Anybody you meet will tell you that weak passwords are responsible for dozens of successful intrusions, both local and remote. As a trained network administrator or security engineer, you have counselled users to make their passwords stronger many times. What you may not be aware of is that many technology professionals make weak passwords or patterns of passwords that endanger not just their own accounts, but the entire network which they maintain. This chapter will show you several tools for testing the passwords on your network, so you can help guide your users to the habit of better passwords:
- Password Attack Planning
- Creating or Adapting Password Lists
- Tools for Creative Password Cracking
- Meet My Friend Johnny
- Meet Johnny's Dad, John the Ripper
- Meet the Ex – xHydra
It is the nature of hashing algorithms to have all hashes be about the same length, and it really doesn't seem any more likely that someone could crack this algorithm as following:
$6$NB7JpssH$oDSf1tDxTVfYrpmldppb/vNtK3J.kT2QUjguR58mQAm0gmDHzsbVRSdsN08.lndGJ0cb1UUQgaPB6JV2Mw.Eq.
Any quicker than they could crack the following alogrithm:
$6$fwiXgv3r$5Clzz0QKr42k23h0PYk/wm10spa2wGZhpVt0ZMN5mEUxJug93w1SAtOgWFkIF.pdOiU.CywnZwaVZDAw8JWFO0
Sadly, even on a slow computer, the first hash of a password Password is going to be cracked in fewer than 20 seconds, while the second password hash for GoodLuckTryingToCrackMyPassword! may take several months to crack. The list illustrated in the following contains some of the passwords you will find in any of the dozens of word lists you can find on the Internet, and which make cracking passwords so much easier. Some common hashes can be cracked by https://www.google.co.in, just by pasting the hash into the search bar. Most web applications and operating systems add a few characters, called salt, to the user's password choice, so as to make a simple cryptographic hash a bit more complicated and less guessable.
The following image shows the nature of hashes. For each word in the top set, no matter how long the word, the hash below is exactly the same size. It is, however, exponentially more difficult to brute-force a longer password than a shorter one:

Passwords are normally the keys to any system or network. Ever since the dawn of computers, passwords have been used to lock system data from unwanted eyes. So, password cracking is a much-needed skill in the hacking trade. Capture or crack the right password and you have the keys to the kingdom, access to anywhere, any time. We'll also talk a bit about creating strong passwords as we go along. If you are a Systems Administrator reading this book, you're the person we are talking about. It is your password an attacker is going after. Sure, typing a 12 or 14 character password every time you log in to something is a pain, but how important is your network?
Personally, we wish the word "password" hadn't been used for this function from the beginning. It should be called "keys". Normal users of systems cry and whine about password-protected data. Most relate the word password to entry into a clubhouse or something. A user will have locks and burglar alarms on all his property but will use a four letter password on his computer. People relate the word "key" to locking something important. Actually, if your password is just a "word" you will be pwned in minutes. Its best to use "pass phrases"; something like "Mary had a little lamb." is a lot better than just a word. We'll see just how important this is in this chapter as we crack think about the passwords you use.
One method of password attacks we have covered in Chapter 5, Sniffing and Spoofing. On a Windows network running NetBIOS, capturing NTLM hashes is child's play. They're just floating around in the ARP cloud waiting to be plucked. As we have shown in earlier chapters, when you are using Metasploit, you don't need to even crack this hash to a password but can just pass the hash to another Windows system.
Sometimes you need the actual password. System admins sometimes get lazy and use the same password on several classes of device. Let's say you have some Windows hashes and you need to get into a router or a Linux machine for which you are not sure of the password. There is a good chance that the passwords are the same on other systems, so you can crack the hashes that the NTLM protocol leaks. Lots of us are guilty of reusing passwords for infrastructure devices, even though we know better. It might be safer to use different usernames and passwords for routers and other infrastructure devices, and never use the Domain Administrator accounts to log into any machines, unless it is absolutely necessary.
In this chapter, we will be looking at cracking passwords and not just passing hashes.
For any good password cracker, sometimes the fastest way to crack a password is using a password list. It's even best to sometimes run a list of, say, the 500 worst passwords against the users on your system to find those lazy lusers who are using bad passwords. A bad password most of the time can be broken in seconds compared to hours, days, or weeks when using a strong pass-phrase.
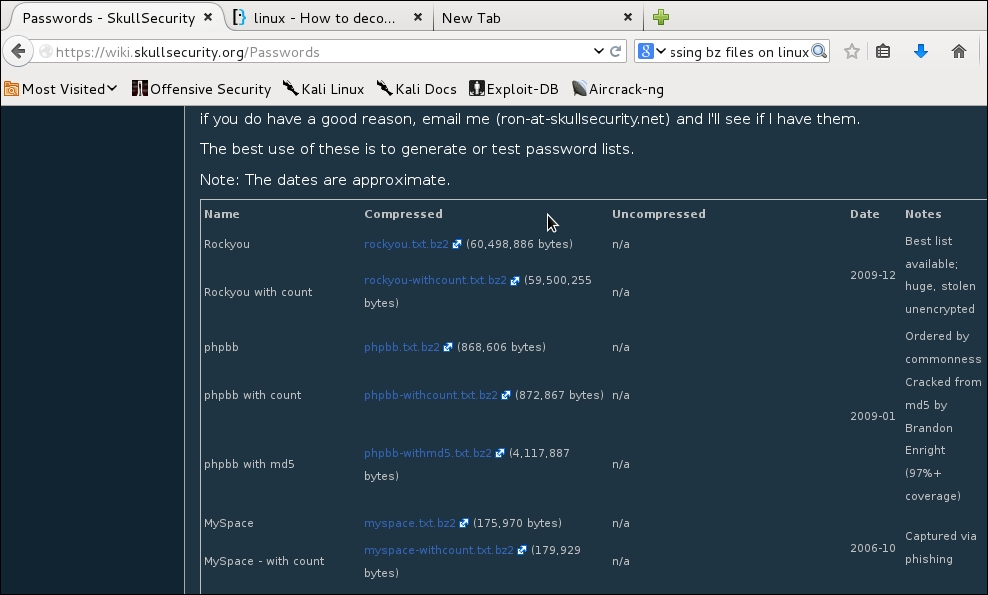
Following is a link and a listing of some good password files. A Google search will also lead you to lists of common passwords and also lists of passwords stolen from websites. When using a list of stolen passwords, only use the lists that have been scrubbed of the user names. Using a full set of stolen credentials (username & password) could land you in trouble. With a list of just passwords, you just have a list of words with no link back to the original user. This is safe and legal to use: https://wiki.skullsecurity.org/Passwords
Sometimes when you get a list of passwords, the list might be tabbed columns in a text file or may have strange spaces of tabs mixed with the words in the file. You'll want to clean these spaces and tabs and have a single word per line for the word list to work with password crackers.
One of the earliest concepts of Unix was small programs within the system that can be piped together to perform complex tasks. Linux is the Red-Headed Cousin of Unix, and these tools are in every distribution of Linux, including Kali. This is "Old School", but it works so well once you understand how to do it. We are going to go through each program used and then show how to string these together to perform this task all in a single line of commands.
Following is a list of 500 common passwords. The words were listed in an HTML table and the rows were numbered, so when copied to a text file what we get in the raw form is as follows. Most of the word lists you can find have approximately the same extremely common bad passwords, and though we are working in English, there are wordlists in other languages. Weak passwords are not strictly the province of the English-speaking world.
That said, the next image is a great example of very common, but very weak, English-language passwords. It would waste space to show all 500 words, so we are presenting the 500-common-original.txt file on the publisher's website:

