Device hardening is the process of securing a system or device by reducing its attack surface, which in turn reduces the potential for vulnerabilities. In principle, a system with fewer functions is more secure than a system with many functions, so less is truly more in this case.
ICS device hardening can be split up into several disciplines. One discipline involves disabling unnecessary and unused options and features on ICS devices:
- If you are not using the diagnostic web portal on your ICS device, disable it
- If you do not need telnet, SSH, SNMP, or other protocols, disable them
- If the ICS device doesn't provide the ability to disable the aforementioned protocols, consider sticking them behind an industrial-style firewall and blocking the corresponding service port. Several vendors have started building industrial firewalls:

Another discipline of device hardening involves restricting (physical) access to the devices:
- Administratively disable unused communication ports and/or physically block those ports from being connected to with blockout devices:

- Lock in cables so they cannot be disconnected:

- Install ICS devices in enclosures that can be locked
A third discipline of device hardening is geared more toward availability. If you recall, from the security triad's (CIA) perspective, availability is often of higher importance than integrity or confidentiality. Therefore, the triad is often referenced as AIC for ICS systems. A resilient and redundant ICS network starts with redundancy-enabled ICS devices, so plan for that during the procurement steps of the design phase of the ICS.
Where applicable, ICS devices should have:
- Redundant power sources:

- Redundant communication paths/ports:

- Redundant I/O:

- Redundant computing and controllers:
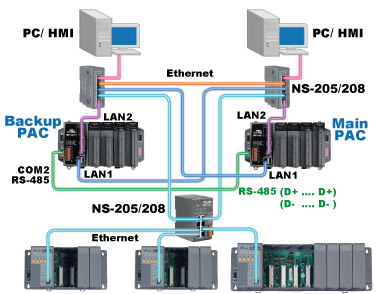
Combining these three disciplines in device hardening allows for creating of a resilient core of the ICS.
