Cyberspace as a domain for modern warfare creates a lot of complexities that don’t exist in other types of conflicts. You cannot visually identify the enemy, nor be sure what his nationality is. The one thing that you can count on is that someone has to pay for the necessities of virtual combat. Therefore, one sound strategy in any cyber investigation is to follow the money trail created by the necessary logistics of organizing a cyber attack—domain registration, hosting services, acquisition of software, bandwidth, and so on.
One of the main reasons why malicious activities can prosper online is due to lax verification of domain registration data, also known as WHOIS information. Starting with Internet Corporation for Assigned Names and Numbers (ICANN) and continuing with hosting companies and accredited domain registrars of all sizes, verification is not universally enforced.
Fortunately, one of the forensic methods that can crack false identity data is the global trend toward social computing. In the digital world of the Internet, as in physical space, you leave evidence of where you’ve been.
If you’re an ardent social computing fan who is active in Facebook, MySpace, LiveJournal, or Twitter, your virtual footprint will be very extensive. If you make your living on the Internet as a web service provider or forum administrator, your footprint will be even larger.
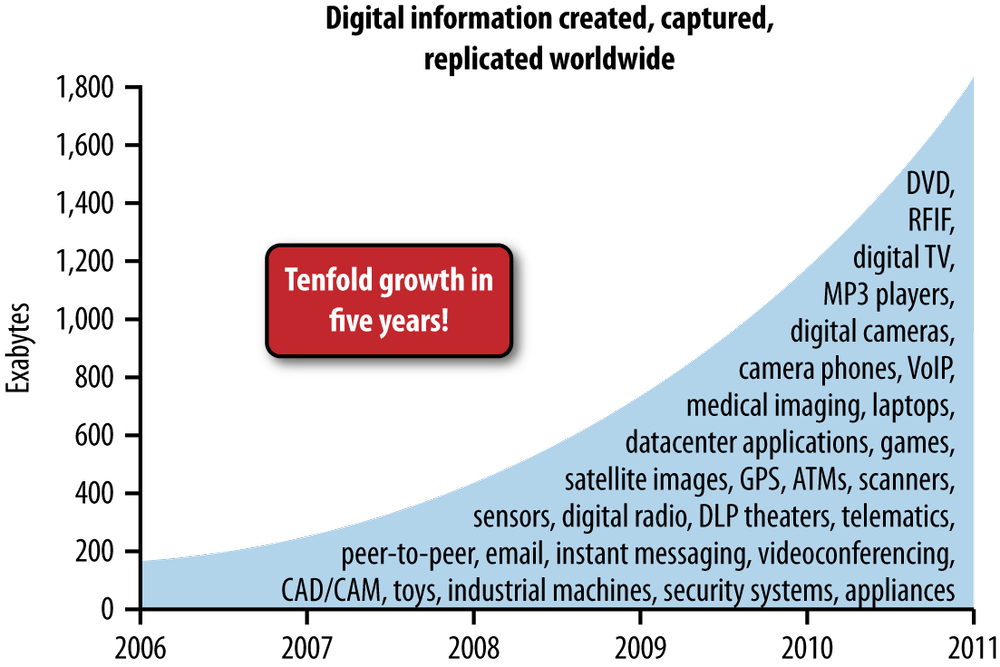
The IDC is an organization that studies how much data is generated by individuals and businesses each year (Figure 7-1). According to the IDC whitepaper “The Diverse and Exploding Digital Universe” (March 2008), “the digital universe contained 281,000,000,000 gigabytes, which works out to about 45 gigabytes per person on the planet.” Of that, half is due to an individual’s actions online. The other half is what the IDC refers to as your digital shadow—ambient content created by others about you (video on traffic cameras or at ATMs, credit card transactions, medical records, etc.).
Now imagine that you want to create a forum to recruit, train, and launch cyber attacks against state networks or websites. You won’t use your real name or known alias for fear of reprisals. Instead you’ll create a fictitious name for your domain registration and/or server hosting plan that cannot be traced back to you.
This is not as easy as it sounds, because some domain registrars will attempt to verify the authenticity of the information that you provide. Your name and address may also have to match those attached to the credit card that you use to make the purchase. This poses a serious problem for those individuals who want to act surreptitiously.
Because of that, members of the cyber underground have identified which hosting providers and domain registrars have lax verification and payment policies, and patronize them exclusively. The Russian Business Network (RBN) is a prime example. Although the RBN went dark in November 2007 after an increasing amount of attention was being paid to its operations, some of the IP blocks associated with it are still active.
