Ettercap can detect when relevant information such as passwords is transmitted through it. However, it is often not enough to intercept a set of credentials when performing a penetration test, we might be looking for other information like credit card numbers, social security numbers, names, pictures, or documents. It is therefore useful to have a tool that can listen to all the traffic in the network so that we can save and analyze it later; this tool is a sniffer and the best one for our purposes is Wireshark and it is included in Kali Linux..
In this recipe, we will use Wireshark to capture all the packets sent between the client and the server in order to obtain information.
- Run Wireshark from the middle of the Windows client and
vulnerable_vmfrom Kali's Applications menu | Sniffing & Spoofing or from the terminal run:wireshark
- When Wireshark loads, select the network interface you want to capture packets from. We will use
vboxnet0, as shown:
- Then click on Start. You will immediately see Wireshark capturing ARP packets, that's our attack.
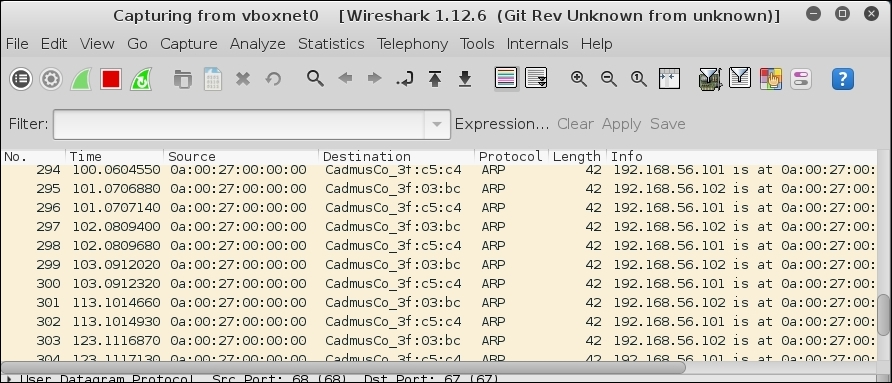
- Now, go to the client virtual machine and browse to
http://192.168.56.102/dvwaand log in to DVWA. - In Wireshark, look for a HTTP packet from 192.168.56.101 to 192.168.56.102 with POST
/dvwa/login.phpin itsinfofield.
If we look through all the captured packets, we will find the one corresponding to the authentication and see that it was sent in clear text so we can get the username and password from there.
If we look at the Ettercap's window we can also see the username and password there, as shown:

By capturing traffic between the client and the server, an attacker is able to extract and use all kinds of sensitive information such as usernames and passwords, session cookies, account numbers, credit card numbers, privileged e-mails, and many others.
Wireshark listens to every packet that the interface we selected to listen receives and puts it in readable form in its interface. We can select to listen from multiple interfaces.
When we first started the sniffing, we learned how the ARP spoofing attack works. It sends a lot of ARP packets to the client and the server in order to prevent their address resolution tables (ARP tables) from getting the correct values from the legitimate hosts.
Finally, when we made a request to the server, we saw how Wireshark captured all the information contained in that request, including the protocol, the source and the destination IP; more importantly, it included the data sent by the client, which included the administrator's password.
Studying Wireshark data is a little tiresome so it is very important to learn how to use display filters when capturing packets. You can go to the following sites to learn more:
With Wireshark, you can select which kind of data is captured by using capture filters. This is a very useful feature, especially when performing a MITM attack due to the amount of traffic being generated. You can read more about this on the following sites:
