Some of the information regarding the US Department of Defense organizational chart has been changed since this chapter was written. A few changes are represented in the footnotes; however, the DoD’s process of reshaping itself is ongoing and their review process was too lengthy to meet the publishing requirements for this second edition. Thus, readers are encouraged to check the facts contained in this chapter with the latest guidance from the US DoD.
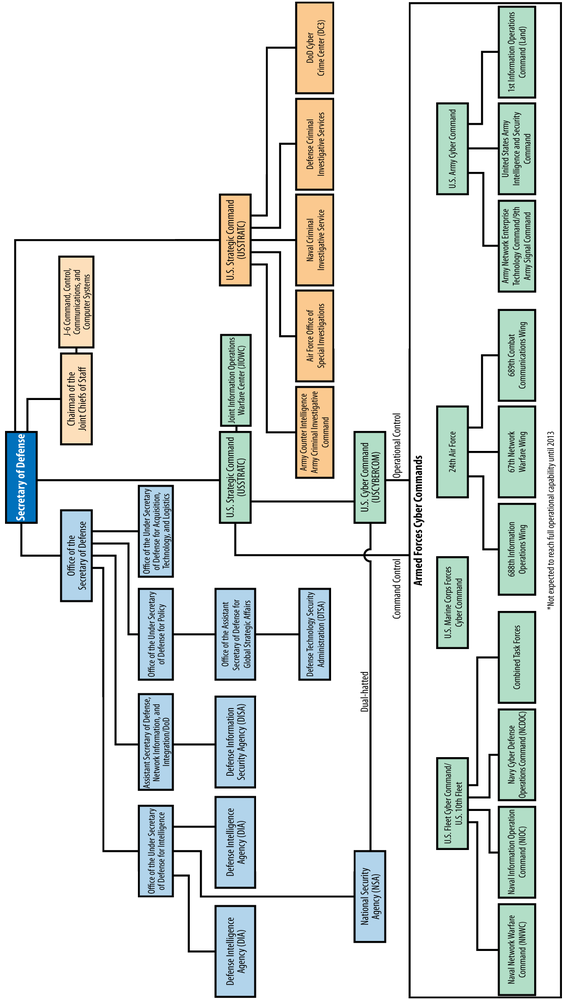
The US Department of Defense (DOD) has taken a decentralized approach to the organization of its cyber security structure. There are various organizations, divisions, and agencies that address the DoD’s cyber security needs at both the policymaking and operational levels. The Joint Chiefs of Staff, the US Joint Forces Command (JFCOM), and several offices within the Office of the Secretary of Defense have roles in developing policy and guiding cyber security strategy.[207] At the operational level, the central organization to DOD’s cyber security efforts is US Cyber Command (USCYBERCOM), which was created in June 2009 under US Strategic Command (USSTRATCOM).[208] The Joint Information Operations Warfare Center (JIOWC) was also created to plan, integrate, and synchronize information operations (IO) in direct support of Joint Force Commanders and to serve as the USSTRATCOM lead for enhancing IO across the Department of Defense. Additionally, the director of the NSA doubles as the director of USCYBERCOM, making them dual-hatted organizations.[209]
Each branch of the military has designated a support component for cyber security that operates under USCYBERCOM. These are the US Army Cyber Command, the US Fleet Cyber Command/US 10th Fleet, the 24th Air Force/AFCYBER, and the Marine Corps Cyber Command (able to conduct cyber operations but is not expected to achieve full operational capability until 2013).[210] There are several other DOD organizations that play an important role in cyber security. Network Operations Security Centers (NOSCs) provide network-operations reporting and situational awareness for each of the military service branches, as well as for the various theater commands. The National Guard and the DOD Criminal Investigative Services also have cyber security functions.[211]
Figure 17-1 shows the US Department of Defense’s cyber organizational structure.
The following list outlines the DOD’s cyber security organizational structure, including the cyber-related roles and responsibilities of each organization.
Establishes and develops doctrine, policies, and associated joint tactics, techniques, and procedures (TTP) for DOD’s global information grid (GIG), information assurance (IA), and joint and combined operations.
Ensures all joint education, training, plans, and operations include, and are consistent with, information operations (IO) policy, strategy, and doctrine.
- Global Operations (Information Operations and Computer Network Operations), J-39
Focal point for IO within the Joint Staff.
Provides recommendations and advice to the President, Secretary of Defense (SECDEF), National Security Council (NSC), and Homeland Security Council (HSC) on all aspects of computer network operations (CNO).
- Information and Cyberspace Policy, J-5
Develops policy that contributes to effective execution of information and cyberspace operations.
Develops policy that contributes to military freedom of action in cyberspace.
Establishes joint cyberspace policies for effective strategic planning.
Fosters joint and interagency collaboration regarding cyberspace issues, including national cyber initiatives.
- Network Operations, J-63
Develops DOD and Joint Staff strategies and positions for cyberspace and network operations.[212]
Recommends and synchronizes cyberspace and network operations guidance in joint doctrine.
Researches, reviews, and synchronizes DOD and joint network operations policies in DOD directives, instructions, and Joint Staff policies.
- Joint Education and Doctrine, J-7
Coordinates with the military services and combatant commands to integrate computer network attack and information operations doctrine into joint doctrine for military operations.
