▶ 13.3 Crypto Atop the Protocol Stack
We achieve very important benefits if we apply cryptography at the very top of the application layer or even above the network protocol stack. It is much easier to develop software as an application instead of making changes to OS or networking software (FIGURE 13.15). This also provides the benefits of end-to-end crypto.
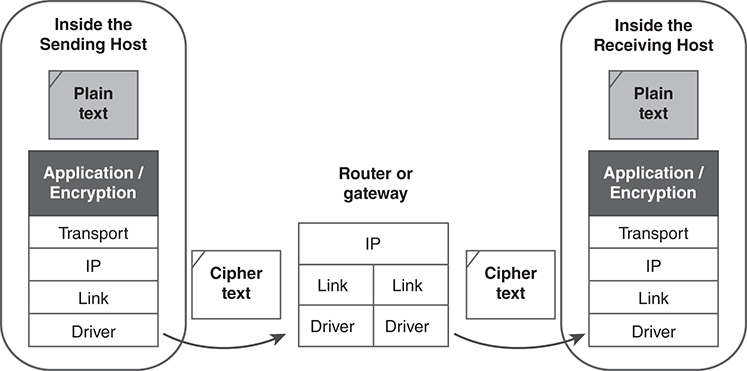
FIGURE 13.15 Application layer encryption in transit.
An important feature of encrypting above the stack is network transparency: The encryption doesn’t interfere with the network’s ability to carry the application’s traffic. Figure 13.7 shows this clearly: The packet headers are almost entirely in plaintext, although the data is in ciphertext. This allows the encrypted packets to be treated like any other internet packets. The routing headers remain comprehensible to the routers, and the TCP headers still allow reliable, orderly delivery.
Privacy-Enhanced Mail
Proposals for email encryption arose in the 1980s, often taking advantage of innovations in public-key cryptography. The prototype for end-to-end email encryption was the Privacy-Enhanced Mail (PEM) protocol. Although PEM supported mail encryption with shared secret keys, its important contribution was to use RSA public keys to wrap the secret key that encrypts a message (FIGURE 13.16).

FIGURE 13.16 Encryption and key wrapping for email to Bob.
Although PEM served as the model for internet email encryption, it was never widely used itself. The design posed challenges that discouraged its deployment. One problem was that PEM was designed around a single, centralized certification hierarchy. Every PEM email user had to have a public-key certificate issued by a PEM-approved certificate authority. Moreover, there were expenses both in issuing certificates and in licensing of RSA patent rights. RSA Data Security, the company holding the patent rights, offered to issue a certificate and license the patent to any PEM user in exchange for a $25 fee. This went counter to the prevailing customs of the internet community, at a time where most internet software was free.
Pretty Good Privacy
PGP became a de facto standard for email encryption and, in fact, for desktop encryption in general. The original software was distributed free, including its source code. Instead of relying on a hierarchical certification authority, it used the “web of trust” to provide confidence in certificate authenticity. Both the web of trust and certification hierarchies were introduced in Section 8.6.2.
Aside from PGP, there are several commercial email products that also provide encryption. Lotus Notes, the desktop email and information management product, provides email encryption and integrity protection based on RSA. Notes was, in fact, the first product to license the RSA algorithm in the 1980s. Microsoft’s Outlook Exchange email also can encrypt and sign messages.
Secure Multipurpose Internet Message Extensions (S/MIME) is an extension to existing internet email protocols that adds cryptographic protection. Both PGP and S/MIME provide open standards for email security. In addition to free and licensed products from the PGP Corporation, there are other products that implement PGP-style email, notably the Gnu Privacy Guard (GPG). S/MIME is supported by many mailers, including Mozilla’s Thunderbird.
Adoption of End-to-End Encryption
Today, the most widely used end-to-end encryption systems reside on smartphones. Apple provides end-to-end encryption on all video calls and text messages between its iOS devices. Google and Facebook also provide end-to-end encrypted messaging services. There are also messaging apps that provide end-to-end encryption, notably WhatsApp and Signal. Smartphone encryption relies on built-in smartphone security features to safely automate the key-management process.
