Let's get back to the task at hand for this chapter: applying physical security. Physical security encompasses the security controls that prevent or restrict physical access to the devices, systems and the environment of an ICS. This activity should be an all-inclusive exercise, where every approach angle to the premises gets covered. It should include recommended physical IT security best practices as well as controls aimed at ICS environments. The following are general recommendations to cover physical security for an Industrial control system, the facility it is in, and the surrounding area:
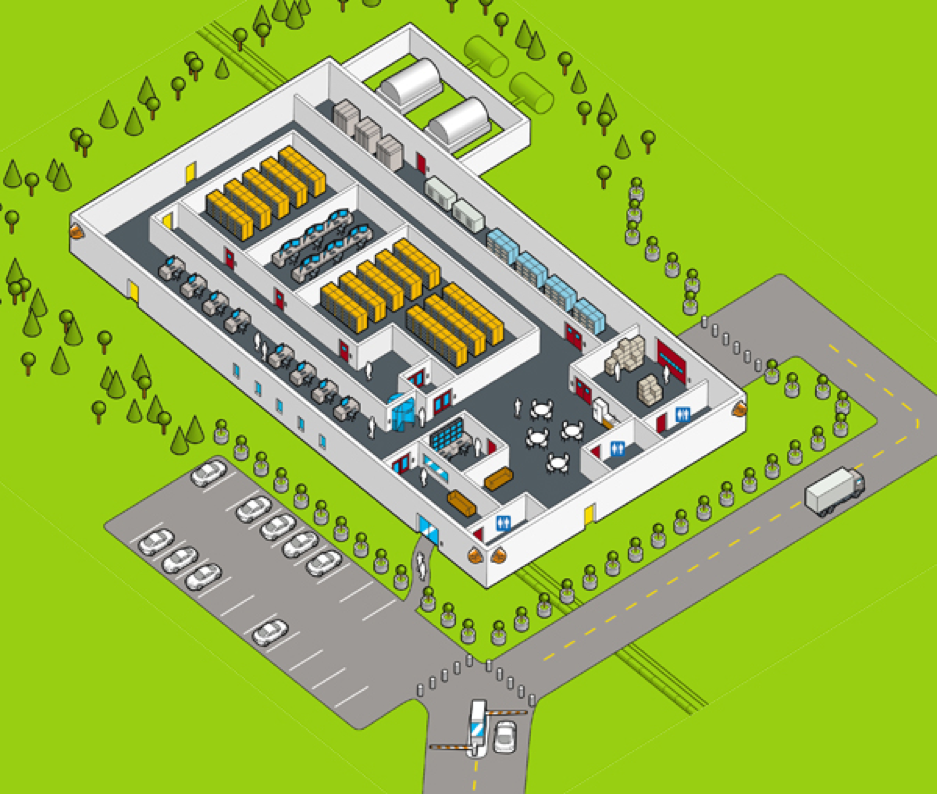
- Location, location, location: Choosing the right location for the ICS facility is of utmost importance. One wants to stay clear of known earthquake fault lines and away from hurricane areas. You should also choose your neighbors wisely. Prisons, airports, or chemical plants can cause unexpected disturbances.
- Engineer landscaping with security in mind: Overgrown trees, overly large boulders, and other large obstacles can hinder the surveillance of the building and the surrounding area. Keep a 100-foot buffer zone around the site and design landscaping so the camera and watch guards can do their job properly. Properly sized and placed natural obstacles, such as boulders, can help with the defense of weak spots in perimeter defenses, such as walls, gates, windows, doors, and fences. Where landscaping does not protect the building from vehicles, use crash-proof barriers, such as anti-ram bollards or posts, instead:

- Fences: A fence is used as a first line of perimeter defense. By surrounding the facility with a fence or wall of at least 6-7 feet in height, casual intruders are deterred from trespassing the facility premises. A fence that is 8-feet tall or higher will stop even the most determined intruders.
- Vehicle and personnel entry points: Control access to the facility with a staffed guard station that operates with retractable ram posts. Employees use badge swiping stations and/or pin pass entries to get through the gate. Visitors check in with the guard and are handled according to the visiting policies:

