Another way to limit the impact of a compromise is by using a security mitigation software solution, such as Microsoft's Enhanced Mitigation Experience Toolkit (EMET) or Microsoft's AppLocker. Microsoft's Enhanced Mitigation Experience Toolkit functions by intercepting application programming interface, or API calls, and enforcing protection profiles on those calls. This way, dangerous or malicious calls can be prevented.
EMET doesn't run as a service and isn't attached to an application like a debugger. Instead, EMET leverages a shim infrastructure built into Windows, called the application compatibility framework. This is a highly optimized low-level interface and, as such, EMET presents no additional resource overhead to the protected applications and services.
A Shim infrastructure implements a form of application programming interface hooking. Specifically, it leverages the nature of linking to redirect API calls from Windows to alternative code—the shim itself. The Windows Portable Executable (PE) and Common Object File Format (COFF) specification includes several headers, and the data directories in this header provide a layer of indirection between the application and the linked file.
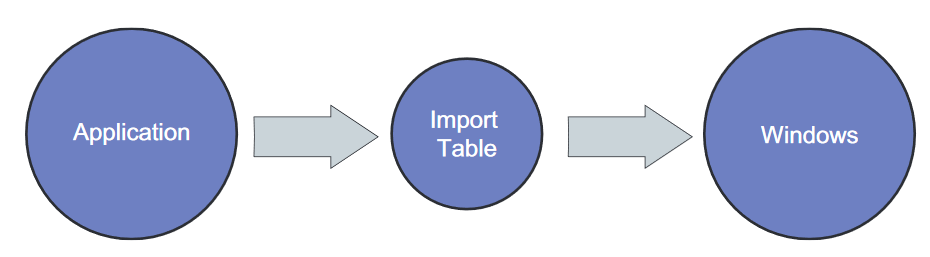
For example, if an executable makes a call to a Windows function, this call to external library files will take place through the Import Address Table (IAT), as shown in the following diagram:
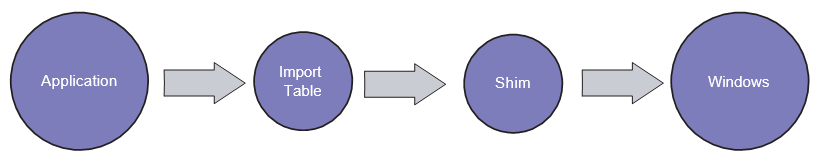
Using the shim infrastructure, you can modify the address of the Windows function resolved in the import table, replacing it with a pointer to a function in the alternate shim code:
EMET leverages this shim architecture to enforce its protection profiles. EMET protection profiles are XML files that contain preconfigured EMET settings. Companies can provide EMET protection profiles that are tailored to work with the applications and systems they sell. The company tests and validates that the settings in the protection profile work for a variety of operating systems and applications. Rockwell Automaton has provided a precompiled protection profile, which is free for download here: http://support.microsoft.com/kb/2458544. A valid (free) Rockwell Automation account is necessary to download the profile.
The RA Products included in the protection profile .xml file include the following:
- Connected Components Workbench
- FactoryTalk Activation
- RSLinx Classic
- RSLinx Enterprise
- FactoryTalk View
- FactoryTalk Gateway (Server/Remote)
- FactoryTalk ViewPoint (SE/ME)
- FactoryTalk Studio 5000 (RSLogix 5000 v21)
- FactoryTalk Batch
- FactoryTalk AssetCentre
- FactoryTalk Historian SE
- FactoryTalk Vantage Point
- FactoryTalk Transaction Manager
- RS Bizware
- RSView32 Suite:
- RSView32 Active Display
- RSView32 Webserver
- RSView32 TrendX
- RSView32 Messenger
- RSView32 SPC
- RSView32 Recipe Pro
We will use this list to set up an EMET profile in the upcoming exercise.
