CHAPTER 9
Evidence Handling
There are few events in the field of computer security as satisfying or worthwhile as a successful courtroom experience. If a computer security incident you have investigated leads to a court proceeding, the digital evidence and documents you obtained are likely to be used as exhibits in the trial. Special rules exist to ensure that the exhibits are genuine and exactly what they purport to be. Therefore, during adverse civil or criminal proceedings, your collection, handling, and storage of electronic media, paper documents, equipment, and any other physical evidence can be challenged by an adversary.
It is important that you follow and enforce evidence-handling procedures that will meet the requirements of the judging body and withstand any challenges. However, it is equally important that your evidence procedures do not create so much overhead that they become too cumbersome and difficult to implement at your organization. This chapter explains how to ensure that all the information you obtain is collected, handled, and stored in an appropriate manner. We present effective and efficient evidence-handling procedures, with guidelines for implementing these procedures in your organization.
During an investigation of a computer security incident, you may be unsure whether an item (such as a floppy disk) should be marked as evidence or merely be an attachment or addendum to an investigative report. According to the U.S. Federal Rules of Evidence (FRE), relevant evidence is defined as any information “having a tendency to make the existence of any fact that is of consequence to the determination of the action more probable or less probable than it would be without the information.” (FRE 401).
We can define evidence as any information of probative value, meaning it proves something or helps prove something relevant to the case. It is safest to treat any information of probative value that you obtain during an investigation as evidence. Therefore, any document, electronic media, electronic files, printouts, or other objects obtained during an investigation that may assist you in proving your case should be treated as evidence and handled according to your organization’s evidence-handling procedures.
TIP
The Department of Justice’s Computer Crime and Intellectual Property Section (CCIPS) has created an excellent (and free) manual as a reference document. The Searching and Seizing Computers and Obtaining Electronic Evidence in Criminal Proceedings manual is federal and criminally oriented, but overall an excellent reference. The manual can be obtained at http://www.cybercrime.gov/s&manual2002.htm.
The best evidence rule essentially requires that, absent some exceptions, the original of a writing or recording must be admitted in court in order to prove its contents. Fortunately, the FRE have addressed how this rule applies to electronic evidence. Rule 1001(3) provides, “[if] data are stored in a computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an ‘original.’” Under this rule, multiple copies of electronic files may each constitute an “original.” Many computer security professionals rely heavily on FRE 1001(3), because the electronic evidence collected is often transferred to different media.
We needed to store evidence for a criminal case for more than two years. The suspect ended up pleading guilty, based in large part on the strength of the forensic evidence. However, if the case had gone to trial, we would have needed to produce the “best evidence” for the trial.
At my organization, we define best evidence as the most complete copy of evidence that we have obtained that is closest linked to the original evidence. If we have the original evidence media, then it is our best evidence. If a client keeps the copy of the original evidence media, then the client has maintained control of the best evidence. In this case, we treat our forensic duplication as if it were the best evidence as defined by law. Hereafter, when we state “best evidence,” we refer to the best evidence that we have in our possession.
Sometimes, the course a case takes is outside the control of the client/victim. However, to ensure proper due diligence, we always assume a case will end up in a judicial proceeding, and we handle the evidence accordingly. If criminal or civil proceedings are a possibility, we often urge the client/victim to allow us to take control of the original evidence, since we have evidence-handling procedures in place.
For our purposes, we define original evidence as the original copy of the evidence media provided by a client/victim. We define best evidence as the original duplication of the evidence media, or the duplication most closely linked to the original evidence. The evidence custodian should store either the best evidence or the original evidence for every investigation in the evidence safe, as described in the “Overview of Evidence-Handling Procedures” section later in this chapter.
One of the most common mistakes made by computer security professionals is failure to adequately document when responding to a computer security incident. Critical data might not ever be collected, the data may be lost, or the data’s origins and meaning may become unknown. Added to the technical complexity of evidence collection is the fact that the properly retrieved evidence requires a paper trail. Such documentation is seemingly against the natural instincts of the technically savvy individuals who often investigate computer security incidents.
All investigators need to understand the challenges of evidence handling and how to meet these challenges. That is why every organization that performs computer security investigations requires a formal evidence-handling procedure. The biggest challenges to evidence handling are that the evidence collected must be authenticated at a judicial proceeding and the chain-of-custody for the evidence must be maintained. You also must be able to validate your evidence.
Legal Issues
Evidence-handling procedures are frequently attacked in suppression hearings. If the evidence you obtained from a hard drive is suppressed because you failed to maintain a chain of custody, it can have a devastating effect on a prosecutor’s case.
