CHAPTER 24
Business Continuity Management
Maintaining or reconstituting an organizational operation under adverse conditions is something that must be fully thought out. The size of an organization does not change the importance of business continuity management (BCM). Even if an enterprise is run from a garage with records in a shoebox, it must be prepared for disaster. Organizations are exposed to major disruptive events that affect their business processes. Hence, BCM becomes both more important and more critical. BCM is part of continuous risk management. BCM is a planning effort and an operational practice involving reactive, diagnostic, and compensating controls for availability and integrity failures. Refer also to Chapter 11 on information assurance risk management.
BCM is a fundamental part of an organization’s recovery process. It is a diagnostic and corrective risk management approach designed to protect an organization’s processes, assets, interests, clients, and business objectives. It provides a framework to assess threats, the susceptibility of systems to the threats, and the effects on the organization. A well-designed BCM plan provides fundamental and reliable controls to protect organizations from outages, denial of services, and operational errors. Comprehensive BCM allows the organization to maintain its integrity, availability, sustainability, and industry competitiveness. BCM ensures critical business resource processes, and outputs are secured, protected, and functional in the event of adverse or disastrous conditions.
This chapter describes the importance of BCM and the associated best practices and the types of planning that supports it. Examples are business continuity planning, business unit resumption planning, crisis management planning, disaster recovery planning, and impact analysis.
Importance of Business Continuity Management
BCM ensures that an organization is ready to face and respond to major disruptions that threaten the operation and survival of the organization. Even if an organization has not experienced a disaster, BCM planning defines key functional areas and processes of the organization, as well as the impact of discontinuity. This allows the organization to prepare for the worst-case scenario and to take steps to improve its resilience to the disruption of resources, infrastructure, and support required by these functions and processes.
Despite the size, nature of business, and whether it is in the public or private sector, an organization always needs to answer to the expectations of government, regulators, insurers, business partners, investors, and other key stakeholders. By having BCM as part of the management practice, organizations may fulfill the expectations.
By maintaining continuity, BCM helps minimize financial impact during serious incidents by protecting tangible and intangible assets. Through demonstrating a professional approach to managing adverse situations, reputation is maintained, and chances of negative publicity are mitigated. When an organization ensures its continuity and proves that essential services will remain uninterrupted, customers remain loyal to the organization. From the employee standpoint, BCM also protects information assets and improves job security.
Critical Success Factors for BCM Implementation
![]()
The following are critical success factors to ensure the sustainability of a BCM program:
• Management support The most important element in sustaining the BCM program is obtaining management support. This ensures the management will allocate resources for this project. In addition to being the key driver of organizational change, management awareness of the scope of business and overall responsibility steers the program and sets priorities for the success of this initiative.
• Accountability and responsibility The BCM initiative establishes reporting levels and individual responsibilities. All departments should know their role in incorporating BCM in its respective functional areas. To ensure all departments are aware of this role and understand the importance of BCM, a BCM team lead should oversee the overall process development and report to management on obstacles faced.
• Integral part of information assurance management program In some organizations, BCM runs in parallel with the information assurance management program. In others, the information assurance management is subordinate to BCM. Regardless of the model adopted, it is imperative not to separate BCM from the organization’s information assurance management program and overall management processes. This allows continuous monitoring and improvement. You should integrate BCM into the total change management process. The rationale for this is to ensure the process remains current, usable, and effective.
Business Continuity Management Processes
The BCM team establishes the objectives and activity scope in conjunction with the chief risk officer. Managing acceptable risk ultimately guides the team. Together, the BCM team develops the continuity planning policy statement for review, approval, and continuous improvement. The team then develops project plans and submits them for the approval by senior management. This approval avoids conflicts and erroneous assumptions. Management must give permission before the program proceeds. The BCM process consists of six stages:
1. Recognize BCP is essential.
2. Identify the business needs.
3. Develop BCM strategies.
4. Develop and implement BCM response.
5. Develop BCM culture.
6. Execute, maintain, and audit.
The phases are illustrated in Figure 24-1.
