CHAPTER 12
Information Assurance Policy
The information assurance policy is undoubtedly the most important element for a successful information assurance management program. In the same way that it is unthinkable that a country could function without laws and legislations, it is unthinkable that an organization could operate without information assurance policies.
Establishing the IAMS starts with identifying information assets and associated life cycles. This is followed by a risk identification and assessment exercise on the assets that provides a sound basis to develop and implement controls to manage the risks. A successful risk assessment exercise is also important in that it gives the correct foundation to formulate the information assurance policy of the organization.
Policy is a formal rule of conduct, controlled by some authority. This chapter provides guidance to information assurance units and related stakeholders about the necessary information to develop a comprehensive information assurance policy document.
Importance of Policy
The following outlines why an organization needs a policy document:
• To establish a foundation for an effective information assurance management program. Good management control makes good business sense. Failure to implement controls may lead to financial penalties, loss of customer confidence, and loss of competitive advantage. An information assurance policy is the cornerstone of any effective information assurance management program.
• An effective information assurance management program covers a management framework for information assurance and the implementation of information assurance controls. The most critical component in the information assurance management framework is a policy document.
• The policy must establish and define appropriate security conduct. No one likes cumbersome or inefficient security controls, particularly if they affect business processes. Despite an increase in the number of security risks, most information assurance organizations still find it difficult to enforce information assurance and obtain necessary employee support. Policies convey senior management’s information assurance commitment and expectations. Once policies are approved and endorsed by senior management, information assurance becomes an important agenda item within the organization. Employees should then be encouraged to support senior leadership with their own information assurance efforts.
• To support regulatory and governance requirements and fiduciary duties. With the emergence of various legislation and regulatory requirements, the management needs to demonstrate to stakeholders that sufficient internal controls have been implemented. Policy is a management control and demonstrates management commitment to improving and enforcing information assurance.
• To ensure consistent implementation of security controls. Security is as strong as its weakest link. Any mishap in the information assurance chain may jeopardize the entire security effort. Thus, it is important that everyone subscribe to the required minimum level of security. This is possible only when policy rules are clearly documented and understood by all.
• To support the coordination of activities of internal and external groups. In today’s business environment in which outsourcing and business partnerships are becoming the norm, there is a need to have a policy document to manage and monitor the activities of the various parties who have access to information assets.
Policy and Other Governance Functions
![]()
Policies provide direction to an organization’s intents and objectives that meet its requirements in various areas. Guidelines and procedures are developed and aligned to these policies. They are distributed to the employees to create awareness and better understanding of the organization’s processes. This ensures effective implementation of them.
Figure 12-1 illustrates the hierarchy of security documents usually found in an organization.

Figure 12-1 Framework of security documents
The next section defines and discusses the differences between policy, procedures, standards, and guidelines.
Policy in Relation to Standards
Standards are mandatory rules, regulations, activities, or actions designed as supporting documents to provide policies with direction and specificity. They ensure policies developed are meaningful and practical. Policies without enough specificity are difficult to endorse and also do not convey accurate meaning. Standards and procedures provide the necessary specificity regarding the “what” and “how” of a policy. Policies and standards are generally mandatory as well as being compliance documents.
While related to each other, policies and standards differ significantly. Policies are high-level requirement statements and address a broad audience. Standards may be both high- and low-level requirement documents. For example, some standards may focus on information assurance management issues, while others focus on specific technical requirements and specifications. They target a specific audience. Policies and information assurance management standards as well as international technical standards are developed to be relevant for several years. On the other hand, industry standards are usually developed and updated to reflect rapid changes in technology.
Table 12-1 illustrates the difference between policy and standard.

Table 12-1 Examples of Policy and Standard Statements
Policy in Relation to Guidelines
Guidelines provide advice designed to achieve a policy’s objectives and standards.
Guidelines are useful in situations where employees need to comply with a local policy because of the nature of the business and its operations. For example, a company with multiple subsidiaries may introduce guidelines on business continuity management. It provides room for subsidiaries to develop business continuity plans reflecting the parent company’s business objectives. Each subsidiary may develop a local policy on business continuity management, guided by the recommendations provided in the guidelines issued by the parent company. Table 12-2 shows examples of policies, standards, and guidelines.

