The information that is required to make decisions is prioritized based on what goal or milestone needs to be reached. Think about everything that we've learned so far about the intelligence cycle. Once strategic priorities have been identified, they are passed down to the Tactical Level for prioritization. After the Tactical Level priorities are defined, they are passed down to the operational teams to tackle. The prioritized items at each level can be considered targets that need to be reached to gain information for action or establish a capability.
The US military has used a targeting process to provide steps for actions against an enemy:
- Find a target by identifying it and locating it
- Fix-ate on the target so that they know its whereabouts
- Finish a target (capture or kill) with assigned resources
- Exploit information gathered during the mission from available sources
- Analyze information to find additional targets to take action on
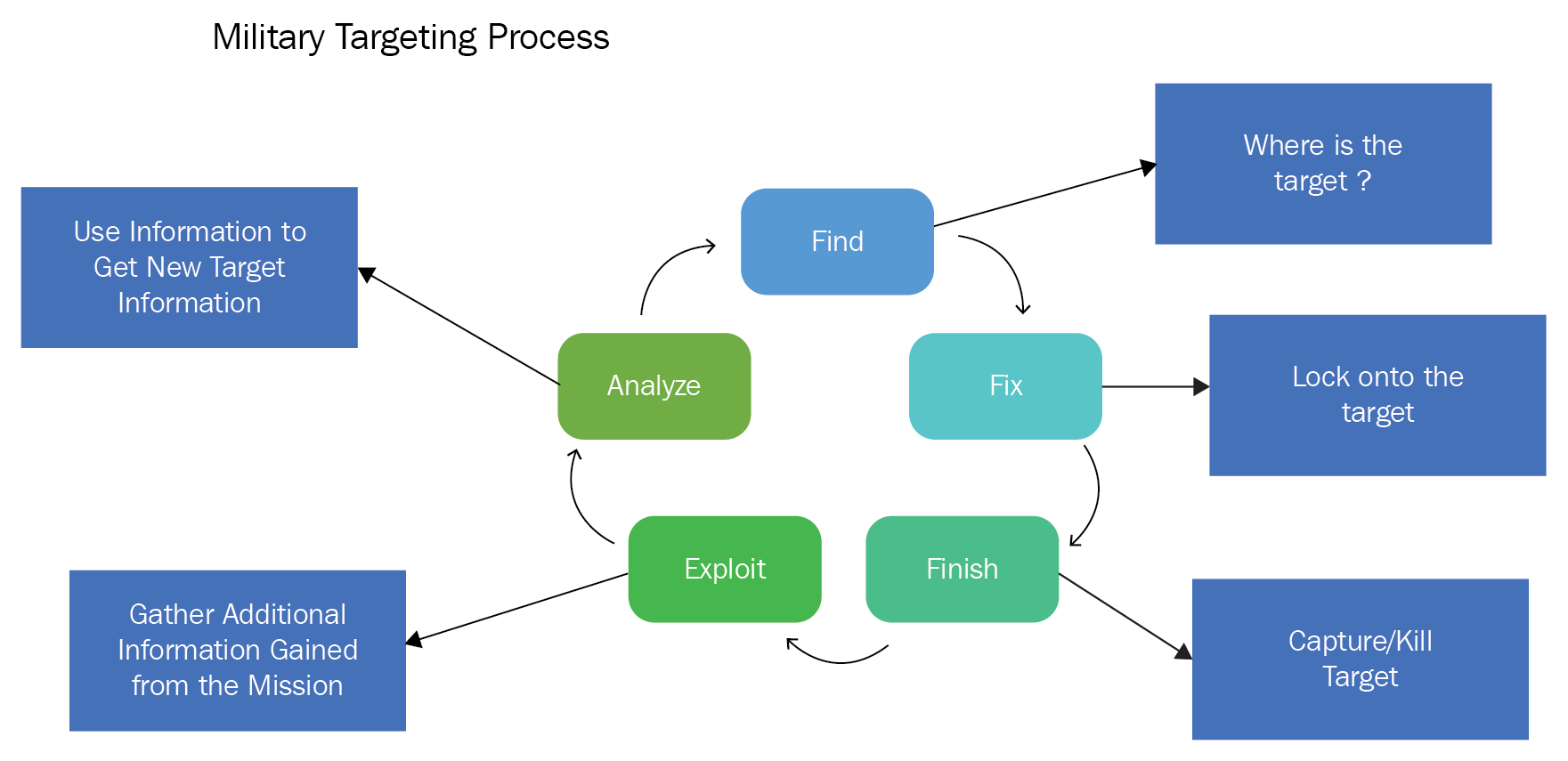
Although there can be similarities, the definition of targets for the military, and the definition for businesses is different. In the military, the objective may be to capture or kill a high-value target or high-value individual. Of course, this does not entirely translate between the two worlds. However, we can put them into items that we can understand in the business world.
