No single solution can truly protect against all attack vectors and plug every security hole of a system. By applying a defense in-depth model and layering protective measures, gaps in the security of one layer can be closed by controls on another layer, creating a holistic security posture. The layering of protective measures is much like how back in the middle ages, a king would protect his gold and jewels in a secret treasure room down in the dungeons of his castle:

The first line or layer of defense were the guards on watch towers, keeping an eye out for anything out of the ordinary approaching the castle surroundings. To that point, the clearing around a castle is a form of defense as well. By keeping an open stretch of land around the castle, there were no easy hiding places for an attacker to use. The second layer of defense was the moat surrounding the castle, often filled with hungry crocodiles as movies would like to have you believe. If a thief made it through the water (and past the crocodiles), a large brick wall that had to be climbed formed the next layer of defense. Ideally, the wall had no crevices, holes or other points of support that a person could leverage to climb the wall with. Guards stationed on watch towers or surveying the parapet walls were always on the lookout for intruders approaching or climbing the walls:
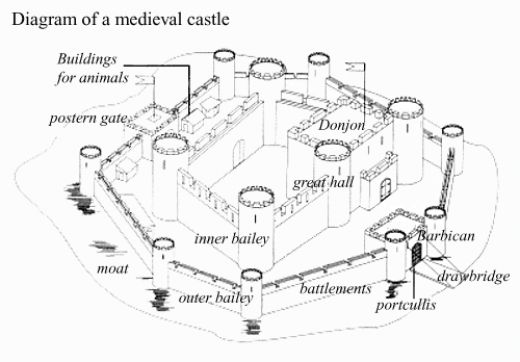
If an intruder made it all the way up the inner wall of the castle, he or she would now have to wander down the castle hallways and stairs and down to the dungeons to get to the secret treasure room. The location of the treasure room had to be known beforehand or discovered by exploration, prolonging the journey through the castle and increasing the chances of getting caught. Typically, the last layer of defense is a fortified locked door into the treasure room with a couple of guards on either side of the door.
In our medieval castle example, the applied security controls are mostly physical in nature as they mainly involve physically keeping people from entering the castle or detecting a physical breach of the perimeter (guards on watch). Now let's imagine the king in our castle example had found a way to make gold out of lead through a secret alchemy process. Instead of gold and jewels, the dungeon is now home to a sophisticated smelting process, controlled by a state-of-the-art Distributed Control System (DCS). The secret formula that turns lead into gold is stored on a server in one of the tower chambers. The alchemy process is run by a handful of trusted and well-vetted employees and all of the control and supervisory systems of the ICS are connected together over an Ethernet network with a remote access solution allowing access for remote interaction. The king has access to the entire ICS from his chambers so he can keep an eye on how fast he is getting richer and how he can interact with the systems whenever the need arises.
By installing a remotely accessible ICS network in the castle, it is no longer efficient to just physically defend the castle and the ICS in the dungeon against intruders. A defensive strategy needs to involve things such as securing against unauthorized people using the remote access solution and preventing an intruder that makes it to the castle from just plugging in an open network jack on the wall and jumping on the network. Unauthorized users of the system need to be denied access and authorized users need to be restricted in what they have access to while physically or remotely interacting with ICS systems. Guests of the king and guest users of the network need to be properly handled. Data in transit or stored on hard drives needs to be protected from prying eyes to protect the kings secret formula and sensitive data from theft or tampering with. The system needs to be defended against production downtime from tampering with ICS equipment or network attacks like DOS attacks on ICS equipment. Also, safety-related risks such as the tampering with the formula's parameters or changing of process variables to cause unexpected equipment and process behavior needs to be defended against.
The proper way of addressing all the concerns involved with securing and defending an ICS is by implementing a defense in-depth strategy. Back in Chapter 5, The Purdue Model and a Converged Plantwide Ethernet, we defined the layers of a defense in-depth model:
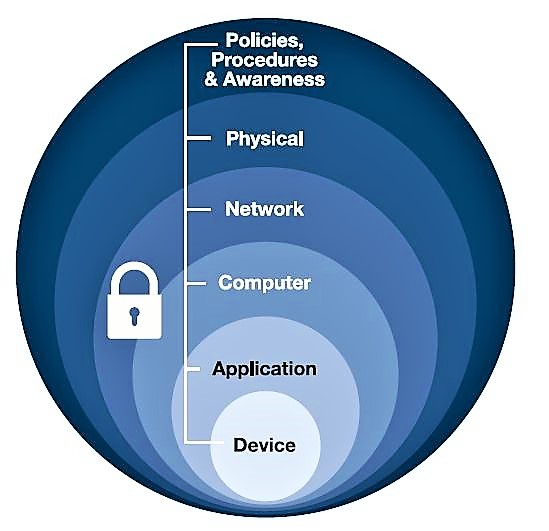
These are the layers defined in the defense-in-depth model, as shown in the figure above:
- Physical: Limit physical access for authorized personnel to cell/area zones, control panels, devices, cabling, and control rooms, through the use of locks, gates, key cards, and biometrics. This may also involve using policies, procedures, and technology to escort and track visitors.
- Network: Security framework—for example, firewall policies, ACL policies for switches and routers, AAA, intrusion detection, and prevention systems.
- Computer: Patch management, anti-malware software, removal of unused applications/protocols/services, closing unnecessary logical ports, and protecting physical ports.
- Application: Authentication, authorization and accounting (AAA) as well as vulnerability management, patch management and secure development life cycle management.
- Device: Device hardening, communication encryption and restrictive access as well as patch management, device life cycle management, and configuration and change management.
The model takes a systematic approach at securing all aspects (layers) of an ICS. Covering all layers of the model will guide the implementer through the process of securing an ICS from every aspect. Let’s look closer at each aspect or layer of the defense in-depth model in the next section.
