John the Ripper is the application that underlies Johnny. You may be like us, and be more comfortable on the command line than in a GUI when using the password cracking tools, like John the Ripper. You may go for the CLI because it uses fewer resources than the GUI, or because you are working through a ssh connection to a server without a GUI interface. It is easy to use John the Ripper, and there are a lot more options and ways to use John by using the command lines that have not yet been added to Johnny.
You can see all the various hashing algorithms supported by John and test the speed of your system for cracking by running the following command:
john –test
This will run through all the various hashing algorithms supported by John and give you the time it will take for the various hashes. The following image shows the read-out from the test flag:

We're going to run John against a set of hashes obtained from an earlier exploitation of a system. Note the flags we are using to perform this. We are using –format=nt2 and then picking the file:
john –format=nt2 hashdump.txt
With this cracking run, we are cracking passwords that are more than 6 characters. Note the time it has taken to run this process. This shows that when it comes to passwords, the length is more important than the complexity.
In the following screenshot, you can see that it took 1 day and 23 hours to crack a pretty simple 7 character password. The second password, which was 8 characters long, did not crack after 4 days 14 hours and 56 minutes. Yes, each extra character makes the time it takes to crack grow exponentially:
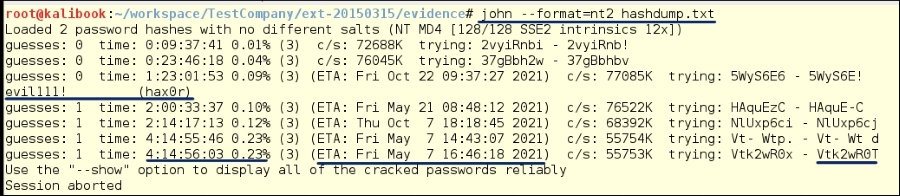
By running the –show flag after the run, you can see the cracked word and that we have one still left to crack:

This cracking was done on a VM with one running processor. Adding processors will increase the number of running treads during cracking, and that makes the job take less time. People have built machines filled with processors and GPU cards that can crack passwords like we are using in a matter of hours. Even if your neighbourhood evil hacker has these kinds of systems, the longer password is still better. Systems like these are the reason for using passwords or pass-phrases with a length over 14 characters. Even with pass-phrases over 14 characters, this shows that if you have the hash, it is just a matter of time and processing power before you have the password.