Table 12-2 Examples of Policy, Standard, and Guideline Statements
Policy in Relation to Procedures
Procedures define the specifics of how the policy and supporting standards and guidelines should be deployed and used in an operational environment. A policy statement provides high-level direction for addressing a particular problem, while procedures provide systematic instructions, guidance, and/or methods that employees need to use. Procedures are typically mandatory.
For example, to avoid data loss or corruption, a policy {XE “policy”} can describe the need for backups, for offsite storage, and for safeguarding backup media. A procedure can describe how to use backup software and when to make backups. Table 12-3 illustrates the differences between policy, standard, guideline, and procedure statements.

Table 12-3 Examples of Policy, Standard, Guideline, and Procedure Statements
Policy Development Steps
This section details the policy development steps starting from gathering key reference materials, defining a framework for policies, developing a policy, and reviewing and approving the policy, as well as the enforcement processes. Figure 12-2 shows the relationship among these steps.
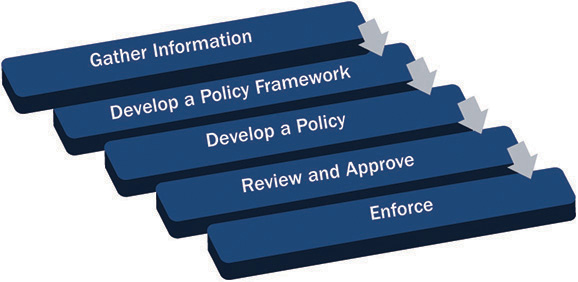
Figure 12-2 Policy development steps
Information Gathering
Information gathering is essential to policy development. This ensures that developed policies are consistent with the organization’s culture, vision, and mission.
An important reason to expend resources on background research is that it ensures that a policy developed is in line with the strategic direction of the organization. For example, it would not be sensible to develop a group wide information assurance policy for a company with multiple subsidiaries when it has been decided to decentralize information assurance management.
The following documents should be studied and/or reviewed during the information gathering step:
• An overview of IT infrastructure and a list of IT systems used as background reference
• Current policies, standards, guidelines, or procedures
• Risk assessment (refer to Chapter 11 for details on risk assessment) or audit reports as references; they indicate the organization’s current and future information assurance needs
• Security incidents or other loss-related historical information and any information that might help in identifying areas that need further attention
It is normal for information systems to change frequently; therefore, related documentation becomes outdated and introduce new risks. You should interview relevant parties to learn background information prior to policy development. Some organizations do practice oral policies or informal culture-based policies. Such policies are ones that the employees practice on a daily basis without formal documentation. Interview sessions can uncover undocumented policies practiced by organizations. Oral policies should be discouraged because they are rarely enforceable and are subject to conflicting interpretation.
Policy Framework Definition
After the relevant information collection, compile a list containing the topics covered. Organizations may want to prioritize policy coverage based on the urgency of issues to be addressed.
Next, the organization should define how it intends to present the information assurance policies. For example, issue some policies in the form of a manual. Alternatively, the information assurance department may issue memos summarizing the policies periodically or post them on the Intranet.
As there may be several topics addressed in the policy document, it is crucial that information is conveyed to the right parties. It may be useful for the organization to identify the target audience group that the policy will address.
Policy Development
Before developing the policy document, the organization should understand the style of existing policies, the documentation format, and the system for numbering policies. The message should be kept brief, with words such as shall (imperative form) applied to indicate that an item in a policy statement is mandatory and such words should be used consistently throughout the policy. Most organizations will not have a single policy to cover all of information assurance needs. Large organizations may have a single master policy supported by subpolicies, with each subpolicy being pertinent to particular aspects of the organization. Standards, procedures, and guidelines may be referenced in the policies.

Review and Approval
Several review cycles are recommended to gain support from the key players. As more feedback is received, the policy has greater chances to be accepted later. At a minimum, it should be a three-step process peer review; review by internal parties such as internal audit, IT, human resources, or legal department; and finally, review by senior management.
The final step in the review process is endorsement by senior management. A notice to all employees informing them that compliance is mandatory as a condition of continued employment should be stated on the first page of the document or on the main page of an organization’s web site if the policy is posted on the intranet. This conveys to readers that the policy is indeed supported by top management and that they have given their serious commitment to it.

