C Common Vulnerabilities
by Steven Hernandez, Corey Schou
Information Assurance Handbook: Effective Computer Security and Risk Management Strategies
C Common Vulnerabilities
by Steven Hernandez, Corey Schou
Information Assurance Handbook: Effective Computer Security and Risk Management Strategies
- Cover
- Title
- Copyright Page
- Dedication
- Contents
- Foreword
- Acknowledgments
- Introduction
- Part I Information Assurance Basics
- Chapter 1 Developing an Information Assurance Strategy
- Chapter 2 The Need for Information Assurance
- Chapter 3 Information Assurance Principles
- The MSR Model of Information Assurance
- Information Assurance
- Information Assurance: Business Enabler
- Information Assurance: Protects the Fabric of an Organization’s Systems
- Information Assurance: Cost Effective and Cost Beneficial
- Information Assurance: Shared Responsibilities
- Information Assurance: Robust Approach
- Information Assurance: Reassessed Periodically
- Information Assurance: Restricted by Social Obligations
- Implications from Lack of Information Assurance
- Further Reading
- Critical Thinking Exercises
- Chapter 4 Information Assurance Concepts
- Chapter 5 Organizations Providing Resources for Professionals
- Chapter 6 Information Assurance Management System
- Chapter 7 Current Practices, Regulations, and Plans for Information Assurance Strategy
- Part II Information Assurance Planning Process
- Chapter 8 Approaches to Implementing Information Assurance
- Chapter 9 Organizational Structure for Managing Information Assurance
- Chapter 10 Asset Management
- Chapter 11 Information Assurance Risk Management
- Chapter 12 Information Assurance Policy
- Chapter 13 Human Resource Assurance
- Chapter 14 Advantages of Certification, Accreditation, and Assurance
- Concepts and Definitions
- Purpose of Certification and Accreditation
- Primary Roles for Supporting Certification and Accreditation
- Certification and Accreditation Process
- Certification Baselines
- Considerations for Product Evaluation, Certification, and Accreditation
- Further Reading
- Critical Thinking Exercises
- Part III Risk Mitigation Process
- Chapter 15 Information Assurance in System Development and Acquisition
- Chapter 16 Physical and Environmental Security Controls
- Chapter 17 Information Assurance Awareness, Training, and Education (AT&E)
- Chapter 18 Preventive Information Assurance Tools
- Chapter 19 Access Control
- Part IV Information Assurance Detection and Recovery Processes
- Chapter 20 Information Assurance Monitoring Tools and Methods
- Chapter 21 Information Assurance Measurements and Metrics
- Chapter 22 Incident Handling
- Chapter 23 Computer Forensics
- Chapter 24 Business Continuity Management
- Chapter 25 Backup and Restoration
- Part V Application of Information Assurance to Select Industries
- Chapter 26 Healthcare
- Overview of Information Assurance Approach
- Healthcare-Specific Terminology
- Information Assurance Management
- Information Assurance Risk Management
- Risk Mitigation
- Policy, Procedures, Standards, and Guidance
- Human Resources
- Certification, Accreditation, and Assurance
- Information Assurance in System Development and Acquisition
- Physical and Environmental Security Controls
- Awareness, Training, and Education
- Access Control
- Continuous Monitoring, Incident Response, and Forensics
- Business Continuity and Backups
- Further Reading
- Critical Thinking Exercises
- Chapter 27 Retail
- Overview of the Information Assurance Approach
- Information Assurance Management
- Information Assurance Risk Management
- Risk Mitigation
- Policy, Procedures, Standards, and Guidance
- Human Resources
- Certification, Accreditation, and Assurance
- Information Assurance: System Development and Acquisition
- Physical and Environmental Security Controls
- Awareness, Training, and Education
- Access Control
- Continuous Monitoring, Incident Response, and Forensics
- Business Continuity and Backups
- Further Reading
- Critical Thinking Exercises
- Chapter 28 Industrial Control Systems
- Overview of the Information Assurance Approach
- Industrial Control–Specific Language
- Information Assurance Management
- Information Assurance Risk Management
- Risk Mitigation
- Policy, Procedures, Standards, and Guidance
- Certification, Accreditation, and Assurance
- Human Resources
- Information Assurance in System Development and Acquisition
- Physical and Environmental Security Controls
- Awareness, Training, and Education
- Access Control
- Continuous Monitoring, Incident Response, and Forensics
- Business Continuity and Backups
- Further Reading
- Critical Thinking Exercises
- Chapter 26 Healthcare
- Part VI Appendixes
- A Suggestions for Critical Thinking Exercises
- B Common Threats
- C Common Vulnerabilities
- D Sample Information Assurance Policy for Passwords
- E Sample Risk Analysis Table
- F Select Privacy Laws and Regulations by Country/Economy or State
- G Information System Security Checklist
- H References and Sources of Information
- I List of Acronyms
- Glossary
- Index
APPENDIX C
Common Vulnerabilities
Vulnerabilities are flaws that create weaknesses in the overall information assurance of the system or network. This appendix will provide a general overview of types of vulnerabilities and the nature/effect of those vulnerabilities.