Despite the widespread availability of email encryption software—both for free and from vendors—the overwhelming majority of email users can’t read encrypted email or verify signatures on messages they receive. Many people are resigned to the fact that they can’t transmit critical messages via email. Aside from technical experts, few people take the trouble to install secure email software and assign themselves a public-key pair.
Organizations that transmit a number of sensitive messages (like health institutions subject to HIPAA regulations) use email applications with built-in cryptographic services. The enterprise’s IT department handles software distribution and key management.
13.3.1 Transport Layer Security—SSL and TLS
When we limit ourselves to secret-key cryptography, our secure network communications must rely on preshared secrets. We clearly need secure communications if we are to transact business over the internet. The notorious internet security incidents of the late 1980s highlighted the risks to internet traffic. Because the CERT started to track security incidents at that time, subsequent incidents just underscored internet risks. In 1994, a CERT advisory on password sniffing led the national television news programs to warn “everyone” to change their internet passwords. Attackers had installed password sniffing software in major internet service providers.
The World Wide Web
As the World Wide Web evolved in the early 1990s, many observers realized that it could implement an online form of shopping by catalog. At that time, countless companies flourished by printing and distributing product catalogs on paper and by accepting orders over the phone. This early form of “online shopping” firmly established the role of credit cards in ordering products electronically.
The challenge was, of course, to keep the credit cards from leaking to thieves. Although the general public might have let a news report on internet security pass either unheard or misunderstood, those familiar with the internet knew better than to risk sensitive data to potential sniffing. Safe and secure internet shopping required confidentiality for the credit card numbers.
Originally, the World Wide Web was text-oriented. The developer, Tim Berners-Lee, was a physicist who developed the technology as a way to publish technical papers and to provide built-in cross-references between related papers. Developers at the National Center for Supercomputer Applications at the University of Illinois realized that they could easily incorporate images into the text-only documents. Most of the changes were in the browser software that displayed the document on the client computer. Their browser, called Mosaic, appealed to nontechnical computer users.
Netscape Software
In 1994, Mosaic’s developers joined a private company named Netscape Communications to develop a secure browser and web server. The Netscape Commerce Server provided companies with a way to sell products on the internet and safely collect credit card numbers. The browser, called Netscape Navigator (FIGURE 13.17), used SSL to establish a secure connection across the internet.

FIGURE 13.17 Netscape Navigator software.
© AOL Inc.
Netscape provided the RSA patent holders with 1 percent of the company in exchange for the rights to use RSA in the browser. In 1995, Netscape first offered its stock for sale, and the small company’s value quickly rose to more than $200 million. Netscape set the stage for overnight stock market success by many internet companies over the next several years.
Secure Sockets Layer/Transport Layer Security
Website security measures based on SSL and TLS are arguably the world’s most widely used cryptographic mechanisms. SSL showed developers how to apply cryptography effectively without troubling end users with key management. As noted earlier, the creators of the SSL protocol no longer support it; today’s version is maintained by the IETF under the name Transport Layer Security. However, we will keep with tradition and industry convention and refer to today’s protocol as SSL.
Modern SSL supports several different cipher suites that allow selection of different public-key, one-way hash, and secret-key algorithms. Here, however, we focus on the protocols most often used in web applications.
The SSL protocol typically uses RSA to establish a secret shared between the client and server. Once SSL has established the shared secret, it uses a secret-key algorithm to protect the connection’s data. Initially, SSL simply wrapped a shared key, much as is shown in Figure 13.14; however, this proved to be vulnerable to several attacks. The modern protocol consists of three parts:
Handshake protocol: establishes the shared secret and the keys to be used to protect SSL traffic.
Record protocol: transfers information using a symmetric cipher and integrity check.
Alert protocol: indicates errors and the end of a secure session.
SSL is designed to work atop a TCP connection; it applies security to an orderly stream of bytes moving between the client and server. However, once the handshake is complete, the client and server use the same shared secret to protect a whole series of TCP connections. This relationship is called an SSL session.
In the following sections, we will examine the SSL handshake protocol and the record protocol.
13.3.2 SSL Handshake Protocol
The SSL handshake protocol uses public keys to establish a shared secret. First, the client and the server exchange randomly generated nonces. Next, they exchange temporary Diffie–Hellman public keys. They use the keys to generate a common “pre-master secret” and combine it with the nonces to produce the shared master secret. Alice uses the bank’s public-key certificate to authenticate the bank’s server and the messages it sends.
