CHAPTER 6
Information Assurance Management System
Information assurance is not dependent on the size of an organization nor is it an once-in-a-lifetime event. It is an ongoing process. The Maconachy-Schou-Ragsdale (MSR) model points out that technology does provide some protection to information assets. However, technology alone is not enough. If an organization does not have a set of well-designed policies and procedures serving as the foundation of information assurance initiatives, deploying even the best technology would be worthless. Organizations of any size can effectively reduce risk exposures by having processes in place that address security.
Implementing and maintaining a high-quality information assurance program requires constant business process engineering and reinvention. However, you must remember that reinvention implies that at some point in the past invention occurred. With the exception of mature organizations (see Chapter 9), processes were never invented; they grew, evolved, and were controlled by bureaucratic rule systems. If they had been invented, there would be some sort of master plan for the system. This plan would include a description of the environment and how it is connected to the organization being reinvented and how to modify itself to contend with a changing environment. If it is true that there is no master plan, you must use a different approach to identify the environment and the organizational processes. If an organization does not establish an information assurance strategy, it must be prepared to implement information assurance through cultural and similar levels of influence.
Organizational processes are changing every day and are frequently distinguished by the formation of autonomous workgroups or teams. Team-based mission-driven organizations are characterized by their reliance on empowerment and knowledge-enabled workers. This transition requires a complete revolution in how individuals interact with their organizational cohorts. To initiate this transition, senior leaders may well use some advice from Peter Drucker in his book The Age of Discontinuity.
Knowledge is either relevant to a task or irrelevant to the task. The task decides, not the name, the age, or the budget of the discipline or the rank of the individual plying it. Knowledge is to be organized as a team in which the task decides who is in charge, when, for what, and for how long.
He points out that although modern, knowledge-based workers still require an organizational superior, the knowledge work knows no hierarchy because there is no higher or lower knowledge. Therefore, information assurance programs and the associated management must be prepared to not only lead knowledge-based work teams but also manage the freely flowing nature of knowledge.
The absence of a knowledge hierarchy means that senior leaders must strive to lead information assurance management without forcing a dysfunctional bureaucratic structure. In reengineered organizations, decisions are made on a just-in-time (JIT) basis by assembling ad hoc decision teams with knowledge particular to the problem at hand. Incident response as described in Chapter 22 and business continuity planning as described in Chapter 24 are excellent examples of ad hoc team formation. These teams contain individuals from all levels of the organization. In addition, organizations that rely on knowledge workers must recognize that information is an asset to be protected and allocated as a strategic and sometimes scarce resource.
To establish integrated information assurance programs, organizations must break down three traditional barriers. The first is bureaucratic systems, the second is a failure to empower while relying on short-term thinking, and the third is a failure to identify stakeholders correctly. Information assurance management strives to overcome these three challenges through the development of systems incorporating people, processes, and technology to ensure information assurance processes are not viewed as invasive but rather pervade the fabric of the organization.
To manage information assurance effectively and efficiently, there is a need to establish a system. This system is the information assurance management system (IAMS). The IAMS combines the MSR components of people, process, and technology, and it is based on a sound risk management approach to protecting information assets. It stresses the importance of a process-based approach in managing and improving information assurance. The information assurance components of people, process, and technology will be elaborated further in Chapter 9.
Effective IAMSs are described in ISO/IEC 27001 and other related standards published jointly by ISO and IEC. To achieve continuous improvement in managing information assurance, ISO/IEC 27001 incorporates the typical Plan-Do-Check-Act (PDCA) approach that is the central discussion point in this chapter. The PDCA model can be used to drive information assurance initiatives effectively.
This chapter first establishes security considerations made throughout the information asset life cycle. This is followed by a discussion on the PDCA model as found in ISO/IEC 27001.
Security Considerations for the Information Asset Life Cycle
Information has life cycles. The term information life cycle means the cyclical stages through which information flows, typically characterized as creation, processing, use or transmission, storage, retention, and eventually disposal.
Organizations constantly acquire data from their environment as well as create information internally. Both data and information are processed and used to meet organizational goals and objectives. The result is stored for retrieval and later use. Information may be archived and retained as part of legal requirements. Finally, when the organization has no use for it, the information is disposed.
Figure 6-1 provides a model for the information asset life cycle. The model shows the stages that information assets pass through during their life cycle.
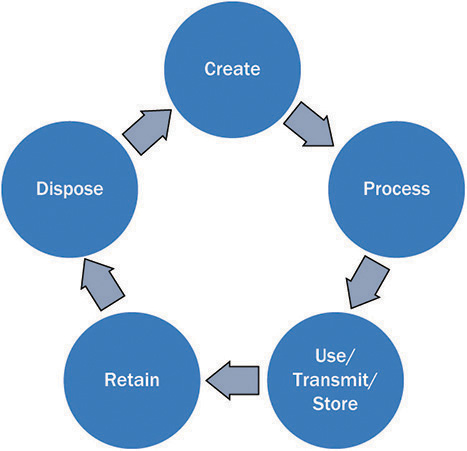
Figure 6-1 Information life cycle model
As explained earlier, information assets are constantly under threat. These threats may be internal or external sources and can be caused by accidental or malicious acts. Using technology to transmit, store, process, and retrieve information increasingly exposes organizations to emerging threats. As information is becoming better recognized as a valuable business asset, security considerations should be incorporated throughout the information asset life cycle to preserve the confidentiality, integrity, availability, and usability of information.
