CHAPTER 17
Information Assurance Awareness, Training, and Education (AT&E)
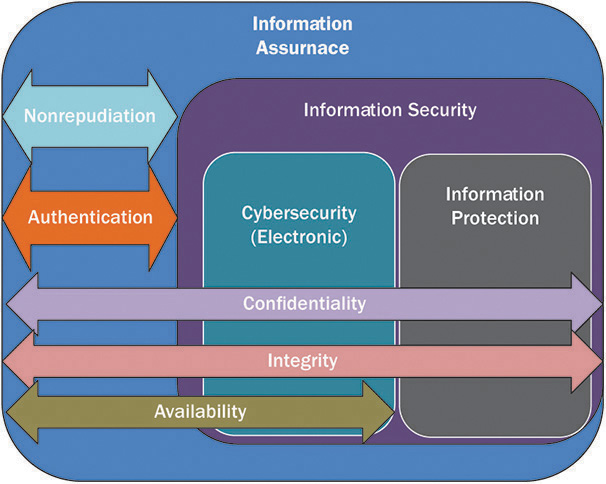
Organizations invest millions to secure their systems as new threats and information risks emerge. Most fail to realize a common “weakest link” in securing systems and networks is the human, especially an organization’s employees. Frequently, employees do not understand their role in the information assurance plan. They do not see the big picture described in Chapter 2. They see only parts and do not see how they fit into cybersecurity, information protection, information security, and finally information assurance. This lack of awareness means employees do not effectively apply appropriate countermeasures from the MSR model. Some examples of information assurance risks attributed to employees include the following:
• Using weak passwords
• Downloading malware
• Using of out-of-date antivirus signatures and software
• Being unaware of becoming targets of social engineering attacks
However, with a proper information assurance AT&E development program, users become the organization’s strongest information assurance asset. Users are the front line of any organization. They handle information and have access to sensitive systems, and often they are “just trying to do the right thing.” An enterprise-wide AT&E program is essential to ensure employees are equipped to handle modern threats and those who would take advantage of their willingness to help!
The AT&E program ensures that employees understand personal responsibility and organizational policies. It allows them to better use and protect information system resources entrusted to them. This chapter discusses various types of AT&E programs and makes suggestions about program implementation.
An effective AT&E program has four stages: literacy, awareness, training, and education (LATE). Not all employees will progress through the entire program to education nor is progression of all employees to education necessary for effectiveness. However, the AT&E program will not succeed if literacy is not established. Employees must have a common vocabulary to be able to communicate about information assurance.
Purpose of the AT&E Program
The purposes of information assurance AT&E are as follows:
• To circulate and ensure effective implementation of the organization’s information assurance policies, procedures, and guidelines
• To cultivate a strong information assurance culture by making employees aware of their responsibilities with regard to information assurance
• To emphasize the fact that the organization is taking information assurance seriously and therefore will train its employees about the importance of protecting the organization’s information assets
• To encourage employees to seek additional education about information assurance
• To encourage employees to be more information assurance–conscious in their daily tasks, for example, by considering information assurance risks when making business decisions
• To highlight management’s support for and commitment to information assurance
• To inform employees about information assurance risks and controls in a general sense and provide more specific information and guidance where necessary
Employees should understand how their actions affect the overall information assurance posture of the organization. They must understand not only how to protect the organization’s information but also why this protection is important. Making them aware of their information assurance responsibilities and training them about proper practices makes it easier for them to understand the impact they have and do the right things in risky situations.
Benefits of the AT&E Program
![]()
The following are the benefits introduced by awareness, training, and education programs:
• An AT&E program raises an organization’s reputation and brand. An organization’s reputation and brand are enhanced if their customers perceive the organization as an entity that protects the availability, integrity, sensitivity, and confidentiality of their customers’ data.
• An AT&E program minimizes the severity and number of information assurance incidents. Early detection of information assurance incidents reduces impacts to an organization. This reduction decreases direct costs such as data recovery and customer notification. A significant reduction in crucial indirect costs such as loss of reputation, customers, and productivity is an additional benefit.
• An AT&E program provides better protection for assets. An organization’s information and information assets can be better protected by training employees to recognize and respond proactively to real or potential information assurance concerns.
