A well-designed, defensible network should have a number of monitoring elements available for forensic analysis when it is attacked or compromised. For example, most networks will have deployed intrusion detection systems, firewall and router traffic logs, and access logs contained on the server itself. There exists a bevy of tools and techniques that can allow an investigator to gain further insight using open source data. This includes routing information from the border gateway protocol (BGP), [37] domain name system (DNS), darknet monitoring, blacklist services (such as those offered by Spamhaus, CBL, etc.), and, to a lesser degree, Internet registry information (e.g., ARIN, RIPE, APNIC, etc.).
Performing a traceroute on each IP will show an experienced computer security engineer where the attacks originated from and what path the packets took to get to the target.
This chapter takes a rudimentary look at these computer forensic tools by way of some real-world examples.
The following serves as an introduction to several key internetworking concepts. This is fairly complex subject matter, and will be discussed only at a very high level here.
The border gateway protocol (BGP) is widely characterized as the “glue of the Internet.” Every Internet service provider uses BGP to move packets between source and destination nodes. Essentially, each BGP “speaking” router will dynamically maintain a table of network addresses, or “prefixes,” which details network availability.
For the sake of the examples outlined in this chapter, there are three main concepts you should understand:
- Autonomous system
“[A] collection of connected IP routing prefixes under the control of one or more network operators that presents a common, clearly defined routing policy to the Internet” (*RFC 1930)
- I-BGP
Internal Border Gateway Protocol; used to communicate routing information within a single autonomous system
- E-BGP
External Border Gateway Protocol; used to communicate routing information between separate autonomous systems
BGP data is a very powerful tool for attribution analysis. Using this information, it is possible for an investigator to identify the “source” network of an attack, as you’ll read about in the upcoming case studies.
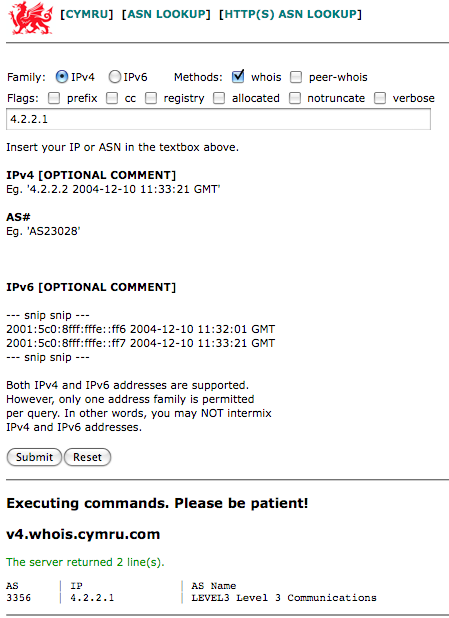
There are a number of ways to query BGP information that do not require access to an ISP router or knowledge of very specialized routing specifics. For example, using the Team Cymru IP to ASN service it is possible to retrieve global routing information, as shown in Figure 9-1.
The screenshot shows that IP address 4.2.2.1 is routed by autonomous system (AS) 3356, which is administered by Level 3 Communications. Another excellent resource is offered by RIPE.
The domain name system is another example of open source Internet data that can greatly aid an investigation into suspected intrusion IP addresses. DNS is a global hierarchal system, which allows a user to translate a common name (www.foo.com, for example) into an IP address. Based on its DNS name, it may be possible to uncover information that would help reveal the attacking IP address. For example, is the attacking machine a mail server or a web server? Could it be a router or a client machine located on a dial-up service? This information is very useful in determining technical attack attribution. There exist several online tools to assist in this search, including DomainTools.
It is also possible to leverage “black lists” to determine whether the suspect IP address has been associated with any previous malfeasance, such as spamming, scanning, or malware infection. Several organizations offer these services, including Spamhaus and the SANS Internet Storm Center.
On January 18, 2009, a large-scale distributed denial of service (DDoS) attack began against Kyrgyzstan Internet service providers (ISPs). Key national web server site Asiainfo.kg and the Kyrgyzstan official domain registration service Domain.kg have been available only intermittently since that date.