Note we have the line numbers to the left, which we need to discard, and five words per line separated by tabs and spaces. We will want to move each word to a new line.
The cat command reads a text file, and prints to out to the screen or to another file. Using it along with the cut command, we will strip out the line numbers first. The cut command sees the tabs as spacers between fields so the numbers are the first field in the line. We want to cut the numbers and leave the words, so we cut the first field and keep the others. To do this, run the following:
cat 500-common-orginal.txt | cut -f2
We get the returned output return as follows. If you look, you will see that this is a list of the first word only in every line and not the whole list. Using the -f2 flag, we have cut everything except the second field in every line. The following image has some words scrubbed out to keep this book's Grating, but some people are vulgar by nature. Some words in the list may not be fit to print, but they are in the top 500 common passwords. When hacking, you are dealing with a person's nature, and that is not necessarily socially correct. People are often found to choose rude words, when they believe nobody will ever see what they wrote, or where they believe themselves to be anonymous:

Since we want all the words from each line, and we have to include the other five columns in the command, five words in a line, plus the number, is six fields to a line, and we want to cut the first field (the number) and keep the rest, so we change the -f flag to -f2-6. This will cut field 1 and print out fields 2 through 6. We see in the following that the return has cut out the number row, but we still have five words per line. This will not run correctly in the password cracker; we still need to move all the words to their own line:
cat 500-common-orginal.txt | cut -f2-6
This command string gets rid of the line numbers, though it would not be a matter of more than a couple of seconds to leave the line numbers in. It wouldn't be as neat, though, and sometimes neatness counts. The following image is the output of the command:

To get all the words on a new line we use the --output-delimiter flag and use the value of $'
', which tells us the output for every delimiter, which is the tab space in the line, to move the next field to a new line:
cat 500-common-orginal.txt | cut -f2-6 --output-delimiter=$'
'

Now we have each word on a new line, but we also need to print this to a file for use. To do this, we will use the redirect command > to send the output to a new text file. Be careful, the > command sends the output of the commands being run to a file, but if the filename exists, it will overwrite the contents of the file. If you want to increase the size of a file you already have, use the command >> to append the output to an already existing file.
The following image shows the commands sending the words to the working file of weak passwords, and to test the output file for content and format:

Run the ls command to double-check that you are in the right directory, and that your chosen output file does not exist, then run the following to output to a file:
cat 500-common-orginal.txt | cut -f2-6 --output-delimiter=$'
' > 500-common.txt
Notice that this time there is no output to the screen, but when the ls command is run again we see the new file in the working directory. By cutting the new file, we see our new password file ready for use.
