Understanding What a Router Does
The previous sections introduced some basic concepts about routers and discussed where they might be deployed. This section presents some advanced concepts in IP routing behavior, providing examples based on the network topology presented in the first sections.
You now know that a router has a routing table containing network prefixes for IP network addresses it knows about. This section explains how a router uses its routing table to determine which interface it should forward an IP datagram over in order to send it to its destination.
IP datagrams flow through a network one router at a time. Each router in a path must make its own decision about the best interface to forward a packet over to get it to its destination. This is what is meant by hop-by-hop forwarding.
Sample Network
The sample network has been simplified for this section by removing the serial link between RouterA and RouterC. This simple network is shown in Figure 1-5.
Figure 1-5. Simplified version of the sample network.
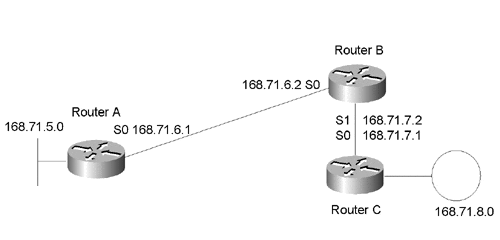
In most instances, the router forwarding a datagram does not know whether the next hop router is the final router in the chain or merely another hop in a longer chain.
In Figure 1-5, if RouterA received a packet for 168.71.8.2 (a host on the Token Ring attached to RouterC), it would simply forward the packet to RouterB. RouterA would neither know nor care that RouterB was not actually connected to 168.71.8.0 and thus would have to hand the packet off to yet another router.
As far as RouterA is concerned, the route to network prefix 168.71.8.0 is known via 168.71.6.2 over serial 0. "Known via" means that this is the IP address of the advertising router. In this case, RouterB advertised 168.71.8.0 to RouterA.
Note
Routers typically do not advertise networks back out the interface they are known via. This is called using a Split Horizon. Split Horizon is explained later in this chapter.
On a point-to-point link, such as a T1 connection, the advertising router is always the only other router on the link. On a multipoint link, such as Frame Relay, several routers may be advertising routes that arrive over a serial interface. In this case, it is imperative to store the next hop address to identify which router is advertising the routes. The multipoint example is covered later in this chapter.
Note
It is important to understand that the source and destination addresses of an IP packet never changes at it flows through the network unless the packet goes through a device that performs network address translation (NAT). NAT devices can be used when you want to connect your private network to the Internet and you do not have officially registered IP addresses configured on your network devices. At a minimum, you need one valid IP address for use on your end of the connection to your Internet Service Provider (ISP). Your NAT device will use this address as the source address for any packets generated by your end systems. This book is focused on fundamental behaviors of IP in router-based networks. NAT is not a fundamental IP concept but rather an advanced application of IP address management, so it will not be covered in any further detail. You can assume that, in the context of the materials presented in this book, all IP addresses in all IP datagrams remain unchanged as the packets traverse the network scenarios presented. See RFC 1631 for more information on NAT.
How a Router Knows What to Do
Routers send each other information about networks they know about. They do this with different types of protocols that are generically referred to as routingprotocols. Routers use this information to build a routing table that consists of the available networks, the costs associated with reaching the available networks, and the path to the next hop router.
In Figure 1-6, RouterA would like to advertise its connection to 168.71.5.0 to RouterB. RouterB would in turn like to advertise its connection to 168.71.8.0 to RouterA. The sample network in Figure 1.6 has been further simplified because only two routers are necessary to discuss this point.
Figure 1-6. A simplified view of the sample network.
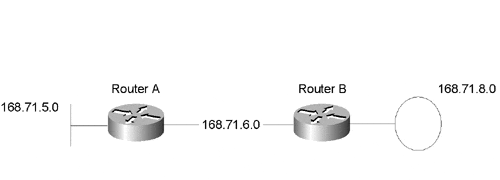
The two primary classes of routing protocols in use today are link state and distance vector, described as follows:
A router running a link state protocol sends updates that describe the state of the links attached to the router, the IP networks, or subnets assigned to the links and the costs associated with using those links. Other routers listen to these updates and then build a picture of the network's topology based on what networks the other routers have indicated they are connected to. The metric (unit of measurement) for link state protocols is typically cost based. A low-speed link costs more than a high-speed link in terms of performance. Paths that run over lower-cost higher-speed links are preferred.
A router running a distance vector protocol sends updates that contain all of the networks that the router knows about, not just the networks it is connected to. The advertising router increases the metric (typically a hop count) of the routes it has heard about and advertises them to the next routers in the path.
Choosing Your Routing Protocol
In general, link state routing protocols such as ISIS and OSPF are more difficult to configure and troubleshoot than distance vector protocols, but they offer greater scalability when used in large, complex networks. In addition, link state protocols usually recover from network problems (converge) faster that distance vector protocols.
Distance vector protocols such as RIP and IGRP are easy to configure but may not work well in large, complex networks due to the length of time they can take to converge. Neither RIP V1 nor RIP V2 is capable of taking into account the speed of a link connecting two routers. This means that they will treat two parallel paths of unequal speeds between two routers as if they were the same speed and send the same number of packets over each link instead of sending more over the faster link and fewer or no packets over the slower link. (IGRP does understand the speed of a link and can handle parallel links of unequal speed to a certain degree.)
Some IP routing protocols, such as OSPF, ISIS, RIP V2, and EIGRP, support concepts such as variable length subnet masking (VLSM) and non-contiguous major networks.
In general, it is usually best to use the simplest routing protocol that meets your needs:
In a network with no redundant links or parallel paths and no requirements for VLSM or discontiguous major networks, RIP V1 might be perfectly suitable.
In a network that requires VLSM and or discontiguous major networks and that does not have redundant links or parallel paths, RIP V2 might be perfectly suitable.
In a network that has redundant links or parallel paths and does not require VLSM or discontiguous major networks, IGRP might be perfectly suitable.
In a network with parallel paths and/or redundant links and that requires VLSM or discontiguous major networks, use either OSPF, EIGRP, or ISIS for IP.
This book is not intended to be an in-depth study of IP routing protocols themselves. Routing protocols are mentioned because many fundamental behaviors of IP routing require some kind of routing protocol to be running.
The behaviors presented here apply universally to all IP routing protocols. You can configure a simple network using OSPF instead of RIP and use the scenarios that follow later in this book in the exact same way they are presented. The resulting behaviors are basically the same.
See Interconnectionsby Radia Perlman, published by Addison-Wesley (ISBN 0-201-56332-0) and Internetworking WithTCP/IP by Douglas Comer, published by Prentice Hall (ISBN 0-13-474321-0) for more information on different types of routing protocols.