The genius of the RBN was that it built a bulletproof loop that guaranteed its online businesses uninterrupted service, regardless of how many complaints were filed against its various websites.
Like the RBN, the StopGeorgia.ru forum is part of a network that’s been bulletproofed. The rest of this chapter walks you through the intricate relationships, aliases, and shell companies that were created to serve that purpose. Before getting to the specifics of the StopGeorgia.ru network, let’s begin with an introduction to how bulletproofing works.
A bulletproof network refers to a series of business relationships that make it extremely difficult for authorities to shut down web enterprises engaged in criminal activities.
Every bulletproof network begins with the inherent weakness of ICANN to enforce accurate WHOIS information.
ICANN is a nonprofit organization with headquarters in Marina del Rey, CA. The organization took over registration and accreditation responsibilities from the US government in 1998.
When you register a domain name with an accredited registrar, ICANN issues a corresponding IP address. The registration process requires that the customer provide accurate WHOIS information. Unfortunately, ICANN hasn’t been effective in enforcing its own rules.
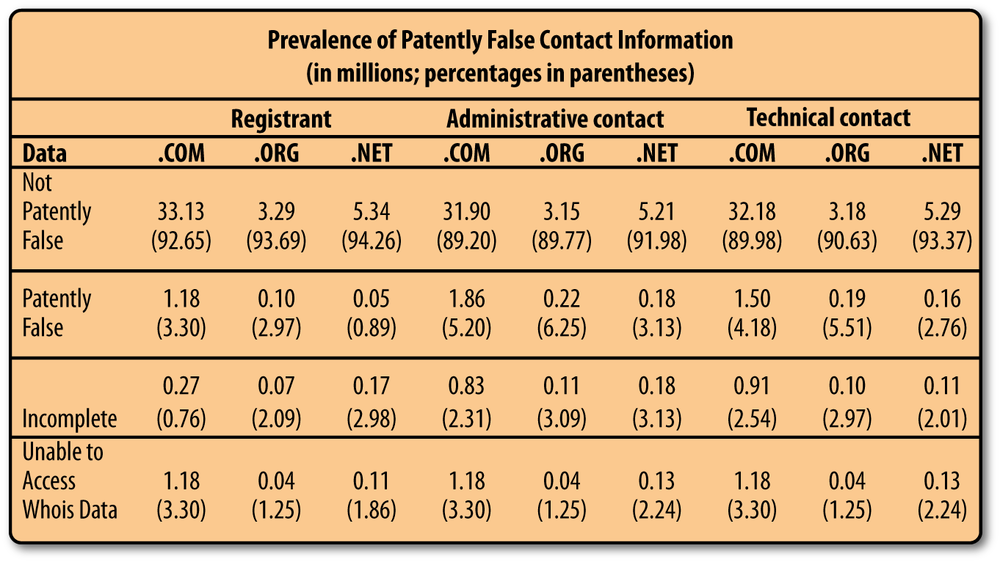
A GAO audit in 2005 looked into this problem and found that an estimated “2.31 million domain names (5.14 percent) have been registered with patently false data—data that appeared obviously and intentionally false without verification against any reference data—in one or more of the required contact information fields” (from the GAO report “Internet Management—Prevalence of False Contact Information for Registered Domain Names,” published in November 2005; see Figure 7-2).
ICANN relies on registrars to enforce the collection of accurate registration information, which is level two of the bulletproof network: an ICANN-accredited registrar.
A person who wants to create an Internet presence for nefarious purposes needs to find an accredited registrar that won’t seek to verify false registration information. This will allow her to enter a pseudonym instead of her real name, as well as false contact information (email and telephone). In the case of StopGeorgia.ru, that registrar was Naunet, a Russian Internet services company that offers domain registration and hosting services.
