In the previous recipe and in Chapter 6, Exploitation – Low Hanging Fruits, we extracted password hashes from databases. Sometimes, this is the only way of finding password information when performing penetration tests. In order to find the real password, we need to decipher them and as hashes are generated through irreversible algorithms we have no way of decrypting the password directly, hence it is necessary to use slower methods like brute force and dictionary cracking.
In this recipe, we will use John the Ripper (JTR or simply John), the most popular password cracker, to recover passwords from the hashes extracted in the Step by step basic SQL Injection recipe in Chapter 6, Exploitation – Low Hanging Fruits.
- Although JTR is very flexible with respect to how it receives input, to prevent misinterpretations, we first need to set usernames and password hashes in a specific format. Create a text file called
hashes_6_7.txtcontaining one name and hash per line, separated by a colon (username:hash), as illustrated:
- Once we have the file, we can go to a terminal and execute the following command:
john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5 hashes_6_7.txt
We are using one of the word lists preloaded into Kali Linux. We can see that there are five out of six passwords in the word list. We can also see that John checked 10,336,000 comparisons per second (10,336 KC/s).
- John also has the option to apply modifier rules — add prefixes or suffixes, change the case of letters, and use leetspeak on every password. Let's try it on the still uncracked password:
john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5 hashes_6_7.txt –rules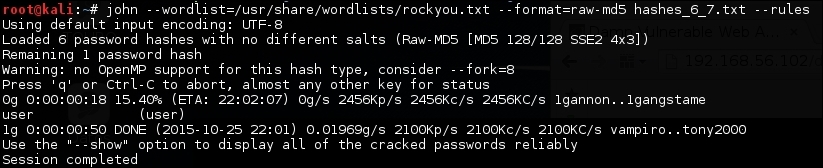
We can see that the rules worked and we found the last password.
John (and every other offline password cracker) works by hashing the words in the list (or the ones it generates) and comparing them to the hashes to be cracked and, when there is a match, it assumes the password has been found.
The first command uses the --wordlist option to tell John what words to use. If it is omitted, it generates its own list to generate a brute force attack. The --format option tells us what algorithm was used to generate the hashes and if the format has been omitted, John tries to guess it, usually with good results. Lastly, we put the file that contains the hashes we want to crack.
We can increase the chance of finding passwords by using the --rules option because it looks at common modifications people make to words when trying to create harder passwords to crack. For example, for the word "password", John will also try the following, among others:
PasswordPASSWORDpassword123Pa$$w0rd