Since information should be secured throughout its life cycle, securing information assets against the full spectrum of threats requires a process-oriented approach. The following section discusses the most commonly used process model, named the PDCA model from ISO/IEC 27001, which can be used to drive information assurance initiatives effectively.
Plan-Do-Check-Act Model
The Plan-Do-Check-Act model demonstrates the process of managing security throughout the life cycle. This includes the implementation of a continuous improvement process to attain an effective information assurance management system. The IAMS is adaptable to future changes and developments, business objectives, requirements, and processes; in addition, it reflects the needs of customers, suppliers, and business partners. The best-known example of the PDCA specification of IAMS is in the international standard ISO/IEC 27001 and its supporting standards in the ISO/IEC 27000 ISMS family.
The PDCA model highlights the fact that improvement programs initiate thorough planning, result in effective actions, and progress through planning in a continuous improvement cycle.
The outcome of each PDCA cycle is a managed information assurance environment in the organization.
![]()
Figure 6-2 depicts how the PDCA steps fit together.
• Plan Establish the IAMS.
• Do Implement, operate, and maintain the IAMS.
• Check Monitor and review the IAMS.
• Act Execute, maintain and improve the IAMS.

Figure 6-2 PDCA model applied to IAMS process
Based on the PDCA model, the information assurance requirements and expectations from the board members, stockholders, customers, business partners, and regulators are inputs. The output is an information assurance system satisfying the requirements and expectations mapped to the organization’s business needs and objectives. The main stages of the PDCA model are described next.
Plan
As the name suggests, this phase is about initial planning for the IAMS. This phase requires meticulous documentation of decisions and the associated criteria. This phase focuses on establishing and documenting the IAMS. The main outcomes of this phase are establishing a documented information assurance policy, defining the scope of the IAMS, and defining a risk management approach (consisting of risk assessment and a risk treatment plan). It is essential that everything related to the planned activities is well documented for management purposes, internal audits, and traceability. This is the planning baseline for implementation.
The parts that make up the Plan phase are as follows:
• Defining the scope of the IAMS. It could be the whole organization or a particular site. This is a management decision.
• Planning and documenting the IAMS policy that sets out basic concepts for information assurance management.
• Determining a systematic approach to risk assessment, that is, clarifying and documenting risk assessment procedures and risk acceptance criteria.
• Identifying the risks by identifying and evaluating information assets, identifying the likelihood of threats, and identifying the loss impact should the threat take place.
• Performing risk assessment (analyzing and evaluating the risks).
• Determining the possible options of the risk treatment that will be adopted that will enable the selection of the control and control objectives.
• Preparing the statement of applicability (SOA). The SOA documentation includes control objectives along with the reason for their selection. It also includes a list of nonapplicable controls with justification for their omission.
Since risks keep changing based on the environmental dynamics, risk management is an ongoing activity. Assess these risks continually to provide protection to exposed assets. The process of reevaluating the risk will be conducted during the Check phase.
Do
The Do phase focuses on implementing and operating the controls selected and planned in the previous phase. The security policy, controls, processes, and procedures are now put into practice. This phase is outlined as follows:
• Defining, implementing, and operating methods to measure control effectiveness.
• Determining the appropriate management actions and priorities for controlling information security risks. This includes the allocation of organizational resources, roles, and responsibilities.
• Developing a risk treatment plan clarifying the activities to be executed to minimize unacceptable risks.
• Developing and implementing procedures for the detection of security incidents to minimize the damages caused if an incident occurs. It is important to check the procedures periodically.
• Implementing and operating the selected controls based on the risk assessment results.
• Implementing and operating training and awareness programs.
• Preparing procedure manuals to govern the operations needed for the controls in place.
Check
This phase assesses the performance of the IAMS process. The primary activity is management review, which is a series of processes in which management observes the effectiveness of the IAMS (in other words, that security controls are in place and achieving their objectives) and makes decisions on improving it. The parts that make up this phase are as follows:
• Executing, monitoring, and reviewing procedures
• Measuring control effectiveness
• Reviewing and re-assessing the risk and residual risk periodically
• Conducting reviews of the effectiveness of the IAMS at regular intervals
• Conducting internal IAMS audits at planned intervals
• Performing a formal periodic review of the IAMS to ensure that the scope remains sufficient and improvements in the IAMS process are identified and implemented
• Recording actions and events that could have an impact on the effectiveness or performance of IAMS
Act
The Act phase focuses on continually improving the effectiveness of the IAMS. Implementing corrective and preventive actions based on the results of the management review is essential. This phase is as follows:
• Implementing and operating the improvements identified in the IAMS
• Implementing corrective and preventive actions
• Communicating the results and actions with all responsible parties
• Ensuring that the improvements accomplish their intended objectives
Ongoing iteration of the PDCA cycle ensures that the organization continues to manage existing, emerging, and new risk issues in the organization and IT environment as they evolve over time. Thus, this guarantees continuous improvement and demonstrates the seriousness of the organization toward information assurance.