The FRE, as well as the laws of many state jurisdictions, define computer data as “writings and recordings.” Documents and recorded material must be authenticated before they may be introduced into evidence.
Authentication, defined in FRE 901(a), basically means that whomever collected the evidence should testify during direct examination that the information is what the proponent claims. In other words, the most common way to authenticate evidence is to have a witness who has personal knowledge as to the origins of that piece of evidence provide testimony.
If evidence cannot be authenticated, it is usually considered inadmissible, and that information cannot be presented to the judging body. You meet the demands of authentication by ensuring that whomever collected the evidence is a matter of record. It is important to develop some sort of internal document that records the manner in which evidence is collected.
Maintaining the chain of custody requires that evidence collected is stored in a tamper-proof manner, where it cannot be accessed by unauthorized individuals. A complete chain-of-custody record must be kept for each item obtained. Chain of custody requires that you can trace the location of the evidence from the moment it was collected to the moment it was presented in a judicial proceeding.
To meet chain-of-custody requirements, many police departments and federal law enforcement agencies have property departments that store evidence (the best evidence) in a secure place. Experts and law enforcement officers must “check-out” the evidence whenever they need to review it, and then “check-in” the evidence each time it is returned to storage.
Your organization can meet the challenge of chain-of-custody requirements by maintaining positive control (the evidence was kept within your possession or within your sight at all times) of all the best evidence collected, until it can be hand carried or shipped to your evidence custodians for proper storage. Your organization’s best evidence should always be stored within a safe or storage room that is inaccessible to anyone other than the appointed evidence custodians. We refer to this storage area as the evidence safe. Any access to the evidence safe should be controlled by your evidence custodians.
Appointing Evidence Custodians
We recommend appointing at least two individuals within your organization as evidence custodians. Assigning this job within your organization makes it much easier to maintain proper evidence-handling procedures.
Being an evidence custodian constitutes an additional duty for individuals and makes them responsible for the appropriate handling and documentation of all best evidence collected. The evidence custodians may be asked to testify in court, so they must be prepared to answer the question, “What experience/background/training have you had in this area?” Therefore, you may want to consider hiring people who have law enforcement experience or some other background in evidence handling.
The specially trained evidence custodians assume the greatest burdens of evidence-handling requirements. Any employee can collect evidence and transport evidence, but only your organization’s evidence custodians can inventory that evidence and ensure it is properly stored. The evidence custodians would also be required to:
The duties of the evidence custodians should be clearly stated and documented. We strongly suggest that this appointment should be in writing, approved and confirmed by a high-level manager. Also, we recommend designating one person as primary evidence custodian and another as alternate evidence custodian.
Another challenge is to ensure that the data you collected is identical to the data that you present in court. It is not uncommon for several years to pass between the collection of evidence and the production of evidence at a judicial proceeding. Your organization can meet the challenge of validation by ensuring MD5 hashes of the original media match those of the forensic duplication. MD5 hash values should also be generated for every file that contributes to the case (every file that is evidence).
CAUTION
MD5 sums calculated six months after evidence collection may not be helpful. The MD5 hashes should be performed (including time/date stamps) when the evidence is acquired. You do not want to open the door to challenges that force you to prove that the evidence was not modified between the time it was collected and the generation of the MD5 sum.
When duplicating a hard drive with EnCase, you can use the verify function within the EnCase application. When using dd to perform a forensic duplication, you must record an MD5 hash of both the original evidence media and the binary file or files that compose the forensic duplication. (See Chapter 7 for details on using EnCase.)
Legal Issues
Case law exists (motion filed in USA vs. Harold Naparst-U.S. District Court, District of New Hampshire) that suggests an EnCase evidence file can be considered as “best evidence.” This means that your organization may be able to provide EnCase evidence files during discovery.
When handling evidence during an investigation, you will generally adhere to the following procedures:
1. If examining the contents of a hard drive currently placed within a computer, record information about the computer system under examination.
2. Take digital photographs of the original system and/or media that is being duplicated.
3. Fill out an evidence tag for the original media or for the forensic duplication (whichever hard drive you will keep as best evidence and store in your evidence safe).
4. Label all media appropriately with an evidence label.
5. Store the best evidence copy of the evidence media in your evidence safe.
6. An evidence custodian enters a record of the best evidence into the evidence log. For each piece of best evidence, there will be a corresponding entry in the evidence log.