An example of how the business world sets targets is by using an acronym called S.M.A.R.T.:
- Specific: Defines what needs to be achieved
- Measurable: Establishes a metric for progress
- Assignable: Attributes who is responsible for the objective
- Relevant/realistic: Ensures that the target is achievable and pertinent to the organization
- Time limited: Specifies the date when it will be completed
Here are some business target examples:
- Budgets: The amount of funds that an organization has to complete a task (or series of tasks) for development, operations, or maintenance:
- Project to be completed at or under budget spend
- Funds allocated to operations must not go over X dollar amount per quarter
- Project milestone: An achievement within a project that takes place at a predetermined time:
- Milestone A is complete when all deliverables are presented to the stakeholder for review at the end of the 3rd quarter
- Milestone B is complete when all deliverables are accepted by the stakeholder at the end of the 4th quarter
- Project deliverable: A product, capability, or result that provides value to a customer at the end of a project
- Key Performance Indicators: A quantifiable measurement that is used to gauge the performance of a process, capability, and so on to meet key business objectives:
- Decrease the total average of HIGH severity vulnerabilities to 5 per system
- Initial contact for all MEDIUM category helpdesk tickets is within 24 hours
- Software testing metrics:
- Decrease the number of defects found
- Decrease the number of defects accepted
- Decrease the number of defects rejected
- Decrease the number of defects deferred
- Total number of test cases
- Key risk indicators: A measurement that conveys the early signs that certain activities or areas are increasing or decreasing in risk:
- The baseline remediation time for incidents must be 5 days over a 3-month period, provide a warning to X personnel if average remediation time for an incident is 7 days over a 1-month period
- Risk levels: A measurement based on the product of impact and probability:
- Due to the legacy equipment and systems used to build our widgets, we must meet a low-risk rating for the Z application through mitigating controls
To better understand how we can apply the targeting process, we will use the target of a quarterly budget as an example:
- Find:
- First, we need to establish an annual budget
- Without this information, we will not be able to continue planning
- Fix:
- Once we have our annual budget, we can divide it equally for each quarter
- This information will help us understand our spending limits per quarter
- Finish:
- We will need to monitor and control our expenditures to ensure that we do not go over what we've allocated for each quarter
- Once the quarter is complete, we can now begin to look at the information that we've gathered
- Exploit:
- We can now look at the information and begin to ask some questions:
- Did we spend more than we anticipated?
- Did we spend exactly what we expected?
- Did we spend less than we anticipated?
- We can now look at the information and begin to ask some questions:
- Analyze:
- We can now start addressing new targets for the next quarter:
- If we were under budget, where can we use extra funds to provide value?
- If we were over budget, where can we decrease resources to ensure that we don't follow the same path in the current quarter?
- We can now start addressing new targets for the next quarter:

Understanding the difference between the application of this version of the targeting process between military and commercial is essential in that the term target can be applied to several things non-military related. For our purposes, we want to be able to target the capabilities that enable cyber intelligence throughout the organization. By filtering the priorities of information to be collected, Operational Level teams can begin the targeting process to provide the information as required as well as build the capability between teams to communicate cyber intelligence.