For effective and comprehensive implementation, organizations should adopt the PDCA model when developing the process of IAMS. The PDCA requirements are defined and mandated in the internationally accepted information security standard ISO/IEC 27001. This standard defines other mandatory requirements, all of which must be complied with to claim compliance with this international standard.
Boyd’s OODA Loop
U.S. Air Force Colonel John Boyd developed the Observe, Orient, Decide, and Act (OODA) loop to help describe strategic military operations. Boyd’s intention was to develop a framework that would help soldiers direct their resources toward defeating an enemy. Boyd’s loop consists of the following phases:
• Observe Gather raw information about the situation at hand. Be as accurate and thorough as possible.
• Orient This step is designed to weed out bias and includes areas such as genetic heritage, cultural tradition, and previous experiences. Boyd often stated this is the most important phase because these areas inherently influence thoughts. When done properly, this phase can help confuse an adversary because they will make decisions based on the perceived biases.
• Decide Based on the output of the orientation, a decision is made to act.
• Act The action is performed.
Organizations and senior leaders who can complete the OODA loop faster than others hold a distinct competitive advantage in both the marketplace and information assurance situational awareness. Managers frequently rely on the thoughts of American revolutionary Patrick Henry, who said: “I have but one lamp by which my feet are guided and that is the lamp of experience. I have no way of knowing the future but by the past.” An important feature of the OODA loop is that the bias of past events and previous experience does not cloud their thinking. Senior leaders must understand a zero-day event may not behave like previous events and the mitigation actions of the past may have already been accounted for by the adversary (they may be performing their own OODA or PDCA process!).
The Kill Chain
Another important concept comes from the U.S. military targeting doctrine that describes the kill chain as find, fix, track, target, engage, and assess (F2T2EA). All steps of the process must be successfully performed to produce the desired outcome. In information assurance and cybersecurity industries, many variations of this concept exist. They often involve an adversary studying an organization as a target, developing or acquiring a suitable payload for attack, attacking, and then observing the results before attempting their next move.
If an adversary’s kill chain is understood, then efficient and multifaceted disruption methods can be developed to prevent an attack. Through careful restriction of firewall ports and services, it becomes harder to find vulnerable services. Through the use of continuous monitoring and patching, vulnerabilities become harder to target, and hardened systems and intrusion prevention systems lessen the impact of engagement. And careful use of system error messages and reporting discloses little for assessment and observation.
Organizations can merge the PDCA, OODA, and kill chain approaches to help determine the best security architecture for the organization and therefore the best defense-in-depth approach. Organizations that perform continuous risk management and OODA and apply the kill chain analysis will fare substantially better than organizations focusing on a single technology or deep technical solutions for risk mitigation.
Further Reading
• Brehmer, B. “The Dynamic OODA Loop: Amalgamating Boyd’s OODA Loop and the Cybernetic Approach to Command and Control.” 10th International Command and Control Research and Technology Symposium, 2005. pp. 1–15.
• Dove, R. “Embedding Agile Security in System Architecture.” Insight 12, no. 2 (2009): 14–17.
• International Organization Standardization and the International Electrotechnical Commission 2013 Information Technology – Security Techniques – Code of Practice for Information Security Controls (ISO/IEC 27002). ISOIEC. www.iso.org/iso/home/store/catalogue_ics/catalogue_detail_ics.htm?csnumber=54533.
• Maconachy, V.C., et al. “A Model for Information Assurance: An Integrated Approach.” Proceedings of the 2nd Annual IEEE Systems, Man, and Cybernetics Information Assurance Workshop, West Point, New York. June 5–6, 2001. pp. 306–310.
• Mitropoulos, S., et al. “On Incident Handling and Response: A State-of-the-Art Approach.” Computers & Security, 25, no. 5 (2006): 351–370.
• Nichols, R. Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves. McGraw-Hill Education, 2000.
• Schou, Corey D., et al. “Business Process Reengineering: Increasing Empowerment And Enablement.” Proceedings Federal Software Technology Conference. Salt Lake, Utah. April 1995.
• Schou, Corey D., et al. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2007.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
• Von Lubitz, Dag KJE, et al. “All Hazards Approach to Disaster Management: The Role of Information and Knowledge Management, Boyd’s OODA Loop, and Network-Centricity.” Disasters. 32, no. 4 (2008): 561–585.
Critical Thinking Exercises
1. Why is the planning phase extremely important for an organization?
2. Should all controls be subject to the ongoing Check phase?