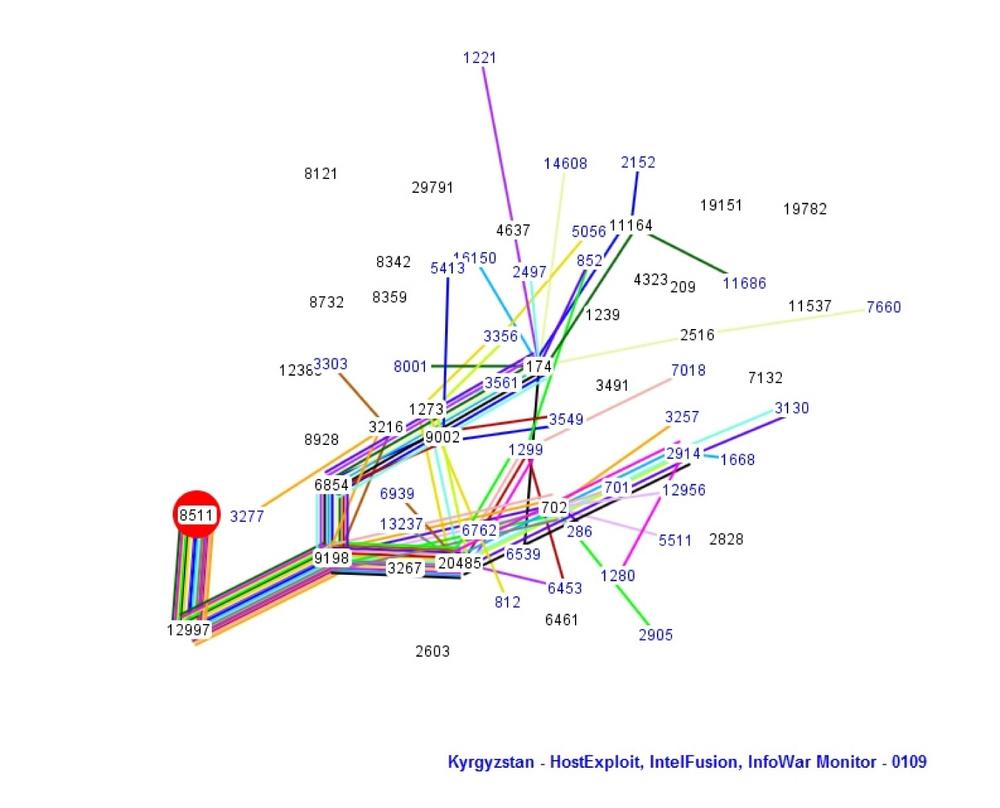
Russian-based servers primarily known for cyber crime activity have been identified through IP analysis of the attacks on Kyrgyzstan. Figure 9-2 shows the Internet routing during the later stages of the Kyrgyzstan DDoS attacks.
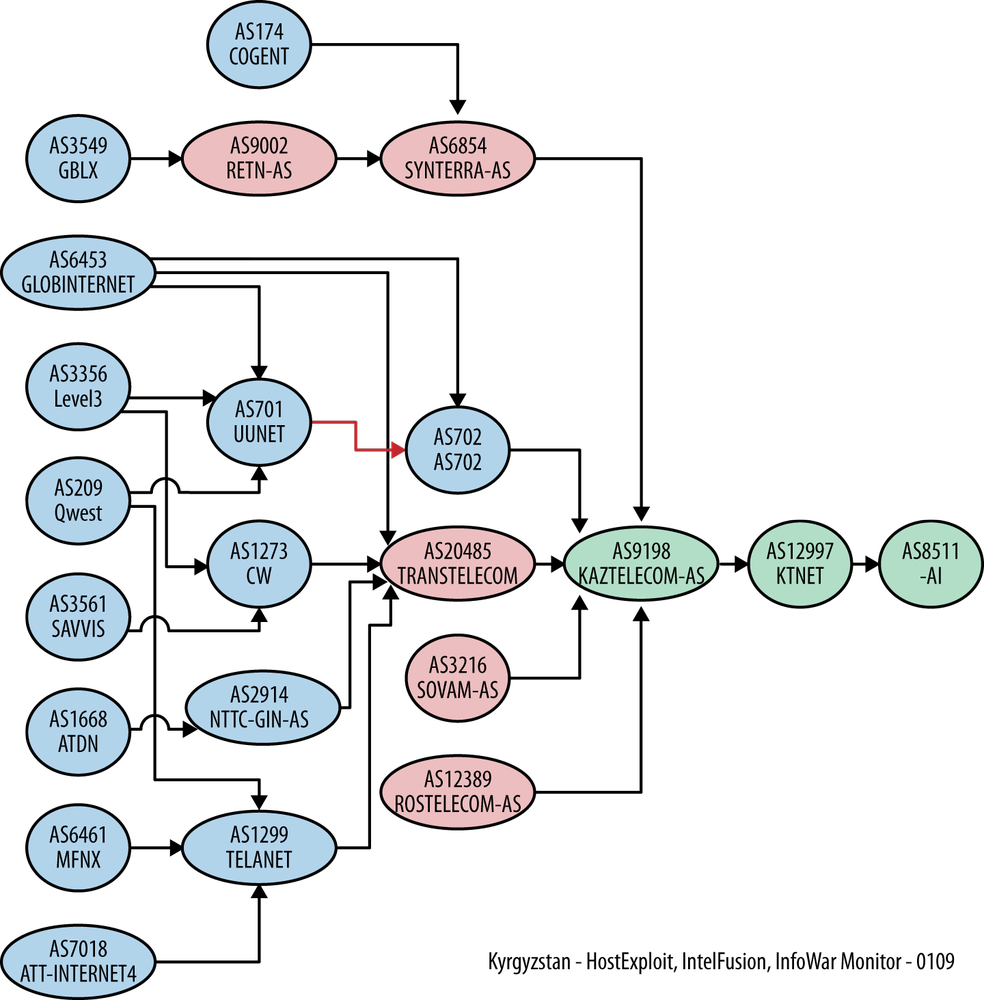
Figure 9-3 provides a BGP Internet traffic routing for the period of January 15, 2009, with a primary focus on highlighting the DDoS traffic against AS8511 Asiainfo of Kyrgyzstan. The BGP represents a route map for how Internet traffic should move from one ISP to another in the most efficient way.
Figure 9-3 is a diagram of packet flow through various autonomous system (AS) networks. If you look closely you’ll recognize a few that are mentioned in the table that supports the diagram. Packets don’t necessarily follow the maxim that says the shortest distance between two points is a straight line. In fact, that rarely happens. A traceroute is a sometimes complex path that packets take to move from the source to the destination. AS numbers act like intersections that help investigators discover the server networks that were used.
An AS number is linked to a block of IP addresses. These in turn are owned by a large Internet services company, such as The Planet, or a utility such as Qwest or ComCor TV, a Russian cable company.
When AS networks agree to carry one another’s traffic, it’s known as “peering.” Peering can occur in a few different ways, but typically it is either through swaps or some form of payment arrangement.
It’s important to note that just because these packets traveled through a Russian network, it doesn’t convey any geopolitical responsibility or “evidence.” The StopGeorgia.ru forum was, after all, hosted on a US-based server in Plano, TX, but no one is suggesting that the US government was involved in the cyber attacks against Georgian government websites.