In FIGURE 13.18, Alice contacts “the Bank” to transfer some funds. To establish their SSL session, both Alice’s client and the Bank’s server generate and exchange nonces and Diffie–Hellman keys. Then they generate a shared master secret and use it to create working keys to protect their connection.
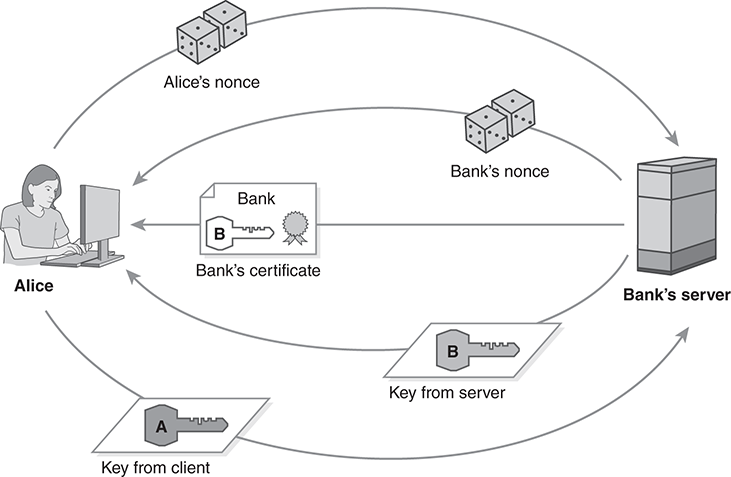
FIGURE 13.18 The SSL handshake protocol.
Originally, the SSL handshake relied entirely on RSA encryption, and this approach is still widely used. The bank’s server omits the “Key from Server” message entirely. The client generates the pre-master secret and wraps it with the bank’s public key. The “Key from Client” message transmits the wrapped pre-master secret to the server. The RSA approach requires less computation, but it sacrifices perfect forward secrecy. (See Section 8.3.1.)
The client and server also use the handshake to select the cryptographic algorithms. The server provides a list of the algorithms it supports for establishing the crypto keys (typically RSA, Diffie–Hellman, or elliptic curve Diffie–Hellman), the encryption algorithms (typically AES), and the integrity mechanisms, which may be integrated into block cipher modes.
Once both hosts have retrieved both nonces and the pre-master secret, they each hash the data to construct secret keys to use. The actual process uses a string of predefined data that is combined with the exchanged variables (FIGURE 13.19). The hash is repeated several times to produce a large key block of random data. SSL subdivides the block into separate pieces of random data for every purpose the crypto functions require.
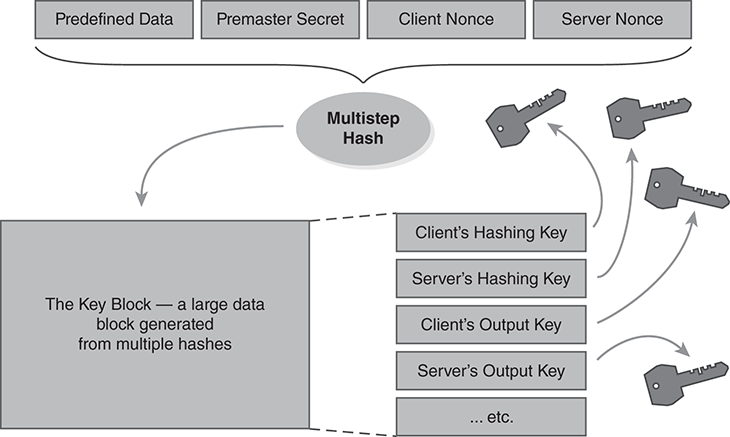
FIGURE 13.19 Constructing SSL keys through hashing.
These may include keys and data for the following six purposes:
Encrypt output from the client
Encrypt output from the server
Keyed hash of output from the client
Keyed hash of output from the server
IV (initialization vector) for output from the client, if the mode requires it
IV for output from the server, if the mode requires it
When SSL was developed originally, the designers didn’t appreciate the risk of reusing a cipher’s key stream. They used the shared secret itself as the encryption key for traffic in both directions. When the developers realized the mistake, they decided it wasn’t significantly more difficult to construct separate keys for encryption and integrity protection in each direction. Although it’s not essential to use separate keys for protecting the integrity of a keyed hash, it is often the safest course to take.