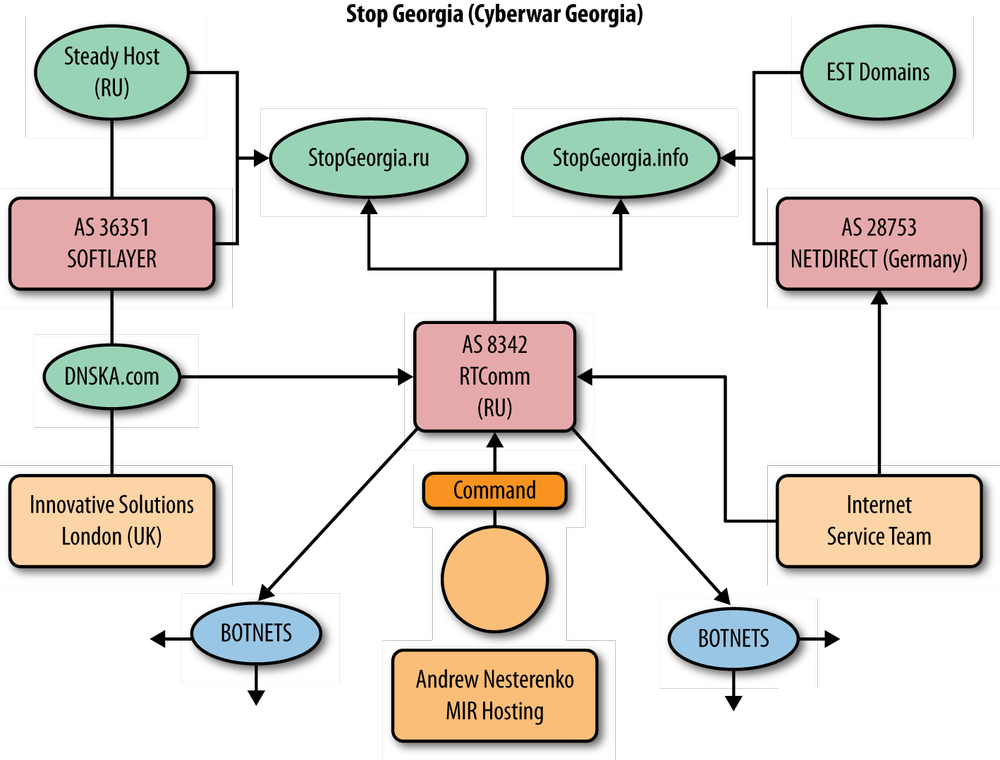
In the case of StopGeorgia.ru, the registrant acquired hosting services through a small Russian company, SteadyHost.ru, which in turn was a reseller for a London company, Innovation IT Solutions Corp, which contracted with a very large data center and hosting company, SoftLayer Technologies.
SoftLayer Technologies and The Planet, both based in Texas, have proven to be attractive options for spam and phishing websites, as had Atrivo/Intercage, based in Northern California. Atrivo was finally shut down in October 2008, resulting in a temporary world-wide plunge in spam levels, according to the Washington Post’s Security Fix column of October 9, 2008.
Figure 7-3 shows linkages between companies that support the StopGeorgia.ru forum.
As we discussed in Chapter 2, StopGeorgia.ru was a password-protected forum built with a bulletin board software application (phpBB) and launched within 24 hours after the commencement of Russia’s ground, sea, and air assault on the nation of Georgia on August 8, 2008.
Cyber attacks against Georgian government websites occurred as early as July 21, 2008, but this particular forum was not active until the day after the invasion. It provided hackers of all levels with vetted target lists, links to malware to be used to attack Georgian government websites, and expert advice for novice hackers (of which there were many).
A WHOIS search on the StopGeorgia.ru domain revealed the following information:
Domain | |
Type | CORPORATE |
Nserver | ns1.gost.in |
Nserver | ns2.gost.in |
State | Registered, Delegated |
Person | Private Person |
Phone | +7 908 3400066 |
Registrar | NAUNET-REG-RIPN |
NAUNET is a Russian registrar that is blacklisted by the Spamhaus Project for providing cyber crime/spam/phish domains (Spamhaus SBL advisory #SBL67369 01 Dec 2008).
The domain name StopGeorgia.ru was acquired at Naunet.ru. Part of the complaint against Naunet on file at Spamhaus is that it has knowingly accepted false information (specifically related to invalid IP DNS addresses in the WHOIS info), which is in violation of Russian Institute for Public Networks (RIPN) rules.
In the WHOIS info for StopGeorgia.ru, the phone number 7 908 3400066 and email address [email protected] are both listed in the registrar information for a variety of websites selling things such as fake passports, adult porn, and ATM skimmers.
Although the domain information for StopGeorgia.ru doesn’t list a person’s name, opting instead for the ubiquitous “private person,” other domains with the same telephone number and email address have been registered under the name Andrej V Uglovatyj.