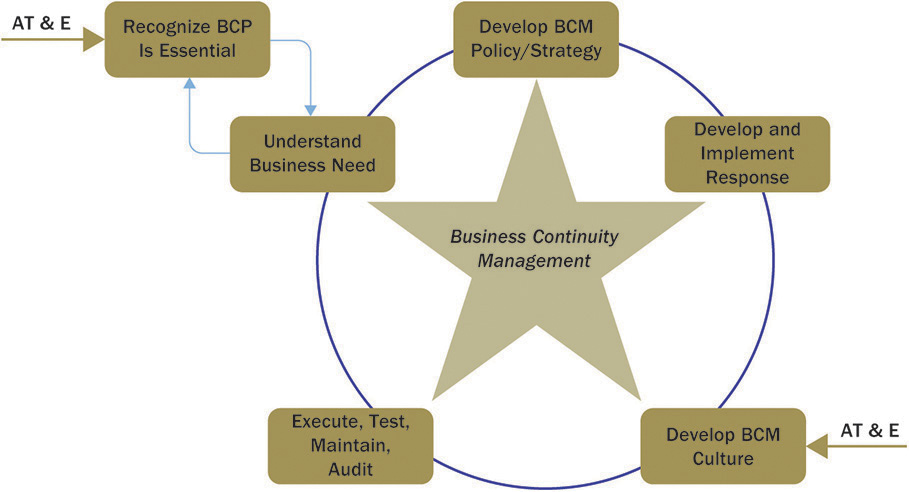
Figure 24-1 Business continuity management life cycle
Stage 1: Recognize BCP Is Essential
Once essential management agrees, establish a BCM program led by the chief risk officer or their designate. The BCM team leader oversees the development and implementation of a BCM program and subcomponents. The BCM team consists of representatives from all functional areas including management, business units, information technology, information assurance, legal, and public relations.
Stage 2: Identify the Business Needs
If an organization does not understand its business and which processes are critical to continued operation, it will not recover from a disaster.
An organization must identify and prioritize critical functional areas and identify minimal acceptable levels of service for each functional area during emergency. The identified functions should meet the objectives stated in the BCM policy. Identify all related supplies, resources, infrastructure, time required for delivery, and processes demanded by critical functional areas. Establish interdependencies among external parties and clearly outline these relationships.
Alignment to Business Strategy and Operations
Before proceeding with business impact analysis and risk assessment, align business continuity to the overall organization’s strategy and operations. By understanding the organization’s direction and focus, the business continuity committee will ensure that it is moving in the right direction to develop strategies and recommendations that suit the organization.
The BCM committee has to understand the organization’s strategy, short-term, and medium-term plans. First, identify current management information goals, input, detailed business processes, output, and quantified value of activity. Then, document all findings at the end of this exercise. This serves as the referencing guidelines to define the scope for the business impact analysis and the risk assessment. Organizations should also consider any regulations, laws, or rules that apply to them. For example, in the United States, ISO 22301 is the voluntary national standard for providing organizational resilience for private entities.
Business Impact Analysis The business impact analysis (BIA) is the groundwork of the BCM process with the objective of identifying functional areas that would suffer the most financial or operational loss in the event of a disruption or disaster. From the collected date, document all department functions, inputs, and processes, to develop a business hierarchy of business functions. The hierarchy provides the basis for classifying the criticality of each function. A business impact analysis identifies and classifies measurable and tangible losses of the business after a disruption to the organization’s business processes. The business impact analysis report provides critical business information in planning for developing strategies for business continuity.
The following are the steps in conducting a BIA:
1. Management establishes the defined scope and terms of reference.
2. Ensure the information-gathering process is effective; select and identify the best interviewees.
3. Design a customized business impact assessment template.
4. Choose an information-gathering technique that will be used (interviews, workshops, questionnaires, qualitative, and quantitative approaches).
