice that the
-uparameter has the copied URL as a value. With-pwe are telling SQLMap that we want to look for SQL Injections in the username parameter and the fact that we want it to retrieve the current database username and database's name once the vulnerability is exploited. We want to retrieve only these two values because we want to only tell if there is an SQL Injection in that URL in the username parameter.
- Once SQLMap detects the DBMS used by the application, it will ask if we want to skip the test for other DBMSes and if we want to include all the tests for the specific system detected, even if they are out of the scope of the current level and risk configured. In this case, we answer
Yesto skip other systems andNoto include all tests. - Once the parameter we specified is found to be vulnerable, SQLMap will ask us if we want to test other parameters, we will answer No to this question, and then see the result:

- If we want to obtain the usernames and passwords, similar to how we did in the previous recipe, we need to know the name of the table that has such information. Execute the following command in the terminal:
sqlmap -u "http://192.168.56.102/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details" -p username -D nowasp --tables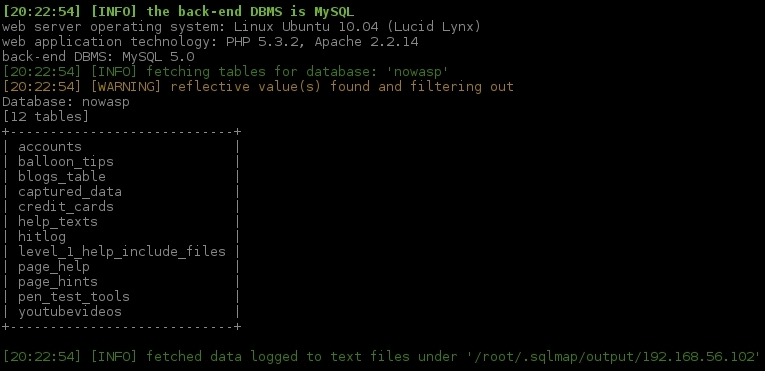
SQLMap saves a log of the injections it performs, so this second attack will take less time than the first one. As you can see, we are specifying the database from which we will extract this information (nowasp) and telling SQLMap that we want a list of tables in such database.
- The
accountstable is the one that has the information we want. Let's dump its contents:sqlmap -u "http://192.168.56.102/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details" -p username -D nowasp -T accounts --dump
We now have the full users' table and we can see that in this case passwords aren't encrypted, so we can use them right as we see them.
SQLMap fuzzes all the inputs in the given URL and data, or only the specified one in the -p option with SQL Injection strings and interprets the response to discover if there is a vulnerability or not. It's a good practice not to fuzz all inputs, it's better to use SQLMap to exploit an injection that we already know exists and always try to narrow the search process by providing all the information available to us, such as vulnerable parameters, DBMS type, and others. Looking for an injection with all the possibilities open could take a lot of time and generate a very suspicious traffic in the network.
In this recipe, we already knew that the username parameter was vulnerable to SQL Injection (since we used the SQL Injection test page from Mutillidae). In the first attack, we only wanted to be sure that there was an injection there and asked for some very basic information: user name (--curent-user) and database name (--current-db).
In the second attack, we specified the database we wanted to query with the -D option and the name obtained from the previous attack, and we also asked for the list of tables it contains with --tables.
After knowing what table we wanted to get (-T accounts), we told SQLMap to dump its contents with --dump.
SQLMap can also inject input variables in POST requests, to do that we only need to add the option --data followed by the POST data inside quotes, for example:
--data "username=test&password=test"
Sometimes, we need to be authenticated in some application in order to have access to the vulnerable URL of an application; if this happens, we can pass a valid session's cookie to SQLMap using the --cookie option:
--cookie "PHPSESSID=ckleiuvrv60fs012hlj72eeh37"
This is also useful to test for injections in cookie values.
Another interesting feature of this tool is that it can bring us an SQL shell where we can issue SQL queries, as if we were connected directly to the database using the --sql-shell; option or, more interesting, we could gain command execution in the database server using --os-shell (this is especially useful when injecting Microsoft SQL Server).
To know all the options and features that SQLMap has, you can run:
sqlmap --help
Kali Linux includes other tools that are capable of detecting and exploiting SQL Injection vulnerabilities that might be useful to use instead of or in conjunction with SQLMap:
- sqlninja: A very popular tool dedicated to MS SQL Server exploitation
- Bbqsql: A blind SQL injection framework written in Python
- jsql: A Java based tool with a fully automated GUI, we just need to introduce the URL and click a button
- Metasploit: It includes various SQL Injection modules for different DBMSes