• An AT&E program reduces the risk of lawsuits against the organization. Organizations should exhibit a genuine corporate concern for information assurance. They should implement processes to ensure its workforce will provide adequate protection for information assets.
Design, Development, and Assessment of Programs
Organizations may kick off information assurance initiatives with literacy exercises followed by both awareness and training programs. To ensure that an information assurance plan is introduced effectively, it needs to be designed and customized to the needs of the organization. One size does not fit all.
Before organizations embark on any information security awareness or training programs, take steps to ensure proper information assurance processes and information assurance roles and responsibilities have been established. This ensures that questions such as “Who should I contact?” and “What reporting process do I need to use?” as well as issues raised by the employees during the programs are answered and discussed. This will reveal that the organization is ready and committed to pursue the information assurance initiatives with the employees’ support.
A well-designed AT&E program begins with a needs analysis. This analysis indicates the literacy level of the audience on the subject and allows needs-based prioritization. Organizations should develop an AT&E strategy based on the results of this assessment. They should focus the strategy on developing, implementing, and maintaining information assurance AT&E programs. Reflect the strategy in the plan, which is a working document containing the strategic elements and how they relate to the overall information assurance strategy.
Develop awareness and training materials to support the plan in the next phase. Security awareness and training materials are widely available on the Web and can be customized to any particular organization’s culture and strategic needs. It is always a good idea to look for feedback once an awareness or training program has been conducted because it will help improve future endeavors on training and awareness. Survey forms, evaluation forms, and independent observations can always be used as input.
Types of Learning Programs
The types of programs usually consist of awareness, training, and education. These are explained in the following subsections. There is also a subtle difference between training and education. The former emphasizes more on skill development especially in using the information system. The latter is more general in the sense that it imparts general knowledge, preparing the audience for a more mature life in managing security of information.
Information Assurance Awareness
After you have established the literacy level of your employees, awareness programs explain to employees their roles in the areas of information assurance. The objective is to provide insight to employees on how they play an important part in the protection of confidentiality, integrity, availability, nonrepudiation, and authentication of the organization’s information assets. Awareness programs serve to motivate a sense of responsibility and encourage employees to be more cautious about their work environment. Because people tend to forget, awareness also reminds people of basic information assurance practices, such as changing passwords at predetermined intervals.
Most organizations focus their awareness efforts on the information security subdomain of information assurance. This targeted approach means all employees will be exposed to how their behavior and role intersect with the confidentiality, integrity, and availability of an organization’s data and services. Organizations should then focus training on the additional responsibilities associated with nonrepudiation and authentication based on their role in the organization.
Implementing a successful information assurance awareness program is often a difficult but rewarding task. The following guidelines can help organizations develop an effective information assurance awareness program:
• Obtain management commitment Management’s commitment should be clearly stated in the information assurance policy. As with all information assurance initiatives, an awareness program will never reach its goals without strong management support. Unless the organization‘s management team is on board, leading and creating awareness for any organization’s awareness program is going to be useless. Funding, employee attendance at awareness sessions and employee perception of the importance of information assurance all depend on support at all layers of management.
Organizations should write the policy in a comprehensive but concise manner. Policies are scoped for numerous years and therefore should convey senior leadership’s high-level commitment to information assurance. Once the policy is produced, employees should be made aware of the policy’s contents and existence. Formal information assurance policies, no matter how carefully they are written, are less valuable unless employees know about them, understand their responsibility within the context of the policy, and comply with them.
• Appoint personnel to lead the planning process Organizations should assemble a team or taskforce to begin the process of planning an awareness program. Dedicate at least one accountable individual to lead information security awareness training across the organization. The task force helps create and approve training materials and determines suitable delivery methods.
• Ensure establishment of an information assurance program and associated policy An information assurance policy is the basis of an effective information assurance program. Organizations in consultation with their information assurance team should begin with documenting all of the high-level goals, requirements, and objectives of the information assurance program in an information assurance policy prior to developing an information security awareness program.