NOTE This list is inspired by and adapted from the BSI (Bundesamt für Sicherheit in der Informationstechnik) threat list.
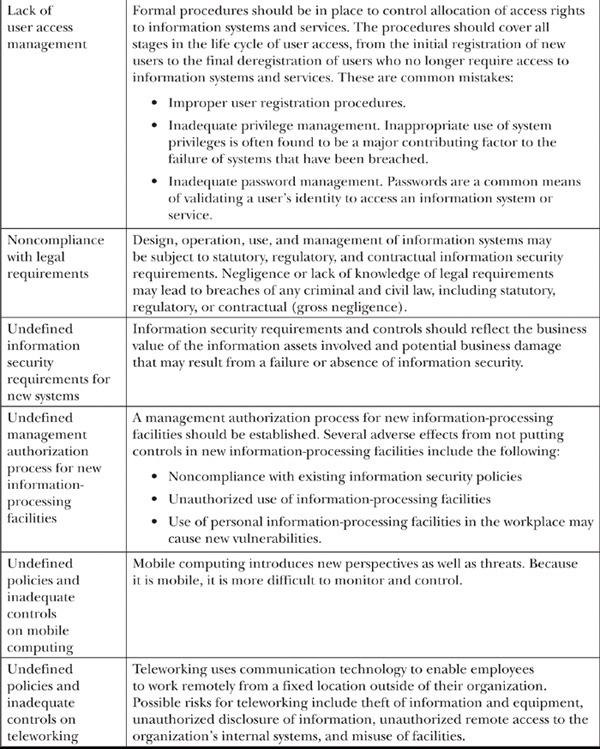
Vulnerability: Organizational Shortcomings
An organization that has poor planning and implementation habits introduces vulnerabilities. Throughout the organizational planning process, you should make sure information assurance is kept in the list of high-importance items. The following are the vulnerabilities in this category:

Vulnerability: Technical Shortcomings
Technical vulnerabilities are frequently derived from managerial shortcomings. For example, the first vulnerability points to a failure to plan; however, this yields technical vulnerabilities. The following are the vulnerabilities in this category:
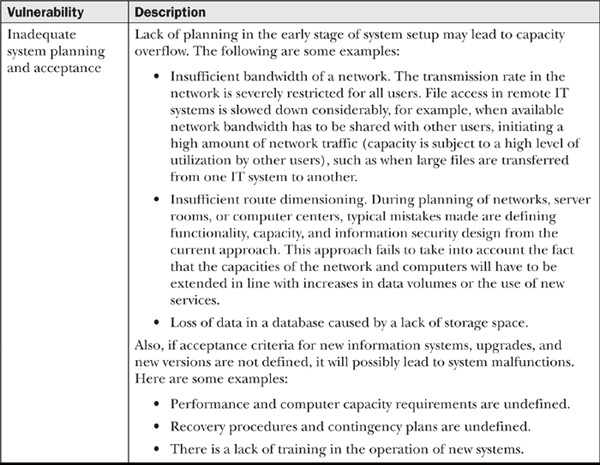
Vulnerability: Procedural Shortcomings
Vulnerabilities are introduced by having poor policies or good policies that do not have sound supporting procedures. Technology will fail if it is not supported by policies, procedures, and people. The following are the vulnerabilities in this category:

-
No Comment