5. Use the data collected and determine the organization’s key business functions.
6. Identify the financial, regulatory, and operational impact over time on disruption for each business function.
7. Determine the maximum tolerable outage for these business functions in terms of achieving organizational goals.
8. Execute these business functions and select the key personnel that will be contributing to this initiative.
9. Identify the critical systems, vital records, supply chain, and infrastructure required for the business functions.
10. Estimate the maximum tolerable outage for these critical systems, vital records, supply chain, and infrastructure.
11. Document and present the findings to management.
At the end of the business impact analysis exercise, the BCM committee team should identify all threats to the company and map them to the following characteristics:
• Critical systems, vital data, and records
• Financial considerations
• Image and brand of the organization
• Internal and external relationship for critical functions
• Key personnel for critical functions
• Operational disruption
• Regulatory responsibilities
• Supply chain and infrastructure for critical functions
In BIA, there are two main recovery periods.
• Recovery time objective (RTO) refers to the timeframe during which a recovery should become effective before a disruption prevents the organization from achieving its business objectives and therefore threatens its survival.
• Recovery point objective (RPO) is the time in which data should be restored to after a major disruption.
The information obtained in business impact analysis will contribute directly to organizational recovery strategies in terms of determining the recovery priority. You can find more details on RTO and RPO in Chapter 25.
Risk Assessment
Risk is a measure of the potential consequences of a disaster against the likelihood of it occurring.
During the BCM process, the BCM team or an independent assessor will conduct a risk assessment to identify internal or external risks to the performance and probability of disruption to critical organizational functions. A risk assessment identifies, quantifies, and prioritizes risks against criteria and relevant objectives. The criteria would include critical resources, effect of disruptions, allowable outage time, and recovery priorities. The result prioritizes and focuses activities on critical functional areas identified during business impact analysis.
Involve owners of the business resources and processes during a risk assessment process. Remember that not all critical systems use information-processing facilities—some are manual or paper-based; risk assessment should consider all critical business processes. It is important to link all risks to obtain a complete business continuity requirement.
Identify and document all “single points of failure” during a risk assessment process. The committee should record and analyze threats to the organization and its business processes, address and treat all critical risks, and document the acceptance of unaddressed but identified risks. Refer to Chapter 11 for details on information assurance risk management.
Stage 3: Develop BCM Strategies
After identifying all functional areas that are at risk, decide on the best approaches to protect assets and systems. This stage of the BCM process focuses on identifying the alternatives available to reduce loss and assesses effective solutions. This process ensures the business continues to operate key functions from the time of the business disruption until the function is able to recover operational ability. The information provided by business impact analysis suggests appropriate strategies.
Maximum tolerable outage or the RTO determines the point at which the survival of the organization is threatened by disruption. Strategies that cannot meet the RTO are unacceptable. RPO must also be considered, as some organizations cannot afford to lose information. As RPO and RTO decrease, the cost and resources required to implement those increases.
There are three levels of BCM strategies and strategic planning. All three levels depend on one another. The three levels of strategies are
• Organizational strategy
• Process-level strategy
• Resource recovery strategy
Organizational Strategy
The organizational strategy provides structured well-defined policy and procedures. This ensures the continuity of key functional areas, its dependencies, and single points of failure. During the development of process-level and resource recovery strategy, make a reference to the organization’s loss reduction strategy.
Process-Level Strategy
A process-level strategy provides a documented framework to support a resource recovery strategy, business continuity plan, and BCM capability prototype.
Based on the findings from the BIA, the process-level strategy examines the interdependencies of all activities, processes, data, infrastructure, and technology. There will be various critical business processes within an organization. Develop separate strategies to handle known processes based on their nature and significance. It is important to develop the process-level strategy within the overall organizational BCM scope and coverage.
The output of the process-level strategy exercise will be a documented strategy. The keys are as follows: Secure agreement and approval by top management. Establish a project plan to execute the agreed strategy. Agree upon and document established relationships and positioning of the critical business functions. Establish the general principles and guidelines for developing resource recovery strategies and business continuity plans. After agreement on the principles and guidelines, develop the corresponding business continuity plan for each of the critical business processes, dependencies, and single points of failure.