• Get their attention To ensure that the awareness initiatives reach everyone in the organization, introducing information assurance as a fun and interesting topic is the most practical approach. In general, people are afraid of information assurance, while others may find it a boring subject. To garner the employees’ attention, the awareness program should be proactive, fresh, and current. Messages need to be made in a variety of ways to accommodate the audience, for example, through presentations and posters. To be influential, awareness presentations should have credible trainers or speakers. They should use creative ways to deliver the message. In addition, the content of the programs should be compelling. Without a high degree of credibility, the integrity and clarity of the message will be lost, and the whole communication process will be a waste of resources.
• Make it applicable to the employee As more information is being stored online and more people are using online services for banking, health, travel, and personal matters, people are interested in protecting themselves online. The organization’s awareness program is an opportunity to help employees learn how to protect their private lives in addition to the organization’s information.
• Measure the effectiveness The effectiveness of an awareness program and its ability to improve information assurance can be measured. The need for information security awareness is broadly recognized, but not many organizations have tried to quantify the value of awareness programs. Evaluation of an awareness program is essential to understand its effectiveness, as well as to use the data gathered as a reference to fine-tune the initiatives to make it even more successful.
• Test the awareness level An awareness program is an agent to create change. Its purpose is not just to convey information but also to change behavior. It should change behavior by persuading employees to take action toward the organization’s objectives. To determine whether an organization has successfully promoted an information assurance–conscious culture within the organization, questions can be asked about whether any information security breaches have happened and employees understand how to report the breaches.
To acquire and maintain management support, the effectiveness of the program should be measured. Improvement activities should be based on these measurements and the results forwarded to upper management. Additionally, organizations may use friendly competition between constituent parts to spur on higher completion rates and lower rates of incidents.
Recall that awareness is at the lowest level of the AT&E solution to information assurance. It is designed to affect short-term memory. It is composed of stimulation, focus, attention, decision, and assimilation. A successful AT&E program will begin by meeting the five requirements listed in Table 17-1.
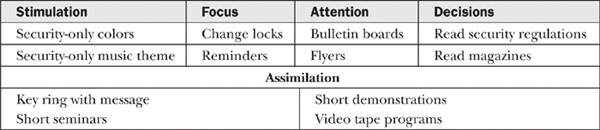
Table 17-1 Awareness Characteristics
In addition to training, literacy is also important. Information assurance literacy places fundamental working knowledge of information assurance into the minds and into the actions of a workforce. This working knowledge should involve both definitions and distinctions; Table 17-2 shows some examples of literacy.

Table 17-2 Examples of Literacy
A literate employee will be able to define appropriate terms, and if well-trained, the employee should be able to make distinctions among the terms.
Information Assurance Training
The distinction between training and awareness is that training aims to teach or improve an individual’s skill, knowledge, or attitude, which allows a person to carry out a specific function, while awareness aims to focus an individual’s attention on an issue or a set of issues.
There is a gray zone between awareness and training. A distinction between them is that in awareness activities the learner is a passive recipient of information, while in the training environment the learner has a more active role in the learning process (see Table 17-3). In other words, awareness explains “what” needs to be done and training explains “how” it should be done. A primary role of awareness programs is to motivate employees/learners to move into a training mode and actively seek more knowledge. A fundamental goal of training programs is to motivate learners to move knowledge and skills from short-term memory to long-term memory. Often, knowledge and skills become chained sequences of behavior that require little higher-level mental processing.

Table 17-3 Training Characteristics
The objective of any information assurance training is to equip personnel with skills that facilitate their security-related job performance. This includes teaching people what is required and the methods and procedures required to do their work. Information assurance training can be categorized from basic information assurance practices to more advanced certification-based programs. It is flexible since it caters either to a unique computer system or to more generic systems. Through training, the organization is on track to produce relevant and required information assurance skills with its related competencies. Refer to Chapter 5 for various certification programs for information assurance professionals. Certification programs are often targeted at the training and experience of an individual.
Information Assurance Education
The distinction between training and education can be made by examining the intent and scope of the instruction. In a training environment, the employee is taught to use specific skills as part of specific job performance. In an education context, the employee would be encouraged to examine and evaluate not only skills and methods of work but fundamental operating principles and tenants upon which job skills are based. The employee is using internalized concepts and skills to perform operations such as analyzing, evaluating, and judging to reach higher cognitive-level decisions that lead to the accommodation of newly integrated knowledge and skill (see Table 17-4). Accommodation is an end process in which the learner makes a conscious decision to modify existing ways of thinking and responding to satisfy new experiences and knowledge.