For the purpose of investigating cyber attacks, the path is not nearly as revealing as the source. In the case of the attack data provided by individuals from ASIAINFO in Kyrgyzstan, some of the IPs resolved to Russian sources; for example, 78.37.132.241 was one of many attacking IPs, and it resolved to an AS network in St. Petersburg, Russia. Another IP (83.167.116.135) originated with Comcor TV in Moscow. Yet another, 86.60.88.191, originated in Riyadh, Saudi Arabia, and is blacklisted by a number of spam-tracking organizations.
In addition to running a traceroute on an attacking IP, it’s important to look at the timeline of conditions taking place within the country that is experiencing a cyber attack. The following timeline was created to help determine attribution in the 2009 Kyrgyzstan DDOS attacks. As of this writing, there is still no confirmation as to the party or parties responsible. What follows is merely my hypothesis of the most likely culprit, as published on the IntelFusion blog in January 2009.
| January 17: Prominent opposition leader detained in Kyrgyzstan |
| January 17: Political confrontation intensifies; opposition activists form new coalition United People’s Movement (UPM) |
| January 19: Two opposition leaders detained and charged |
| January 19: Russia presses Kyrgyzstan to close US base |
| January 20: Kyrgyzstan Opposition denied use of Parliament Press Center |
| January 21: Kyrgyzstan government targets opposition |
| January 22: Journalists ordered to file personal information |
| January 22: Kyrgyz Opposition Party denied registration |
The Kyrgyz cyber attacks during the week of January 18, 2009, fall right in line with an escalating series of repressive political actions by the Bakiev government against this latest attempt to form an opposition political party—the UPM. Bakiev should know, since it was the Tulip Revolution in 2005 (and the last time that DDoS attacks were utilized in Kyrgyzstan) that brought him to power.