Enforcement
Policy enforcement is the final crucial step to ensure the success of an organization’s information assurance management program. Suitable actions should be taken to detect and respond to noncompliance. It is appropriate to discuss noncompliance issues with all parties involved and the human resource department. This discussion encourages proper execution of existing disciplinary processes for noncompliance. To avoid future disputes, the organization should clearly document activities that violate the policy and associated penalties.

Prior to enforcement, employees should understand why a policy is being introduced. Communicate expectations through an information security awareness program to ensure an effective policy development exercise. Refer to Chapter 16 for more details on information security awareness. Additionally, organizations may choose to have employees sign the rules of behavior document. This document signifies employees have read and understand expectations regarding their behavior when using information systems.
Policy Layout
The actual layout of a policy document varies from organization to organization. However, a policy document should consider the following components as a starting point:
• Objectives This section will define the goals of the policy and the issues to be addressed.
• Scope The scope establishes which resources of the organization are covered by the policy. This can include all electronically stored, processed, transmitted, printed, faxed, or verbal information.
• Definitions This section will define important terms and definitions to be used throughout the policy document to establish a common ground of understanding among all readers.
• Responsibilities This section will establish who is responsible for the review, maintenance, and implementation of the policy.
• Compliance This section will detail the consequences if the policy is violated.
• References This section will list materials referred to in the policy document such as specific regulations, decrees, mandates, standards, and other policies.
• Related documents This section will list relevant documents that are created in relation to the policy document.
• Effective date This section will specify the effective date of the policy.
• Signature The document should have a signature of approval by senior management.
Further Reading
• Code of Federal Regulations, Part 5 Administrative Personnel, Subpart C- Employees Responsible for the Management or Use of Federal Computer Systems, Section 930.301 through 930.305 (5 C.F.R 930.301-305).
• Frost, J.C., J.M. Springer, and C.D. Schou. Instructor guide and materials to accompany principles of Introduction to Principles of Computer Security: Security+ and Beyond. McGraw-Hill Education, 2004.
• Nash, A., et al. PKI: Implementing and Managing E-security. McGraw-Hill Education, 2001.
• Nichols, R., et al. Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. McGraw-Hill, 2000.
• National Institute of Standards and Technology. Special Publication 800-100, Information Security Handbook: A Guide for Managers. October 2006.
• National Institute of Standards and Technology. Special Publication 800-53, Revision 4, Recommended Security Controls for Federal Information Systems and Organizations. DOC, April 2013.
• Office of Management and Budget. Memorandum M-04-26, “Personal Use Policies and File Sharing Technology.” September 2004.
• Office of Management and Budget. Circular A-130, “Appendix III, Transmittal Memorandum #4, Management of Federal Information Resources.” November 2000.
• Schmidt, Howard A. Patrolling Cyberspace: Lessons Learned from a Lifetime in Data Security. Larstan Publishing, 2006.
• Schou, Corey D., and K.J. Trimmer. “Information Assurance and Security,” Journal of Organizational and End User Computing, vol. 16, no. 3, July–September 2004.
• Conklin, Wm. Arthur. Introduction to Principles of Computer Security: Security+ and Beyond. McGraw-Hill Education, 2004.
• Schou, Corey D., and D.P. Shoemaker. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2007.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
• Wood, Charles C. Information Security Roles & Responsibilities Made Easy. PentaSafe Security Technologies, 2002.
Critical Thinking Exercises
1. An organization has had more than a dozen personal health information (PHI) breaches in the past year. The organization has a policy in place that stipulates sensitive information is not to be e-mailed or transmitted outside of the organization. The human resources department has just enabled a new “work from home” telework policy. However, individuals have complained ever since the start of the telework program because they are unable to take information with them to work on at remote locations. How can the organization address this issue with policies, standards, procedures, and guidelines?
2. An organization has a clear policy creation mechanism, and the organization’s information assurance team has ensured every specification and requirement is incorporated into the organization’s policy. The organization routinely evaluates the policy every six months to determine whether updates are needed. A breach just occurred, and the encryption policy needs to be updated to include a new standard; however, the next update window isn’t for another five months. Additionally, the policy review process is cumbersome and time-consuming because every department in the organization must review and approve of the policies being created. What could the organization do to help streamline this process?