Resource Recovery Strategy
A resource recovery strategy coordinates and provides the resources required for the execution of the organizational strategy and process-level strategy of the business continuity plan. Consider employees ratios, priority of business processes, location, and technology requirements to determine the resource recovery strategy as well as the organizational process-level strategy. Figure 24-2 illustrates one example of resource recovery strategy. The amount of resources goes up as more resources are made available to aid in business continuity. This in turn provides superior protection for assets and operations.
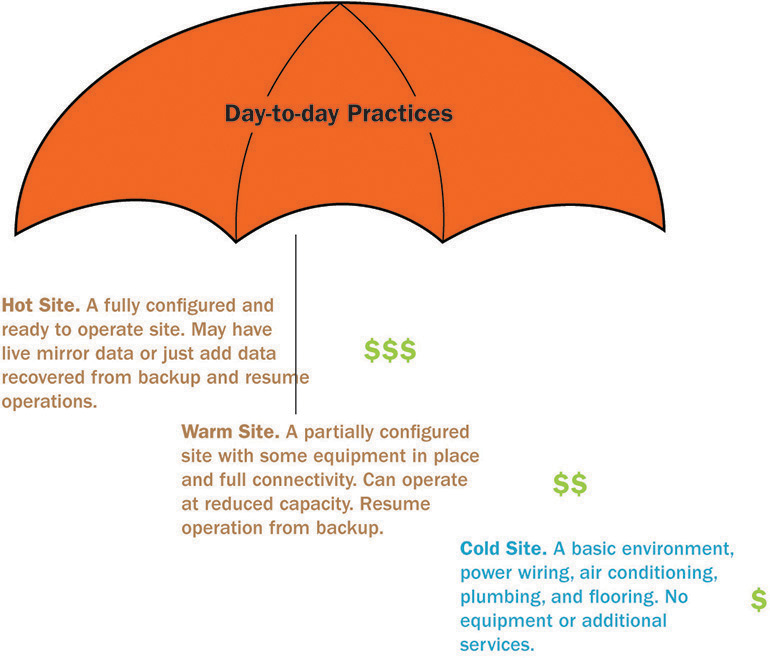
Figure 24-2 Resource recovery strategies
Some of the deliverables of a resource recovery strategy are a managerial endorsement document and defined objectives and a predefined collection of recovery resources and services. The resources and services provide the recovery of business processes within an accepted timeframe and required objectives.
There are many strategies that can be implemented. Specific organizational analysis drives strategies. Therefore, the following are nonspecific and simplified:
• Do nothing The loss of some noncritical functions may be acceptable by the top-level/senior management. Hence, no further action is necessary.
• Change, transfer, or end the process Decisions to alter business processes should consider the organization’s key objectives and any regulatory and legal implications.
• Insure You can turn to financial compensation or support to shift financial risk, but this option will not be able to cater to all impact losses such as reputation and other nonfinancial impacts.
• Mitigate loss Implement some appropriate measures to reduce unacceptable risks within the business.
• Plan for business continuity This is an approach that seeks to improve the organization’s continuity capability in case of major disruptions, therefore allowing for the recovery of key business and system processes within predefined objectives.
Stage 4: Developing and Implementing a BCM Response
After defining organization-wide strategies toward business continuity, develop action plans and identify resources needed to support the plans. The steps in the action plans are not the only course of action. In the real world, every event or crisis is different. Procedures based on the revised strategy may require flexibility for exceptional cases.
As already discussed, there are three primary types of BCM plans. They may be divided into a number of subplan items on specific requirements:
• Business continuity plan (BCP)
• Crisis management plan (CMP)
• Disaster recovery plan (DRP)
• Incident response plan (IRP)
• Information system contingency plan (ISCP)
• Occupant emergency plan (OEP)
Figure 24-3 illustrates the crisis management structures for all six BCM plans. For instance, if an event is out of the scope of assumption of a business continuity plan, the event will be escalated to those implementing the crisis management plan. This structure will enable appropriate levels of authority, ownership, control, and response to be determined during various crises.

Figure 24-3 Crisis management structure
By developing an effective CMP, management demonstrates to the media, stakeholders, markets, customers, and regulators the organization’s capabilities and determinations in crisis management.