7. All examinations are performed on a forensic copy of the best evidence, called a working copy.
8. An evidence custodian ensures that backup copies of the best evidence are created. The evidence custodian will create tape backups once the principal investigator for the case states that the data will no longer be needed in an expeditious manner.
9. An evidence custodian ensures that all disposition dates are met. The dates of evidence disposition are assigned by the principal investigator.
10. An evidence custodian performs a monthly audit to ensure all of the best evidence is present, properly stored, and labeled.
Figure 9-1 shows the general flow of the evidence-handling process.
Before any electronic evidence is gathered, certain data should be recorded regarding the status and identification of the originating computer system. The type of information typically recorded includes the following:
The Evidence System Details form (see Appendix B) fosters better organization of this information. This form lists the details about the computer system that should be collected.
After recording system details (or even prior to this), you may want to take several photographs of the evidence system. There are several reasons for this:
You may want to take photos of all network and phone connections. You may even take photos specifically of the system serial number and hard drive label. Some additional guidelines we follow when taking photos for an incident are:
NOTE
Returning a system to its previous state is critical for organizations that perform covert duplications of media and do not want to alert employees that the contents of their computer system have been duplicated or reviewed. On covert operations, use a checklist of your tools to avoid mistakes. If you brought and used a forensic boot floppy, make sure you leave with it (that is, do not leave it in the suspect’s drive).
All best evidence collected should be labeled in a manner that satisfies federal and state guidelines, at a minimum. Our practice, which supplements the federal guidelines, requires recording the following information for each item we collect:
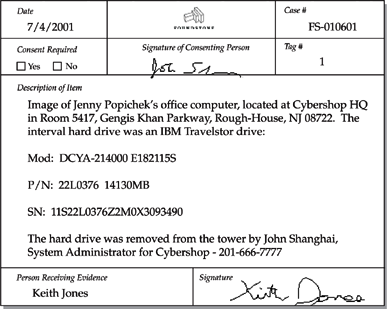
We meet the evidence labeling requirements by using evidence tags. Our evidence tag is modeled after the one used by many federal law enforcement agencies. It provides a record of descriptive data, as well as chain-of-custody data for all evidence obtained. Figure 9-2 shows an example of how the front side of a completed evidence tag might look. Many organizations use a variation of this evidence tag. One of the more common alterations that people take is to remove the references of requiring consent from the evidence tag.
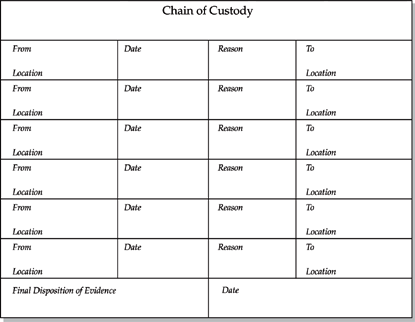
Our evidence tag also requires a list of all the people who have possessed the best evidence. This list will include the full name, position, and organization of the releaser and receiver; the date and time the evidence was transferred; the reason the evidence was transferred; and any notes on changes to the evidence. In this way, the evidence tag also allows us to meet the chain-of-custody requirements. This information is maintained on the back side of our evidence tag, as shown here:
NOTE
The Reason section of the evidence tag is for recording the reason you transferred evidence (or best evidence) to someone. For example, the reason may be to provide the media to the evidence custodian for storage or to provide the evidence media to an investigator to make working copies.
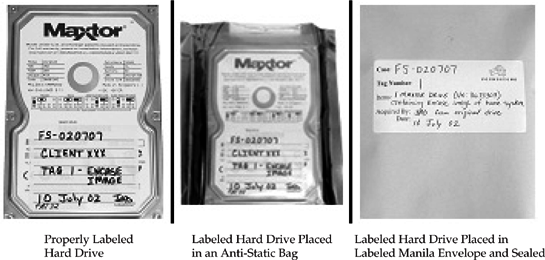
After the evidence tag is created for the best evidence, the evidence itself—the hard drive in this example—must be labeled. We use special labels that allow us to erase permanent marker (Sharpie pens), so we place a single label on a hard drive and change its label when needed. If labeling the original evidence, we suggest that you actually mark your initials and date on the original drive. Most people opt to use a permanent marker, but you could actually scratch your initials on the original evidence media in a discrete location. Your goal is to simply mark the evidence so that it is both readily identified as evidence media, and so you can immediately identify who was the individual who retrieved the evidence (for authentication purposes in court).