Opposition leader Omurbek Tekebaev has pointed out the similarities between 2005 and 2009: “Both then and now, you could see people mistrusted those in power, who lacked moral authority. Both then and now, public opinion was completely controlled by the authorities, and there was persecution of journalists and dissidents, criminal persecution of political opponents,” he said in an IWPR article.
This appears to be a cyber operation for hire by the Bakiev government against its political opposition to control information access. The likely culprits are Russian hackers with moderate skill levels who regularly engage in cyber crime.
There is no evidence that the Russian government is directly involved; however, Moscow has complete control over the servers owned by JSC and Golden Telecom. To date, no action has been taken by the Russian Federation (RF) to deny access to these servers by Russian hackers.
Don Jackson of SecureWorks, an information and network services security provider based in Atlanta, GA, looked at the same evidence and came to a different conclusion. Jackson wrote in the SecureWorks Research blog on January 28, 2009, that the Kyrgyzstan DoS attack was a way for the Kremlin to influence Kyrgyz President Kurmanbek Bakiyev to close the Manas airbase, thus denying the US military effort in Afghanistan a key airport facility.
The problem with this alternate view is that the Kremlin had a much more powerful lever with which to influence the Bakiyev government: money. The Kyrgyz economy was being hard hit by the global economic crash of late 2008/2009, and the Kremlin offered an aid package of $2 billion US in loans if Kyrgyzstan were to close Manas. The Kyrgyz Parliament agreed, and US forces were to be out of the base by August 1, 2009.
As of this writing, there is yet a new twist. On June 25, 2009, the Kyrgyz parliament ratified a new agreement with the US government for the continued use of the Manas airbase to transport supplies to Afghanistan. The price tag? $60 million for one year, more than triple the old rate.
In the face of such lengthy and complex negotiations, a tiny DoS attack that lasted for only a few days hardly seems like an instrument of Kremlin policy in this particular case.
In addition to these two possible explanations, a third may be a dispute between competing ISPs operating within the country. This possibility was recently presented to the author by a colleague who visited Kyrgyzstan and spoke personally with the parties involved.
A final lesson on the Kyrgyz DoS attack of 2009 is the value of alternative analysis, particularly on all questions of attribution.
“Who is looking at your SCADA infrastructure?” a briefing paper that Team Cymru published in early 2009, looks at scans that they spotted in a region of cyberspace where such scans should not have been occurring (i.e., no active services or servers reside there) and therefore any activity or traffic is deemed malicious to some degree. They referred to this region as a “darknet.” As explained in the briefing paper, “Traffic entering a Darknet normally comes from scans generated by automated tools and malware, looking for vulnerable ports with nefarious intent.” These ports belong to Supervisory Control and Data Acquisition (SCADA) systems.
SCADA systems are typically used by utility companies, nuclear power plants, water treatment systems, communications systems, and various industrial processes. Although these systems do have safeguards, they remain vulnerable to a variety of cyber attacks for a number of different reasons. A complicating factor in safeguarding them is the antiquity of the software employed, in some cases dating as far back as the 1970s. More modern SCADA software has updated security, but it relies on the public Internet. Generally speaking, attackers will scan for vulnerabilities and tailor their attacks based on what they find.
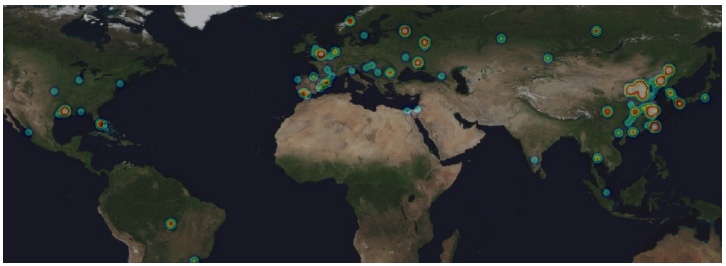
Team Cymru researchers recorded the IP addresses of the machines generating these port scans and identified a geographical location for each using traceroute (see Figure 9-4):
- USA
The two main hotspots for scanning appear to emanate from IPs located in Houston, Texas, and Miami, Florida.