The deliverables at the end of a crisis management planning exercise include a plan that can aid the crisis management team during an occurrence of a crisis. Since media response falls under a CMP, it is important to construct a crisis communication plan where the plan will incorporate communication management of media and stakeholders. The following six sections describe these subcomponents.
Crisis Management Plan
A crisis management plan is developed by large organizations or small to midsize organizations with critical missions. The CMP addresses the strategic issues of a crisis affecting the organization. This plan is essential for large organizations and ensures the existence of an organized, versatile, and robust crisis response. The procedures or guidelines in a CMP should be able to handle not only natural disasters but also man-made business and industrial crises. Examples of these are financial risks, marketing risks, credit risks, reputation or brand name risks, white-collar criminals, business fraud, environmental pollution, and hostile takeovers. The CMP manages the media that reports any incidents; however, there are other organizations that use BCPs for the same purpose.
Some CMPs also include important individuals and their families as part of the plan. An organization cannot expect employees to favor acting in the interest of the organization over their own families or loved ones in the time of crisis. Organizations must ensure the families and loved ones are accounted for in the plan and actions are in place to ensure their safety and well-being. If critical employees must perform during crisis situations, the organization must ensure they can account for the safety of family and loved ones and provide evidence to the critical employees of their safety. This may involve the identification and acquisition of alternative housing.
The crisis management plan must also recognize the human nature of grief and shock during a disaster. Disasters take a heavy psychological toll on personnel when there has been loss of life or extensive physical destruction. The CMP should address grief counseling and other mental health support options. The Red Cross and numerous international disaster support organizations may offer support in this area, but the organization should ensure in advance it can count on the resource when needed.
Personnel are often most interested in what matters to them. Payroll is high on the list of worries for employees in a disaster situation. The organization must communicate the status of payroll and health benefits. Every effort should be made to ensure payroll and health benefits operations. Because of employee grief and stress, organizations must be prepared for lower productivity during the adjustment period.
Large or critical organizations must ensure they have established relationships with local law enforcement and emergency responders prior to an emergency event. These organizations are often eager to review BCPs and CMPs and provide input in the resources available locally and nationally. Depending on the organization’s mission and size, local resources may request the organization participate in joint planning and exercises with local, national, or international counterparts. Smaller organizations should review local emergency response resources such as the Red Cross and local government emergency preparation organizations for further guidance.
Business Continuity Plan
As mentioned, the BCP provides procedures for sustaining operations while recovering from disruptions. It addresses organizational mission and business processes at a lower level than the CMP and is more expansive in addressing specific operational plans for information systems and personnel. The BCP activation is determined by the CRO or another designated senior leader.
If the BCP is the pinnacle strategic document for ensuring contingency operations and recovery from disasters, the organization must ensure the crisis management function is included in the BCP. External affairs, public relations, legal, and senior management must be active participants in not only the development of the BCP but also in its testing and ongoing evolution as the organization changes.
The BCP must be updated as part of the change management process. Organizations may grow, shrink, merge, and even dissolve. The BCP and subordinate plans must be updated to ensure changes to the organization are captured and accurately accounted for in contingency and recovery operations. The BCP can quickly become outdated if not comprehensively maintained throughout the change management process. Worse, it may cause further damage during a disaster because it may cause actions based on outdated information and procedures.
Disaster Recovery Plan
A disaster recovery plan is a subset of BCM. Disaster recovery planning minimizes the effect of a disaster and recommends the steps to ensure resources, personnel, and business processes are available. In addition, it ensures that business-critical data is available to resume operation within a predetermined timeframe. A disaster recovery plan focuses on information technology. It references individual information system contingency plans. In contrast, BCM takes a wider approach when dealing with disaster. BCM includes references to occupant emergency plans, incident response plans, and crisis communication plans.
During the process of developing a DRP, the DR team uses information gathered from business impact analysis and risk assessment. Based on the RPO and RTO, a disaster recovery strategy can be determined.
The DRP minimally addresses the following:
• Data recovery The DRP should state the procedures for recovering data from backup storage. The plan should also indicate priorities for data recovery based on the criticality of corresponding business functions. The data recovery sections should reference the ISCPs as necessary.