Andrej V Uglovatyj, however, is most likely a fictitious person. A search on Yandex.com returns only two unique hits for the name. Considering the amount of data being collected online for individuals today, as well as the fact that Andrej V Uglovatyj is purportedly conducting a number of businesses online, receiving so few hits can only be due to this name being a pseudonym used in shady domain registrations. For example, see the one shown in Figure 7-4 for fake passports at a website named Dokim.ru.
The tagline under Dokim.ru reads “Creation of passports and driver licenses for Russia and EU countries.”
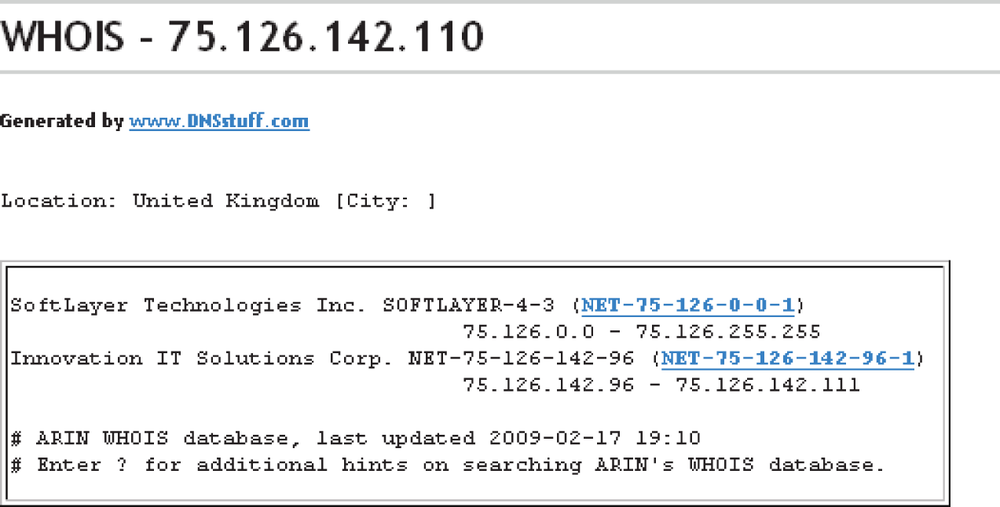
Performing a WHOIS on the IP address is an important step in the money trail process. Someone needed to purchase time on a server to host the PHP forum, which, ironically, used the Army-themed forum template (the ever-stylish camouflage look). The StopGeorgia.ru IP address is 75.126.142.110, which resolves to a small Russian company called SteadyHost (http://www.Steadyhost.ru).
The domain registration for Steadyhost.ru provides the following information:
Domain | |
Type | CORPORATE |
Nserver | |
Nserver | |
State | Registered, delegated |
Person | Sergey A Deduhin |
Phone | +7 905 4754005 |
****@steadyhost.ru | |
Registrar | RUCENTER-REG-RIPN |
Created | 09/30/06 |
Paid till | 09/30/09 |
Source | TC-RIPN |
Sergey A. Deduhin, the person who registered the domain name Steadyhost.ru, doesn’t seem to have any more of an Internet footprint than StopGeorgia.ru’s Andrej V Uglovatyj.
According to contact information at SteadyHost’s website, it has its office in an apartment building at 88 Khoroshevskoe Shosse, Moskva (Moscow).
SteadyHost’s neighbor, in the adjacent building, is the Ministry of Defense Research Institute called the Center for Research of Military Strength of Foreign Countries. And just down the block, at 76 Khoroshevskoe Shosse, is GRU headquarters, also known as the Aquarium (see Figure 7-5).
The GRU is the Main Intelligence Directorate of the Russian Armed Forces. Its primary business is deploying several thousand spies in foreign countries for political and military information gathering.
According to the Federation of American Scientists (FAS) website, the GRU may be thought of as the Russian equivalent of the US Defense Intelligence Agency (DIA). It is involved in the collection of human intelligence (HUMINT) via foreign agents, signals intelligence (SIGINT) via various electronic mediums, and image intelligence (IMINT) via satellite imagery.
In a 1996 interview with Pravda, General Fedor Ladygin, the leader of the GRU at that time, included technical espionage among the missions of his organization (Komsomolskaya Pravda, 05 November 1996). This included hacking computer networks to gain access to sensitive data.