Table 17-4 Education Characteristics
Through information assurance education, professionals are better able to integrate their information assurance skills and competencies into daily practices. A formal education program allows for acquisition of knowledge, skills, and proper understanding of their role at the holistic level. This will cultivate development of right behaviors, values, and wisdom. People who are in charge of information assurance of the organization should be encouraged to pursue higher education relevant to their job scope. Globalized usage of IT will establish their credibility and give them a fair idea of where they stand at an international level. They can also validate their education by seeking external independent certifications as discussed in Chapter 5.
Further Reading
• ACM Computing Curricula Information Technology Volume: Model Curriculum. ACM, Dec. 12, 2008. http://campus.acm.org/public/comments/it-curriculum-draft-may-2008.pdf.
• An Introduction to Computer Security: The NIST Handbook (Special Publication 800-100). NIST, p. 16.
• CNSSI-4012, National Information Assurance Training Standard for Senior Systems Managers. June 2004. Supersedes NSTISSI No. 4012, August 1997.
• CNSSI-4013, National Information Assurance Training Standard for System Administrators (SA). March 2004.
• CNSSI-4014, Information Assurance Training Standard for Information Systems Security Officers. April 2004. Supersedes NSTISSI No. 4014, August 1997.
• CNSSI-4016, National Information Assurance Training Standard For Risk Analysts. November 2005.
• National Institute of Standards and Technology. Special Publication 800-16, A Role-Based Model for Federal Information Technology/Cyber Security Training. NIST. http://csrc.nist.gov/publications/drafts/800-16-rev1/draft_sp800_16_rev1_2nd-draft.pdf.
• NIATEC training materials web site. http://niatec.info/pdf.aspx?id=169.
• NSTISSI-1000, National Information Assurance Certification and Accreditation Process. CNSS, 2004. www.cnss.gov/Assets/pdf/nstissi_1000.pdf.
• NSTISSI-4011 National Training Standard for Information Systems Security (INFOSEC) Professionals. CNSS, June 1994.
• NSTISSI-4015, National Training Standard for Systems Certifiers. November 2000.
• Rusell, C. “Security Awareness – Implementing an Effective Strategy.” SANS Institute, 2002. www.sansorg/reading_room/whitepapers/awareness/416.php.
• Ryan, D., J.C.H. Julie, and C.D. Schou. “On Security Education, Training, and Certifications.” Information Systems Audit and Control Association, 2004.
• Schou, Corey D., et al. “Defining Information Security Education, Training, and Awareness Needs Using Electronic Meeting Space. In Enabling Technologies for Law Enforcement and Security (pp. 356–367). International Society for Optics and Photonics, January 1999.
• Schou, Corey D., and K.J. Trimmer. “Information Assurance and Security,” Journal of Organizational and End User Computing, vol. 16, no. 3, July/September 2004.
• Schou, Corey D., W.V. Maconacy, and J. Frost. Developing Awareness, Training and Education: A Cost Effective Tool for Maintaining System Integrity. SEC 1993:53–63.
• Schou, Corey D., and D.P. Shoemaker. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2008.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
• User’s Guide: How to Raise Information Security Awareness. European Network and Information Security Agency, Dec. 1, 2006. www.enisa.europa.eu/doc/pdf/deliverables/enisa_a_users_guide_how_to_raise_IS_awareness.pdf.
Critical Thinking Exercises
1. An organization wishes to instill a culture of information assurance throughout its operations. What is the best AT&E level to focus on for all employees?
2. An organization has spent significant resources on several tools and technologies designed to prevent spear phishing attacks. While the number of successful attacks has certainly decreased, the organization is still unhappy with the number of successful attacks. It seems to take only one attack to take down a significant portion of the network for a day or longer. Worse, when the antiphishing technology is configured for aggressive detection, legitimate business information is falsely captured and must be manually reviewed before release. The operations manager is suggesting buying more hardware and technology to further inspect e-mail as it comes into the organization, and the CISO is suggesting a targeted awareness and training campaign focused on spear phishing. Which is the best approach?