- Plan for bomb detection: For production facilities that are especially sensitive or likely targets, have the gate guards use mirrors to check underneath vehicles for explosives or provide portable bomb-sniffing devices.
- Premises surveillance: Surveillance cameras in the form of IP cameras or a closed-circuit television (CCTV) system should be installed in and outside the facility and all around the perimeter defense line. Extra care should be taken for all entrances and exits of the facility and every access point throughout the facility. Combining the use of motion-detection devices, low-light cameras, pan-tilt-zoom cameras, and standard fixed cameras is ideal. Recordings should be stored offsite for a predetermined amount of time. Besides video surveillance, security guards with watchdogs should regularly survey the facility and its surrounding area to look for anything out of the ordinary.
- Limit the facility entry points: Control access to the building by establishing a single main entrance, plus a back entrance for delivery or shipping.
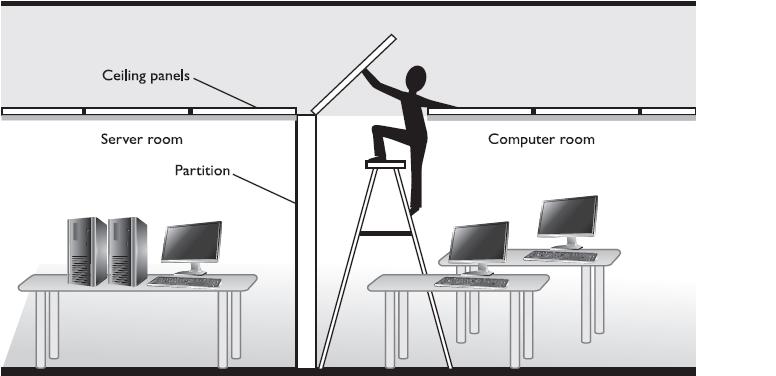
- Walls: For exterior walls, foot-thick or better concrete walls are cheap and effective barriers against severe weather, intruders, and explosive devices. For even better security, walls could be lined with Kevlar. Interior walls that secure sensitive areas, such as data centers, server rooms, or process areas, should go all the way to the ceiling so intruders cannot simply crawl over one in case of a dropped ceiling:
- Windows: We are building a production facility, not an office building, so avoid windows as much as possible as they are a weak spot in the exterior defense of a building. An exception might be the break room or administrative areas. The following types of glass provide extra protection. Each has its own characteristics and applicability:
- Heat strengthened glass
- Fully tempered glass
- Heat soaked tempered glass
- Laminated glass
- Wire glass
- Make fire doors exit only: For exits required by fire codes, install doors that don't have handles on the outside. When any of these doors is opened, a loud alarm should sound and trigger a response from the security command center.
- Secure access to production areas: Strictly control access to the production areas of the ICS facility by means of locked entries into these areas. Only authorized personnel should be allowed into the process area by means of swipe cards and/or biometrics reading devices. All contractors and visitors should be accompanied by an employee at all times.
- Secure access to IT infrastructure equipment: Strictly control access to areas housing IT equipment, such as server rooms, data centers, or networking equipment such as main distribution frame (MDF) and intermediate distribution frame (IDF) cabinets. Install swipe card readers or pin code entry locks on entries to server rooms and data centers. Lock MDF and IDF cabinets with special keys or place the MDF/IDF in a secured area.
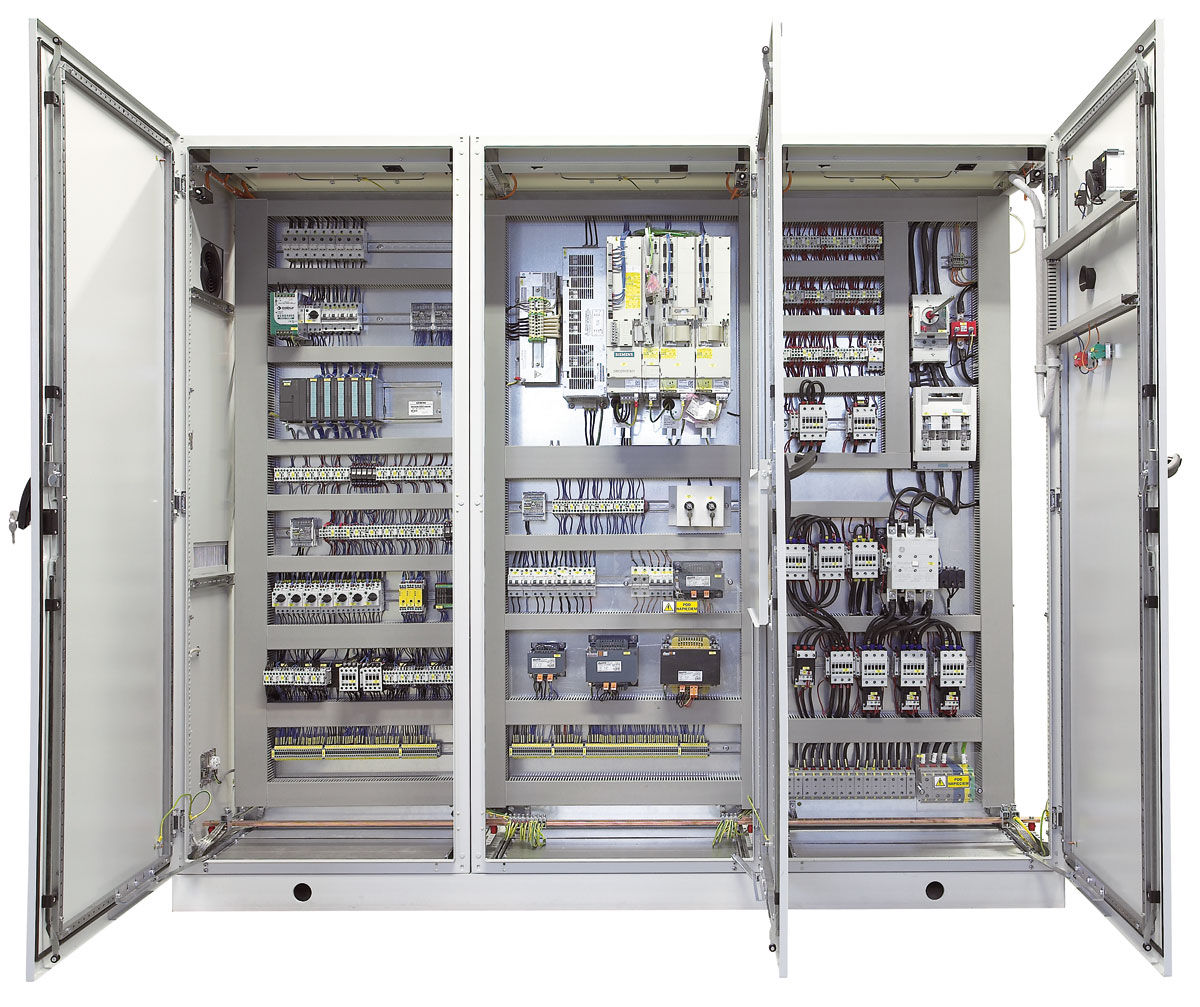
- Sensitive ICS equipment: Secure sensitive ICS equipment, such as PLCs, industrial computers/servers, and networking equipment by placing them in lockable panels or in a securable area, such as locked engineering offices. With physical access to these kinds of ICS devices, gaining access to the data contained within them or disrupting their proper functioning is a simple task. By placing these devices in a secured area, they will be protected against intentional and accidental harm:
- Physical port security: To protect against introducing unauthorized computers, switches, access points, or computer peripherals such as thumb drives, all physical ports should be secured against plugging in these unauthorized devices. For unused switch ports and spare NIC ports, port block-outs can be used:

- To keep cables locked into place, port lock-ins can be used:

- USB ports can be blocked with a blocking device:

All these physical port blocking devices have technical control options as well, which we will discuss in later chapters.
- Use multi-factor authentication: Multi-factor authentication allows more secure identification of users. Biometric identification is becoming a standard for access to sensitive areas of ICS facilities, such as data centers, server rooms, and the production area. Hand geometry or fingerprint scanners are becoming the norm as a secondary authentication mechanism next to a swipe card or pin pass entry. Where possible, use multi-factor authentication to enter the restricted ICS facility area.
Involved authentication processes are not advised for logging into process equipment. In case of emergency, an operator should have unhindered access to the controls that can stop or correct the process flow.
- Harden the core with security layers: Anyone entering the most secure parts of the ICS facility will have been authenticated at least three times, including these:
- At the gate.
- At the employee's entrance. Typically, this is the layer that has the strictest positive control, which means no piggybacking is allowed. To enforce control, you have two options:
- A floor-to-ceiling turnstile. If someone tries to sneak in behind an authenticated user, the door gently revolves in the reverse direction.
- With a mantrap consisting of two separate doors with an airlock in between. Only one door can be opened at a time, and authentication is needed for both doors.
- At the inner door that separates the general area from the production area. At the door to individual restricted areas such as the door to the server room or the entrance to the main control room.
- Watch the exits: Monitor building entrances and exits: not only for the main facility but also for more sensitive areas of the facility. This will help you keep track of who was where when. This can also help you spot when equipment disappears and can assist in evacuation during an emergency.
- Have redundant utilities: Data centers need two sources for utilities, such as electricity, water, voice, and data. Trace electricity sources back to two separate substations and water back to two different main lines. Lines should be underground and should come into different areas of the building, with water separate from other utilities.