The current leader, General Valentin Korabelnikov, added open source intelligence (OSINT) to the GRU’s mission, according to an interview with CDI Russia Weekly on July 17, 2003. The physical location of Steadyhost.ru’s “office” near GRU headquarters is circumstantial and is not offered as proof of GRU involvement; it is simply one element among many to be considered when weighing possible state connections to the attackers.
Most legitimate registrars will confirm at least some of the registration information provided by a customer as part of the process of registering a domain name. Those that don’t have become favorites of spammers and cyber criminals.
If you look closer at the information provided on the StopGeorgia.ru IP address, you’ll see that it is part of an IP block subdelegation leased to Innovation IT Solutions Corp in England by SoftLayer Technologies in Dallas.
Innovation IT Solutions Corp had a website URL, http://init-sol.com, but no website. Instead visitors see a placeholder page providing basic contact information (Figure 7-6).
According to WHOIS data, the Init-sol.com domain name was registered by an employee of Innovation IT Solutions Corp named Andrey Nesterenko. Mr. Nesterenko purchased the domain name through another company—MIRhosting.com.
If you examine the WHOIS records in the following table, you’ll see that Mr. Nesterenko is apparently employed by both companies, and both companies have the same business address: 95 Wilton Road, Suite 3, London. A Google search for that address brings up a variety of businesses, including a porn site (Cheeky-Touch), a teen site, Goldstein Equitas, Inc., and Global Securities Consulting; in other words, 95 Wilton Road, Suite 3, London, is a mail drop.
Domain name | |
Registrant | Innovation IT Solutions Corp Andrey Nesterenko 95 Wilton Road, Suite 3 London London,SW1V 1BZ GB Tel. +44.8458692184 Fax. +44.8450205104 |
Creation date | 10/10/04 |
Expiration date | 10/10/09 |
Domain servers | |
Administrative contact | Innovation IT Solutions Corp |
Status | Active |
Innovation IT Solutions Corp is not a registered business in the UK or anywhere else, and it doesn’t seem to exist outside of its London mail drop address.
Mirhosting.com provides some substantive information on its website regarding its services, albeit in the Russian language. According to Dun and Bradstreet, its principal and sole stockholder, Andrey Nesterenko, is a Russian national living in the Netherlands, yet his business address is a mail drop in London—the same one used by Innovation IT Solutions Corp (see the following WHOIS data):
Domain name | |
Registrant | Innovation IT Solutions Corp Andrey Nesterenko 95 Wilton Road, Suite 3 London London,SW1V 1BZ GB Tel. +44.8458692184 Fax. +44.8450205104 |
Creation date | 10/10/04 |
Expiration date | 10/10/09 |
Domain servers | |
Administrative contact | Innovation IT Solutions Corp |
Status | Active |
The IP address for the StopGeorgia.ru forum (75.126.142.110) can be traced backward from SteadyHost to Innovation IT Solutions Corp to SoftLayer Technologies, a US company based in Dallas, TX, with server locations in Seattle, WA, and Washington, DC. See Figure 7-7.
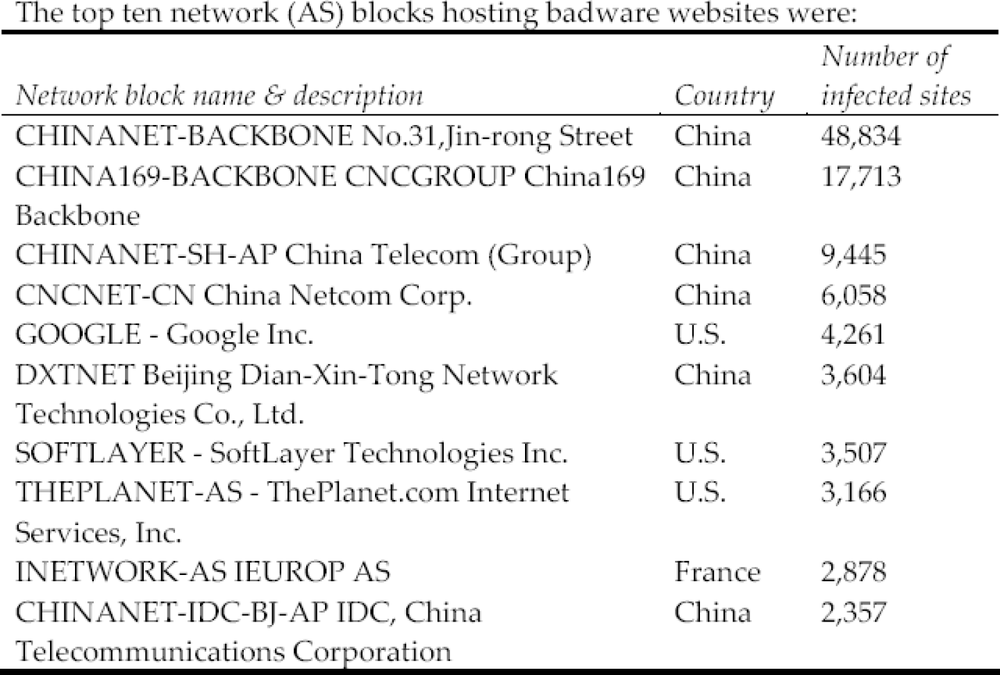
SoftLayer Technologies and The Planet (also in Dallas, TX) share the unique distinction of being on StopBadware.org’s top 10 worst badware network blocks (Figure 7-8). To add some perspective to this, StopBadware.org’s May 2008 report reveals China to be the world leader, hosting 52% of all badware sites, whereas the United States hosts 21%. None of the other countries involved, including Russia, individually hosts more than 4%.