• Facility recovery The organization needs to decide on the type of offsite facilities that should be acquired, whether a hot site, warm site, or cold site, or whether to engage an external party’s facility via reciprocal agreement.
• Technology and supply recovery To restore a business function and process critical business data, the DRP needs to address several matters such as the recovery of network and computer equipment, voice and data communication resources, software, human resources, transportation of equipment and personnel, environmental issues, data and personnel information assurance issues, supplies such as forms and cabling, and documentation on recovery.
Occupant Emergency Plan
The OEP is focused on protecting personnel and ensuring continuity of their functions. Organizations must focus on people, process, and technology if they want to be resilient in adverse times. The OEP provides coordinated procedures for minimizing the loss of life or injury and protecting property damage in response to threats. Personnel and property specific to a facility, not mission or business processes or information systems, drive the OEP. OEPs are best utilized through reference in the BCP or CMP through initiation immediately after an event but prior to DRP or ISCP implementation (the organization will need its staff to enact much of the DRP and ISCP).
The OEP contains information about the facility layout including where emergency supplies are located. These supplies include stable rations, fresh water, batteries, heat sources, sanitation supplies, light sources, emergency communication devices, and in some cases, biohazard suits or breathing filters. The OEP may also contain the locations of alternate information system operating locations and “safe rooms” that may be on standby until an emergency.
OEPs handle personnel safety and evacuation. Routine testing of the OEP should ensure personnel are aware of their physical security and exit procedures. These aspects of the OEP are best practiced during fire drills. The OEP should contain or reference the need to secure office space, workstations, and laptops to prevent vandalism or theft. Of course, personnel security and safety always comes first. The OEP should contain emergency checklists, which can be posted in workspaces that remind employees to take medications, identification, car keys, and other important items if the nature of the incident and time allow.
OEPs often incorporate a “floor warden” or “floor monitor” approach to ensure proper evacuation and accountability for staff. This approach involves ensuring at least two individuals are selected and trained to be responsible for the evacuation of all personnel. If sufficient personnel exist, this responsibility should be rotated throughout the facility to ensure proper training and understanding of emergency procedures.
The OEP should contain procedures for several crisis situations including, but not limited to the following:
• Active shooter
• Bomb threats
• Earthquakes
• Extreme weather such as tornados and hurricanes
• Fires
• Floods
• Hostile employee
• Pandemics
• Prolonged power outages
Organizations should consider filing their OEP with local emergency responders. While localities differ, many local responders will gladly maintain a copy of the OEP on file. This becomes invaluable because the emergency responder will have the exact locations of shelter areas, safe rooms, and evacuation locations for the organization. This single act can mean the difference between life and death in instances such as fires or earthquakes.
Information System Contingency Plan
The information system contingency plan establishes procedures for the assessment and recovery of an information system following a disruptive event. The ISCP is established by the DRP and covers the roles, responsibilities, inventory information, assessment procedures, detailed recovery procedures, and testing of a system.
While the DRP is a higher-level document in the organization, the ISCP is developed for the recovery of the system regardless of site or location. An ISCP can be activated at a system’s production site or the alternate site. This is in contrast to the DRP, which is a site-specific plan developed with procedures to move operations of one or more information systems from a damaged or uninhabitable location to a temporary alternate location.
Once a DRP is enacted and has successfully transferred an information system site to an alternate site, each affected system would then use its respective ISCP to restore, recover, and test systems prior to putting them back into operation.
Incident Response Plan
The incident response plan establishes procedures to address cyberattacks against an organization’s information systems. The procedures are designed to enable security personnel to identify, mitigate, and recover from malicious computer incidents. The IRP should be referenced in the CMPs, DRPs, BCPs, and ISCPs. You can find more information regarding the incident response process in Chapter 22.
Stage 5: Developing a BCM Culture
Relevant personnel across the organization and dependencies from other organizations must be confident and competent with the BCM program. Even with the best strategy and planning, the system will not be effective without acceptance and commitment from employees.