- Assistant Secretary of Defense, Network information, and Integration/DOD CIO
Assists SECDEF on network policies, information technology (IT), network operations, and IA.[213]
Provides strategic-level guidance and oversight for CNO including network operations and IA.
- Defense Information Security Agency (DISA)
Handles day-to-day management of DOD’s GIG, communication, and computer-based information systems.
- Office of the Under Secretary of Defense for Intelligence
Assists SECDEF in IO.[214]
Develops and oversees DOD IO policy and integration activities.
Establishes and oversees specific policies for the integration of CNO, including computer network attack (CNA).
Leads on IO issues within the intelligence community.
- Defense Intelligence Agency (DIA)
- National Security Agency (NSA)
- Defense Security Service (DSS)
- Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics
Incorporates policy and processes into the DOD acquisition process that supports the protection of controlled unclassified information with unclassified DIB networks.
Maintains oversight of the process to conduct damage assessments after unauthorized access to DOD information from an unclassified DIB network.
- Office of the Under Secretary of Defense for Policy
- Office of the Assistant Secretary of Defense for Global Strategic Affairs
- Defense Technology Security Administration (DTSA)
- Joint Information Operations Warfare Center
- US Cyber Command (USCYBERCOM)
- US Army Cyber Command
- Army Network Enterprise Technology Command / 9th Army Signal Command
- US Army Intelligence and Security Command
- 1st Information Operations Command (Land)
- US Fleet Cyber Command/US 10th Fleet
- Naval Network Warfare Command (NNWC)
- Naval Information Operation Command (NIOC)
- Navy Cyber Defense Operations Command (NCDOC)
- Combined Task Forces
(Intentionally blank.)
- 24th Air Force
- 67th Network Warfare Wing
- 688th Information Operations Wing
- 689th Combat Communications Wing
- US Marine Corps Forces Cyber Command
- National Guard
- Army National Guard
(Intentionally blank.)
- Air Force National Guard
(Intentionally blank.)
- Service Network Operations Security Centers
Provides a secure, centralized, system management and monitoring environment for Network, Operations, and Applications infrastructure.
Provides direct support to the geographic combatant commands and marine corps forces for theater network operations issues and, in its entirety, fulfills its direct support responsibilities.
- Army
(Intentionally blank.)
- Navy
(Intentionally blank.)
- Air Force
(Intentionally blank.)
- Marine Corps
(Intentionally blank.)
- Theater Network Operations Security Centers (JFCOM, NORTHCOM, SOUTHCOM, TRANSCOM, SOCOM, CENTCOM, AFRICOM, EUCOM, PACOM)
Conducts computer network defense to secure each portion of the DOD GIG.
JFCOM is a voting member of the joint doctrine development community.
NORTHCOM is lead in assisting the Department of Homeland Security and other civilian agencies during cyber-related incidents as part of its Defense Support of Civil Authorities missions, or civil support.
- Army
(Intentionally blank.)
- Navy
(Intentionally blank.)
- Air Force
(Intentionally blank.)
- Marine Corps
(Intentionally blank.)
- Department of Defense Criminal Investigative Services
- Army Counter Intelligence and Army Criminal Investigative Command (Army CID/IC)
- Air Force Office of Special Investigations (AF OSI)
- Naval Criminal Investigative Service (NCIS)
- Defense Criminal Investigative Services (DCIS)
- DOD Cyber Crime Center (DC3)
Provides criminal, counterintelligence, counterterrorism, and fraud-related computer forensics support to the defense criminal investigative organizations.
Delivers cyber technical training.
Processes digital evidence and analyzes electronic media for criminal law enforcement and DOD counterintelligence investigations and activities.
Performs investigations and provides forensic training to DOD members to ensure that information systems are secure from unauthorized use.
[207] GAO, “Defense Department Cyber Efforts: DOD Faces Challenges In Its Cyber Activities,” US Government Accountability Office, July 2011, http://www.gao.gov/products/GAO-11-75.
[208] Ibid.
[209] GAO, “Defense Department Cyber Efforts: More Detailed Guidance Needed to Ensure Military Services Develop Appropriate Cyberspace Capabilities,” US Government Accountability Office, May 2011, http://www.gao.gov/products/GAO-11-421.
[210] Ibid.
[211] GAO, “Defense Department Cyber Efforts: DOD Faces Challenges In Its Cyber Activities,” US Government Accountability Office, July 2011, http://www.gao.gov/products/GAO-11-75.
[212] JS J6 has been disestablished as per the DOD Efficiencies Study: Networks and Information Integration (NII) and J6 Disestablishments (FY 2012, $13 million, FYDP, $65 million)—Transfers acquisition program oversight responsibilities from the Assistant Secretary of Defense for Networks and Information Integration (ASD(NII)) to the Under Secretary of Defense for Acquisition, Technology, and Logistics (USD (AT&L)) and all remaining NII responsibilities to the DoD Chief Information Officer (CIO). The Joint Staff will transfer its J6 (Command, Control, Communications, and Computer Systems) funding and manpower to the DoD CIO and the US Cyber Command beginning in FY 2012.
[213] See the note above about disestablishment of the JS J6 and the passing of functions from the ASD/NII to the DOD CIO.
[214] IO responsiblities have passed from Ms. Rosemary Wenchal at OUSD(I) to Mr. Austin Branch at OUSD(P).