After labeling the evidence, place it into an anti-static bag (if computer media), and then put it and its evidence tag in a labeled manila envelope. When using an envelope to contain the evidence, at a minimum, the following information must be posted on the exterior of the envelope:
Figure 9-3 illustrates how to properly label a 3.5-inch hard drive being collected as best evidence.
Another suggestion is to seal the envelope with tape, and sign and date it across the tape (similar to packaging classified material). This helps establish that the best evidence has not been modified or tampered with by anyone else.
The investigator collecting the evidence (and all others who have custody of the items) must maintain positive control of the evidence at all times. This requires that consultants working at a client site have a means to store and transport any evidence in a manner that protects the evidence and prevents unauthorized access. At the very least, the container must be able to show signs of tampering by parties outside the chain of custody. The evidence must also be protected from alteration by the environment. This means that the evidence must not be exposed to possibly damaging electromagnetic fields, or kept in areas of extreme temperatures or conditions.
Shipping Evidence Media
When you are performing your forensic analysis off-site, you may not be able to hand deliver the best evidence to your organization’s evidence custodians. Therefore, you will need to ship the best evidence media. When sending media (or any evidence) to an evidence custodian for storage, it must be packaged in a tamper-proof, static-proof, padded container and shipped via a carrier that provides tracking capability.
When shipping evidence, the shipping container must meet the following criteria:
We have purchased hard cases specifically designed to store up to eight hard drives in a protective manner. Figure 9-4 shows an example of a temporary storage case that can be used to transport computer media in a safe manner.
When transporting best evidence on an airplane, we recommend carrying the best evidence on the plane as a carry-on. You may have heard about the dangers of airport security scanning laptops, hard drives, floppy disks, and so on. However, we have never had a drive, floppy, or laptop degaussed by an x-ray machine. In fact, one of our coworkers placed his laptop and several floppy disks in his briefcase and literally scanned them through about 50 times. There was no data loss.
GO GET IT ON THE WEB
Protective cases: http://www.pelican.com
Evidence bags and tape: tape http://www.premiercrown.com/evidence/ieb9000.asp
Evidence labels, seals, and tape: http://www.fitzcoinc.com/products/evidence_labels_seals_tape.htm
Secur-Pak pouches and evidence tape: http://www.bagexperts.com/policepic1.html
You need to record chain-of-custody details on the back of the evidence tag. Once such packaging is completed, you should ship the best evidence via the most expeditious manner to your evidence custodians. You must use a shipper that provides a tracking capability, such as Federal Express (FedEx) or United States Postal Service (USPS), Registered Mail. Note that the tracking information is accessible from the shipper’s web site for only a limited period of time. We recommend printing out the tracking information for your case folder.
NOTE
Upon arrival of the evidence, the evidence custodian assumes the burden of all chain of custody. The evidence custodian signs out the best evidence copies to authorized individuals on an as-needed basis (perhaps for additional analysis). Therefore, should an authorized individual require the best evidence, only one of the evidence custodians can provide access to it.
The Evidence Safe
Every organization that collects evidence as a result of any investigation requires an evidence safe. The evidence safe (or evidence room, vault, or other designation) prevents tampering or unauthorized access to the documents, data, or physical evidence that may be critical to your case. All evidence collected should be kept in the evidence safe. This safe should be kept locked at all times, except when it is being accessed by an evidence custodian. The combination or access keys to the evidence safe should be known only to the evidence custodians. This helps maintain the chain of custody, since an evidence custodian will be required to access the best evidence whenever it is going to be transferred to an individual.
The evidence custodians should receive and store all best evidence for every case your organization investigates. When they receive the evidence, the evidence custodians log the receipt of the evidence in the evidence log. A complete inventory of all the evidence contained within the safe should be kept in the evidence log.
Every time an action is taken for a particular case, the following information should be logged:
Therefore, the evidence log contains entries for each case where evidence was collected, following the entire life cycle of the best evidence from initial submission through final disposition.
We use an Evidence Safe Access Log form for this purpose (see Appendix B). A copy of this form can be maintained on the side of the evidence safe, since most safes are magnetic. The evidence log is stored within the evidence safe.
The first page of the log is a detailed example of how the evidence log must be maintained. Here is an example of the contents of an evidence log (Case Number: FS-010101 (US SuperTrust Bank), Opened: 11 Jan 01):

NOTE
We weighed the pros and cons of using an electronic database to track evidence. We opted for the paper trail due to the ephemeral nature of electronic evidence.
Examinations are performed on working copies of the best evidence. The working copy does not need to be stored in the evidence safe, unless the case merits additional safeguards for the information.
