Rachel was a friend that was asked by a CISO to solve a problem. At the time, her marching orders were simple. Identify vulnerabilities and report vulnerabilities. But she wondered, what does identifying and reporting vulnerabilities solve? It doesn't solve anything. She had identified a problem but there was no means to solve it. Why? She was in a huge environment stretching across the globe that required change requests to be put in and multiple entities to sign off on a single patch.
Let's not even talk about the sheer amount of patches that needed to be reviewed and approved by non-technical staff, or the fear of impacting operations. There isn't a simple solution for this problem as there were other dependencies and unknowns, such as vendors and shadow IT. Her team did not have the ability to patch, which was a huge problem. It was difficult to get anything done. There was an organizational culture change that needed to be addressed. There were policies and procedures that needed to be updated. There were multiple problems in security that need to be prioritized. There were organizational changes, personnel moves, people leaving, people on-boarded, that is, more dependencies.
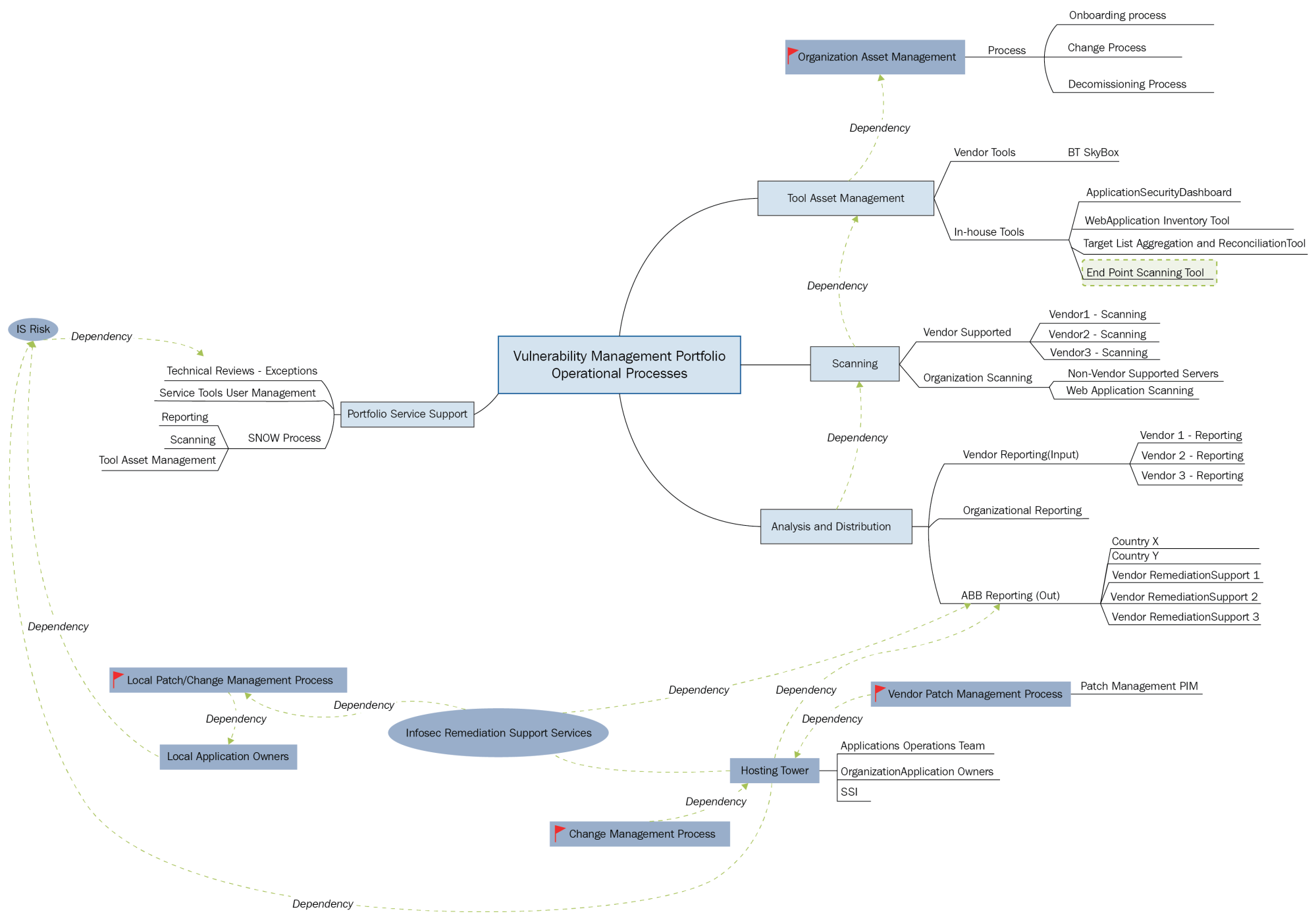
Maybe a single set of services look like the preceding mind map. The IT operations and IT security operations in the organization were a complex beast. But this was just a small problem in the bigger picture.
The real question was, how does your piece of the pie keep this organization safe? Well, her piece of the pie didn't keep her organization safe. The reality was that she had a team that highlighted known vulnerabilities and provided inputs to a risk metric that was presented on a global risk dashboard. On this dashboard were other security teams' pieces of the pie. A dashboard that consisted of red, amber, and green. The more red there was meant the more you were going to be harassed. More green meant that you weren't going to be harassed. Sound familiar?
Does more green really mean that you are at less risk? Does being more red really mean that you are a risk?
The data isn't complete. Maybe it told her that there are certain areas that need attention, but what this didn't tell her is where she needed to pay attention the most as a service manager. More on her story later.
I can't imagine how it would be for the CISOs or security professionals who have to manage all of this data. It's like looking at a ship and knowing all of the holes but not knowing where to plug up first, all while asking for an additional supply of corks to use to fix them, because you may have five or six. Wait! One or two corks are rotted. It's a never-ending cycle of which holes to plug up first. What gator is closest to the boat? Which fiery hoop do I jump through now?
If organizations were castles, we'd have to man the walls and keep a constant eye out for trouble. But castles get breached and it doesn't matter how big or well defended the castle is because there will always be a blind spot. Where are your security blind spots?
So how is it that companies with plenty of resources for tools and personnel still get breached? How many conferences have I been to where I've seen the next big thing in security? There are tools for cyber deception. There are tools that use artificial intelligence and machine learning. We have heuristic analysis and two-factor authentication. NextGen AV! Defense in depth! We have best practices, certifications, and bootcamps. We are manning our castles with personnel who have the best equipment and training but we've still seen major institutions get hacked left and right. Target, JP Morgan, Dun & Bradstreet, they may or may not have been compliant, but they were not secure. We know that compliance is not security. Frameworks, compliance, standards, benchmarks, and so on are all foundation references to building a program but it shouldn't be where we stop. We need to level up, change how we think and operate.
Call it DevSecOps. Call it agility. Call it synergy or collaboration. Our teams have to be as flexible and adaptable as our adversary so that we can anticipate their next moves. We can only do that by processing all of the intelligence that we receive and utilizing it to guide how we decide to protect our organizations.