When StopBadware.org released its report, it attempted to contact the companies that it named to give them an opportunity to respond. SoftLayer Technologies issued the following statement, published on the StopBadware.org blog on June 24, 2008:
SoftLayer Technologies is a provider of data center services centered around the delivery of on-demand server infrastructure. We do not manage the content or applications hosted from our infrastructure as this is the direct responsibility of our customers, many of which are in fact hosting resellers. Having said that, we also have a very strict acceptable use policy which you can find here: http://www.softlayer.com/legal.html.
We try to be as proactive as possible in eliminating any and all content from our network that breaches the terms of this policy. But, as I am sure you are aware, this is not always an easy task.
I have forwarded your email to our abuse department so that they can start investigating the findings you have suggested below. We will take all necessary actions to remove any malicious material from our network so that we can better serve our customers and the entire Internet community.
About 45 days later, the StopGeorgia.ru forum, hosted on a SoftLayer server, became a focal point for a nationalistic Russian hacker attack against Georgian government websites. At no time did SoftLayer Technologies take a proactive role and cancel StopGeorgia.ru’s access to its servers for a Terms of Service violation.
Even with a bulletproofed network, it’s important to remember that while the Kremlin provides open and global Internet access to its citizens, it also collects and controls all of the data originating within its borders.
A recent interview with Anton Nosik, the editor-in-chief of the Russian news website BFM.ru, was published in the Russian online newspaper the New Times. In it, Nosik spoke of SORM-2 (System of Operation Research Measures), which copies every byte of Internet traffic coming from Russian households and businesses and sends it to the Federal Security Service (FSB) via a redundant array of inexpensive disks (RAID).
Nosik also pointed out that the Kremlin either owns the pipes (Rostelekom, Transtelekom, and Elektrotelekom) or controls the licenses of every communications channel in Russia. This degree of control may work against the Russian Federation if an international body determines that it could have acted to stop cyber attacks originating from within its borders but didn’t.
One of the most difficult questions that the Project Grey Goose team faced in investigating the cyber war between Russian and Georgia was whether there was evidence of Russian government involvement. Our key finding in October 2008 was:
We assess with high confidence that the Russian government will likely continue its practice of distancing itself from the Russian nationalistic hacker community thus gaining deniability while passively supporting and enjoying the strategic benefits of their actions.
While forum members are quite open about their targets and methods, we were unable in this round of collection/analysis to find any references to state organizations guiding or directing attacks. There are several possible explanations as to why this is the case.
There was no external involvement or direction from State organizations.
Our collection efforts were not far-reaching or deep enough to identify these connections.
Involvement by State organizations was done in an entirely non-attributable way.
The situation has since changed. In February 2009, the Russian media reported a story that has provided new evidence pointing to how the Russian government sponsors and pays leaders of Russian youth organizations to engage in information operations, up to and including hacking, to silence or suppress opposition groups.
Nashi (http://nashi.su) is short for Molodezhnoye demokraticheskoye antifashistskoye dvizhenye “Nashi” (translation, “Youth Democratic Anti-Fascist Movement ‘Ours!’”). Its logo is shown in Figure 7-9. It was formed in 2005 to either counter the possibility of another youth revolt like the 2004 Orange Revolution in Ukraine or counter a growing interest in Nazism in Russia. Funding for the group purportedly comes from Russian business owners; however, there has been widespread speculation that it receives government funding as well, which has been strengthened in recent days by the Anna Bukovskaya story (related later in this section).