Since the BCM is integral to the organization’s strategic goals as well as day-to-day management, it must be aligned with organizational business objectives. To remain viable during a disaster, organizations must establish a BCM culture and integrate it into daily business operations with the support of the CRO and senior management. Clearly, management must demonstrate their support and commitment in exercising BCM to extend its life span. As with other changes, there will be resistance to BCM plans; use AT&E to help employees understand the importance of BCM to the organization, the structure of the business continuity team, steps taken during the execution of the BCM action plans, and the level of service required during the emergency. You can find more information regarding awareness, education, and training in Chapter 17.
Three techniques are involved in developing and establishing BCM culture within an organization.
• Design and deliver an awareness campaign to create and promote BCM awareness and develop skills, knowledge, and commitment required to ensure a successful BCM practice.
• Ensure the awareness campaign has achieved its goals and monitor BCM awareness for a longer term.
• Perform an assessment on the current BCM awareness level against the management-targeted level.
Stage 6: Execute, Test, Maintain, and Audit
The reliability of the BCM plan is a function of its implementation and effectiveness. Steps of the BCM plan involve the validation of plans by performing simulations of different scenarios by everyone involved. Examine critical systems (such as a UPS) that provide systemic resilience to ensure both reliability and availability. The frequency of exercises depends on the rate of changes made within the organization. Review the result of earlier exercises during the current exercise to ensure identified weaknesses have been addressed.
In addition to ensuring BCM is in order, the organization should keep it current. Changes in specific areas may require more attention. For example, employee turnover, changes in the organization’s functions or services, changes to organizational structure, changes to details of suppliers or contractors, changes made to risk assessment, and changes to business objectives and processes may require modified BCM processes.
An audit highlights all key material weaknesses and issues. An internal auditor, external auditor, or external professional BCM practitioner can perform an audit/review of the BCM. Both internal and external reviewers should provide an independent view on the organization’s BCM policy, strategies, framework, guidelines, procedures, and standards.
Business Continuity in the Cloud
![]()
Cloud computing offers numerous approaches to not only use cloud technologies to enhance existing “on-premise” systems but also systems instantiated on cloud infrastructures. Organizations should be aware of different concerns with various approaches to cloud computing. The most common uses of cloud computing for business continuity include Infrastructure as a Service (IaaS) and Software as a Service (SaaS).
IaaS and SaaS cloud solutions include virtual machines, virtual servers, storage, software, and, in some cases, communication links. As part of overarching business continuity planning, organizations must understand several aspects of the agreement they have with the cloud provider, such as, but not limited to the following:
• Service level agreements
• Uptime of communications links
• Uptime of servers or workstations
• Reliability of data integrity (RPO)
• Availability of data (RTO)
• Jurisdictional concerns
• Where are the cloud provider’s redundant resources located?
• Are the alternate or redundant resources subject to the same legal jurisdictions as the primary resources?
• Does the cloud provider outsource the contingency operations with another provider with less stringent controls?
• Costs
• Do contingency operations enact a separate cost in addition to existing fees?
• Does the cloud provider charge additional fees for the option to use contingency features of its service?
Further Reading
• DRI International. Generally Accepted Practices for Business Continuity Practitioners. Disaster Recovery Journal and DRI International, 2005.
• Good Practice Guidelines. A Framework for Business Continuity Management. Business Continuity Institutes (BCI). 2005.
• Mitropoulos, S., et al. “On Incident Handling and Response: A State-of-the-Art Approach.” Computers & Security, 25, no. 5 (2006): 351–370.
• SAI Global. Practitioners Guide to Business Continuity Management (HB 292-2006). SAI, 2006.
• Schou, Corey D., and D.P. Shoemaker. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2007.
• Swanson, M., et al. Contingency Planning Guide for Information Technology Systems (SP 800-34). NIST, 2002.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
Critical Thinking Exercises
1. An organization has begun developing its business continuity plan. The organization is small and manufactures packaging for a variety of cosmetic products. The roles of CIO and the CFO are assigned to the same person who has been nominated to lead the task of business continuity. What are the strengths and weaknesses of this approach?
2. Why should information assurance place such an emphasis on crisis management and business continuity when disaster recovery is an IT function?