13.3.3 SSL Record Transmission
All SSL packets follow a standard format, shown in FIGURE 13.20. The layout in the figure shows the arrangement for sending encrypted data protected by a block cipher. The first three fields appear in all SSL packets; the “content type” field indicates whether the packet carries data, an alert message, or is negotiating the encryption key.
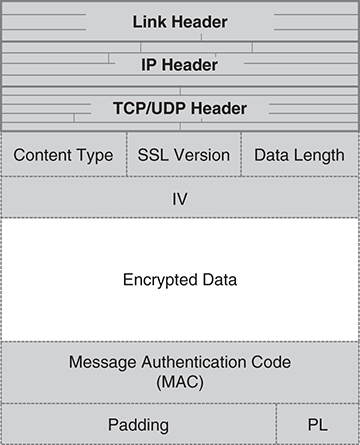
FIGURE 13.20 SSL data packet contents.
The crypto-specific fields provide the information needed to decrypt and verify the packet’s data. The first crypto parameter, the IV, is of course used with a block cipher mode. The last parameters, “padding” and “PL,” provide padding so that the encrypted data matches the block length. The PL field indicates the padding length.
Message Authentication Code
The “message authentication code” field contains the data we use to verify the message’s authenticity and integrity. We calculate the code using the types of techniques introduced earlier. (See Section 8.5.2.) The calculation always relies on a shared secret; in this case, we use one of the secrets constructed from the key block.
The acronym MAC commonly is used to refer to message authentication codes, even though it clashes with the acronym for Ethernet addresses. To keep the two distinct, the acronym “MAC” by itself will refer to an authentication code, while we will refer to Ethernet addresses as “MAC addresses.”
Modern security protocols, including SSL, often use an advanced form of MAC called the hashed MAC or HMAC. This code applies the hash twice. The first time the hash combines half of the bits in the key value with the data being protected. The second hash takes the result of the first one and hashes it with the other bits in the key value. Cryptographers have analyzed the function and found that it covers weaknesses that appear in some hash functions when used by themselves, making the MAC more effective.
Data Compression
In addition to encryption and MAC calculation, SSL also applies compression to the data. This is a systematic process that reduces the volume of data by taking advantage of redundancy in the plaintext. This reduces the amount of data encrypted and transmitted to make the overall operation more efficient.
Application Transparency and End-to-End Crypto
SSL rarely achieves true application transparency because it is usually bundled with the client or server software. However, because the protocol fits almost exactly at the network API, it isn’t hard to keep the protocol separated from the application. Some vendors even provide external hardware to perform much of the SSL processing before it arrives at the server.
However, SSL illustrates a problem with application transparency: The end user doesn’t always know whether or not the traffic is really protected. With email, we can’t read encrypted mail unless we take steps to decrypt it; some software won’t display a signed email message unless the signature is verified.
There is a sharper separation between SSL cryptography and the applications that use it. Web browsers provide indicators, like a visible padlock or key, to show when cryptography protects a page. However, this proved tricky. The browser may need to open several connections to fill a single page, and some of the connections might not be encrypted. If that happens, should it display the padlock or not?
Modern browsers often display a warning when that happens (FIGURE 13.21). The figure shows a warning from the Firefox 3 browser. The warning indicates that although some of the page contents are cryptographically protected, other contents are not protected. Also note the lower right-hand corner of the browser window: There is a very tiny padlock superimposed with an exclamation mark (!). The padlock indicates that SSL is being used, and the exclamation mark indicates that not all of the page’s contents are cryptographically protected.

FIGURE 13.21 Browser warning about incomplete page encryption.
Screenshot reprinted with permission from Apple, Inc.
Although email encryption applications may provide end-to-end crypto to users, SSL does not. In SSL, the cryptographic relationship is between a client and server application, not between end users. SSL encryption takes place automatically. Email encryption relies on the end user to apply cryptography to a message and to validate it upon receipt.