One of the most important supporters of Nashi is Vladislav Surkov, the first deputy chief of the presidential staff and, more importantly, a man who has the ear of Russian Prime Minister Vladmir Putin.
Surkov intends to use Nashi to enforce the Kremlin’s will regarding RUNET communications, i.e., “Ensure the domination of pro-Kremlin views on the Internet” (published by The New Times Online in Russian, February 16, 2009). That’s easier said then done, particularly since that effort was tried and abandoned about 10 years ago by RUNET co-founder Anton Nosek.
Surkov has a new plan that involves the enlistment of Russian youth organizations, including Nashi and United Russia. He has organized a March 2009 conference with about 20 key people in the Russian blogging community, as well as leaders of the aforementioned youth organizations, some of whom include:
Maksim Abrakhimov, the Voronezh commissar of the Nashi movement and blogger
Mariya Drokova, Nashi commissar and recipient of the Order for Services to the Fatherland Second Class medal for her “energetic” work in the area of youth policy
Mariya Sergeyeva, leader of the United Russia youth wing Young Guard
Darya Mitina, former state duma deputy and Russian Communist Youth Union leader
Other attendees included Russian spin doctors who specialize in controlling the messages communicated via the blogosphere. The objective was a straightforward Information Operation:
The aim of the conference is to work out a strategy for information campaigns on the Internet. It is formulated like this: “To every challenge there should be a response, or better still, two responses simultaneously.”
A source who is familiar with the process of preparations for the meeting explained:
If the opposition launches an Internet publication, the Kremlin should respond by launching two projects.
If a user turns up on LiveJournal talking about protests in Vladivostok, 10 Kremlin spin doctors should access his blog and try to persuade the audience that everything that was written is lies.
Although this campaign concerns internal Russian politics, it demonstrates the IO model that the Kremlin uses across the board, including what happened in Georgia in August 2008 thanks to the influence of Vladislov Surkov. His strategies were captured in the book Chronicles of Information War (Yevropa publishing house, Moscow, 2009), written by two Kremlin spin doctors, Maksim Zharov and Timofey Shevyakov. The following is from the book’s introduction:
Net wars have always been an internal peculiarity of the Internet—and were of no interest to anyone in real life. The five-day war showed that the Net is a front just like the traditional media, and a front that is much faster to respond and much larger in scale. August 2008 was the starting point of the virtual reality of conflicts and the moment of recognition of the need to wage war in the information field too.
Confirmation on the relationship between Nashi and the Kremlin came on April 10, 2009, when Nashi commissar Aleksandr Kuznetsov entered the nation of Georgia en route to Tbilisi to conduct an anti-government rally with 15 or 20 other Nashi members scheduled for April 16. Kuznetsov was arrested at the border, and during his interrogation he produced a letter from the Russian Duma’s Committee on Youth Affairs, requesting Russian officials along the way from Moscow to Tskhinvali to assist the “Moscow-Tskhinvali-Tbilisi Motorcade” in its mission. Nashi founder Vasili Yakemenko currently heads that committee.
In Vladimir Socor’s report of this event for the Eurasia Daily Monitor (April 17, 2009), he writes that Kuznetsov’s statements provide corroboration for earlier reports that Nashi is funded by First Deputy Chief of Presidential Staff Vladislav Surkov.
Anna Bukovskaya is a Nashi member and St. Petersburg activist who was paid by the Kremlin to spy on opposition political youth movements, according to an article in the Moscow Times (February 6, 2009):
Anna Bukovskaya, a St. Petersburg activist with the pro-Kremlin Nashi youth group, said she coordinated a group of 30 young people who infiltrated branches of the banned National Bolshevik Party, Youth Yabloko and United Civil Front in Moscow, St. Petersburg, Voronezh and six other cities.
The agents informed Bukovskaya, who passed the information to senior Nashi official Dmitry Golubyatnikov, who in turn contacted ‘Surkov’s people’ in the Kremlin, Bukovskaya told the Moscow Times. Vladislav Surkov is President Dmitry Medvedev’s first deputy chief of staff.
The agents provided information on planned and past events together with pictures and personal information on activists and leaders, including their contact numbers, Bukovskaya said by telephone from St. Petersburg.
They were paid 20,000 rubles ($550) per month, while she received 40,000 rubles per month, she said.