If your organization has numerous initial responders that perform forensic duplications and then forward their duplications to an evidence custodian, a good policy is to have those investigators be responsible for making the working copies of the best evidence. The only data that needs to be forwarded for storage in your organization’s evidence safe is the best evidence. This relieves the evidence custodians from the burden of making working copies for analysis and distributing those copies.
NOTE
Only the best evidence requires an evidence tag. No evidence tags are needed for any working copies of the best evidence. If the best evidence is transferred to different media, the original evidence tag must be appropriately annotated and transferred/co-located with the best evidence. In other words, you do not need to create evidence tags for the working copies you make during your forensic analysis.
You never want to have all your eggs in one basket. One of the advantages digital evidence has over other types of physical evidence is that it can be forensically duplicated an infinite number of times. One of the disadvantages of digital evidence is that hard drives and electronic equipment may fail. Therefore, in order to minimize the malevolent effects of equipment failure or natural disasters, it is prudent to create backups of all electronic evidence.
NOTE
Tape backups should be made as soon as possible. It is not uncommon for a hard drive to have physical errors, corrupting your best evidence copy. Therefore, in an effort to protect your organization from the embarassment of lost evidence, it is best to have redundant tape backups made by the evidence custodian within one month of evidence being acquired.
The evidence custodians should ensure that there is one tape backup of any best evidence. The tape backups will receive their own evidence tag and will be stored in the evidence safe, as if they were best evidence. During the custodial audit, the custodians must determine which cases have not yet been backed up, and then perform the necessary backups. If a case is not backed up, the evidence custodians must clearly mark it on the Monthly Evidence Custodian Audit form. This audit and form are discussed after the next section.
It is often convenient and necessary to practice the disposition of evidence in two stages: initial disposition and final disposition.
Initial disposition occurs when the final investigative report has been completed and the analysis, for all practical purposes, is finished. In other words, the forensic expert or the investigator has no outstanding tasks that require the best evidence. All media that contained working copies of the evidence should be returned to the evidence custodian to be wiped clean and placed back into the rotation as a clean storage drive. The evidence custodian disposes of the best evidence, but not the tape backup of the best evidence.
We adhere to a final disposition of evidence occurring five years from the date a case was initially opened, unless otherwise directed by law, the court, or some deciding body. The disposition date is recorded at the time the evidence is initially logged into the evidence log. The final disposition includes the disposal of all tape or CD-ROM backups containing the specified evidence. The date of the final disposition should be recorded on the evidence tag and in the evidence log.
Evidence custodians should perform a monthly audit to ensure that all best evidence is present, properly stored, and labeled. Our monthly audits require the evidence custodians to ensure the readiness of our incident response hardware as well. While you’re doing this audit, you may also elect to perform a software license inventory for your forensic software and other critical applications.
NOTE
Realizing the strain placed on the evidence custodians, since their custodial duties are an additional task, it is often a good idea to be flexible with the scheduling of these audits. However, you should perform a minimum of six audits per year.
We have created the Monthly Evidence Custodian Audit form (see Appendix B) to foster a timely, accurate, standardized approach to monthly audits. This form is merely a checklist that the evidence custodians adhere to when reviewing the evidence safe and readiness of our incident response capability. This checklist ensures that the evidence custodians review the following:
When a monthly audit has been completed, the most recent Monthly Evidence Custodian Audit form should be stored in a readily found location. Old copies of the form should be filed appropriately and maintained for over one year. We keep only one copy of our Monthly Evidence Custodian Audit form, and we do not maintain any electronic copies. Some folks may recommend keeping two copies of the Monthly Evidence Custodian Audit forms.
Proper evidence handling is a critical aspect of incident response and computer forensics. You want to develop procedures that help your investigators answer any challenges to the integrity of the data they present. You should perform a dry run of your evidence-handling procedures and response capability to communicate your evidence-handling procedures to the investigators who need to be aware of them. In all fairness to the affected parties, you want to ensure that evidence collected is tamper-proof and unaltered. Without proper evidence-handling procedures, how well will your organization hold up to scrutiny and challenges of an adversary?
1. What are the tasks/duties that an evidence custodian should perform?
2. Why should your organization appoint an evidence custodian?
3. Why is the best evidence rule especially important to computer forensic examiners?
4. At what time should you delete or destroy the data/evidence pertaining to an incident?
5. What is meant by chain of custody? What challenges would you offer to evidence accumulated by an organization that could not establish the chain of custody for electronic evidence? How might your challenges affect the weight / value given to the evidence offered?
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.