- Western Europe
There are hotspots in London, United Kingdom, Seville, Spain, and locations in Scandinavia and Southern France.
- Eastern Europe
Hotspots in this region include St. Petersburg and Moscow, as well as a location in the Ukraine and Bucharest, Romania.
- Far East
By far the most concentrated grouping of hot spots, the Far East contains concentrations of SCADA-scanning IPs in Thailand, Hong Kong, Taiwan, Korea, Japan, and several locations in China.
The authors of this report believe that the scans are being generated by infected computers, hence the geolocation of scanning IPs should not be construed as evidence of espionage activities by a foreign government or nonstate actor from that region. The preceding information refers to scans of the following SCADA-associated ports: udp/20000, tcp/502, udp/2222, and tcp/44818.
Any time an individual or company seeks to register a URL, they are legally required to provide accurate identifying data (name, address, contact information). This is an ICANN requirement and is enforced by many of the legitimate providers of domain registration services. Unfortunately, not all providers perform their watchdog duties as well as they should, including ICANN itself (although their rate of fraudulent registrations has decreased recently).
In the case of StopGeorgia.ru, the domain was registered to an alias that appeared on numerous spam sites (see Chapter 7). This works well with domain registration services that do not perform verification checks on all new applications. Unfortunately, there are a number of companies that regard lax registration as a fair trade-off for an increase in sales revenue. This is a critical part of the puzzle for criminal enterprises operating on the Internet.
In other cases, domains are registered with stolen data. In one case that was reported to me, the stolen data was from a US serviceman deployed in Iraq. When he returned to the United States at the end of his tour, he was contacted by his service’s investigative division in reference to his “terrorist” website. The investigation was dropped once it was determined that his identity had been stolen and used to register the domain name; however, that determination didn’t happen in a timely manner and caused quite a bit of consternation on the part of the serviceman and his family.
Nevertheless, checking WHOIS registrations does provide another link in the evidence chain. Sometimes mistakes are made and actual government websites are used as the identifying data (e.g., GhostNet). This is rare, but it does happen. Part of any OSINT investigation is looking for the small oversights that even the most careful individuals make from time to time.
The Cambridge University investigation of the Chinese espionage operation against the Office of His Holiness the Dalai Lama (OHHDL) underscores the value of checking WHOIS data:
During our initial network monitoring exercise, we observed sensitive files being transferred out of the OHHDL using a modified HTTP protocol: the malware picked up files from local disks and sent them to three servers which, according to APNIC, were in China’s Sichuan province, using a custom protocol based on HTTP. The malware uses HTTP GET and HTTP POST messages to transfer files out and also appears to verify successful transmission. Sichuan, by the way, is the location of the Chinese intelligence unit specifically tasked with monitoring the OHHDL.
Note
WHOIS information can be checked with numerous free online Internet toolkits, such as http://www.dnsstuff.com, http://www.robtex.com, http://www.demon.net/external/, and http://www.whois.sc, simply by entering either a domain name (sans the “www”) or an IP address.
There are numerous caveats to using WHOIS in an investigation.
The information contained on a cyber warfare, extremist, or hacker website will most likely be stolen, fraudulent, or garbled. Even legitimate registrants may elect to use a privacy service to mask their WHOIS information.
Another caveat is that multiple websites may be hosted on the same server and yet have nothing to do with one another.
In spite of these issues, an investigation into WHOIS information still may provide pieces of a larger puzzle. The following are some tips that might prove useful when investigating other attack platforms similar to StopGeorgia.ru that engage in cross-border cyber attacks:
If the data is clearly fraudulent (garbled or nonsensical name and address info), it is not a legitimate site.
If the data appears to be legitimate but a web search on the name and email address shows it was used to register numerous blacklisted websites, then again, it is not a legitimate site.
If, as in the case of Innovative IT Solutions Corporation (the hosting company for the StopGeorgia.ru domain), the data is accurate, the next step is to perform a web search on the business address.
If multiple businesses are registered at the same address, it is most likely a mailbox rental facility, and chances are the business is a front for other purposes.
If the business location is adjacent to a government office or, even better, a Ministry of Defense office (as was the case with Steadyhost.ru in Chapter 7), you have secured another piece of the investigative puzzle.