Bukovskaya provided more details during an interview on Russian Ren TV (February 4, 2009):
[Bukovskaya] The project was to become more aggressive, i.e., videos and photos to compromise the opposition, data from their computers; and, as a separate track, the dispatch of provocateurs.
In other words, computer espionage was part of the services Nashi provided, which isn’t surprising, since Konstantin Goloskov, one of the Russian hackers who acknowledged launching distributed denial of service (DDoS) attacks against Estonia, was a commissar in Nashi.
In March 2008, Nashi hackers were accused of orchestrating a series of DDoS attacks against the Russian newspaper Kommersant. A Nashi spokesperson denied that the group was involved.
In October 2007, another Russian youth movement known as The Eurasian Movement of the Youth (ESM) launched a DDoS attack against the president of Ukraine’s website, shutting it down for three days. Furthermore, both Nashi and the ESM participated in protests against the Estonian embassy in Moscow in May 2007.
The blog Windows on Eurasia (May 31, 2007) points to evidence that the FSB guides and encourages youth hackers such as the ESM to act on behalf of Russian government interests. For example, in early 2007, the ESM (http://www.axisglobe.com/article.asp?article=1419) threatened to disable the website of the Ukrainian Security Service:
ESM, the Russian radical youth organization that has been using sophisticated computer assets capable of disrupting a government computer network and eager to do so for political reasons, also vowed to disable the website of the Ukrainian Security Service (http://www.axisglobe.com/article.asp?article=444), SBU, in the near future, unless Yushchenko dismisses Valentyn Nalyvaychenko, SBU’s pro-NATO chief.
Russian journalist Andrei Soldatov wrote about the relationship between the FSB and Russian hackers in an article for Novaya Gazeta (May 31, 2007), beginning with Russian students from the Tomsk region attacking the Chechen news website KavkazCenter.com in 2002. Following the attack, the regional FSB office in Tomsk issued a special press release that said, “[T]he actions of the students do not contradict Russian law but rather is an expression of political orientation and worthy of respect” (Google translation from the Russian).
Soldatov also refers to the National Anti-terrorism Committee (NAC), which was established in 2006 by Vladmir Putin and chaired by Nikolay Patrushev, the director of the FSB, as having an interest in utilizing members of the Russian hacker community when it was in its interest to do so.
On March 3, 2009, Sergei Markov, a state duma deputy and member of the Unified Russia party, participated in a panel discussion with Russian and US experts, including James Lewis of the Center for Strategic and International Studies, about information warfare in the 21st century. During that discussion, Markov stunned everyone present by announcing that it was his assistant who started the Estonia cyber attacks in 2007. The following quote comes from Radio Free Europe, which broke the story on March 6, 2009, on its website:
“Markov, a political analyst who has long been one of Vladimir Putin’s glibbest defenders, went on to explain that this assistant happened to be in ‘one of the unrecognized republics’ during the dispute with Estonia and had decided on his own that ‘something bad had to be done to these fascists.’ So he went ahead and launched a cyberwar.
“‘Turns out it was purely a reaction from civil society,’ Markov reportedly said, adding ominously, ‘and, incidentally, such things will happen more and more.’”
Markov, a supporter of the Nashi youth movement, attended its second annual Innovation Forum on July 21, 2008—one day after the President of Georgia’s website came under a DDoS attack and 19 days before Russia’s invasion of Georgia.
It’s understandable to want to find a telltale piece of evidence that conclusively links the Kremlin with the actions of its hackers. However, it’s important to realize that in the anonymous workings of the Internet, such a goal is not only naive, but it also doesn’t accurately represent the relationships that have been built over the years between Russian politicians and organized youth associations.
The historical evidence presented in this chapter points to a three-tiered model (Figure 7-10) that establishes command and control by the Kremlin through Nashi and other groups whose membership includes hackers, resulting in an organized yet open call for unaffiliated hackers to join in. Russian organized crime provides a protected platform from which these attacks can then be planned and launched. And all of this occurs while providing a cover of plausible deniability to the state. It’s actually quite an impressive accomplishment from a strategic point of view.
The infrastructure—which not only makes those attacks possible but provides the environment for Russian hackers to thrive—is developed and owned by Russian organized crime interests such as Rove Digital, McColo, Atrivo/Intercage, ESTDomains, and others. We’ll further explore the longstanding relationship between the Kremlin and Russian organized crime in Chapter 8.